[hdoj5927][dfs]
http://acm.hdu.edu.cn/showproblem.php?pid=5927
Auxiliary Set
Time Limit: 9000/4500 MS (Java/Others) Memory Limit: 65536/65536 K (Java/Others)
Total Submission(s): 2991 Accepted Submission(s): 851
An auxiliary set is a set containing vertices satisfying at least one of the two conditions:
∙It is an important vertex
∙It is the least common ancestor of two different important vertices.
You are given a tree with n vertices (1 is the root) and q queries.
Each query is a set of nodes which indicates the unimportant vertices in the tree. Answer the size (i.e. number of vertices) of the auxiliary set for each query.
For each test case, the first line contains two integers n (1≤n≤100000), q (0≤q≤100000).
In the following n -1 lines, the i-th line contains two integers ui,vi(1≤ui,vi≤n) indicating there is an edge between uii and vi in the tree.
In the next q lines, the i-th line first comes with an integer mi(1≤mi≤100000) indicating the number of vertices in the query set.Then comes with mi different integers, indicating the nodes in the query set.
It is guaranteed that ∑qi=1mi≤100000.
It is also guaranteed that the number of test cases in which n≥1000 or ∑qi=1mi≥1000 is no more than 10.
Then q lines follow, i-th line contains an integer indicating the size of the auxiliary set for each query.
6 3
6 4
2 5
5 4
1 5
5 3
3 1 2 3
1 5
3 3 1 4
3
6
3
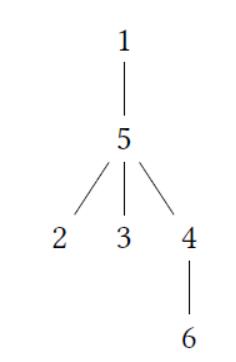
For the query {1,2, 3}:
•node 4, 5, 6 are important nodes For the query {5}:
•node 1,2, 3, 4, 6 are important nodes
•node 5 is the lea of node 4 and node 3 For the query {3, 1,4}:
• node 2, 5, 6 are important nodes
题意:给一棵树,给一堆定义,有q次查询
题解:dfs先跑出各个顶点的深度和父节点,然后给q次询问按照深度排序,最后在q次询问中更新当前顶点对父节点的影响。
#include<bits/stdc++.h>
using namespace std;
typedef long long ll;
#define debug(x) cout<<"["<<#x<<"]"<<" "<<x<<endl;
const int maxn=1e5+;
int head[maxn],cnt,fa[maxn],www[maxn],wwww[maxn],dep[maxn];
struct edge{
int to;
int nex;
int fr;
}e[maxn<<];
struct pot{
int depth;
int id;
}p[maxn];
void adde(int u,int v){
e[cnt].fr=u;
e[cnt].to=v;
e[cnt].nex=head[u];
head[u]=cnt++;
}
void dfs(int u,int f){
fa[u]=f;
dep[u]=dep[f]+;
wwww[u]=;
for(int i=head[u];i!=-;i=e[i].nex){
int v=e[i].to;
if(v==f)continue;
dfs(v,u);
wwww[u]++;
}
}
bool cmp(struct pot aa,struct pot bb){
return aa.depth>bb.depth;
}
int main()
{
int t;
scanf("%d",&t);
int ca=;
while(t--){
int n,q;
scanf("%d%d",&n,&q);
cnt=;
for(int i=;i<=n;i++){
head[i]=-;
wwww[i]=;
}
for(int i=;i<n;i++){
int x,y;
scanf("%d%d",&x,&y);
adde(x,y);
adde(y,x);
}
dfs(,);
printf("Case #%d:\n",ca++);
for(int i=;i<=q;i++){
int w;
scanf("%d",&w);
for(int j=;j<=w;j++){
scanf("%d",&p[j].id);
p[j].depth=dep[p[j].id];
}
int ans=n;
sort(p+,p++w,cmp);
for(int j=;j<=w;j++){
int v=p[j].id;
www[v]++;
if(wwww[v]==www[v]){
www[fa[v]]++;
}
if(wwww[v]-www[v]<){ans--;}
}
for(int j=;j<=w;j++){
int v=p[j].id;
www[v]=;
www[fa[v]]=;
}
printf("%d\n",ans);
}
}
return ;
}
[hdoj5927][dfs]的更多相关文章
- BZOJ 3083: 遥远的国度 [树链剖分 DFS序 LCA]
3083: 遥远的国度 Time Limit: 10 Sec Memory Limit: 1280 MBSubmit: 3127 Solved: 795[Submit][Status][Discu ...
- BZOJ 1103: [POI2007]大都市meg [DFS序 树状数组]
1103: [POI2007]大都市meg Time Limit: 10 Sec Memory Limit: 162 MBSubmit: 2221 Solved: 1179[Submit][Sta ...
- BZOJ 4196: [Noi2015]软件包管理器 [树链剖分 DFS序]
4196: [Noi2015]软件包管理器 Time Limit: 10 Sec Memory Limit: 512 MBSubmit: 1352 Solved: 780[Submit][Stat ...
- 图的遍历(搜索)算法(深度优先算法DFS和广度优先算法BFS)
图的遍历的定义: 从图的某个顶点出发访问遍图中所有顶点,且每个顶点仅被访问一次.(连通图与非连通图) 深度优先遍历(DFS): 1.访问指定的起始顶点: 2.若当前访问的顶点的邻接顶点有未被访问的,则 ...
- BZOJ 2434: [Noi2011]阿狸的打字机 [AC自动机 Fail树 树状数组 DFS序]
2434: [Noi2011]阿狸的打字机 Time Limit: 10 Sec Memory Limit: 256 MBSubmit: 2545 Solved: 1419[Submit][Sta ...
- POJ_2386 Lake Counting (dfs 错了一个负号找了一上午)
来之不易的2017第一发ac http://poj.org/problem?id=2386 Lake Counting Time Limit: 1000MS Memory Limit: 65536 ...
- 深度优先搜索(DFS)
[算法入门] 郭志伟@SYSU:raphealguo(at)qq.com 2012/05/12 1.前言 深度优先搜索(缩写DFS)有点类似广度优先搜索,也是对一个连通图进行遍历的算法.它的思想是从一 ...
- 【BZOJ-3779】重组病毒 LinkCutTree + 线段树 + DFS序
3779: 重组病毒 Time Limit: 20 Sec Memory Limit: 512 MBSubmit: 224 Solved: 95[Submit][Status][Discuss] ...
- 【BZOJ-1146】网络管理Network DFS序 + 带修主席树
1146: [CTSC2008]网络管理Network Time Limit: 50 Sec Memory Limit: 162 MBSubmit: 3495 Solved: 1032[Submi ...
随机推荐
- HTTP_HOST , SERVER_NAME 区别
当端口是80的时候,他们的内容是一样的. 但是当端口不是80的时候,就不一样了. # HTTP_HOST = SERVER_NAME:SERVER_PORT /** * 获取当前的host */ pu ...
- [WCF] - Odata Service 访问失败,查看具体错误信息的方法
Issue 解决 为 Data Service 配置属性如下:[System.ServiceModel.ServiceBehavior(IncludeExceptionDetailInFaults = ...
- JSP的部分知识(一)
通过Servlet进行整个网站的开发是可以的. 不过在Servlet中输出html代码,特别是稍微复杂一点的html代码,就会给人一种很酸爽的感觉. 如果能够直接使用Html代码,然后在html中写j ...
- 别再裸奔了,你的项目代码安全吗,再不加密就out了
在工作中,有时候我们需要部署自己的Python代码 或进行私有化部署时,尤其现在都是通过docker镜像部署,我们并不希望别人能够看到自己的Python源程序. 加密Python源代码的方式,是将.p ...
- EAFP vs LBYL
EAFP vs LBYL 检查数据可以让程序更健壮,用术语来说就是防御性编程.检查数据的时候,有EAFP和LBYL两种不同的编程风格,具体的意思如下: LBYL: Look Before You Le ...
- golang之匿名函数结合defer
defer语句中的函数会在return语句更新返回值变量后再执行,又因为在函数中定义的匿名函数可以访问该函数包括返回值变量在内的所有变量,所以,对匿名函数采用defer机制,可以使其观察函数的返回值. ...
- 嵌入式Linux学习笔记之第二阶段---文件I/O
1.文件IO的四个函数 一些术语: 不带缓冲的I/O: 每个read和write都调用内核中的一个系统调用. 文件描述符: 一个非负整数,对内核而言,所以打开的文件都通过文件描述符引用. ①打开或创建 ...
- PowerBuilder学习笔记之删除和加载PBL文件的方法
删除PBL目录的方法:直接点删除键删除 加载PBL文件的方法:点Browse按钮选择PBL文件
- ASP.Net Core 返回的json数据,自定义日期格式
//代码位置:Startup.cs public void ConfigureServices(IServiceCollection services) { services.AddMvc() .Ad ...
- es6☞对象的解构赋值
变量必须与属性同名 let {name, age} = {name: 'wang', age: 22}; console.log(name, age); //wang 22 let {name} = ...
