poj2635The Embarrassed Cryptographer(同余膜定理)
| Time Limit: 2000MS | Memory Limit: 65536K | |
| Total Submissions: 15069 | Accepted: 4132 |
Description
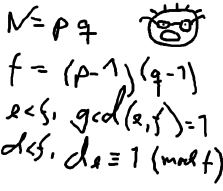 The young and very promising cryptographer Odd Even has implemented the security module of a large system with thousands of users, which is now in use in his company. The cryptographic keys are created from the product of two primes, and are believed to be secure because there is no known method for factoring such a product effectively.
The young and very promising cryptographer Odd Even has implemented the security module of a large system with thousands of users, which is now in use in his company. The cryptographic keys are created from the product of two primes, and are believed to be secure because there is no known method for factoring such a product effectively. What Odd Even did not think of, was that both factors in a key
should be large, not just their product. It is now possible that some of
the users of the system have weak keys. In a desperate attempt not to
be fired, Odd Even secretly goes through all the users keys, to check if
they are strong enough. He uses his very poweful Atari, and is
especially careful when checking his boss' key.
Input
K is the key itself, a product of two primes. L is the wanted minimum
size of the factors in the key. The input set is terminated by a case
where K = 0 and L = 0.
Output
each number K, if one of its factors are strictly less than the
required L, your program should output "BAD p", where p is the smallest
factor in K. Otherwise, it should output "GOOD". Cases should be
separated by a line-break.
Sample Input
143 10
143 20
667 20
667 30
2573 30
2573 40
0 0
Sample Output
GOOD
BAD 11
GOOD
BAD 23
GOOD
BAD 31
/*
* @Author: lyucheng
* @Date: 2017-10-17 19:03:06
* @Last Modified by: lyucheng
* @Last Modified time: 2017-10-17 16:50:37
*/
#include <stdio.h>
#include <vector>
#include <string.h> #define MAXN 105
#define MAXM 1000005 using namespace std; char str[MAXN];
int k;
int p[MAXM];
bool prime[MAXM];
int tol;
int num[MAXM];
vector<int>v; void init(){
tol=;
for(int i=;i<MAXM;i++){
if(prime[i]==false)
p[tol++]=i;
for(int j=;j<tol&&i*p[j]<MAXM;j++){
prime[i*p[j]]=true;
if(i%p[j]==)
break;
}
}
} bool ok(int k){
int s=;
for(int i=(int)v.size()-;i>=;i--){
s*=;
s%=k;
s+=v[i];
s%=k;
}
if(s==)
return true;
else
return false;
} int main(){
// freopen("in.txt","r",stdin);
init();
while(scanf("%s%d",str,&k)!=EOF&&(str[]-''!=&&k!=)){
int n=strlen(str);
v.clear();
for(int i=n-;i>=;i-=){
int s=;
for(int j=max(,i-);j<=i;j++){
s*=;
s+=str[j]-'';
}
v.push_back(s);
}
// for(int i=0;i<(int)v.size();i++){
// cout<<v[i]<<" ";
// }cout<<endl;
bool flag=true;
for(int i=;p[i]<k;i++){
if(ok(p[i])==true){
printf("BAD %d\n",p[i]);
flag=false;
break;
}
}
if(flag==true)
puts("GOOD");
}
return ;
}
poj2635The Embarrassed Cryptographer(同余膜定理)的更多相关文章
- POJ2635The Embarrassed Cryptographer(大数取余+素数筛选+好题)
题目链接 题意:K是由两个素数乘积,如果最小的素数小于L,输出BAD最小的素数,否则输出GOOD 分析 素数打表将 L 大点的素数打出来,一定要比L大,然后就开始枚举,只需K对 素数 取余 看看是否为 ...
- POJ2635-The Embarrassed Cryptographer 大数求余
题目链接:http://poj.org/problem?id=2635 题目分析: http://blog.csdn.net/lyy289065406/article/details/6648530
- POJ 2635 The Embarrassed Cryptographer(大数求余)
题意:给出一个大数,这个大数由两个素数相乘得到,让我们判断是否其中一个素数比L要小,如果两个都小,输出较小的那个. 分析:大数求余的方法:针对题目中的样例,143 11,我们可以这样算,1 % 11 ...
- [ACM] POJ 2635 The Embarrassed Cryptographer (同余定理,素数打表)
The Embarrassed Cryptographer Time Limit: 2000MS Memory Limit: 65536K Total Submissions: 11978 A ...
- POJ 2635 The Embarrassed Cryptographer (千进制,素数筛,同余定理)
The Embarrassed Cryptographer Time Limit: 2000MS Memory Limit: 65536K Total Submissions: 15767 A ...
- POJ2635——The Embarrassed Cryptographer(高精度取模+筛选取素数)
The Embarrassed Cryptographer DescriptionThe young and very promising cryptographer Odd Even has imp ...
- POJ 2635 The Embarrassed Cryptographer
大数取MOD... The Embarrassed Cryptographer Time Limit: 2000MS Memory Limit: 65536K Total Submissions: 1 ...
- (POJ2635)The Embarrassed Cryptographer(大数取模)
The Embarrassed Cryptographer Time Limit: 2000MS Memory Limit: 65536K Total Submissions: 13041 Accep ...
- 推荐系列:最小与最大[DP+余式定理]
最小与最大 [问题描述] 做过了乘积最大这道题,相信这道题也难不倒你. 已知一个数串,可以在适当的位置加入乘号(设加了k个,当然也可不加,即分成k+1个部分),设这k+1个部分的乘积(如果k=0,则乘 ...
随机推荐
- (转)添加PROPAGATION_REQUIRES_NEW 事务没有产生作用
最近在做事务添加时 发现自己的事务没有新建,上网查到 仅用作收藏. 其二 注意 事务的注解 应该在 内层的事务上面 一.描述 Spring遇到嵌套事务时,当被嵌套的事务被定义为" ...
- 《Node.js在CLI下的工程化体系实践》成都OSC源创汇分享总结
背景: 随着开发团队规模不断发展壮大,在人员增加的同时也带来了协作成本的增加,业务项目越来越多,类型也各不相同.常见的类型有组件类.活动类.基于React+redux的业务项目.RN项目.Node.j ...
- oracle存储过程中is和as区别
在存储过程(PROCEDURE)和函数(FUNCTION)中没有区别:在视图(VIEW)中只能用AS不能用IS:在游标(CURSOR)中只能用IS不能用AS.
- Web 开发模式演变历史和趋势
前不久徐飞写了一篇很好的文章:Web 应用的组件化开发.本文尝试从历史发展角度,说说各种研发模式的优劣. 一.简单明快的早期时代 可称之为 Web 1.0 时代,非常适合创业型小项目,不分前后端,经常 ...
- MyCAT-EYE开源
MyCAT EYE MySQL数据库监控工具,实现了对MySQL节点的管理和监控,可供开发人员和DBA使用.后续版本将整合MyCAT2.0的管理和配置. 演示地址: 开发人员视图:http://120 ...
- Relocation 状态压缩DP
Relocation Time Limit:1000MS Memory Limit:65536KB 64bit IO Format:%I64d & %I64u Submit ...
- http://codeforces.com/contest/834
A. The Useless Toy time limit per test 1 second memory limit per test 256 megabytes input standard i ...
- 像 npm 一样在 Andriod 项目中引入 Gradle 依赖
一.前言 作为 Android 开发人员,有没有羡慕过 node.js 的导入三方库的方式,node.js 社区为开发者准备了一个快速可靠的依赖管理库.这样的依赖管理库,让 node.js 导入依赖库 ...
- 小白学Maven第一篇配置
在百度上搜Maven进入官网,然后在进Download里面把apache-maven-3.5.0-bin.zip(记得不要下错)下载下来 然后进行安装 (前提你配置了Java如下图) Java配置: ...
- MySQL(十五)之数据备份中mysqldump详解
前言 其实前面一篇数据备份已经是非常的详细了,这里我想单独的讲解一下mysqldump,相信很多程序员都是用过这个命令的! 一.MySQL数据库的备份与还原 1.1.MySQL数据库备份 1)语法 m ...
