Setting up IPS/inline for Linux in Suricata
不多说,直接上干货!
见官网
https://suricata.readthedocs.io/en/latest/setting-up-ipsinline-for-linux.html
- Docs »
- 11. Setting up IPS/inline for Linux
- Edit on GitHub
11. Setting up IPS/inline for Linux
In this guide will be explained how to work with Suricata in layer3 inline mode and how to set iptables for that purpose.
First start with compiling Suricata with NFQ support. For instructions see Ubuntu Installation. For more information about NFQ and iptables, see NFQ.
To check if you have NFQ enabled in your Suricata, enter the following command:
suricata --build-info
and examine if you have NFQ between the features.
To run suricata with the NFQ mode, you have to make use of the -q option. This option tells Suricata which of the queue numbers it should use.
sudo suricata -c /etc/suricata/suricata.yaml -q 0
11.1. Iptables configuration
First of all it is important to know which traffic you would like to send to Suricata. Traffic that passes your computer or traffic that is generated by your computer.
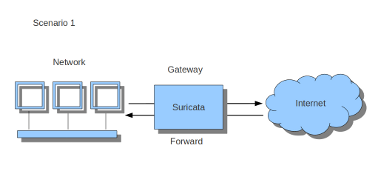
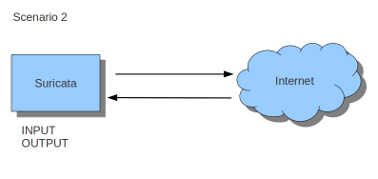
If Suricata is running on a gateway and is meant to protect the computers behind that gateway you are dealing with the first scenario: forward_ing . If Suricata has to protect the computer it is running on, you are dealing with the second scenario: host (see drawing 2). These two ways of using Suricata can also be combined.
The easiest rule in case of the gateway-scenario to send traffic to Suricata is:
sudo iptables -I FORWARD -j NFQUEUE
In this case, all forwarded traffic goes to Suricata.
In case of the host situation, these are the two most simple iptable rules;
sudo iptables -I INPUT -j NFQUEUE
sudo iptables -I OUTPUT -j NFQUEUE
It is possible to set a queue number. If you do not, the queue number will be 0 by default.
Imagine you want Suricata to check for example just TCP-traffic, or all incoming traffic on port 80, or all traffic on destination-port 80, you can do so like this:
sudo iptables -I INPUT -p tcp -j NFQUEUE
sudo iptables -I OUTPUT -p tcp -j NFQUEUE
In this case, Suricata checks just TCP traffic.
sudo iptables -I INPUT -p tcp --sport 80 -j NFQUEUE
sudo iptables -I OUTPUT -p tcp --dport 80 -j NFQUEUE
In this example, Suricata checks all input and output on port 80.
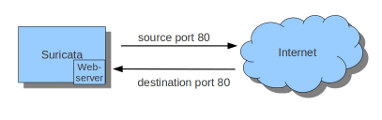
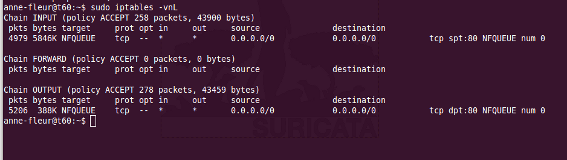
To see if you have set your iptables rules correct make sure Suricata is running and enter:
sudo iptables -vnL
In the example you can see if packets are being logged.
This description of the use of iptables is the way to use it with IPv4. To use it with IPv6 all previous mentioned commands have to start with ‘ip6tables’. It is also possible to let Suricata check both kinds of traffic.
There is also a way to use iptables with multiple networks (and interface cards). Example:
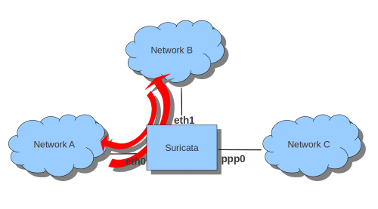
sudo iptables -I FORWARD -i eth0 -o eth1 -j NFQUEUE
sudo iptables -I FORWARD -i eth1 -o eth0 -j NFQUEUE
The options -i (input) -o (output) can be combined with all previous mentioned options
If you would stop Suricata and use internet, the traffic will not come through. To make internet work correctly, you have to erase all iptable rules.
To erase all iptable rules, enter:
sudo iptables -F
Setting up IPS/inline for Linux in Suricata的更多相关文章
- The Guideline of Setting Up Samba Server on linux(Ubuntu)
The Guideline of Setting Up Samba Server on linux(Ubuntu) From terminate command window, install the ...
- Suricata, to 10Gbps and beyond(X86架构)
Introduction Since the beginning of July 2012, OISF team is able to access to a server where one int ...
- Kali linux 2016.2(Rolling)中的payloads模块详解
不多说,直接上干货! 前期博客 Kali linux 2016.2(Rolling)中的Exploits模块详解 payloads模块,也就是shellcode,就是在漏洞利用成功后所要做的事情.在M ...
- Linux 驱动开发
linux驱动开发总结(一) 基础性总结 1, linux驱动一般分为3大类: * 字符设备 * 块设备 * 网络设备 2, 开发环境构建: * 交叉工具链构建 * NFS和tftp服务器安装 3, ...
- 使用.NetCore在Linux上写TCP listen 重启后无法绑定地址
拥抱.net core的过程中, 将公司的一套java项目改成了.net core 2.0版的. 里面的tcp服务被我用msdn的SocketAsyncEventArgs方式重写了, 然而在测试的过程 ...
- linux记录-docker配置mysql
docker部署mysql 1.拉取镜像 docker pull mysql 2.docker rm containerID 删除镜像iD 3.创建镜像 docker run --name=m ...
- linux从head.s到start_kernelstart_kernel之---内核重定位后分析
参考: https://biscuitos.github.io/blog/ARM-BOOT/ zImage 重定位之后实践 zImage 重定位之后,ARM 将 pc 指针指向了重定位 zImage ...
- Linux设备驱动中的阻塞和非阻塞I/O <转载>
Green 博客园 首页 新随笔 联系 订阅 管理 Linux设备驱动中的阻塞和非阻塞I/O [基本概念] 1.阻塞 阻塞操作是指在执行设备操作时,托不能获得资源,则挂起进程直到满足操作所需的条件 ...
- pytbull 手册
- Official documentation for pytbull v2.1 - Table of content Description Architecture Remote mode Lo ...
随机推荐
- 开启 J2EE(六)— Servlet之Filter具体解释及乱码处理实例
版权声明:本文为博主原创文章,未经博主同意不得转载. https://blog.csdn.net/akkzhjj/article/details/36471477 定义和功能 Filter:过滤器,它 ...
- Netty实现时间服务演示样例
相关知识点: [1] ChannelGroup是一个容纳打开的通道实例的线程安全的集合,方便我们统一施加操作.所以在使用的过程中能够将一些相关的Channel归类为一个有意义的集合.关闭的通道会自己主 ...
- Delphi语言最好的JSON代码库 mORMot学习笔记1(无数评论)
mORMot没有控件安装,直接添加到lib路径,工程中直接添加syncommons,syndb等到uses里 --------------------------------------------- ...
- eclipse、idea切换大小写的快捷键
idea : ctrl+shift+U切换大小写 eclipse : ctrl+shift+X 切换成大写 ctrl+shift+Y 切换成小写
- POJ1228:Grandpa's Estate(给定一些点,问是否可以确定一个凸包)
Being the only living descendant of his grandfather, Kamran the Believer inherited all of the grandp ...
- NOIP2007普及 守望者的逃离
传送门 普及组的题目……很水. 原来写了一个模拟不过好像状态考虑的不全得了80,这次我们考虑一下dp做法. 守卫者有两种移动的方法,一种是闪现,一种是跑,我们可以把闪现和跑分开处理. 首先只处理闪现的 ...
- bzoj1783
博弈论+dp 从未做过博弈论... 思路是这样的,我们倒着考虑,分别设f[i]表示先手选了a[i]后能取得的最大值,g[i]表示先手取了a[i]后后手能获得的最大值 g[i]=f[mx],f[mx]是 ...
- 【旧文章搬运】分析了一下360安全卫士的HOOK(二)——架构与实现
原文发表于百度空间及看雪论坛,2009-10-14 看雪论坛地址:https://bbs.pediy.com/thread-99460.htm 刚发这篇文章的时候,因为内容涉及360的核心产品,文章被 ...
- 039--CSS
一.CSS定义 CSS 规则由两个主要的部分构成:选择器,以及一条或多条声明. ''' selector { property: value; property: value; ... propert ...
- ASP.NET Core MVC 2.x 全面教程_ASP.NET Core MVC 21. Model 验证 Again
深入的将Model验证 手动添加验证的错误 view里面显示每个属性的验证错误信息 显示整个model级别错误 自定义验证 如果业务逻辑需要比较复杂的验证.而且这个验证逻辑可能到处复用的话就应该考虑使 ...
