k8s nginx ingress配置TLS
在没有配置任何nginx下,k8s的nginx默认只支持TLS1.2,不支持TLS1.0和TLS1.1
默认的 nginx-config(部分可能叫 nginx-configuration)的配置如下:
apiVersion: v1
data:
allow-backend-server-header: 'true'
enable-underscores-in-headers: 'true'
generate-request-id: 'true'
http-redirect-code: ''
ignore-invalid-headers: 'true'
max-worker-connections: ''
proxy-body-size: 20m
proxy-connect-timeout: ''
reuse-port: 'true'
server-tokens: 'false'
ssl-redirect: 'false'
worker-cpu-affinity: auto
kind: ConfigMap
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: >
{"apiVersion":"v1","data":{"allow-backend-server-header":"true","enable-underscores-in-headers":"true","generate-request-id":"true","ignore-invalid-headers":"true","max-worker-connections":"","proxy-body-size":"20m","proxy-connect-timeout":"","reuse-port":"true","server-tokens":"false","ssl-redirect":"false","worker-cpu-affinity":"auto"},"kind":"ConfigMap","metadata":{"annotations":{},"labels":{"app":"ingress-nginx"},"name":"nginx-configuration","namespace":"kube-system"}}
labels:
app: ingress-nginx
name: nginx-configuration
namespace: kube-system
selfLink: /api/v1/namespaces/kube-system/configmaps/nginx-configuration
看了下官方的文档,如果需要支持TLS1.0和TLS1.1需要改下 nginx-config 同时重启下容器即可
To provide the most secure baseline configuration possible,
nginx-ingress defaults to using TLS 1.2 only and a secure set of TLS ciphers.
The default configuration, though secure, does not support some older browsers and operating systems. For instance, TLS 1.1+ is only enabled by default from Android 5.0 on. At the time of writing, May , approximately % of Android devices are not compatible with nginx-ingress's default configuration. To change this default behavior, use a ConfigMap. A sample ConfigMap fragment to allow these older clients to connect could look something like the following:
kind: ConfigMap
apiVersion: v1
metadata:
name: nginx-config
data:
ssl-ciphers: "ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA"
ssl-protocols: "TLSv1 TLSv1.1 TLSv1.2"
为了避免影响到之前的配置,切勿直接复制这个yaml配置替换你的配置!!!
在你原有的配置上加上 ssl-ciphers 和 ssl-protocols 配置即可
apiVersion: v1
data:
allow-backend-server-header: 'true'
enable-underscores-in-headers: 'true'
generate-request-id: 'true'
http-redirect-code: ''
ignore-invalid-headers: 'true'
max-worker-connections: ''
proxy-body-size: 20m
proxy-connect-timeout: ''
reuse-port: 'true'
server-tokens: 'false'
ssl-ciphers: >-
ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA
ssl-protocols: TLSv1 TLSv1. TLSv1.
ssl-redirect: 'false'
worker-cpu-affinity: auto
kind: ConfigMap
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: >
{"apiVersion":"v1","data":{"allow-backend-server-header":"true","enable-underscores-in-headers":"true","generate-request-id":"true","ignore-invalid-headers":"true","max-worker-connections":"","proxy-body-size":"20m","proxy-connect-timeout":"","reuse-port":"true","server-tokens":"false","ssl-redirect":"false","worker-cpu-affinity":"auto"},"kind":"ConfigMap","metadata":{"annotations":{},"labels":{"app":"ingress-nginx"},"name":"nginx-configuration","namespace":"kube-system"}}
labels:
app: ingress-nginx
name: nginx-configuration
namespace: kube-system
selfLink: /api/v1/namespaces/kube-system/configmaps/nginx-configuration
加上配置之后呢,需要重启下容器 nginx-ingress
验证,能正常相应即可:
$ curl -v --tlsv1. https://test.com
$ curl -v --tlsv1. https://test.com
$ curl -v --tlsv1. https://test.com
下图是成功访问的响应:
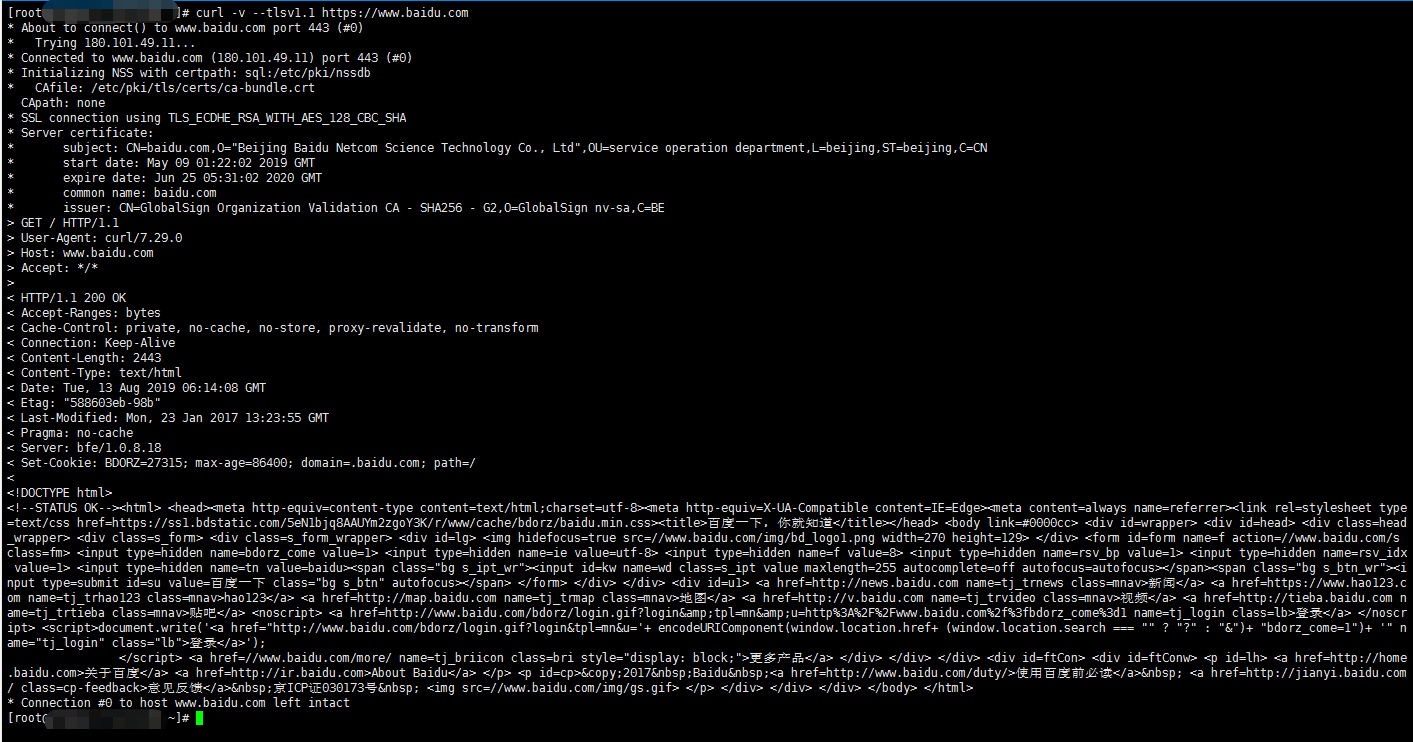
下图是错误的响应:

参考文档:https://kubernetes.github.io/ingress-nginx/user-guide/tls/#legacy-tls
k8s nginx ingress配置TLS的更多相关文章
- Kubernetes 部署 Nginx Ingress Controller 之 nginxinc/kubernetes-ingress
更新:这里用的是 nginxinc/kubernetes-ingress ,还有个 kubernetes/ingress-nginx ,它们的区别见 Differences Between nginx ...
- 微信小程序Nginx环境配置
环境配置概述 主要内容: SSL免费证书申请步骤 Nginx HTTPS 配置 TLS 1.2 升级过程 微信小程序要求使用 https 发送请求,那么Web服务器就要配置成支持 https,需要先申 ...
- Nginx Ingress 高并发实践
概述 Nginx Ingress Controller 基于 Nginx 实现了 Kubernetes Ingress API,Nginx 是公认的高性能网关,但如果不对其进行一些参数调优,就不能充分 ...
- [转帖]在 k8s 中通过 Ingress 配置域名访问
在 k8s 中通过 Ingress 配置域名访问 https://juejin.im/post/5db8da4b6fb9a0204520b310 在上篇文章中我们已经使用 k8s 部署了第一个应用,此 ...
- 见异思迁:K8s 部署 Nginx Ingress Controller 之 kubernetes/ingress-nginx
前天才发现,区区一个 nginx ingress controller 竟然2个不同的实现.一个叫 kubernetes/ingress-nginx ,是由 kubernetes 社区维护的,对应的容 ...
- k8s的ingress使用
ingress 可以配置一个入口来提供k8s上service从外部来访问的url.负载平衡流量.终止SSL和提供基于名称的虚拟主机. 配置ingress的yaml: 要求域名解析无误 要求servic ...
- Kubernetes 使用 ingress 配置 https 集群(十五)
目录 一.背景 1.1 需求 1.2 Ingress 1.3 环境介绍 二.安装部署 2.1.创建后端 Pod 应用 2.2 创建后端 Pod Service 2.3.创建 ingress 资源 2. ...
- 11. Ingress及Ingress Controller(主nginx ingress controller)
11. Ingress,Ingress Controller拥有七层代理调度能力 什么是Ingress: Ingress是授权入站连接到达集群服务的规则集合 Ingress是一个Kubernetes资 ...
- k8s系列---ingress资源和ingress-controller
https://www.cnblogs.com/zhangeamon/p/7007076.html http://blog.itpub.net/28916011/viewspace-2214747/ ...
随机推荐
- 查询sql server占用内存的情况
se master go select * from sysperfinfo where counter_name like '%Total Server Memory (KB)%' go
- zabbix 4.2 安装教程
1.我这里使用的是ali的yum源 #wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-7 ...
- 【LeetCode】动态规划(下篇共39题)
[600] Non-negative Integers without Consecutive Ones [629] K Inverse Pairs Array [638] Shopping Offe ...
- java.util.Date 与 java.sql.Date 相关知识点解析
问:java.sql.Date 和 java.util.Date 有什么区别? 答:这两个类的区别是 java.sql.Date是针对 SQL 语句使用的,它只包含日期而没有时间部分,一般在读写数 ...
- YottaChain主网全面上线预示商业应用的落地区块链云存储不一样的云
Yottachain存储网12月24日平安夜全面启动,意味着全球首个可商用的区块链存储公链全面落地.对于数据存储来说,小到我们个人的照片文档,大到政企机构数据库资料,都是互联网生活中如影随形的标配. ...
- java中super的用法总结
package com.ssm.java; /** * Super * usage1:super. 直接去调用父类的方法和属性. * usage2:放在构造器中的第一位,代表引用父类的构造器. */ ...
- html简单标签代码
html简单标签代码demo <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "ht ...
- hypermesh生成MNF柔性体
软件HyperworksX 2019: 该版本默认的是optistruct模板 1.导入几何→分网→材料定义(注意单位,建议统一mks单位制)→定义单元属性→创建刚性单元: 2.创建load coll ...
- IntelliJ IDEA中创建xml文件
1.file—setting,左上角输入template, 2.在左侧栏找到File And Code Templates 3.中间选中Files 4.点击+号,添加模板 5.输入模板名字:Nam ...
- Python中import的使用方法
源文出处: "import"的本质参照: Python中import机制 python导入自定义模块和包
