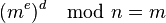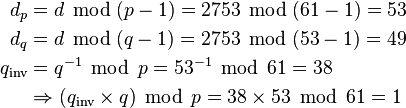RSA (cryptosystem)
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
RSA is one of the first practical实用性的 public-key cryptosystems and is widely used for secure data transmission.
In such a cryptosystem密码系统, the encryption key is public and differs from the decryption key which is kept secret. 加密的key是公开的,解密的key是保密的
In RSA, this asymmetry不对称 is based on the practical difficulty of factoring因素 the product of two large prime numbers, the factoring problem.
RSA is made of the initial letters of the surnames of Ron Rivest, Adi Shamir, and Leonard Adleman, who first publicly described the algorithm in 1977.
Clifford Cocks, an English mathematician数学家 working for the UK intelligence agency情报机构 GCHQ, had developed an equivalent system in 1973, but it was not declassified撤销文件的机密等级 until 1997.[1]
A user of RSA creates and then publishes a public key based on two large prime numbers, along with an auxiliary辅助的 value.
The prime numbers must be kept secret.
Anyone can use the public key to encrypt a message, but with currently published methods,
if the public key is large enough, only someone with knowledge of the prime numbers can feasibly切实 decode the message.[2]
Breaking RSAencryption is known as the RSA problem; whether it is as hard as the factoring problem remains an open question.
RSA is a relatively slow algorithm, and because of this it is less commonly used to directly encrypt user data.
More often通常, RSA passes encrypted shared keys for symmetric对称的 key cryptography密码学;密码使用法 which in turn can perform bulk encryption-decryption operations at much higher speed.
Operation
The RSA algorithm involves four steps: key generation, key distribution, encryption and decryption.
RSA involves a public key and a private key. The public key can be known by everyone and is used for encrypting messages.
The intention is that messages encrypted with the public key can only be decrypted in a reasonable amount of time using the private key.
The basic principle behind RSA is the observation that it is practical to find three very large positive integers e,d and n such that with modular exponentiation 模幂运算for all m:
and that even knowing e and n or even m it can be extremely difficult to find d.
Additionally, for some operations it is convenient that the order of the two exponentiations can be changed and that this relation also implies:
Key distribution
To enable Bob to send his encrypted messages, Alice transmits her public key (n, e) to Bob via a reliable,可靠的 but not necessarily secret route路线, and keeps the private key d secret and this is never revealed透露 to anyone. Once distributed the keys can be reused over and over.
公钥(m,e) 私钥d
Bob用公钥将信息加密后,发送给Alice。 只有Alice自己知道私钥
Encryption
Bob then wishes to send message M to Alice.
He first turns M into an integer m, such that 0 ≤ m < n and gcd(m, n) = 1 by using an agreed-upon reversible可逆的 protocol known as a padding scheme.
He then computes the ciphertext密文 c, using the public key e of Alice, corresponding to
This can be done efficiently, even for 500-bit numbers, using modular exponentiation. Bob then transmits c to Alice.
Decryption
Alice can recover m from c by using her private key exponent d by computing
Given m, she can recover the original message M by reversing the padding scheme.
Key generation
The keys for the RSA algorithm are generated the following way:
- Choose two distinct prime numbers p and q.
- For security purposes, the integers p and q should be chosen at random, and should be similar in magnitude量级 but 'differ in length by a few digits'[2] to make factoring harder. Prime integers can be efficiently found using aprimality test.
- Compute n = pq.
- n is used as the modulus模数 for both the public and private keys. Its length, usually expressed in bits, is the key length.
- Compute φ(n) = φ(p)φ(q) = (p − 1)(q − 1) = n − (p + q − 1), where φ is Euler's totient function. This value is kept private.
- Choose an integer d such that 1 < d < φ(n) and gcd(d, φ(n)) = 1; i.e., d and φ(n) are coprime.
- Determine e as e ≡ d−1 (mod φ(n)); i.e., e is the modular multiplicative inverse of d (modulo φ(n))
-
-
- This is more clearly stated as: solve for e given d⋅e ≡ 1 (mod φ(n))
- e having a short bit-length and small Hamming weight results in more efficient encryption – most commonly 216 + 1 = 65,537. However, much smaller values of e (such as 3) have been shown to be less secure in some settings.[13]
- e is released as the public key exponent.
- d is kept as the private key exponent.
-
The public key consists of the modulus n and the public (or encryption) exponent e. The private key consists of the modulus n and the private (or decryption) exponent d, which must be kept secret. p, q, and φ(n) must also be kept secret because they can be used to calculate d.
- An alternative, used by PKCS#1, is to choose d matching de ≡ 1 (mod λ) with λ = lcm(p − 1, q − 1), where lcm is the least common multiple. Using λ instead of φ(n) allows more choices for d. λ can also be defined using theCarmichael function, λ(n).
Since any common factors of (p-1) and (q-1) are present in the factorisation of p*q-1,[14] it is recommended that (p-1) and (q-1) have only very small common factors, if any besides the necessary 2.[15][2][16]
Example
Here is an example of RSA encryption and decryption. The parameters used here are artificially small, but one can also use OpenSSL to generate and examine a real keypair.
- Choose two distinct prime numbers, such as
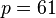 and
and 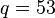 //233*9001
//233*9001
- Compute n = pq giving
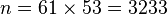 //2097233
//2097233
- Compute the totient欧拉函数 of the product as φ(n) = (p − 1)(q − 1) giving
 //2088000
//2088000
- Choose any number 1 < d < 3120 that is coprime 互质 to 3120.
Choosing a prime number for d leaves us only to check that d is not a divisor因子 of 3120.
- Let
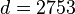 //d不能是3120的因子
//d不能是3120的因子
5.Compute e, the modular multiplicative inverse of d (mod φ(n)) yielding, 2753*e%3120=1;

- Worked example for the modular multiplicative inverse: 通过计算得到e

 d*7%2088000=1;求出d=1193143
d*7%2088000=1;求出d=1193143
The public key is (n = 3233, e = 17). For a padded plaintext没有加密过的文件 message m, the encryption function is
- 用公钥对m进行加密

The private key is (d = 2753). For an encrypted ciphertext密文 c, the decryption function is
- 用私钥对c进行解密
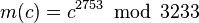
For instance, in order to encrypt m = 65, we calculate
 对65进行加密,65^17%3233=
对65进行加密,65^17%3233=
To decrypt c = 2790, we calculate
 对2790进行解密,2790^2753%3233
对2790进行解密,2790^2753%3233
Both of these calculations can be computed efficiently using the square-and-multiply algorithm for modular exponentiation.
In real-life situations the primes selected would be much larger;
in our example it would be trivial to factor n, 3233 (obtained from the freely available public key) back to the primes p and q.
Given e, also from the public key, we could then compute d and so acquire the private key.
Practical implementations use the Chinese remainder theorem to speed up the calculation using modulus of factors (mod pq using mod p and mod q).
The values dp, dq and qinv, which are part of the private key are computed as follows:
Here is how dp, dq and qinv are used for efficient decryption. (Encryption is efficient by choice of a suitable d and e pair)
RSA Public Key: (N, 7) 公钥的两个参数应该是(m,e)
N = 233 * M //p=233 q=9001 232*9000=2088000
RSA的公钥 (2097233,7) Modulus=2097233 Exponent=7
a密文是197372,对其解密
b密文是333079,对其解密
d*e%((233-1)(9001-1))
=d*7%2088000=1
for(int i = ; i <= ; i++)
{
if(i*% == )
{
Console.WriteLine(i);
break;
}
}
打印结果:1193143,所以d=1193143
a密文是197372,对其解密 a=197372^1193143mod2097233
b密文是333079,对其解密 b=333079^1193143mod2097233
https://www.cs.drexel.edu/~jpopyack/IntroCS/HW/RSAWorksheet.html
https://www.cs.drexel.edu/~introcs/Fa11/notes/10.1_Cryptography/RSA_Express_EncryptDecrypt.html
http://extranet.cryptomathic.com/rsacalc/index
BigInteger number = ;
int exponent = ;
BigInteger modulus = ;
Console.WriteLine("({0}^{1}) Mod {2} = {3}",
number, exponent, modulus,
BigInteger.ModPow(number, exponent, modulus));
a=378
b=390696
RSA (cryptosystem)的更多相关文章
- RSA算法原理——(2)RSA简介及基础数论知识
上期为大家介绍了目前常见加密算法,相信阅读过的同学们对目前的加密算法也算是有了一个大概的了解.如果你对这些解密算法概念及特点还不是很清晰的话,昌昌非常推荐大家可以看看HTTPS的加密通信原理,因为HT ...
- 全面解决.Net与Java互通时的RSA加解密问题,使用PEM格式的密钥文件
作者: zyl910 一.缘由 RSA是一种常用的非对称加密算法.所以有时需要在不用编程语言中分别使用RSA的加密.解密.例如用Java做后台服务端,用C#开发桌面的客户端软件时. 由于 .Net.J ...
- 模反元素 RSA Euler's totient function
https://baike.baidu.com/item/模反元素/20417595 如果两个正整数a和n互质,那么一定可以找到整数b,使得 ab-1 被n整除,或者说ab被n除的余数是1.这时,b就 ...
- RSA算法原理与加密解密 求私钥等价求求模反元素 等价于分解出2个质数 (r*X+1)%[(p-1)(q-1)]=0
Rsapaper.pdf http://people.csail.mit.edu/rivest/Rsapaper.pdf [概述Abstract 1.将字符串按照双方约定的规则转化为小于n的正整数m, ...
- RSA遇上中国剩余定理
1.Introduction 最近读论文刚好用到了这个,之前只是有耳闻,没有仔细研究过,这里就好好捋一下,会逐步完善 不过貌似CRT(中国剩余定理)的实现更容易被攻击 2. RSA: Overview ...
- [转载] TLS协议分析 与 现代加密通信协议设计
https://blog.helong.info/blog/2015/09/06/tls-protocol-analysis-and-crypto-protocol-design/?from=time ...
- emSecure Use Digital Signatures to protect your products
emSecure Use Digital Signatures to protect your products emSecure is an RSA based software solution ...
- TLS协议分析
TLS协议分析 本文目标: 学习鉴赏TLS协议的设计,透彻理解原理和重点细节 跟进一下密码学应用领域的历史和进展 整理现代加密通信协议设计的一般思路 本文有门槛,读者需要对现代密码学有清晰而系统的理解 ...
- Factorization
Factorization or factoring consists of writing a number or another mathematical object as a product ...
随机推荐
- 【BZOJ】【1045/1465】【HAOI2008】糖果传递
思路题/神奇的转化…… orz hzwer 或许这个思路可以从单行而非环形的递推中找到?(单行的时候,从左往右直接递推即可…… 感觉好神奇>_<脑残患者想不出…… P.S.话说在$n\le ...
- 服务器NPC的ID如何分配的
服务器ID分配包括NPC,Monster,Pet的ID分配都是调用allocateUID然后自动保存的ID加一,pet说是通过玩家的ID移位获得的,调试一下发现还是调用allocateUID,如果通过 ...
- [原] blade中C++ singleton的实现
最近看了龚大大KalyGE中的singleton, 觉得非常不错(C++中线程安全并且高效的singleton). 可惜blade的代码都是C++03的, 没有使用C++11的任何特性. 笔者对于si ...
- 帝国cms数据还原后提示数据库表不存在怎么解决?
下午,ytkah用帝国cms在wamp调试时发现了一个问题,还原备份好的数据后更新的页面提示数据库表不存在,查看了phpmyadmin分类的数据库表实际上是存在的,这个是怎么回事呢?重新搭建一个新站点 ...
- codeforces 459C Pashmak and Buses(模拟,组合数A)
题目 跑个案例看看结果就知道了:8 2 3 题目给的数据是 n,k,d 相当于高中数学题:k个人中选择d个人排成一列,有多少种不同的方案数,列出其中n中就可以了. #include<iostre ...
- PYTHON发送邮件时,有的服务器不用密码认证的
#!/usr/bin/python # coding: UTF-8 import smtplib from email.mime.text import MIMEText receivers_list ...
- WCF传输Dataset大数据量 -压缩
由于WCF不能传输DataTable(不能序列化),所以更多项目中都会使用DataSet作为查询集合的首选返回类型,但是由于DataSet会生成很多的状态信息等,所以DataSet体积也会变大,有几种 ...
- js:字符串(string)转json
第一种方式: 使用js函数eval(); testJson=eval(testJson);是错误的转换方式. 正确的转换方式需要加(): testJson = eval("(" + ...
- Codeforces Round #337 (Div. 2) C. Harmony Analysis 数学
C. Harmony Analysis The semester is already ending, so Danil made an effort and decided to visit a ...
- jmeter 异步子请求测试随笔
好久没写技术类的博客了,都不知道自己都在忙啥.... 最近陆续遇到了一些异步子请求的测试需求,比如打开某一个页面A,A页面里的js会再调用B,C,D,E等请求,针对这个页面的测试,我最近做了一些思考: ...