Wifite v2 is now available
Wifite v2 is now available
What's new in this version:
- support for cracking WPS-encrypted networks (via reaver)
- 2 new WEP attacks
- more accurate WPA handshake capture
- various bug fixes
Version 2 does not include a GUI, so everything must be done at the command-line.
mention in the New York Times
Wifite was mentioned in the New York Times' article "New Hacking Tools Pose Bigger Threats to Wi-Fi Users" from February 16, 2011. Here is a link to the article.
introduction
Designed and tested on Linux; works with Backtrack 5, BlackBuntu, BackBox, and Pentoo! Linux only; no windows or OSX support (but you're welcome to try).
purpose
To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Wifite aims to be the "set it and forget it" wireless auditing tool.
features
- sorts targets by signal strength (in dB); cracks closest access points first
- automatically de-authenticates clients of hidden networks to reveal SSIDs
- numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- customizable settings (timeouts, packets/sec, etc)
- "anonymous" feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- all captured WPA handshakes are backed up to wifite.py's current directory
- smart WPA de-authentication; cycles between all clients and broadcast deauths
- stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- displays session summary at exit; shows any cracked keys
- all passwords saved to cracked.txt
- built-in updater: ./wifite.py -upgrade
requirements
- linux operating system (confirmed working on Backtrack 5, BackBox, BlackBuntu, Pentoo, Ubuntu 8.10 (BT4R1), Ubuntu 10.04, Debian 6, Fedora 16)
- tested working with python 2.6.x, and python 2.7.x,
- wireless drivers patched for monitor mode and injection. Most security distributions (Backtrack, BlackBuntu, etc) come with wireless drivers pre-patched,
- aircrack-ng (v1.1) suite: available via apt: apt-get install aircrack-ng or at the aircrack-ng website,
suggested applications
- reaver, for attacking WPS-encrypted networks
- pyrit, cowpatty, tshark: not required, but help verify WPA handshake captures
For help installing any of these programs, see the installation guide (hosted on github)
execution
download the latest version:
wget -O wifite.py http://wifite.googlecode.com/svn/trunk/wifite.py
change permissions to executable:
chmod +x wifite.py
execute:
python wifite.py
or, to see a list of commands with info:
./wifite.py -help
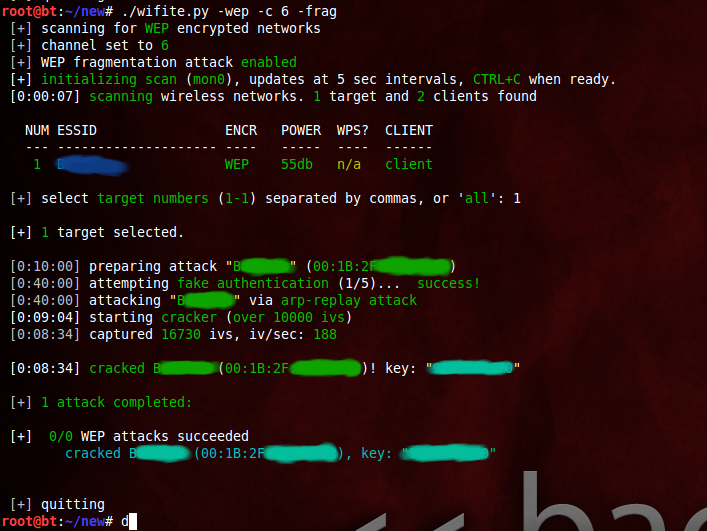
screenshots
successful WEP attack (after 90 seconds):
successful WPS attacks (after 17 hours):

examples
the program contains lots of interactivity (waits for user input). these command-line options are meant to make the program 100% automated -- no supervision required.
to crack all WEP access points:
./wifite.py -all -wep
to crack all WPS access points with signal strength greater than (or equal to) 50dB:
./wifite.py -p 50-wps
to attack all access points, use 'darkc0de.lst' for cracking WPA handshakes:
./wifite.py -all --dict /pentest/passwords/wordlists/darkc0de.lst
to attack all WPA access points, but do not try to crack -- any captured handshakes are saved automatically:
./wifite.py -all -wpa --dict none
to crack all WEP access points greater than 50dB in strength, giving 5 minutes for each WEP attack method, and send packets at 600 packets/sec:
./wifite.py --pow 50-wept 300-pps 600
to attempt to crack WEP-encrypted access point "2WIRE752" endlessly -- program will not stop until key is cracked or user interrrupts with ctrl+C):
./wifite.py -e "2WIRE752"-wept 0
Wifite v2 is now available的更多相关文章
- Wifite.py 修正版脚本代码
Kali2.0系统自带的WiFite脚本代码中有几行错误,以下是修正后的代码: #!/usr/bin/python # -*- coding: utf-8 -*- """ ...
- 自动化无线网破解工具wifite2
自动化无线网破解工具wifite2 wifite是一款自动化wifi密码破解工具,特点是支持多个wep.wpa加密的wifi网络,不支持windows和osx. wifite的特点是可以同时攻击多个采 ...
- 如何搭建自己的SPRING INITIALIZR server
这两天在慕课学Spring boot ,用idea通过spring initializr新建项目 即使用代理连不上.无奈. 参考了 GitHub - spring-io/initializr: A w ...
- Atitit. 破解 拦截 绕过 网站 手机 短信 验证码 方式 v2 attilax 总结
Atitit. 破解 拦截 绕过 网站 手机 短信 验证码 方式 v2 attilax 总结 1. 验证码的前世今生11.1. 第一代验证码 图片验证码11.2. 第二代验证码 用户操作 ,比如 ...
- [Android]Android端ORM框架——RapidORM(v2.1)
以下内容为原创,欢迎转载,转载请注明 来自天天博客:http://www.cnblogs.com/tiantianbyconan/p/6020412.html [Android]Android端ORM ...
- [Android]Android端ORM框架——RapidORM(v2.0)
以下内容为原创,欢迎转载,转载请注明 来自天天博客:http://www.cnblogs.com/tiantianbyconan/p/5626716.html [Android]Android端ORM ...
- JuCheap V2.0响应式后台管理系统模板正式发布beta版本
JuCheap V1.* 查看地址: http://blog.csdn.net/allenwdj/article/details/49155339 经过半年的努力,JuCheap后台通用响应式管理后台 ...
- Atitit. 项目文档目录大纲 总集合 v2
Atitit. 项目文档目录大纲 总集合 v2 -----Atitti.原有项目源码的架构,框架,配置与环境说明 v3 q511 -----Atitit.开发环境 与 工具 以及技术框架 以及 注意 ...
- python gettitle v2.0
#!/usr/bin/env python # coding=utf-8 import threading import requests import Queue import sys import ...
随机推荐
- css3创建一个上下线性渐变色背景的div
<!DOCTYPE HTML> <html> <head> <meta charset="utf-8"> <title> ...
- [3] 智能指针std::auto_ptr
[1]std::auto_ptr 对于编译器来说,智能指针实质是一个栈对象,而并非指针类型. 智能指针通过构造函数获取堆内存的管理所有权,而在其生命期结束时,再通过析构函数释放由它所管理的堆内存. 所 ...
- :first-child 类似的 :first 匹配第一个元素,但是:first-child选择器可以匹配多个:即为每个父级元素匹配第一个子元素。这相当于:nth-child(1)
描述: 在每个 ul 中查找第一个 li HTML 代码: <ul> <li>John</li> <li>Karl</li> <li& ...
- Ugly Number
public class Solution { public bool IsUgly(int num) { ) return false; ) return true; *==num){ num = ...
- asp.net 之 购物车
using System; using System.Collections.Generic; using System.Linq; using System.Web; using System.We ...
- WF4.0入门(一)
WF的全称是Windows Workflow Foundation .这是 Microsoft 快速构建基于工作流的应用程序的编程模型.引擎和工具.NET Framework 4 中这个 WF 版本更 ...
- 微信JS SDK PHP Demo
一.JSSDK类定义 <?php class JSSDK { private $appId; private $appSecret; public function __construct($a ...
- Going from u to v or from v to u?_POJ2762强连通+并查集缩点+拓扑排序
Going from u to v or from v to u? Time Limit: 2000MS Memory Limit: 65536K Description I ...
- noi 4977 怪盗基德的滑翔翼
题目链接: http://noi.openjudge.cn/ch0206/4977/ LIS http://paste.ubuntu.com/23406594/
- Codeforces Round #316 (Div. 2) D. Tree Requests dfs序
D. Tree Requests time limit per test 2 seconds memory limit per test 256 megabytes input standard in ...
