Linux操作系统安全-局域网私有CA(Certificate Authority)证书服务器实战篇
Linux操作系统安全-局域网私有CA(Certificate Authority)证书服务器实战篇
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
一.试验架构说明
node101.yinzhengjie.org.cn:
CA服务器 node108.yinzhengjie.org.cn:
CA客户端
[root@node101.yinzhengjie.org.cn ~]# uname -r
3.10.-.el7.x86_64
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# uname -m
x86_64
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# cat /etc/redhat-release
CentOS Linux release 7.6. (Core)
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# free -h
total used free shared buff/cache available
Mem: .6G 132M .2G 8.6M 299M .3G
Swap: .9G 0B .9G
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# hostname -i
172.30.1.101
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# cat /etc/hostname
node101.yinzhengjie.org.cn
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
:: localhost localhost.localdomain localhost6 localhost6.localdomain6 172.30.1.101 node101.yinzhengjie.org.cn
172.30.1.102 node102.yinzhengjie.org.cn
172.30.1.103 node103.yinzhengjie.org.cn
172.30.1.104 node104.yinzhengjie.org.cn
172.30.1.105 node105.yinzhengjie.org.cn
172.30.1.106 node106.yinzhengjie.org.cn
172.30.1.107 node107.yinzhengjie.org.cn
172.30.1.108 node108.yinzhengjie.org.cn
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# cat /etc/hosts
[root@node108.yinzhengjie.org.cn ~]# uname -r
3.10.-.el7.x86_64
[root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]# uname -m
x86_64
[root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]# free -h
total used free shared buff/cache available
Mem: .7G 98M .5G 8.5M 148M .4G
Swap: .9G 0B .9G
[root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]# cat /etc/redhat-release
CentOS Linux release 7.6. (Core)
[root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]# hostname -i
172.30.1.108
[root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
:: localhost localhost.localdomain localhost6 localhost6.localdomain6 172.30.1.101 node101.yinzhengjie.org.cn
172.30.1.102 node102.yinzhengjie.org.cn
172.30.1.103 node103.yinzhengjie.org.cn
172.30.1.104 node104.yinzhengjie.org.cn
172.30.1.105 node105.yinzhengjie.org.cn
172.30.1.106 node106.yinzhengjie.org.cn
172.30.1.107 node107.yinzhengjie.org.cn
172.30.1.108 node108.yinzhengjie.org.cn [root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]# cat /etc/hosts
二.生成自签名证书
1>.查看opennssl的配置文件
openssl的配置文件:
/etc/pki/tls/openssl.cnf
三种策略:match匹配、optional可选、supplied提供
match:
要求申请填写的信息跟CA设置信息必须一致
optional:
可有可无,跟CA设置信息可不一致
supplied:
必须填写这项申请信息,
[root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/pki/tls/openssl.cnf
HOME = .
RANDFILE = $ENV::HOME/.rnd
oid_section = new_oids
[ new_oids ]
tsa_policy1 = 1.2.3.4.
tsa_policy2 = 1.2.3.4.5.6
tsa_policy3 = 1.2.3.4.5.7
[ ca ]
default_ca = CA_default # 默认的CA标题名称,该名称会定有很多CA服务器相关参数
[ CA_default ] # 上一行指定的CA标题名称就是这里定义的
dir = /etc/pki/CA # 存放CA的目录
certs = $dir/certs # 存放证书的目录
crl_dir = $dir/crl # 存放证书吊销列表信息
database = $dir/index.txt # 一个文本文件用来保存已颁发证书的信息,该文件默认不存在,需要手动创建
new_certs_dir = $dir/newcerts # 默认存放新颁发的证书
certificate = $dir/cacert.pem # 指定CA的证书,即CA自签名证书
serial = $dir/serial # 指定下一个颁发证书的编号,该文件默认不存在,需要手动创建
crlnumber = $dir/crlnumber # 指定下一个吊销证书的编号
crl = $dir/crl.pem # 指定CRL证书文件文件名称
private_key = $dir/private/cakey.pem # 指定CA的私钥文件名称
RANDFILE = $dir/private/.rand # private random number file
x509_extensions = usr_cert # The extentions to add to the cert
name_opt = ca_default # Subject Name options
cert_opt = ca_default # Certificate field options
default_days = # 指定证书的默认有效期
default_crl_days= # 指定多久发布一次CRL信息(证书吊销信息)
default_md = sha256 # 使用默认的加密算法
preserve = no # keep passed DN ordering
policy = policy_match #匹配策略名称,见下一行有定义该名称
[ policy_match ] #用于CA的策略证书
countryName = match #match要求申请填写的信息跟CA设置信息必须一致。国家信息要一样
stateOrProvinceName = match #同上,省份也要一样
organizationName = match #同上,一般情况下,自建的CA服务器国家,省份和组织单位都是一样的。
organizationalUnitName = optional #optional表示可选项,即可有可无,跟CA设置信息可不一致
commonName = supplied #supplied表示必须填写这项申请信息, 即填写用户申请的域名
emailAddress = optional #optional表示可选项,即邮箱可以写也可以不写
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
default_bits =
default_md = sha256
default_keyfile = privkey.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca # The extentions to add to the self signed cert
string_mask = utf8only
[ req_distinguished_name ]
countryName = Country Name ( letter code)
countryName_default = XX
countryName_min =
countryName_max =
stateOrProvinceName = State or Province Name (full name)
localityName = Locality Name (eg, city)
localityName_default = Default City
.organizationName = Organization Name (eg, company)
.organizationName_default = Default Company Ltd
organizationalUnitName = Organizational Unit Name (eg, section)
commonName = Common Name (eg, your name or your server\'s hostname)
commonName_max =
emailAddress = Email Address
emailAddress_max =
[ req_attributes ]
challengePassword = A challenge password
challengePassword_min =
challengePassword_max =
unstructuredName = An optional company name
[ usr_cert ]
basicConstraints=CA:FALSE
nsComment = "OpenSSL Generated Certificate"
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
[ v3_ca ]
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid:always,issuer
basicConstraints = CA:true
[ crl_ext ]
authorityKeyIdentifier=keyid:always
[ proxy_cert_ext ]
basicConstraints=CA:FALSE
nsComment = "OpenSSL Generated Certificate"
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
proxyCertInfo=critical,language:id-ppl-anyLanguage,pathlen:,policy:foo
[ tsa ]
default_tsa = tsa_config1 # the default TSA section
[ tsa_config1 ]
dir = ./demoCA # TSA root directory
serial = $dir/tsaserial # The current serial number (mandatory)
crypto_device = builtin # OpenSSL engine to use for signing
signer_cert = $dir/tsacert.pem # The TSA signing certificate
# (optional)
certs = $dir/cacert.pem # Certificate chain to include in reply
# (optional)
signer_key = $dir/private/tsakey.pem # The TSA private key (optional)
default_policy = tsa_policy1 # Policy if request did not specify it
# (optional)
other_policies = tsa_policy2, tsa_policy3 # acceptable policies (optional)
digests = sha1, sha256, sha384, sha512 # Acceptable message digests (mandatory)
accuracy = secs:, millisecs:, microsecs: # (optional)
clock_precision_digits = # number of digits after dot. (optional)
ordering = yes # Is ordering defined for timestamps?
# (optional, default: no)
tsa_name = yes # Must the TSA name be included in the reply?
# (optional, default: no)
ess_cert_id_chain = no # Must the ESS cert id chain be included?
# (optional, default: no)
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# egrep -v "^ *#|^$" /etc/pki/tls/openssl.cnf
2>.生成私钥
[root@node101.yinzhengjie.org.cn ~]# yum -y install tree
Loaded plugins: fastestmirror
Determining fastest mirrors
* base: mirror.bit.edu.cn
* extras: mirrors.tuna.tsinghua.edu.cn
* updates: mirrors.tuna.tsinghua.edu.cn
base | 3.6 kB ::
extras | 2.9 kB ::
updates | 2.9 kB ::
(/): base//x86_64/group_gz | kB ::
(/): extras//x86_64/primary_db | kB ::
(/): base//x86_64/primary_db | 6.0 MB ::
(/): updates//x86_64/primary_db | 5.8 MB ::
Resolving Dependencies
--> Running transaction check
---> Package tree.x86_64 :1.6.-.el7 will be installed
--> Finished Dependency Resolution Dependencies Resolved ============================================================================================================================================================================
Package Arch Version Repository Size
============================================================================================================================================================================
Installing:
tree x86_64 1.6.-.el7 base k Transaction Summary
============================================================================================================================================================================
Install Package Total download size: k
Installed size: k
Downloading packages:
tree-1.6.-.el7.x86_64.rpm | kB ::
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : tree-1.6.-.el7.x86_64 /
Verifying : tree-1.6.-.el7.x86_64 / Installed:
tree.x86_64 :1.6.-.el7 Complete!
[root@node101.yinzhengjie.org.cn ~]#
[root@node101.yinzhengjie.org.cn ~]# yum -y install tree
[root@node101.yinzhengjie.org.cn ~]# cd /etc/pki/CA/
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── certs
├── crl
├── newcerts
└── private directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# (umask ;openssl genrsa -out private/cakey.pem )
Generating RSA private key, bit long modulus
...........................................................................................+++
........+++
e is (0x10001)
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── certs
├── crl
├── newcerts
└── private
└── cakey.pem directories, file
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# ll private/
total
-rw------- root root Dec : cakey.pem
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048)
3>.生成自签名证书
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── certs
├── crl
├── newcerts
└── private
└── cakey.pem directories, file
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# ll private/
total
-rw------- root root Dec : cakey.pem
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name ( letter code) [XX]:CN
State or Province Name (full name) []:shanxi
Locality Name (eg, city) [Default City]:ankang
Organization Name (eg, company) [Default Company Ltd]:yinzhengjie
Organizational Unit Name (eg, section) []:devops
Common Name (eg, your name or your server's hostname) []:ca.yinzhengjie.org.cn
Email Address []:
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem #新生成的证书文件,可以下载到windows系统查看,如下图所示(在windows系统需要修改文件后缀为crt才能打开哟).
├── certs
├── crl
├── newcerts
└── private
└── cakey.pem directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
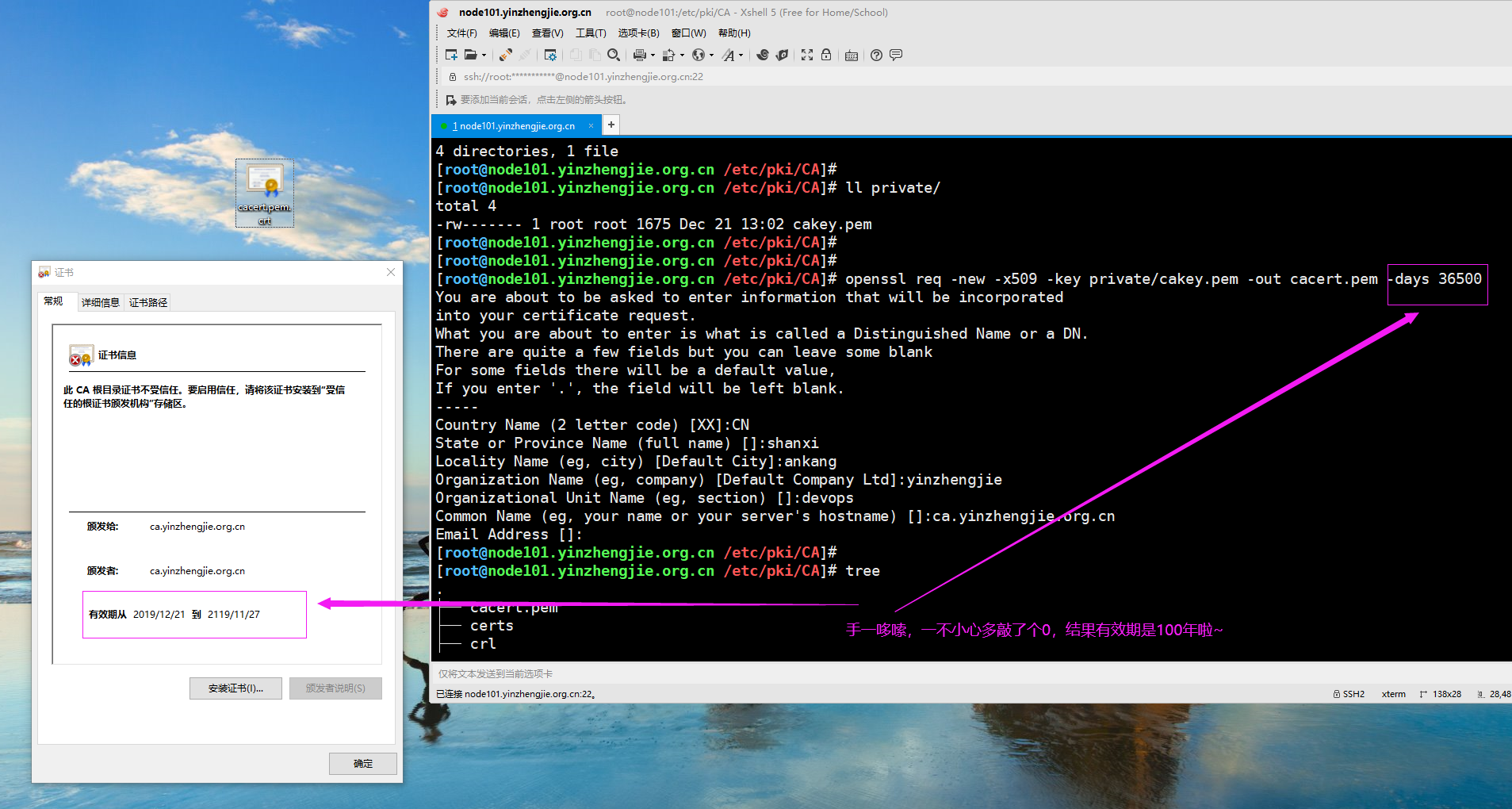
三.CA客户端申请证书
1>.生成私钥
[root@node108.yinzhengjie.org.cn ~]# mkdir /data/ssl -pv
mkdir: created directory ‘/data’
mkdir: created directory ‘/data/ssl’
[root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]# cd /data/ssl/
[root@node108.yinzhengjie.org.cn /data/ssl]#
[root@node108.yinzhengjie.org.cn /data/ssl]# (umask ;openssl genrsa -out myapp.key )
Generating RSA private key, bit long modulus
.++++++
.....................................++++++
e is (0x10001)
[root@node108.yinzhengjie.org.cn /data/ssl]#
[root@node108.yinzhengjie.org.cn /data/ssl]# ll
total
-rw------- root root Dec : myapp.key
[root@node108.yinzhengjie.org.cn /data/ssl]#
[root@node108.yinzhengjie.org.cn /data/ssl]#
2>.利用私钥生成证书请求并发送至CA服务器上
[root@node108.yinzhengjie.org.cn /data/ssl]# ll
total
-rw------- root root Dec : myapp.key
[root@node108.yinzhengjie.org.cn /data/ssl]#
[root@node108.yinzhengjie.org.cn /data/ssl]# openssl req -new -key myapp.key -out myapp.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name ( letter code) [XX]:CN
State or Province Name (full name) []:shanxi
Locality Name (eg, city) [Default City]:ankang
Organization Name (eg, company) [Default Company Ltd]:yinzhengjie
Organizational Unit Name (eg, section) []:devops
Common Name (eg, your name or your server's hostname) []:*.yinzhengjie.org.cn
Email Address []: Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@node108.yinzhengjie.org.cn /data/ssl]#
[root@node108.yinzhengjie.org.cn /data/ssl]# ll
total
-rw-r--r-- root root Dec : myapp.csr
-rw------- root root Dec : myapp.key
[root@node108.yinzhengjie.org.cn /data/ssl]#
[root@node108.yinzhengjie.org.cn /data/ssl]# scp myapp.csr node101.yinzhengjie.org.cn:/etc/pki/CA/
The authenticity of host 'node101.yinzhengjie.org.cn (172.30.1.101)' can't be established.
ECDSA key fingerprint is SHA256:KEchoZnVBkijeoWfG2nvx2ptthsXv7IjkxIJYule57g.
ECDSA key fingerprint is MD5::c8:f5:6e:5f:cf::ec:c4:::d2:d0::3c:da.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'node101.yinzhengjie.org.cn,172.30.1.101' (ECDSA) to the list of known hosts.
root@node101.yinzhengjie.org.cn's password:
myapp.csr % .0KB/s :
[root@node108.yinzhengjie.org.cn /data/ssl]#
[root@node108.yinzhengjie.org.cn /data/ssl]#
四.颁发证书
1>.颁发证书过程及故障排除
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem
├── certs
├── crl
├── myapp.csr
├── newcerts
└── private
└── cakey.pem directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl ca -in myapp.csr -out certs/myapp.crt -days
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/index.txt: No such file or directory
unable to open '/etc/pki/CA/index.txt'
:error::system library:fopen:No such file or directory:bss_file.c::fopen('/etc/pki/CA/index.txt','r')
:error::BIO routines:FILE_CTRL:system lib:bss_file.c::
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# touch index.txt #根据上面的报错提示,说明缺少index.txt文件,因此我们手动创建出来
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl ca -in myapp.csr -out certs/myapp.crt -days
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/serial: No such file or directory
error while loading serial number
:error::system library:fopen:No such file or directory:bss_file.c::fopen('/etc/pki/CA/serial','r')
:error::BIO routines:FILE_CTRL:system lib:bss_file.c::
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# echo 0F > serial #根据上面的提示,说明仍然是少了文件,因此我们继续手动创建出来
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat serial
0F
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl ca -in myapp.csr -out certs/myapp.crt -days 1000 #执行颁发证书的指令
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: (0xf)
Validity
Not Before: Dec :: GMT
Not After : Sep :: GMT
Subject:
countryName = CN
stateOrProvinceName = shanxi
organizationName = yinzhengjie
organizationalUnitName = devops
commonName = *.yinzhengjie.org.cn
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
D0:F2:4D:0E::E5:FF:0D:AC::B2:B3:7C:::F2:AB::C1:
X509v3 Authority Key Identifier:
keyid::3E::F0:EA:BE:7F:DA:8B:A4:7A:F6:::F0:9A::BC:: Certificate is to be certified until Sep :: GMT ( days)
Sign the certificate? [y/n]:y out of certificate requests certified, commit? [y/n]y
Write out database with new entries
Data Base Updated
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem
├── certs
│ └── myapp.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── myapp.csr
├── newcerts
│ └── 0F.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# ll certs/myapp.crt newcerts/0F.pem #我们发现这两个新生成的文件大小是一样的
-rw-r--r-- root root Dec : certs/myapp.crt
-rw-r--r-- root root Dec : newcerts/0F.pem
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# diff certs/myapp.crt newcerts/0F.pem #很显然,这两个文件内容是一样的
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
2>.查看证书信息
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat newcerts/0F.pem #查看证书信息
Certificate:
Data:
Version: (0x2)
Serial Number: (0xf)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=shanxi, L=ankang, O=yinzhengjie, OU=devops, CN=ca.yinzhengjie.org.cn
Validity
Not Before: Dec :: GMT
Not After : Sep :: GMT
Subject: C=CN, ST=shanxi, O=yinzhengjie, OU=devops, CN=*.yinzhengjie.org.cn
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: ( bit)
Modulus:
:b7:a1:2e:0c:f3:a4:e8:bc::0b:9b::3b::
:ed:8d::5a:e2::4d:::cc:f5:1d:ef:bb:
::d3:3e:a6::f8:6d:::::fd::cc:
5b:6d:::::::ab:5f:ea:ae::::
2c:::e4::5f::ff:eb:0a:ea:2a:fa:6f::
::fb:d1:b4:7e::a9::ba::2e:1c:0f:f6:
:::e6:c5:ca:::8c:::c7:5d:e0:b6:
d7::e5::b8::ff:fb::ca::cc:d3:7c:6c:
:c4:b0:f7:f3:::a2:
Exponent: (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
D0:F2:4D:0E::E5:FF:0D:AC::B2:B3:7C:::F2:AB::C1:
X509v3 Authority Key Identifier:
keyid::3E::F0:EA:BE:7F:DA:8B:A4:7A:F6:::F0:9A::BC:: Signature Algorithm: sha256WithRSAEncryption
::7f::fe:e5:c2:ad:fd:dc:c2:bc:0b:::fb::a8:
2e:dc::8c:f6:a9::2d:2a:c1::bb::5c::::1f:
4a:a8:c3:a5::1a:::ac:0e::::dd:f8::::
bd:fc:cf::8a:cf:7e::7a::be:a7:3f:::cc:::
:6f:::5c:c7:0b:fa:c5::d2:2f:dc:d3:f4::::
f2::1b:0c:fc:3c:c1::c2:c8::ed:2a::3b::::
e1::::5d:3f:bf:d5:::c2::d8::dd:fe:1c::
::::b7:c8:f2:3e:::d1::6c:f6::3d:b7:fc:
d9::be:ad::a2:f1:7f:b8:::b2:2e::a7:::e1:
7a:::9b:1c::7d:::5d::ce:c8:6f:eb::7e:d5:
::c9:ea:a0:b1:::3b::f7:c2::8f:8d:b2:a0::
c6:dd:f3:::de:3a::::3e:c2:b0::ca:b1::2f:
fd:e2:::9c:dc:f3:e5:d6:::::3a::2c::4c:
:::b7::4e::bf:9c:1c:0c:f0:ce::af:be::a7:
ea::bf:af
-----BEGIN CERTIFICATE-----
MIIDTDCCAjSgAwIBAgIBDzANBgkqhkiG9w0BAQsFADB2MQswCQYDVQQGEwJDTjEP
MA0GA1UECAwGc2hhbnhpMQ8wDQYDVQQHDAZhbmthbmcxFDASBgNVBAoMC3lpbnpo
ZW5namllMQ8wDQYDVQQLDAZkZXZvcHMxHjAcBgNVBAMMFWNhLnlpbnpoZW5namll
Lm9yZy5jbjAeFw0xOTEyMjEwNjI3NThaFw0yMjA5MTYwNjI3NThaMGQxCzAJBgNV
BAYTAkNOMQ8wDQYDVQQIDAZzaGFueGkxFDASBgNVBAoMC3lpbnpoZW5namllMQ8w
DQYDVQQLDAZkZXZvcHMxHTAbBgNVBAMMFCoueWluemhlbmdqaWUub3JnLmNuMIGf
MA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC3oS4M86TovEELm0A7JoDtjQNa4hVN
BZjM9R3vuyYy0z6mR/htJCM1I/0JzFttJSOWNJCSq1/qriEHZyxREOQ0Xwj/6wrq
KvpvR3GI+9G0fmWpUrqHLhwP9lVWQubFyjVkjJZ2x13gtteZ5Re4lf/7IsqZzNN8
bHDEsPfzhzKiRQIDAQABo3sweTAJBgNVHRMEAjAAMCwGCWCGSAGG+EIBDQQfFh1P
cGVuU1NMIEdlbmVyYXRlZCBDZXJ0aWZpY2F0ZTAdBgNVHQ4EFgQU0PJNDjLl/w2s
UbKzfCMS8qsxwXQwHwYDVR0jBBgwFoAUYT5G8Oq+f9qLpHr2iTXwmmW8BRMwDQYJ
KoZIhvcNAQELBQADggEBAClIfzj+5cKt/dzCvAs4iPuZqC7caYz2qSQtKsEnu1Bc
FnAlH0qow6UhGnkwrA6IggTd+BQiVr38z4aKz36IejS+pz9YBcwzlXFvUzlcxwv6
xWbSL9zT9IYBU/JjGwz8PMGSwsgk7Sp2Ozcgk+FHcSZdP7/VA2LCSdiE3f4cg2BD
iHe3yPI+lWPRV2z2BT23/NmAvq05ovF/uEZZsi4hp4ZT4XpDlZscM32EA12Yzshv
6wF+1YKRyeqgsWc5OyH3wlCPjbKgksbd83aF3jp3AyY+wrAnyrFEL/3idZac3PPl
1iRiZUQ6QiwITBiHQbcJTmi/nBwM8M5Qr74zp+qYv68=
-----END CERTIFICATE-----
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat newcerts/0F.pem #查看证书信息,也可以直接查看myapp.crt证书文件,因为它们是一样的
3>.将证书下载到windows操作系统查看
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# sz certs/myapp.crt #如下图所示,下载文件到本地,下载时选择crt结尾的,其实下载0F.pem也可以(因为文件内容相同),但windows识别crt格式的文件可以直接查看。 [root@node101.yinzhengjie.org.cn /etc/pki/CA]#

4>.颁发证书后查看文件内容变更
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem
├── certs
│ └── myapp.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── myapp.csr
├── newcerts
│ └── 0F.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat index.txt #该文件记录了证书文件相关信息,首字母"V"表示证书有效,若证书被吊销的话,可能首字母是"R"
V 220916062758Z 0F unknown /C=CN/ST=shanxi/O=yinzhengjie/OU=devops/CN=*.yinzhengjie.org.cn
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat serial [root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat index.txt.old #存放之前版本的信息
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat serial.old #存放之前的版本信息
0F
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat index.txt.attr #如果看到"unique_subject=yes"想必大家也猜到啥意思了,没错它规定了证书必须是唯一性的,也就是说我们不能对同一个证书请求多次颁发证书文件。
unique_subject = yes
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
五.windows导入咱们自己生成自签名证书
1>.如下图所示,咱们的操作系统"无法找到该证书的颁发者。",因此我们可以考虑将"*.yinzhengjie.org.cn"证书的颁发者证书也下载到本地导入并安装
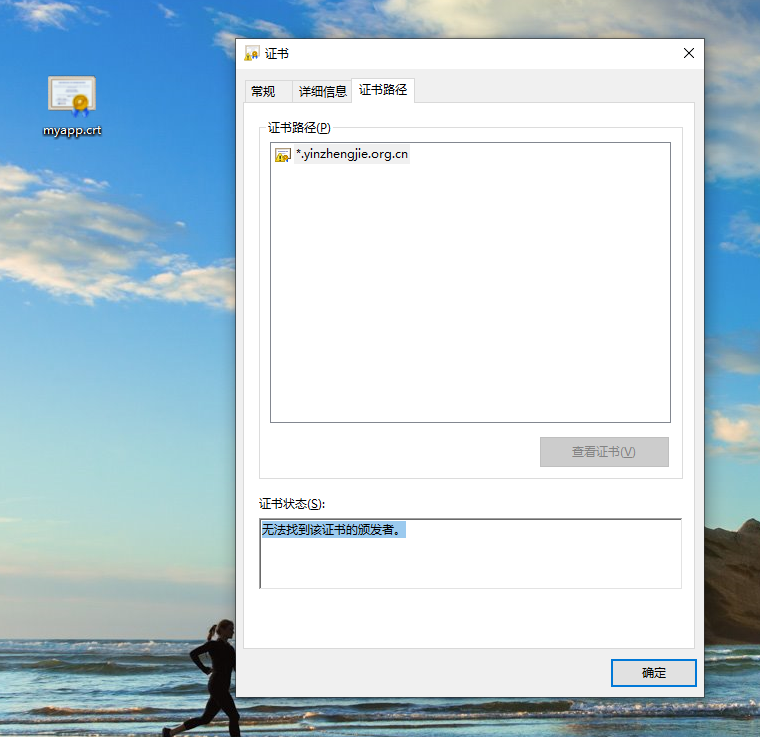
2>.下载CA服务器证书到本地并更名为"*.crt"或者"*.cer"文件后缀,如下图所示(紧接着安装证书)
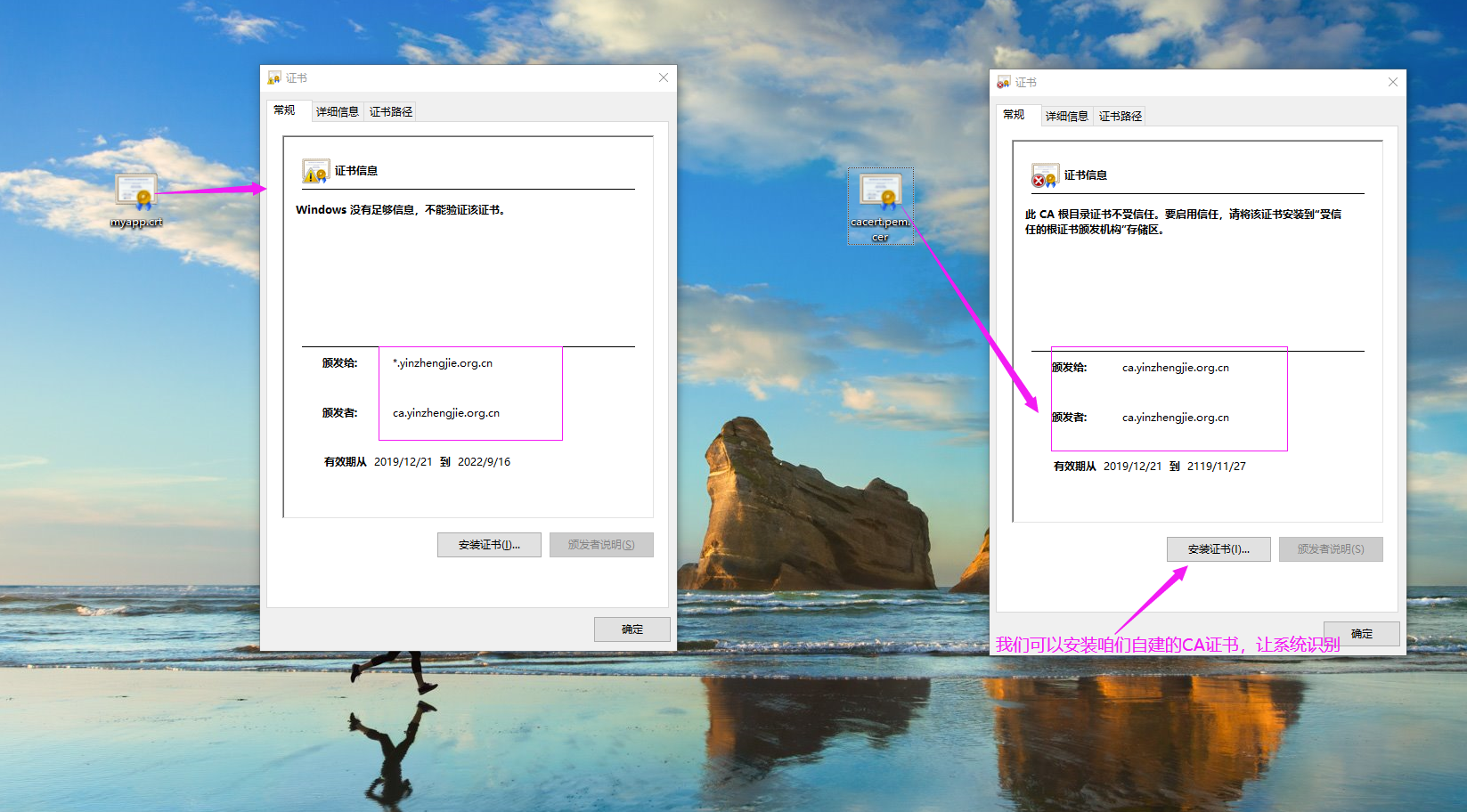
3>.如下图所示,点击"安装证书"会弹出右侧的对话框,继续点击"下一步"
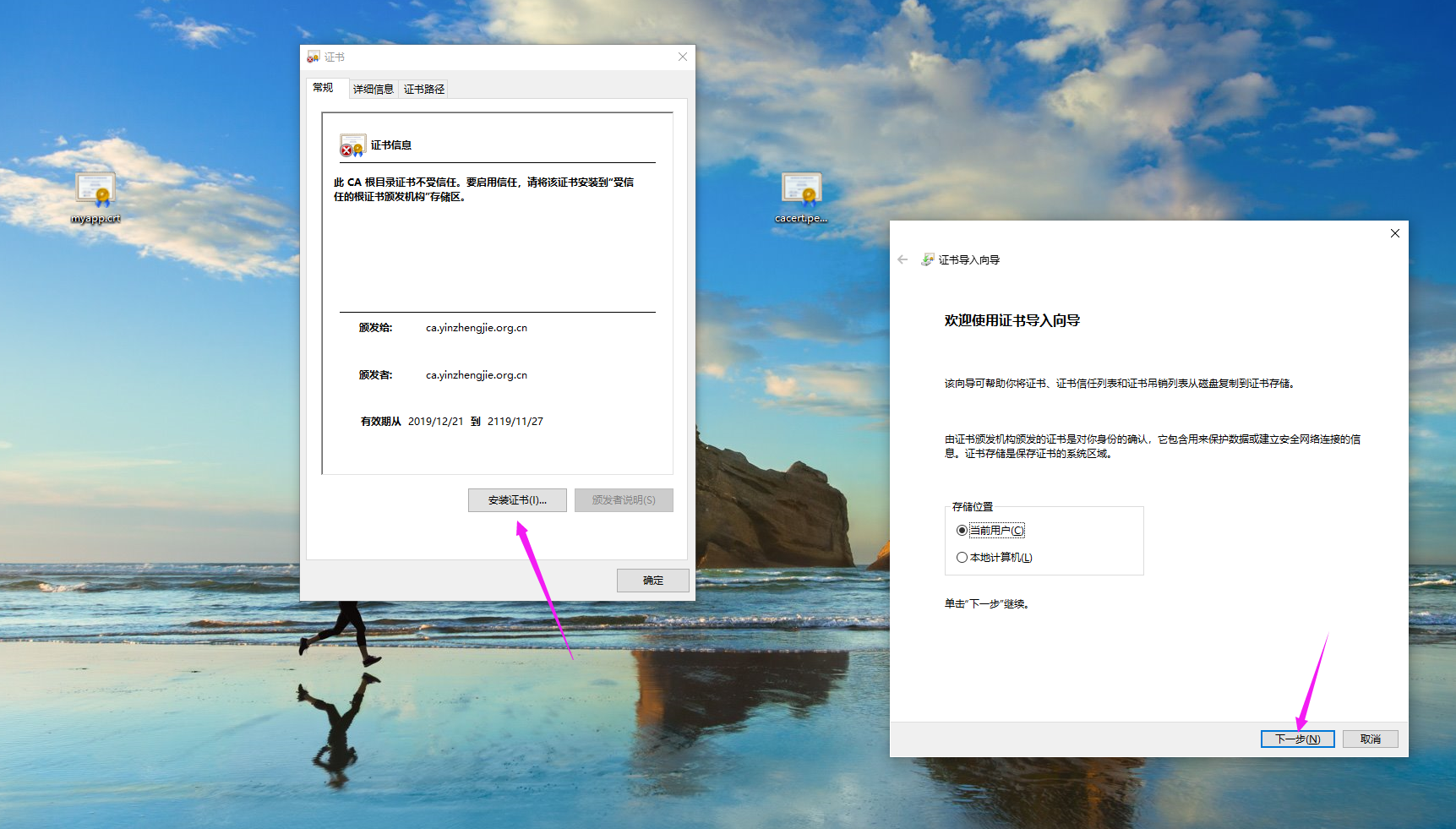
4>.如下图所示,将我们的证书选择为"受信任的根证书颁发机构"

5>.配置完成后,点击"下一步"
6>.继续点击"完成"
7>.接下来会弹出如下图所示的对话框以确认安装证书提示,点击"是"
8>.点击"确定",证书导入成功
9>.证书安装完成后,再次打开证书查看相应信息,如下图所示

六.使用openssl命令在命令行查看证书信息
1>.将证书文件拷贝到客户端
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# ll
total
-rw-r--r-- root root Dec : cacert.pem
drwxr-xr-x. root root Dec : certs
drwxr-xr-x. root root Oct crl
-rw-r--r-- root root Dec : index.txt
-rw-r--r-- root root Dec : index.txt.attr
-rw-r--r-- root root Dec : index.txt.old
-rw-r--r-- root root Dec : myapp.csr
drwxr-xr-x. root root Dec : newcerts
drwx------. root root Dec : private
-rw-r--r-- root root Dec : serial
-rw-r--r-- root root Dec : serial.old
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem
├── certs
│ └── myapp.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── myapp.csr
├── newcerts
│ └── 0F.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# scp certs/myapp.crt root@node108.yinzhengjie.org.cn:/data/ssl
myapp.crt % .1MB/s :
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
2>.客户端查看证书信息
[root@node108.yinzhengjie.org.cn ~]# ll /data/ssl/
total
-rw-r--r-- root root Dec : myapp.crt
-rw-r--r-- root root Dec : myapp.csr
-rw------- root root Dec : myapp.key
[root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]# openssl x509 -in /data/ssl/myapp.crt -noout -text #以文本方式在客户端查看证书信息
Certificate:
Data:
Version: (0x2)
Serial Number: (0xf)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=shanxi, L=ankang, O=yinzhengjie, OU=devops, CN=ca.yinzhengjie.org.cn
Validity
Not Before: Dec :: GMT
Not After : Sep :: GMT
Subject: C=CN, ST=shanxi, O=yinzhengjie, OU=devops, CN=*.yinzhengjie.org.cn
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: ( bit)
Modulus:
:b7:a1:2e:0c:f3:a4:e8:bc::0b:9b::3b::
:ed:8d::5a:e2::4d:::cc:f5:1d:ef:bb:
::d3:3e:a6::f8:6d:::::fd::cc:
5b:6d:::::::ab:5f:ea:ae::::
2c:::e4::5f::ff:eb:0a:ea:2a:fa:6f::
::fb:d1:b4:7e::a9::ba::2e:1c:0f:f6:
:::e6:c5:ca:::8c:::c7:5d:e0:b6:
d7::e5::b8::ff:fb::ca::cc:d3:7c:6c:
:c4:b0:f7:f3:::a2:
Exponent: (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
D0:F2:4D:0E::E5:FF:0D:AC::B2:B3:7C:::F2:AB::C1:
X509v3 Authority Key Identifier:
keyid::3E::F0:EA:BE:7F:DA:8B:A4:7A:F6:::F0:9A::BC:: Signature Algorithm: sha256WithRSAEncryption
::7f::fe:e5:c2:ad:fd:dc:c2:bc:0b:::fb::a8:
2e:dc::8c:f6:a9::2d:2a:c1::bb::5c::::1f:
4a:a8:c3:a5::1a:::ac:0e::::dd:f8::::
bd:fc:cf::8a:cf:7e::7a::be:a7:3f:::cc:::
:6f:::5c:c7:0b:fa:c5::d2:2f:dc:d3:f4::::
f2::1b:0c:fc:3c:c1::c2:c8::ed:2a::3b::::
e1::::5d:3f:bf:d5:::c2::d8::dd:fe:1c::
::::b7:c8:f2:3e:::d1::6c:f6::3d:b7:fc:
d9::be:ad::a2:f1:7f:b8:::b2:2e::a7:::e1:
7a:::9b:1c::7d:::5d::ce:c8:6f:eb::7e:d5:
::c9:ea:a0:b1:::3b::f7:c2::8f:8d:b2:a0::
c6:dd:f3:::de:3a::::3e:c2:b0::ca:b1::2f:
fd:e2:::9c:dc:f3:e5:d6:::::3a::2c::4c:
:::b7::4e::bf:9c:1c:0c:f0:ce::af:be::a7:
ea::bf:af
[root@node108.yinzhengjie.org.cn ~]#
[root@node108.yinzhengjie.org.cn ~]#
七.吊销证书
1>.吊销证书
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem
├── certs
│ └── myapp.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── myapp.csr
├── newcerts
│ └── 0F.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat index.txt #注意第一个字母是"V",说明该证书是可以正常使用的
V 220916062758Z 0F unknown /C=CN/ST=shanxi/O=yinzhengjie/OU=devops/CN=*.yinzhengjie.org.cn
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl ca -revoke certs/myapp.crt #我们将指定的证书吊销
Using configuration from /etc/pki/tls/openssl.cnf
Revoking Certificate 0F.
Data Base Updated
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat index.txt #注意观察第一个字母是"R",说明该 证书已经被吊销了
R 220916062758Z 191221071820Z 0F unknown /C=CN/ST=shanxi/O=yinzhengjie/OU=devops/CN=*.yinzhengjie.org.cn
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
2>.生成吊销证书列表CRL
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem
├── certs
│ └── myapp.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.attr.old
├── index.txt.old
├── myapp.csr
├── newcerts
│ └── 0F.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl ca -gencrl -out crl.pem
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/crlnumber: No such file or directory
error while loading CRL number
140432981714832:error:02001002:system library:fopen:No such file or directory:bss_file.c:402:fopen('/etc/pki/CA/crlnumber','r')
:error::BIO routines:FILE_CTRL:system lib:bss_file.c::
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# echo FF > crlnumber #根据报错可知是缺少证书吊销列表的编号文件
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl ca -gencrl -out crl.pem #生成证书吊销列表
Using configuration from /etc/pki/tls/openssl.cnf
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# cat crlnumber [root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem
├── certs
│ └── myapp.crt
├── crl
├── crlnumber
├── crlnumber.old
├── crl.pem
├── index.txt
├── index.txt.attr
├── index.txt.attr.old
├── index.txt.old
├── myapp.csr
├── newcerts
│ └── 0F.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
3>.查看已经被吊销的证书列表
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem
├── certs
│ └── myapp.crt
├── crl
├── crlnumber
├── crlnumber.old
├── crl.pem
├── index.txt
├── index.txt.attr
├── index.txt.attr.old
├── index.txt.old
├── myapp.csr
├── newcerts
│ └── 0F.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl crl -in /etc/pki/CA/crl.pem -noout -text
Certificate Revocation List (CRL):
Version (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: /C=CN/ST=shanxi/L=ankang/O=yinzhengjie/OU=devops/CN=ca.yinzhengjie.org.cn
Last Update: Dec :: GMT
Next Update: Jan :: GMT
CRL extensions:
X509v3 CRL Number: Revoked Certificates:
Serial Number: 0F
Revocation Date: Dec :: GMT
Signature Algorithm: sha256WithRSAEncryption
b5::5a:ee:3d:e2:7c:d8::::a3:::b8:a7:c4::
da:a7::9f:ff::c0:::5e:ca:6e::f6::ed:e0::
db::::c0:::a7::c8:f6:f5:ea::ec::1b::
:3e:b6:::f5::8c:::af::aa::2e:6c:ac:6c:
8b:::9d:1a:c1:8e::b0:cb:::2f::::::
cd::ba:1b::db:e5:c1:8f:ea:cd:ce:::e7:ad:4c:2b:
:::ab:fa:7e:e9:1e:f1::b4::::a9:c6::ef:
::c5::1b::::ce:5e:4d:ef:::ff:ea:f6:2e:
:ee:cd:4f:ed:0a:a5::c4:::::d7::8f:b0::
:5b:0d:8c::c4:1f::1d:5e:a9:c2:a2:ba::6d:e8:5e:
:::0a:fe::f2:8f:::fa:f6::d0:b4:a2:d8::
6f:ab::ae:::5c:ef:ec:8d:::b1:f7:d5:::4e:
:c8:::3c:c4:2c:a9::1e::::5a::b9:2a:b1:
f7::3f:4b:1f:3b::5c:::ba:8c:5c:8f:::f6:5e:
c7:1d::e4
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
4>.将已经吊销的证书文件拷贝到windows操作系统
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# sz crl.pem #下载到windows操作系统后,由于操作系统不识别因此我们得修改文件后缀,如下图所示。 [root@node101.yinzhengjie.org.cn /etc/pki/CA]#
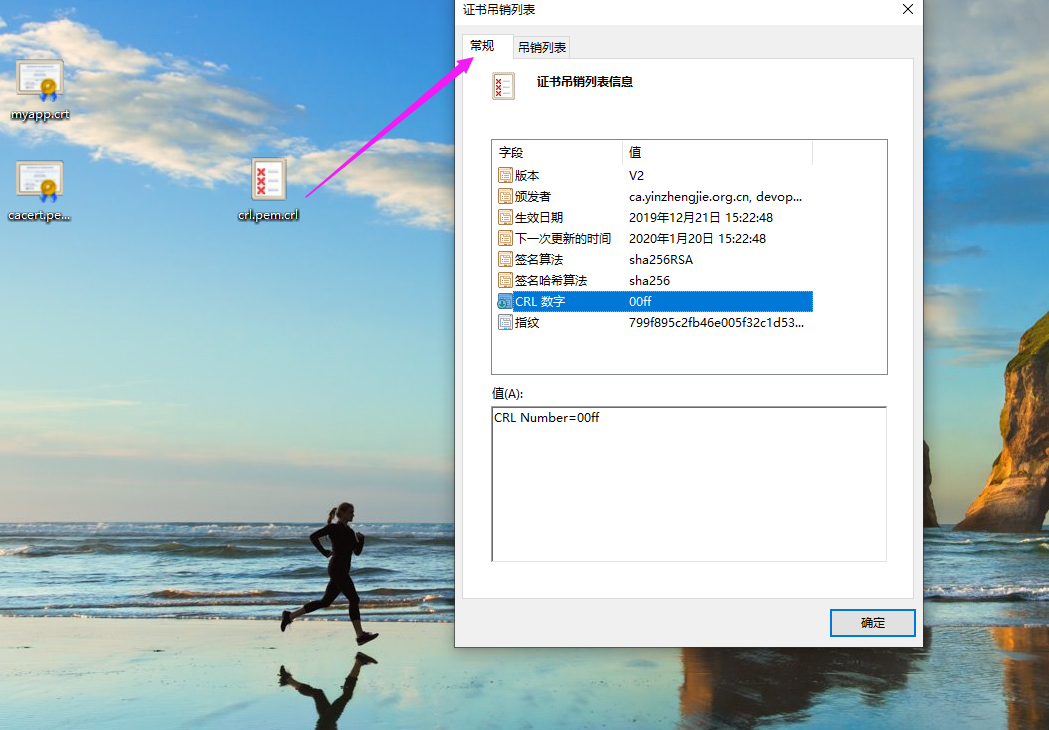
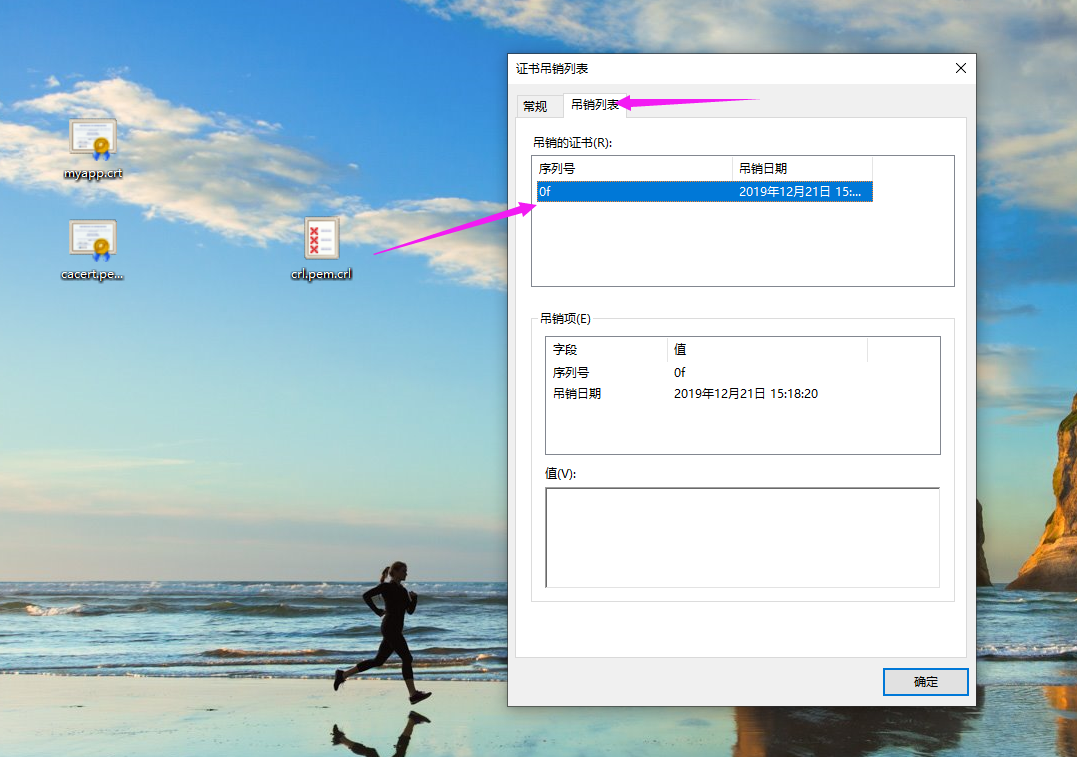
如下图所示,我们可以查看已经被吊销的证书列表。
八.验证证书的合法性
1>.验证CA自签名的证书合法性
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# tree
.
├── cacert.pem
├── certs
│?? └── myapp.crt
├── crl
├── crlnumber
├── crlnumber.old
├── crl.pem
├── index.txt
├── index.txt.attr
├── index.txt.attr.old
├── index.txt.old
├── myapp.csr
├── newcerts
│?? └── 0F.pem
├── private
│?? └── cakey.pem
├── serial
└── serial.old directories, files
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl verify -CAfile cacert.pem certs/myapp.crt #很显然,咱们服务器自签名的证书是合法的,输出是"OK"
certs/myapp.crt: OK
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
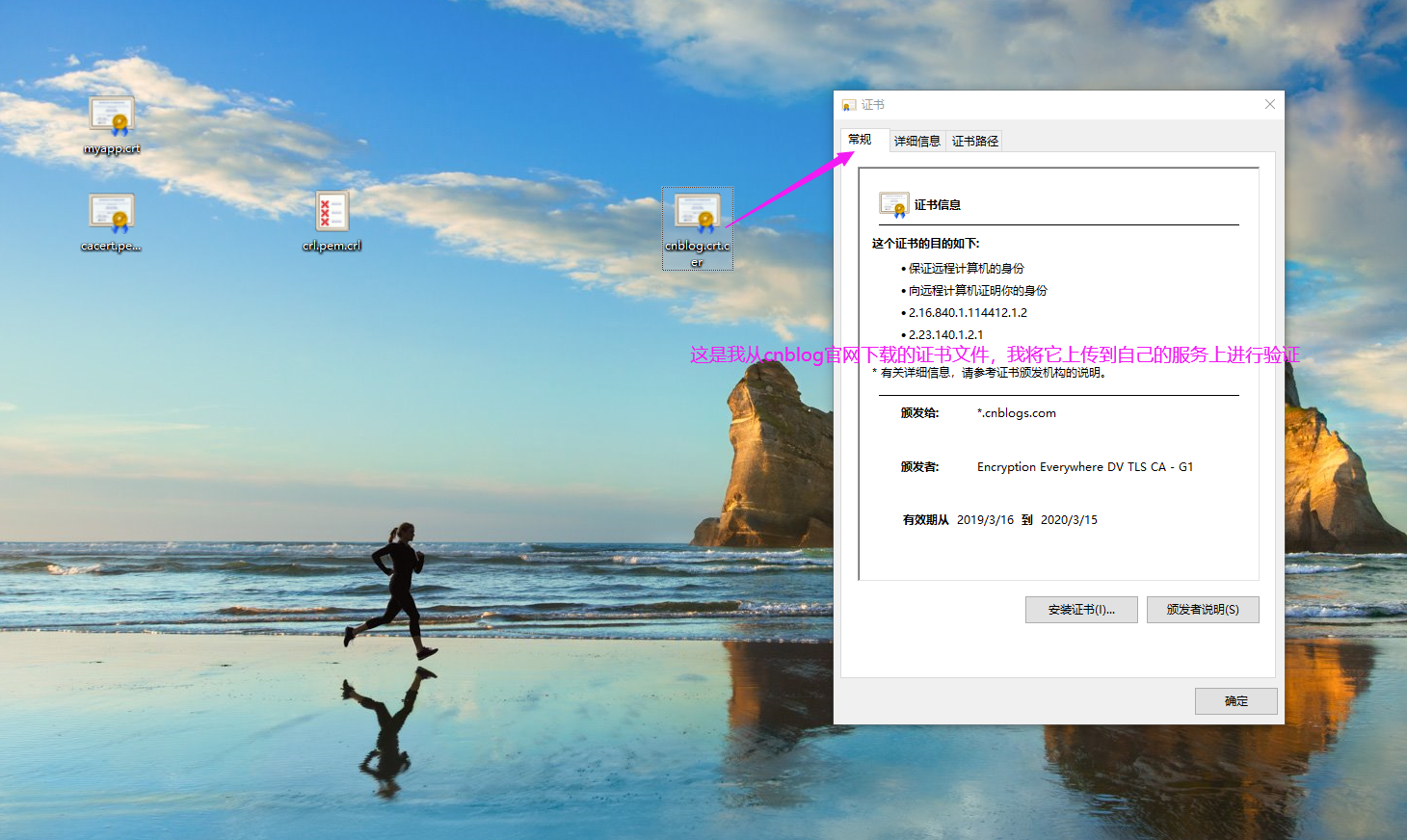
2>.验证"*cnblogs.com"证书的合法性
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# ll cnblog.crt.cer
-rw-r--r-- root root Dec : cnblog.crt.cer
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]# openssl verify -CAfile cacert.pem cnblog.crt.cer
unable to load certificate
:error:0906D06C:PEM routines:PEM_read_bio:no start line:pem_lib.c::Expecting: TRUSTED CERTIFICATE
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
[root@node101.yinzhengjie.org.cn /etc/pki/CA]#
Linux操作系统安全-局域网私有CA(Certificate Authority)证书服务器实战篇的更多相关文章
- 加密解密(2)*客户端,服务器,CA(Certificate Authority),公钥,私钥,证书,签名,验证
加密解密(2)*客户端,服务器,CA(Certificate Authority),公钥,私钥,证书,签名,验证 各角色比喻 客户端:通常为请求方,要验证服务器的身份. 服务器:通常为响应方,有时也要 ...
- Linux 加密安全和私有CA的搭建方法
常用安全技术 3A: 认证:身份确认 授权:权限分配 审计:监控做了什么 安全通信 加密算法和协议 对称加密: 非对称加密 单向加密:哈希(hash)加密 认证协议 对称加密: 加密和解密使用的是同一 ...
- 基于开源CA系统ejbca community 6.3.1.1构建私有CA管理数字证书
最后更新于2017年01月24日 一.为什么 为什么写这篇文章?ca是什么?数字证书是什么?ejbca又是什么? 让我们从http与https说起.http是超文本传输协议(HyperText Tra ...
- 自签名证书和私有CA签名的证书的区别 创建自签名证书 创建私有CA 证书类型 证书扩展名【转】
自签名的证书无法被吊销,CA签名的证书可以被吊销 能不能吊销证书的区别在于,如果你的私钥被黑客获取,如果证书不能被吊销,则黑客可以伪装成你与用户进行通信 如果你的规划需要创建多个证书,那么使用私有 ...
- 创建私有CA并签发证书
一.创建私有CA 1.创建所需要的文件 2.创建私有密钥 3.CA自签证书 -new: 生成新证书签署请求: -x509: 专用于CA生成自签证书:不自签的时候不要加该选项 ...
- 搭建私有CA并实现证书颁发
一.搭建私有CA服务器 1.安装包 # yum -y install openssl 2.生成密钥对儿 # cd /etc/pki/CA # (umask 077;openssl genrsa -ou ...
- CA机构介绍(Certificate Authority 域名SSL证书颁发机构)
SSL证书机构即CA机构的全称为Certificate Authority证书认证中心,只有通过WebTrust国际安全审计认证,根证书才能预装到主流浏览器,成为全球可信的ssl证书颁发机构. HTT ...
- 使用 OpenSSL 创建私有 CA:2 中间证书
OpenSSL 创建私有 CA 三部曲:使用 OpenSSL 创建私有 CA:1 根证书使用 OpenSSL 创建私有 CA:2 中间证书使用 OpenSSL 创建私有 CA:3 用户证书 本文将在前 ...
- 使用 OpenSSL 创建私有 CA:1 根证书
OpenSSL 创建私有 CA 三部曲:使用 OpenSSL 创建私有 CA:1 根证书使用 OpenSSL 创建私有 CA:2 中间证书使用 OpenSSL 创建私有 CA:3 用户证书 OpenS ...
随机推荐
- JDK Mac 安装
JDK安装步骤 一台mac os 环境 jdk.sdk.Android studio 1.打开终端-输入命令Java 2.从下面的图中可以看到,终端会自动给出提示,没有可以使用的java命令 ...
- 问题查询-tomcat内存泄露
1.报警信息 内容: 微信服务器向公众号推送消息或事件后,开发者5秒内没有返回 次数: 5分钟 239次 错误样例: [OpenID=o][Stamp=1562718361][3rdUrl=url][ ...
- 百度语音识别在ROS下的应用-导航
先去wiki下载百度的ros语音识别包:http://wiki.ros.org/baidu_speech 里面包含语音识别voice和speak的node节点,不过voice_node里面有一个小的错 ...
- spering getBean(),IOC
IOC:前面都是对bean定义的处理,postProcess已经实例化了. 解析bean的时候,把需要依赖注入的字段和方法,在postProcessMergedBeanDefinition方法中加到A ...
- git 版本(commit) 回退 -- 使用git reset 指令
刚刚提交了三个commit, git reflog显示如下: 最后一个commit在文件末尾加了一行:v3,以此类推: 下面,使用git reset --hard commitID来进行commit回 ...
- 2.1:CGPROGRAM
文章著作权归作者所有.转载请联系作者,并在文中注明出处,给出原文链接. 本系列原更新于作者的github博客,这里给出链接. 前言 经过前面两个章节的铺垫,我们对渲染以及Unity Shaderlab ...
- 解决Docker服务无法正常启动
重新docker服务报错如下: systemctl restart docker.service Cannot connect to the Docker datemon at tcp://0.0.0 ...
- Sitecore 9 介绍
Sitecore 9就在这里.这个最新版本更大,更智能,更易于使用 - 并且更好地帮助您实现业务和数字目标. 现在,Sitecore 9对营销人员和非Sitecore开发人员来说更容易使用.它拥有许多 ...
- Blackbox_exporter黑盒监测
一.概述 blackbox_exporter是Prometheus 官方提供的 exporter 之一,可以提供 http.dns.tcp.icmp 的监控数据采集.Blackbox_exporter ...
- 新的部署架构之下,如何拿shell?
和朋友聊起一个话题,服务器部署架构升级对安全的影响.从最简单的一台服务器,到应用.数据库.文件服务器分离:从本地机房服务器到云服务器产品矩阵:从虚拟化到容器化部署,一直在往更安全的方向改变. 本文试图 ...
