华为设备acl配置
拓扑图:
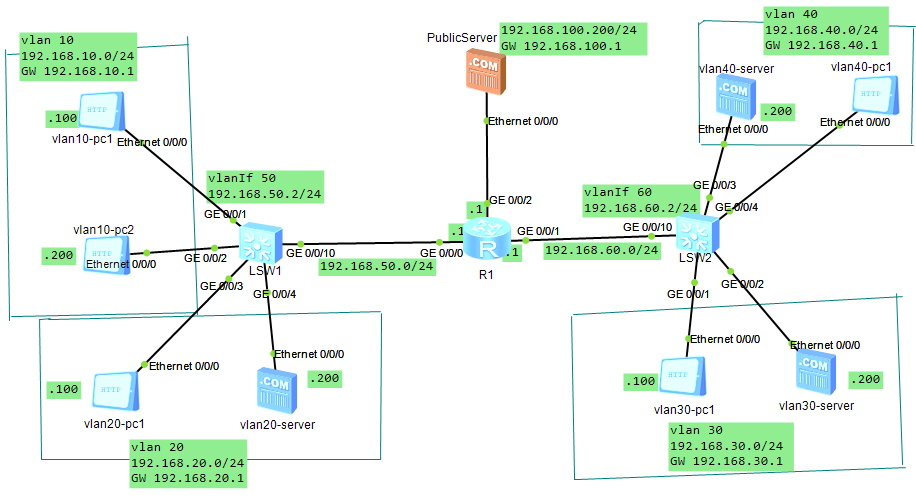
需求:
1、-vlan10内所有的主机,只能通过http访问vlan30-server的服务器;不能访问vlan40-server服务器
2、-vlan20-pc1主机,可以访问vlan40-server服务器,不能访问vlan30-server服务器
3、-vlan30-pc1主机,不能访问vlan20-server服务器,可以访问vlan40-server服务器
4、-PublicServer服务器对vlan10和vlan20 仅仅提供ftp服务
5、-PublicServer服务器对vlan30-server和vlan40-server仅仅提供http服务
6、-PublicServer服务器对所有pc提供dns服务
7、-所有节点和主机均能够ping通
配置:
三层交换机SW1-left
sw-left:
[sw1]sys sw-left
[sw-left]vlan batch 10 20 50
[sw-left]port-group group-member g0/0/1 g0/0/2
[sw-left-port-group]port link-type access
[sw-left-GigabitEthernet0/0/1]port link-type access
[sw-left-GigabitEthernet0/0/2]port link-type access
[sw-left-port-group]port default vlan 10
[sw-left-GigabitEthernet0/0/1]port default vlan 10
[sw-left-GigabitEthernet0/0/2]port default vlan 10
[sw-left-port-group]q
[sw-left]port-group group-member g0/0/3 g0/0/4
[sw-left-port-group]port link-type access
[sw-left-GigabitEthernet0/0/3]port link-type access
[sw-left-GigabitEthernet0/0/4]port link-type access
[sw-left-port-group]port default vlan 20
[sw-left-GigabitEthernet0/0/3]port default vlan 20
[sw-left-GigabitEthernet0/0/4]port default vlan 20
[sw-left-port-group]q
[sw-left]int g0/0/10
[sw-left-GigabitEthernet0/0/10]port link-type access
[sw-left-GigabitEthernet0/0/10]port default vlan 50
[sw-left-GigabitEthernet0/0/10]q
[sw-left]int vlanif 10
[sw-left-Vlanif10]ip add 192.168.10.1 24
[sw-left-Vlanif10]int vlanif 20
[sw-left-Vlanif20]ip add 192.168.20.1 24
[sw-left-Vlanif20]int vlanif 50
[sw-left-Vlanif50]ip add 192.168.50.2 24
[sw-left-Vlanif50]q
[sw-left]rip
[sw-left-rip-1]version 2
[sw-left-rip-1]undo summary
[sw-left-rip-1]network 192.168.10.0
[sw-left-rip-1]network 192.168.20.0
[sw-left-rip-1]network 192.168.50.0
[sw-left-rip-1]
路由器: R1
<Huawei>sys
[Huawei]sys R1
[R1]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 192.168.60.1 24
[R1-GigabitEthernet0/0/1]int g0/0/2
[R1-GigabitEthernet0/0/2]ip add 192.168.100.1 24
[R1-GigabitEthernet0/0/2]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 192.168.50.1 24
[R1-GigabitEthernet0/0/0]q
[R1]rip
[R1-rip-1]version 2
[R1-rip-1]undo summary
[R1-rip-1]network 192.168.50.0
[R1-rip-1]network 192.168.60.0
[R1-rip-1]network 192.168.100.0
[R1-rip-1]
交换机: SW2-right
<Huawei>sys
[Huawei]sys sw-right
[sw-right]vlan batch 30 40 60
[sw-right]port-group group-member g0/0/1 g0/0/2
[sw-right-port-group]port link-type access
[sw-right-GigabitEthernet0/0/1]port link-type access
[sw-right-GigabitEthernet0/0/2]port link-type access
[sw-right-GigabitEthernet0/0/1]port default vlan 30
[sw-right-GigabitEthernet0/0/2]port default vlan 30
[sw-right-port-group]q
[sw-right]port-group group-member g0/0/3 g0/0/4
[sw-right-port-group]port link-type access
[sw-right-GigabitEthernet0/0/3]port link-type access
[sw-right-GigabitEthernet0/0/4]port link-type access
[sw-right-port-group]port default vlan 40
[sw-right-GigabitEthernet0/0/3]port default vlan 40
[sw-right-GigabitEthernet0/0/4]port default vlan 40
[sw-right-port-group]q
[sw-right]int g0/0/10
[sw-right-GigabitEthernet0/0/10]port link-type access
[sw-right-GigabitEthernet0/0/10]port default vlan 60
[sw-right-GigabitEthernet0/0/10]q
[sw-right]int vlanif 30
[sw-right-Vlanif30]ip add 192.168.30.1 24
[sw-right-Vlanif30]int vlanif 40
[sw-right-Vlanif40]ip add 192.168.40.1 24
[sw-right-Vlanif40]int vlanif 60
[sw-right-Vlanif60]ip add 192.168.60.2 24
[sw-right-Vlanif60]q
[sw-right]rip
[sw-right-rip-1]version 2
[sw-right-rip-1]undo summary
[sw-right-rip-1]network 192.168.30.0
[sw-right-rip-1]network 192.168.40.0
[sw-right-rip-1]network 192.168.60.0
[sw-right-rip-1]
测试所有终端设备全部ping通后继续ing...
分析规则:
1、-vlan10内所有的主机,只能通过http访问vlan30-server的服务器;不能访问vlan40-server服务器
192.168.10.0 0.0.0.255 网段要带掩码, 192.168.30.200 0 ip 掩码可简写为 0
rule permit tcp source 192.168.10.0 0.0.0.255 destination 192.168.30.200 0 destination-port eq 80
rule deny ip source 192.168.10.0 0.0.0.255 destination 192.168.40.200 0.0.0.0
返回规则
rule permit ip source 192.168.30.200 0 destination 192.168.10.0 0.0.0.255
2、-vlan20-pc1主机,可以访问vlan40-server服务器,不能访问vlan30-server服务器
rule permit ip source 192.168.20.100 0 destination 192.168.40.200 0
rule deny ip source 192.168.20.100 0 destination 192.168.30.200 0
返回规则
rule permit ip source 192.168.40.200 0 destination 192.168.20.100 0
3、-vlan30-pc1主机,不能访问vlan20-server服务器,可以访问vlan40-server服务器
rule deny ip source 192.168.30.100 0 destination 192.168.20.200 0
vlan30 和vlan40 不跨路由器规则 无需设置规则
返回规则
无
4、-PublicServer服务器对vlan10和vlan20 仅仅提供ftp服务
rule permit tcp source 192.168.10.0 0.0.0.255 destination 192.168.100.200 0 destination-port eq 21
rule permit tcp source 192.168.20.0 0.0.0.255 destination 192.168.100.200 0 destination-port eq 21
返回规则
rule permit ip source 192.168.100.200 0 destination 192.168.10.0 0.0.0.255
rule permit ip source 192.168.100.200 0 destination 192.168.20.0 0.0.0.255
5、-PublicServer服务器对vlan30和vlan40-server仅仅提供http服务
rule permit tcp source 192.168.30.0 0.0.0.255 destination 192.168.100.200 0 destination-port eq 80
rule permit tcp source 192.168.40.200 0 destination 192.168.100.200 0 destination-port eq 80
返回规则
rule permit ip source 192.168.100.200 0 destination 192.168.30.0 0.0.0.255
rule permit ip source 192.168.100.200 0 destination 192.168.40.0 0.0.0.255
6、-PublicServer服务器对所有pc提供dns服务
rule permit udp source any destination 192.168.100.200 0 destination-port eq 53
返回规则
rule permit ip source 192.168.100.200 0 destination any
7、-所有节点和主机均能够ping通
rule permit icmp source any destination any
以上规则在三个路由接口的outbound(出站)总结为:
int g0/0/1: acl3000
即是:vlan10,vlan20及PublicServer服务器,在int g0/0/1的outbound规则
rule permit tcp source 192.168.10.0 0.0.0.255 destination 192.168.30.200 0 destination-port eq 80
rule permit ip source 192.168.20.100 0 destination 192.168.40.200 0
rule deny ip source 192.168.10.0 0.0.0.255 destination 192.168.40.200 0.0.0.0
rule deny ip source 192.168.20.100 0 destination 192.168.30.200 0
rule permit icmp source any destination any
rule deny ip source any destination any
int g0/0/0: acl3001
即是:vlan30,vlan40及PublicServer服务器,在int g0/0/0的outbound规则
rule permit ip source 192.168.30.200 0 destination 192.168.10.0 0.0.0.255
rule permit ip source 192.168.40.200 0 destination 192.168.20.100 0
rule permit ip source 192.168.100.200 0 destination any
rule permit icmp source any destination any
rule deny ip source any destination any
int g0/0/2 acl3002
即是:vlan10,vlan20,vlan30,vlan40,在int g0/0/2的outbound规则
rule permit tcp source 192.168.10.0 0.0.0.255 destination 192.168.100.200 0 destination-port eq 21
rule permit tcp source 192.168.20.0 0.0.0.255 destination 192.168.100.200 0 destination-port eq 21
rule permit tcp source 192.168.30.0 0.0.0.255 destination 192.168.100.200 0 destination-port eq 80
rule permit tcp source 192.168.40.200 0 destination 192.168.100.200 0 destination-port eq 80
rule permit udp source any destination 192.168.100.200 0 destination-port eq 53
rule permit icmp source any destination any
rule deny ip source any destination any
在路由器R1上分别是创建并应用acl规则
[R1]acl 3000
[R1-acl-adv-3000]rule permit tcp source 192.168.10.0 0.0.0.255 destination 192.1
68.30.200 0 destination-port eq 80
[R1-acl-adv-3000]
[R1-acl-adv-3000]rule permit ip source 192.168.20.100 0 destination 192.168.40.2
00 0
[R1-acl-adv-3000]
[R1-acl-adv-3000]rule deny ip source 192.168.10.0 0.0.0.255 destination 192.168.
40.200 0.0.0.0
[R1-acl-adv-3000]
[R1-acl-adv-3000]rule deny ip source 192.168.20.100 0 destination 192.168.30.200
0
[R1-acl-adv-3000]
[R1-acl-adv-3000]rule permit icmp source any destination any
[R1-acl-adv-3000]
[R1-acl-adv-3000]rule deny ip source any destination any
[R1-acl-adv-3000]acl 3001
[R1-acl-adv-3001]rule permit ip source 192.168.30.200 0 destination 192.168.10.0
0.0.0.255
[R1-acl-adv-3001]
[R1-acl-adv-3001]rule permit ip source 192.168.40.200 0 destination 192.168.20.1
00 0
[R1-acl-adv-3001]
[R1-acl-adv-3001]rule permit ip source 192.168.100.200 0 destination any
[R1-acl-adv-3001]
[R1-acl-adv-3001]rule permit icmp source any destination any
[R1-acl-adv-3001]
[R1-acl-adv-3001]rule deny ip source any destination any
[R1-acl-adv-3001]acl 3002
[R1-acl-adv-3002]rule permit tcp source 192.168.10.0 0.0.0.255 destination 192.1
68.100.200 0 destination-port eq 21
[R1-acl-adv-3002]
[R1-acl-adv-3002]rule permit tcp source 192.168.20.0 0.0.0.255 destination 192.1
68.100.200 0 destination-port eq 21
[R1-acl-adv-3002]
[R1-acl-adv-3002]rule permit tcp source 192.168.30.0 0.0.0.255 destination 192.1
68.100.200 0 destination-port eq 80
[R1-acl-adv-3002]
[R1-acl-adv-3002]rule permit tcp source 192.168.40.200 0 destination 192.168.100
.200 0 destination-port eq 80
[R1-acl-adv-3002]
[R1-acl-adv-3002]rule permit udp source any destination 192.168.100.200 0 destin
ation-port eq 53
[R1-acl-adv-3002]
[R1-acl-adv-3002]rule permit icmp source any destination any
[R1-acl-adv-3002]
[R1-acl-adv-3002]rule deny ip source any destination any
[R1-acl-adv-3002]q
[R1]int g0/0/1
[R1-GigabitEthernet0/0/1]traffic-filter outbound acl 3000
[R1-GigabitEthernet0/0/1]int g0/0/0
[R1-GigabitEthernet0/0/0]traffic-filter outbound acl 3001
[R1-GigabitEthernet0/0/0]int g0/0/2
[R1-GigabitEthernet0/0/2]traffic-filter outbound acl 3002
[R1-GigabitEthernet0/0/2]
测试:
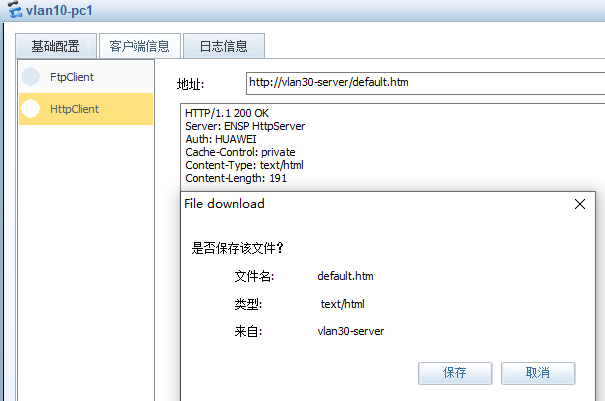
1、-vlan10内所有的主机,只能通过http访问vlan30-server的服务器;不能访问vlan40-server服务器
vlan10 只能通过http访问vlan30-server服务器
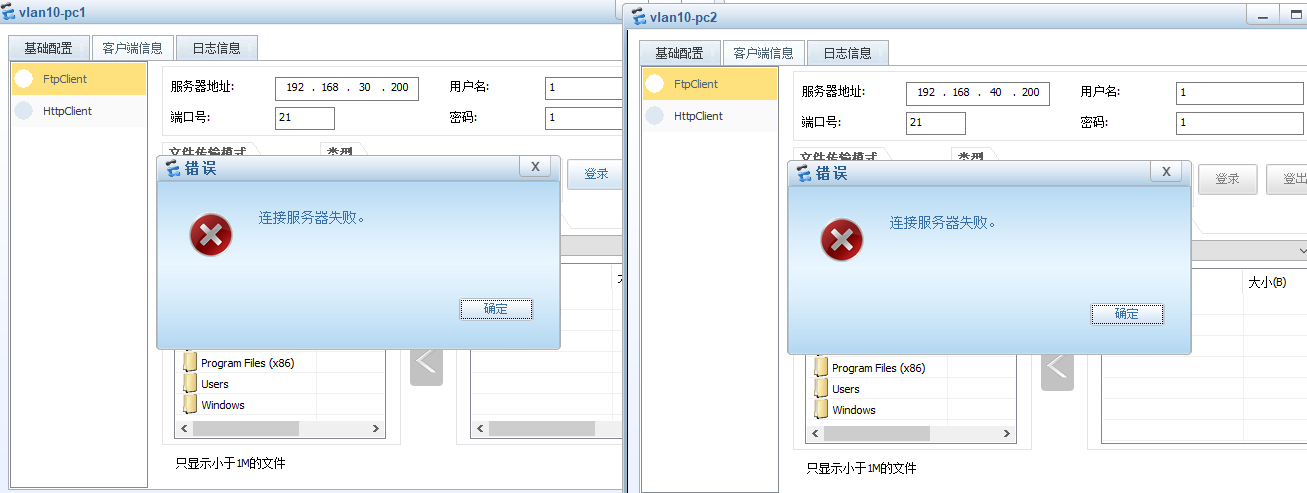
vlan10 访问vlan30-server的http正常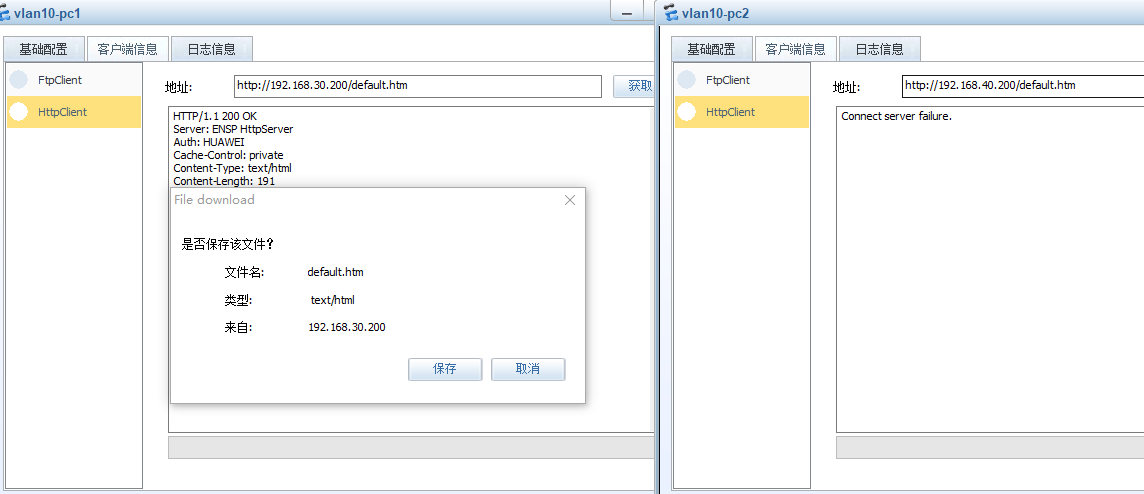
6、-PublicServer服务器对所有pc提供dns服务
当pc通过域名解析访问服务器时,必须满足其它规则里也不冲突.
1、-vlan10内所有的主机,只能通过http访问vlan30-server的服务器;不能访问vlan40-server服务器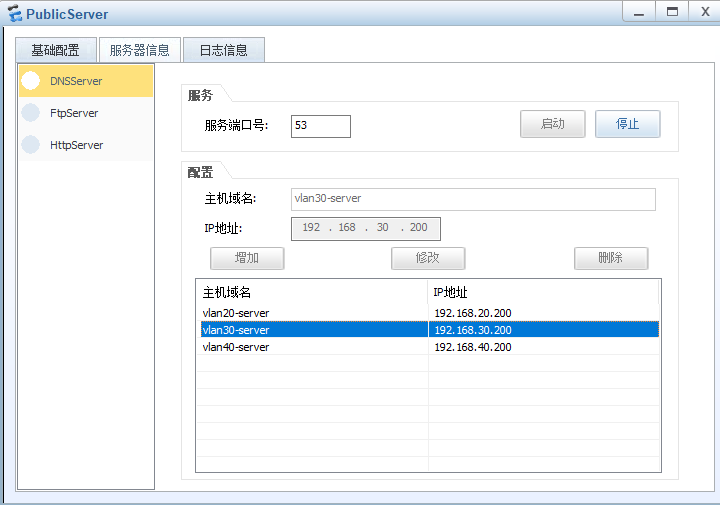

华为设备acl配置的更多相关文章
- 华为设备ACL与NAT技术
ACL 访问控制列表(Access Control Lists),是应用在路由器(或三层交换机)接口上的指令列表,用来告诉路由器哪些数据可以接收,哪些数据是需要被拒绝的,ACL的定义是基于协议的,它适 ...
- 华为S5700基础配置----备份和恢复配置文件
一:备份配置文件 设备作为FTP服务器,用户PC作为FTP客户端 # 配置设备的FTP功能及FTP用户信息. <HUAWEI> system-view [HUAWEI] ftp serve ...
- 思科设备ACL与NAT技术
ACL 访问控制列表(Access Control Lists),是应用在路由器(或三层交换机)接口上的指令列表,用来告诉路由器哪些数据可以接收,哪些数据是需要被拒绝的,ACL的定义是基于协议的,它适 ...
- 基本的访问控制列表ACL配置
摘要: 访问控制列表ACL (Access Control L ist)是由permit或 deny语句组成的一系列有顺序的规则集合,这些规则根据数据包的源地址.目的地址.源端口.目的端口等信息 来 ...
- 华为交换机ACL如何使用及原则
华为交换机ACL如何使用及原则 转载自:辣条①号 源链接:https://boke.wsfnk.com/archives/480.html ACL(访问控制列表)的应用原则:标准ACL,尽量用在 ...
- (转载)linux中设备文件配置程序udev详解
如果你使用Linux比较长时间了,那你就知道,在对待设备文件这块,Linux改变了几次策略.在Linux早期,设备文件仅仅是是一些带有适当的属性集的普通文件,它由mknod命令创建,文件存放在/dev ...
- linux下通过acl配置灵活目录文件权限(可用于ftp,web服务器的用户权限控制)
linux下通过acl配置灵活目录文件权限(可用于ftp,web服务器的用户权限控制) 发表于2012//07由feng linux 本身的ugo rwx的权限,对于精确的权限控制很是力不从心的,ac ...
- 华为RH8100V3RAID 10配置
a)华为RH8100V3RAID 10配置 1)开机按照提示按Ctrl+H键进入RAID卡WEBBIOS管理界面: 2)选中“Start”回车,进入RAID卡管理配置界面: 3)移动鼠标到 “conf ...
- 由于 web 服务器上此资源的访问控制列表(acl)配置或加密设置,您无权查看此目录或页面。
场景:IIS中遇到无法预览的有关问题(HTTP 异常 401.3 - Unauthorized 由于 Web 服务器上此资源的访问控制列表(ACL)配置或加密设置 IIS中遇到无法预览的问题(HTTP ...
随机推荐
- [THUSC2017]杜老师:bitset+线性基
算法一(50pts) 分析 有一个很显然的暴力做法,对于区间内的每个数开个bitset,然后暴力分解质因数.如果对于一个数,它的一个质因子的指数是奇数,那么就把bitset的对应位设成\(1\).答案 ...
- 同一个tomcat部署多个项目11
在开发项目中,有时候我们需要在同一个tomcat中部署多个项目,小编之前也是遇到了这样的情况,碰过不少的壁,故整理总结如下,以供大家参考.(以Linux为例,其他系统同样适用) 一.首先将需要部署的项 ...
- c++函数相关
1,内连函数 inline 返回值类型 函数名(形参列表) 普通函数成为内连函数:在普通函数声明之前加上inline 成员函数成为内连函数:在类中定义的函数全部默认为内连函数,可以显示加上inline ...
- DataList是外部传入的子项数据列表
//定义适配器类public class MyAdapter extends RecyclerView.Adapter<MyAdapter.MyViewHolder>{ private C ...
- php缓冲区
我理解的要点: 1.所有缓冲区控制是在一个PHP执行进程中发生的.如:你打开n个demo.php,他们之间开启和关闭缓冲是互不影响的. 2.output_buffering在程序中用ini_set是不 ...
- 在HTML标签元素中,绑定JS函数
<a onclick="ShowMsg(this)" id="myA" href="#">按钮</a> //JS方法 ...
- Python中的self用法之面向对象
class Student(object): def __init__(self, name, score): self.__name = name self.__score = score def ...
- kafka window安装与配置
一.安装jdk1.8(此处省略) 二.安装zookeeper1. 下载安装包:http://zookeeper.apache.org/releases.html,解压到指定目录(如下) 2. 在系统变 ...
- oauth2.0协议原理
OAuth的授权不会使用第三方触及到用户的帐号信息(如用户密码),即第三方无需使用用户的用户名与密码就可以申请获得该用户资源的授权,因此OAuth是安全的. OAuth的作用:就是让“客户端”安全可控 ...
- xmake v2.2.2, 让C/C++拥有包依赖自动构建
前言 历经四个多月,xmake终于更新了新版本v2.2.2,并且上线了重量级功能:原生支持的远程依赖包管理. 而这个特性,其实我陆陆续续写了将近一年的时间,才初步完成,对于此特性的开发进展和历史,有兴 ...
