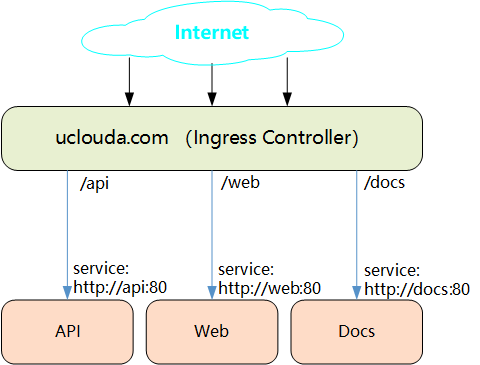
027.掌握Service-Ingress使用
一 Ingress简介
1.1 Ingress
二 Ingress创建
2.1 创建Ingress Controller
1 apiVersion: extensions/v1beta1
2 kind: DaemonSet
3 metadata:
4 name: nginx-ingress-lb
5 labels:
6 name: nginx-ingress-lb
7 namespace: default
8 spec:
9 template:
10 metadata:
11 labels:
12 name: nginx-ingress-lb
13 spec:
14 terminationGracePeriodSeconds: 60
15 containers:
16 - image: gcr.azk8s.cn/google_containers/nginx-ingress-controller:0.9.0-beta.2
17 name: nginx-ingress-lb
18 readinessProbe:
19 httpGet:
20 path: /healthz
21 port: 10254
22 scheme: HTTP
23 livenessProbe:
24 httpGet:
25 path: /healthz
26 port: 10254
27 scheme: HTTP
28 initialDelaySeconds: 10
29 timeoutSeconds: 1
30 ports:
31 - containerPort: 80
32 hostPort: 80
33 - containerPort: 443
34 hostPort: 443
35 env:
36 - name: POD_NAME
37 valueFrom:
38 fieldRef:
39 fieldPath: metadata.name
40 - name: POD_NAMESPACE
41 valueFrom:
42 fieldRef:
43 fieldPath: metadata.namespace
44 args:
45 - /nginx-ingress-controller
46 - --default-backend-service=$(POD_NAMESPACE)/default-http-backend
1 apiVersion: extensions/v1beta1
2 kind: Deployment
3 metadata:
4 name: default-http-backend
5 labels:
6 k8s-app: default-http-backend
7 namespace: default
8 spec:
9 replicas: 1
10 template:
11 metadata:
12 labels:
13 k8s-app: default-http-backend
14 spec:
15 terminationGracePeriodSeconds: 60
16 containers:
17 - name: default-http-backend
18 image: gcr.azk8s.cn/google_containers/defaultbackend:1.0
19 livenessProbe:
20 httpGet:
21 path: /healthz
22 port: 8080
23 scheme: HTTP
24 initialDelaySeconds: 30
25 timeoutSeconds: 5
26 ports:
27 - containerPort: 8080
28 resources:
29 limits:
30 cpu: 10m
31 memory: 20Mi
32 requests:
33 cpu: 10m
34 memory: 20Mi
35 ---
36 apiVersion: v1
37 kind: Service
38 metadata:
39 name: default-http-backend
40 namespace: default
41 labels:
42 k8s-app: default-http-backend
43 spec:
44 ports:
45 - port: 80
46 targetPort: 8080
47 selector:
48 k8s-app: default-http-backend
2.2 定义ingress策略
1 apiVersion: extensions/v1beta1
2 kind: Ingress
3 metadata:
4 name: mywebsite-ingress
5 spec:
6 rules:
7 - host: mywebsite.com
8 http:
9 paths:
10 - path: /demo
11 backend:
12 serviceName: myweb
13 servicePort: 8080
1 Pod
2 NAME READY STATUS RESTARTS AGE
3 ……
4 mysql-m652j 1/1 Running 0 21m #入门实例中的mysql,用于测试
5 myweb-gnhk4 1/1 Running 0 20m
6 myweb-vzg58 1/1 Running 0 20m #入门实例中的myweb,用于测试
7 nginx-ingress-lb-6mj49 1/1 Running 0 16m
8 nginx-ingress-lb-7z74c 1/1 Running 0 16m
9 nginx-ingress-lb-9wlpd 1/1 Running 0 16m
10 nginx-ingress-lb-flgvs 1/1 Running 0 16m
11 nginx-ingress-lb-gcczc 1/1 Running 0 16m
12 nginx-ingress-lb-hcfg6 1/1 Running 0 16m #2.1中的ingress-lb
1 SVC
2 NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S)
3 default-http-backend ClusterIP 10.254.236.120 <none> 80/TCP #默认的backend svc
4 ……
5 mysql ClusterIP 10.254.84.247 <none> 3306/TCP #入门实例中的mysql svc,用于测试
6 myweb NodePort 10.254.119.124 <none> 8080:30001/TCP #入门实例中的myweb svc,用于测试
1 ingress
2 NAME HOSTS ADDRESS PORTS AGE
3 mywebsite-ingress mywebsite.com 80 9m12s
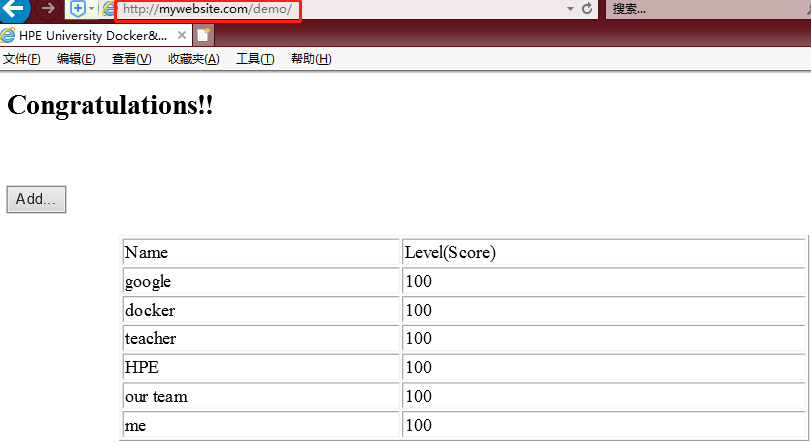
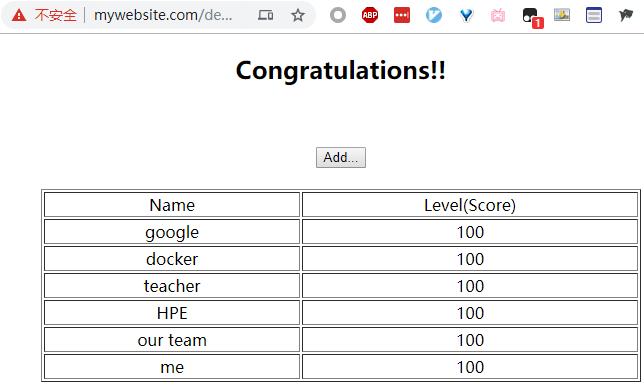
2.3 测试访问
- 将后端Pod的8080暴露于nodeport的30001(因此入门实例可以通过nodeport的30001直接访问服务);
- 后端selector选择了真正实现功能的tomcat pod。
2.4 Ingress策略配置详解
- 转发到单个后端服务上
1 apiVersion: extensions/v1beta1
2 kind: Ingress
3 metadata:
4 name: test-ingress
5 spec:
6 backend:
7 serviceName: myweb
8 servicePort: 8080
- 同一域名下,不同的URL路径被转发到不同的服务上
1 apiVersion: extensions/v1beta1
2 kind: Ingress
3 metadata:
4 name: test-ingress
5 spec:
6 rules:
7 - host: mywebsite.com
8 http:
9 paths:
10 - path: /demo
11 backend:
12 serviceName: myweb
13 servicePort: 8080
14 - path: /api
15 backend:
16 serviceName: myapi
17 servicePort: 8081
- 不同的域名(虚拟主机名)被转发到不同的服务上
1 apiVersion: extensions/v1beta1
2 kind: Ingress
3 metadata:
4 name: test-ingress
5 spec:
6 rules:
7 - host: foo.bar.com
8 http:
9 paths:
10 - backend:
11 serviceName: service1
12 servicePort: 8080
13 - host: bar.foo.com
14 http:
15 paths:
16 - backend:
17 serviceName: service2
18 servicePort: 8080
- 不使用域名的转发规则
1 apiVersion: extensions/v1beta1
2 kind: Ingress
3 metadata:
4 name: test-ingress
5 spec:
6 rules:
7 - http:
8 paths:
9 - path: /demo
10 backend:
11 serviceName: myweb
12 servicePort: 8080
1 ……
2 if (%pass_access_scheme = http) {
3 return 301 https://$best_http_host$request_uri;
4 }
5 ……
1 apiVersion: extensions/v1beta1
2 kind: Ingress
3 metadata:
4 name: test-ingress
5 annotations:
6 ingress.kubernetes.io/ssl-redirect: "false"
7 spec:
8 rules:
9 - http:
10 paths:
11 - path: /demo
12 backend:
13 serviceName: myweb
14 servicePort: 8080
三 Ingress TLS
3.1 Ingress TLS配置步骤
- 创建自签名的密钥和SSL证书文件。
- 将证书保存到Kubernetes中的一个Secret资源对象上。
- 将该Secret对象设置到Ingress中。
3.2 单域名TLS设置
- 创建自签名证书
1 [root@k8smaster01 study]# openssl req -x509 -nodes -days 3650 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=mywebsite.com"
- 创建secret对象
- 方法一:kubectl create secret命令行方式
- 方法二:编辑mywebsite-ingress-secret.yaml文件
1 apiVersion: v1
2 kind: Secret
3 metadata:
4 name: mywebsite-ingress-secret
5 namespace: default
6 type: kubernetes.io/tls
7 data:
8 tls.crt: MIIDAzCCAeugAwIBAgIJAP5FWrsNH3MMMA0GCSqGSIb3DQEBCwUAMBgxFjAUBgNVBAMMDW15d2Vic2l0ZS5jb20wHhcNMTkxMTI2MDkxODA2WhcNMjkxMTIzMDkxODA2WjAYMRYwFAYDVQQDDA1teXdlYnNpdGUuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwxh45nxBk3ROD1Dl6NWa+PGgQWcty3Mcu57RyNFTQ2MOOZ0l53kML9cuLau4OJqk7yvI6rKhtNP5kMNzFrdrsL5cX44wItO3XA2GtO7r7t7PrTwoDskGqQiz0yDw0Ya1TpkOFbCA9VphojXHAL77s2YUG1sZrOSUU0SL3H0v8xUnKIiUPzRCzBqGFUeR7zDuATFQbjrkHUWiPIQ9/7n4YVj35ChHhWco4kuP4RL6l5lZqegYxx2vkSgGWcmJor2d+8Qiv3t5HPrZcKrSnWdWvpZ9IPA8iT6Yl9lmk9cmoVcB9mXklbhm0fs2/S8vvyrCt7GO0PyIyQ2uGiQIBbIZ0QIDAQABo1AwTjAdBgNVHQ4EFgQU/Ji8BRdqF54yhOXkFxQgpeePUpYwHwYDVR0jBBgwFoAU/Ji8BRdqF54yhOXkFxQgpeePUpYwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEAeN95smuD4mG9zqAn7r1/FTt2OkTxofj7Q9x5ccoLDYJmBv8whbs0/oF0NOYwdsLJirrF0xuWksWvMFpPRJiNe/4c8nYPdPDaUsxcS2fesvvBL5Dw45J6RBIAFKNyoC9wtwtPR88oes82y7WlrgvML83bC9B5cB+HnJzPoWPArgUvPZeZxcQw3Vq088axdyOZBV27rWNKNCFWKve+TF+vt3zD0FeDOYCTY94HRfRzjKimRadrnEl4+w4j+dYMjwuy4CEFSwW7pb/AntWTcjQWBTuWyqvNTIG9+Vchz+YjRZG1P/AInkl4J/QmS1cvCN2zKVFyZS5DdlIX1wvsI93C3A==
13 tls.key: MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDDGHjmfEGTdE4PUOXo1Zr48aBBZy3Lcxy7ntHI0VNDYw45nSXneQwv1y4tq7g4mqTvK8jqsqG00/mQw3MWt2uwvlxfjjAi07dcDYa07uvu3s+tPCgOyQapCLPTIPDRhrVOmQ4VsID1WmGiNccAvvuzZhQbWxms5JRTRIvcfS/zFScoiJQ/NELMGoYVR5HvMO4BMVBuOuQdRaI8hD3/ufhhWPfkKEeFZyjiS4/hEvqXmVmp6BjHHa+RKAZZyYmivZ37xCK/e3kc+tlwqtKdZ1a+ln0g8DyJPpiX2WaT1yahVwH2ZeSVuGbR+zb9Ly+/KsK3sY7Q/IjJDa4aJAgFshnRAgMBAAECggEAKFAYO1gVnMh9kMCgoTnyKdqTyK/vUIjauRIaOyq1z8jaGaGVQX1LvV7zVdCT4m5iAmHDxGtg6qKagQVB9MG16PGM2NnirG+fBdBts1ljOxqjQyKZDGURkUARGGFIIaN6N2F8/ZJZM1mXrxL5qffMvscrBHQQnB8nXwVc+RSNIecx7UQ1nGjhfabfywwVRT8PpjxKN35+bbFUEKPPf4sh3hf7B7+aZZep7Y32AXUtJUH8MKXo98QJ22kZja4zZI96O/q2s10CXv13x7FHOlaNtxha5qWW7lynWm4q7dKvZ0gF2Yd59/Nry3p6oGGAkBcDTR9T11BBEYMoQYx1BYdKoQKBgQD+RRbKQq8b24zrPPU3jFANDG9IKyjMEjdxQzPUgNjEXKdwA/Ge37Byzgjkf2bWPUCJb7Gzt6PHEnYHTxP1zWc1iM0r10qRHI5+J+dFtaleJdzm/sRiIta5QVLuwy+giKFdmbwA1d4Frl93DivexFj153LRCHsHJcLWK15GwC1IXQKBgQDEbE7WaePmzoTOV2XRfrykNiEv7U7acy8gfXTbT5HRIF89GJyMpYYF8e6+S/K3/HKSP2PsWDz35K8ax0OQrk2LvAe9DxA+sjNwxnTam8oRmDG9xoPD8VvuLRivUVxzftcxxgKindZNC78F3NzPRGcKeeq2jLqqUvIJQlpoC1NwBQKBgCl0oDOXza7wC7iqtpw43zBRb69Hgh5LdgicWU3zN+RD6vSjX/h0JfOBzgdbEiwpzmTZ9hIEBcrGIsIsTWfM9l/PDwxvzHN+QWkmHlnKNXPpHmv265PIdFO958SPxCsbO5vkHbfRJqKsfFoP0G1Ae/STqK+V/2D58hsy9Or6GCftAoGBAJeVPgIaFda46aSTre/ObqYLX/Esof3Thjr8loHpFg7dfKIZrDaeRp+v5R7WXam/GGvkn6h1MBfeU4PG4010NkPwB8jPJyo7O5d8kBFkyLxrR3e9C1LboKZeBv7FOyOmb0vqE36LcCZlOjW8DGunzh03mPrn/+YRvNeIbVx94RZBAoGBAIpirteUaXDZWTUH2i0uPrBeVYMJQWZGu4BCqnAVCP/wWERY2O7tPgUSRyd5Alg0VpmU0tkmaWj7Wejbs9KYjNNvLfmleR771aIgE/cL4Lp3ijvSHaQEFPob3HKoC0LR2Cw0jH6wX1B1MT5ymIIlXYn3aAmu790HbwySwjrxkmAY
1 apiVersion: extensions/v1beta1
2 kind: Ingress
3 metadata:
4 name: mywebsite-ingress-tls
5 spec:
6 tls:
7 - hosts:
8 - mywebsite.com
9 secretName: mywebsite-ingress-secret
10 rules:
11 - host: mywebsite.com
12 http:
13 paths:
14 - path: /demo
15 backend:
16 serviceName: myweb
17 servicePort: 8080
3.3 多域名TLS设置
1 [req]
2 req_extensions = v3_req
3 distinguished_name = req_distinguished_name
4 [req_distinguished_name]
5 [ v3_req ]
6 basicConstraints = CA:FALSE
7 keyUsage = nonRepudiation, digitalSignature, keyEncipherment
8 subjectAltName = @alt_names
9 [alt_names]
10 DNS.1 = mywebsite.com
11 DNS.2 = mywebsite2.com
[root@k8smaster01 study]# openssl req -x509 -new -nodes -key ca.key -days 3650 -out ca.crt -subj "/CN=mywebsite.com" #生成自签名CA证书
[root@k8smaster01 study]# openssl genrsa -out ingress.key 2048
[root@k8smaster01 study]# openssl req -new -key ingress.key -out ingress.csr -subj "/CN=mywebsite.com" -config openssl.cnf #基于openssl.cnf和CA证书生成ingress SSL证书
027.掌握Service-Ingress使用的更多相关文章
- 十九、Service Ingress
Service Ingress Ingress-Nginx github 地址:https://github.com/kubernetes/ingress-nginx Ingress-Nginx 官方 ...
- K8S原来如此简单(四)Service+Ingress
上一篇我们通过deployment实现了pod的横向扩展,但是仍然不能负载,也不能对外提供服务,现在我们来看看如何通过k8s实现负载与外网访问 Service service为一组pod提供一个统一的 ...
- 007.kubernets的headless service配置和ingress的简单配置
前面配置了servcie的nodepoint和clusterIP附在均衡 一 headless service配置 1.1 默认下的DNS配置 [root@docker-server1 deploym ...
- kubernetes nginx ingress 使用记录
前言 ingress是一种可以暴露k8s集群内部service的方式,用户编辑配置文件定义一个ingress资源即可实现外部网络访问内网service. ingress controller是来管理所 ...
- kubernetes-核心资源之Ingress
1.Ingress 在Kubernetes中,服务和Pod的IP地址仅可以在集群网络内部使用,对于集群外的应用是不可见的.为了使外部的应用能够访问集群内的服务,在Kubernetes中可以通过Node ...
- Ingress介绍与安装配置
在 Kubernetes 集群中,Ingress是授权入站连接到达集群服务的规则集合,为您提供七层负载均衡能力.您可以给 Ingress 配置提供外部可访问的 URL.负载均衡.SSL.基于名称的虚拟 ...
- Kubernetes Ingress管理
目录 Ingress介绍 1.Pod漂移问题 2.端口管理问题 3.域名分配及动态更新问题 Nginx Ingress配置 1.部署默认后端 2.部署Ingress Controller 3.部署In ...
- kubernetes对象之Ingress
系列目录 概述 向外网暴露集群内服务,以使客户端能够访问,有以下几种方法,本文重点描述Ingress. LoadBalancer LoadBalancer一般由云服务供应商提供或者用户自定义,运行在集 ...
- Kubernetes 系列(三):Kubernetes使用Traefik Ingress暴露服务
一.Kubernetes 服务暴露介绍 从 kubernetes 1.2 版本开始,kubernetes提供了 Ingress 对象来实现对外暴露服务:到目前为止 kubernetes 总共有三种暴露 ...
- [系统集成] 基于Kubernetes 部署 jenkins 并动态分配资源
基于kubernetes 部署 jenkins master 比较简单,难点是为 jenkins 动态分配资源.基于kubernetes 为 jenkins 动态分配资源需要实现下述功能: 资源分配: ...
随机推荐
- 2019ICPC南京网络赛B super_log(a的b塔次方)
https://nanti.jisuanke.com/t/41299 分析:题目给出a,b,mod求满足条件的最小a,由题目的式子得,每次只要能递归下去,b就会+1,所以就可以认为b其实是次数,什么的 ...
- C#常用到的命令及常用控件的属性
Application.Exit()应用程序退退出 this.Close()当前窗口退出 int h = DateTime.Now.Hour; //获取当前时间的小时部分 int m = D ...
- MS15-020 文件共享漏洞利用
Metasploit MS15-020漏洞利用 环境: 共享机/受害者:windows xp IP:192.168.222.1 攻击机:kali linux IP:192.168.10.1 msfco ...
- mysqli存储过程
<?php$link = mysqli_connect('localhost','root','','chinatupai'); $sql = "call getEmail('000 ...
- [LC] 253. Meeting Rooms II
Given an array of meeting time intervals consisting of start and end times [[s1,e1],[s2,e2],...] (si ...
- OpenCV 对两幅图像求和(求混合(blending))
#include <cv.h> #include <highgui.h> #include <iostream> using namespace cv; int m ...
- chop|divorce|harsh|mutual|compel|
这个英音很special VERB 砍;剁;劈;切If you chop something, you cut it into pieces with strong downward movement ...
- valgrind 的使用简介
zz自 http://blog.csdn.net/destina/article/details/6198443 感谢作者的分享! 一 valgrind是什么? Valgrind是一套Linux下 ...
- JVM类文件结构
作为一名Java后台开发的程序员, 深入理解JVM, 重要性不言而喻, 这篇文章主要是记录JVM类文件结构相关知识. 2. 实例 这部分比较抽象, 所以以实例的形式来学习. 这部分作为资料, 以便后面 ...
- Python如何让字典保持有序
问题: Python如何让字典保持有序 ? 解决方案: 使用collections.OrderedDict代替Dict. 验证程序: from collections import OrderedDi ...