Lab 1-2
Analyze the file Lab01-02.exe.
Questions and Short Answers
Upload the Lab01-02.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
A: As of this writing, the file matches 3 of 41 antivirus signatures.

注:在写这篇博客时的数据是 69 反病毒引擎里面 43 个是反病毒签名。
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
A: There are several indications that the program is packed with UPX. You can unpack it by downloading UPX and running
upx –d.Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
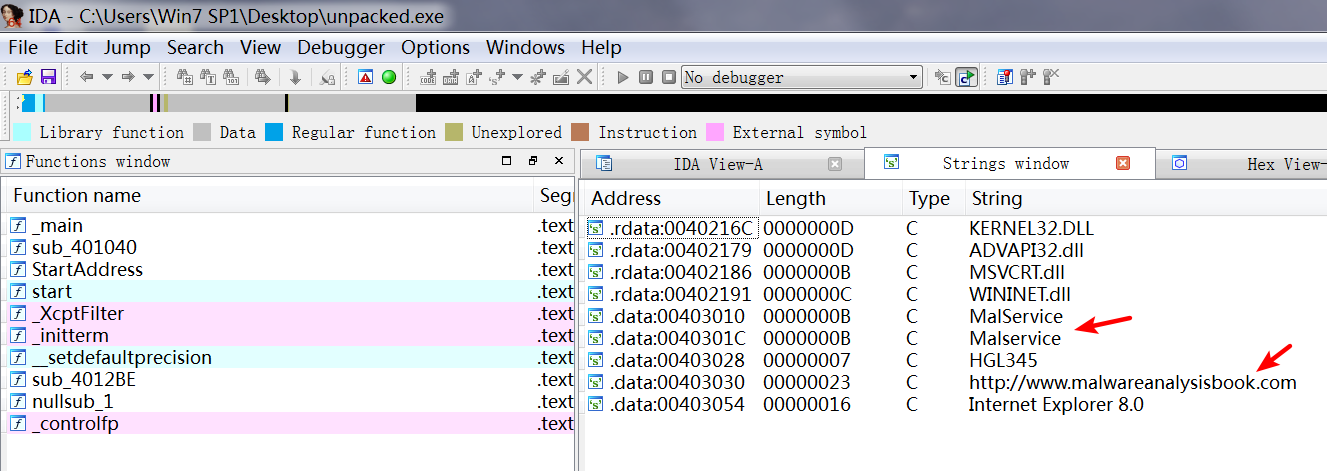
A: After unpacking the file, you’ll see that the most interesting imports are CreateService, InternetOpen, and InternetOpenURL.
What host- or network-based indicators could be used to identify this malware on infected machines?
A: You should check infected machines for a service called Malservice and for network traffic to http://www.malwareanalysisbook.com/.
Detailed Analysis
When analyzing Lab 1-2, we upload the file to VirusTotal.com and see that it matches at least three virus signatures. One antivirus engine identifies it as a malicious downloader that downloads additional malware; the other two identify it as packed malware. This demonstrates the usefulness of VirusTotal.com. Had we used only one antivirus program to scan this file, we would probably not get any information.
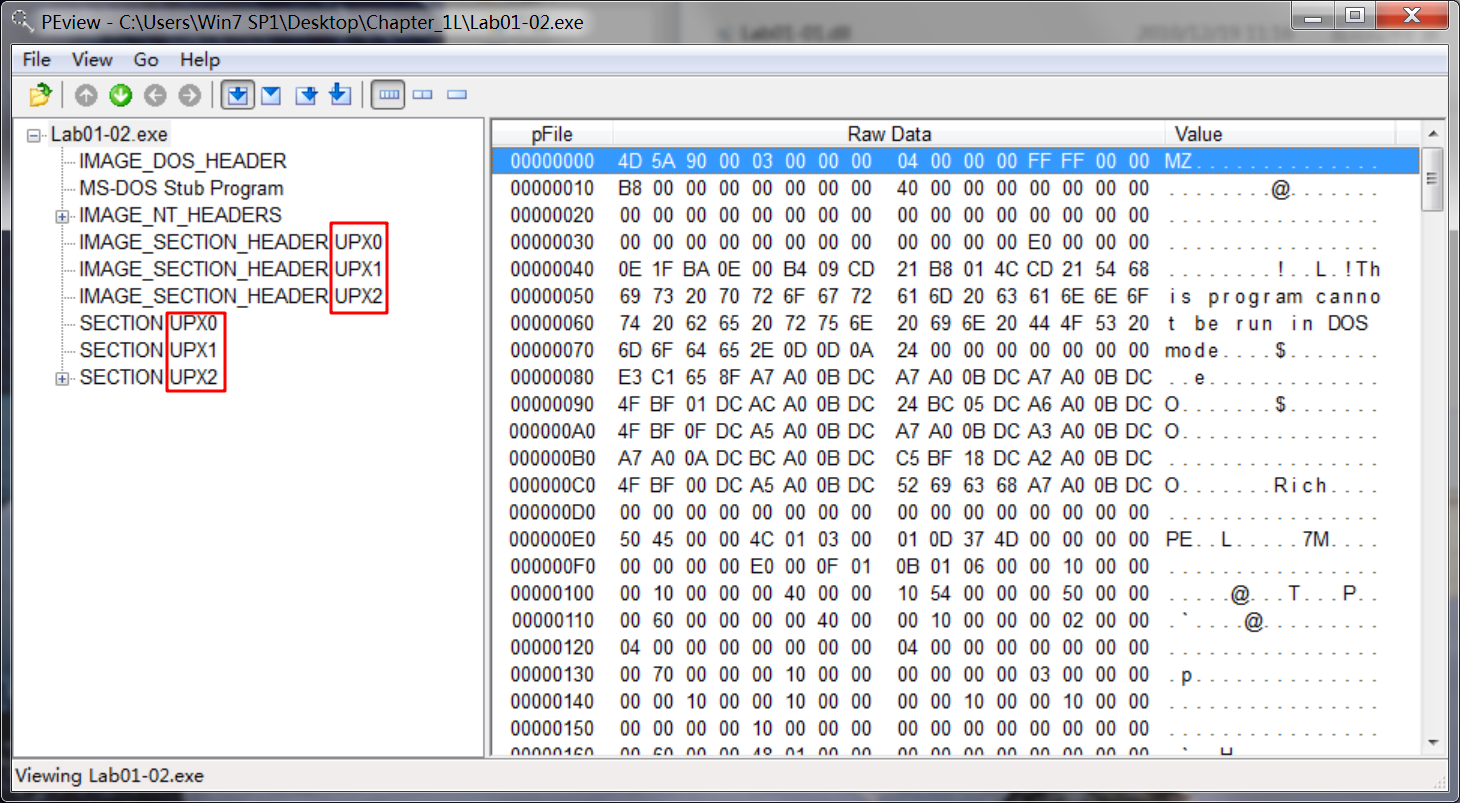
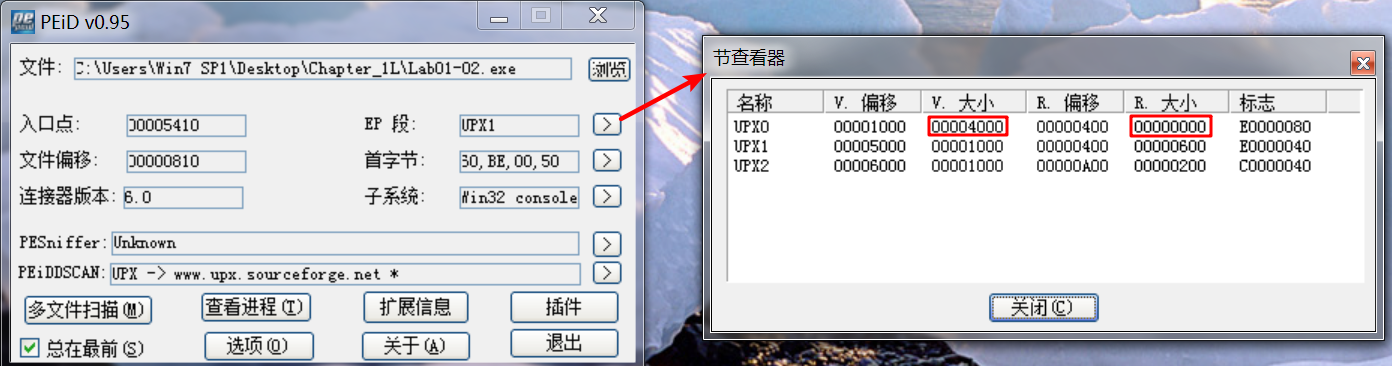
Upon opening the file with PEview, several indicators tell us that this file is packed. The most obvious indicators are sections named UPX0, UPX1, and UPX2—section names for UPX-packed malware. We could use PEiD to confirm the file’s packed nature, but it is not foolproof. Even if PEiD fails to identify the file as UPX-packed, notice the relatively small number of imports and that the first section, UPX0, has a virtual size of 0x4000 but a raw
data size of 0. UPX0 is the largest section, and it’s marked executable, so it’s probably where the original unpacked code belongs.

Having identified the program as packed, we can unpack it by downloading UPX from http://upx.sourceforge.net/ and running the following command:
upx -o newFlilename -d originalFilenameThe -d option says decompress the file, and the -o option specifies the output filename.
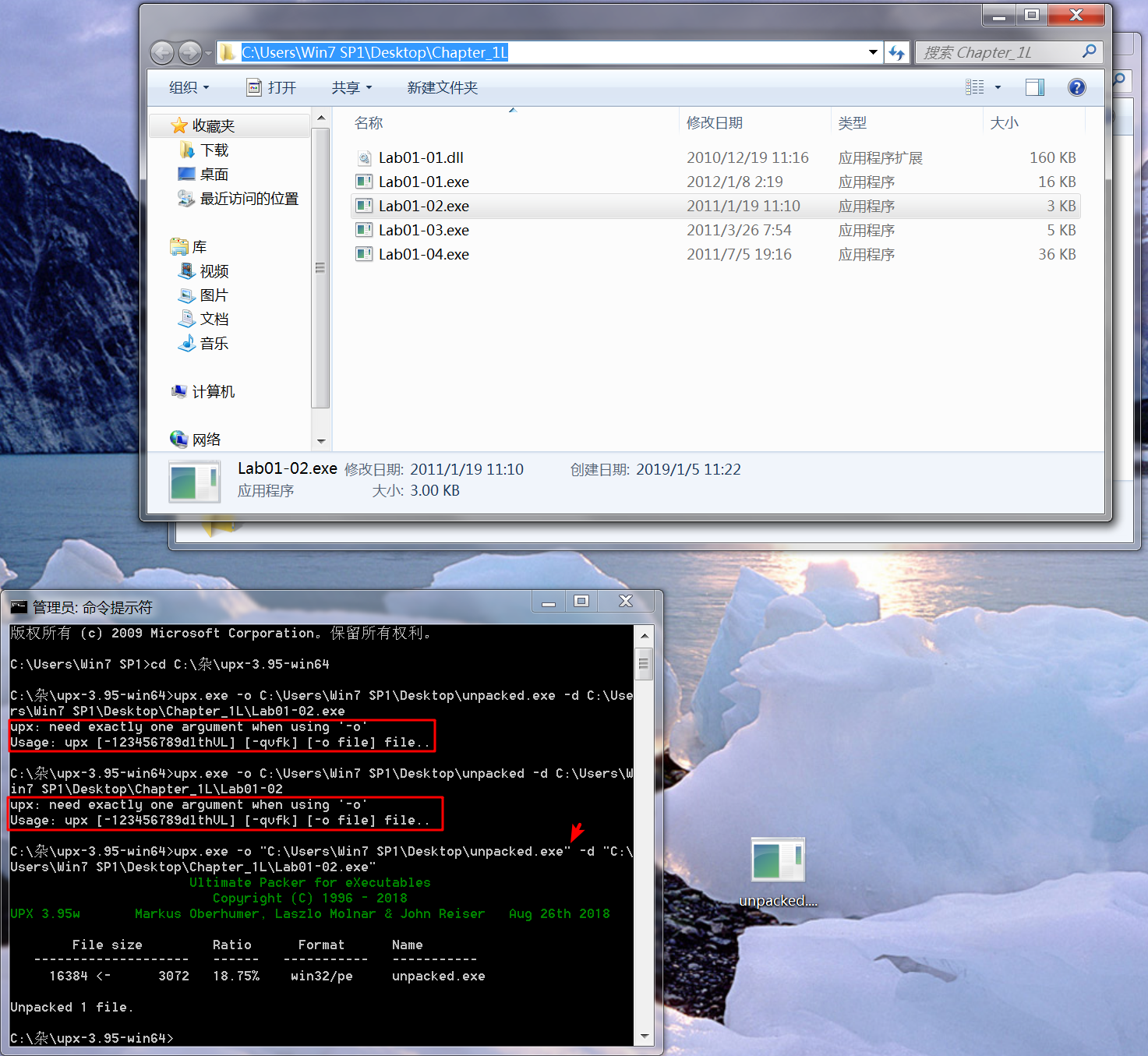
注:newFilename, originalFilename 记得加双引号(" "),否则会报错。
After unpacking, we look at the imports sections and the strings. The imports from kernel32.dll and msvcrt.dll are imported by nearly every program, so they tell us little about this specific program. The imports from wininet.dll tell us that this code connects to the Internet (InternetOpen and InternetOpenURL), and the import from advapi32.dll (CreateService) tell us that the code creates a service. When we look at the strings, we see www.malwareanalysisbook.com, which is probably the URL opened by InternetOpenURL as well as by Malservice, which could be the name of the service that is created.
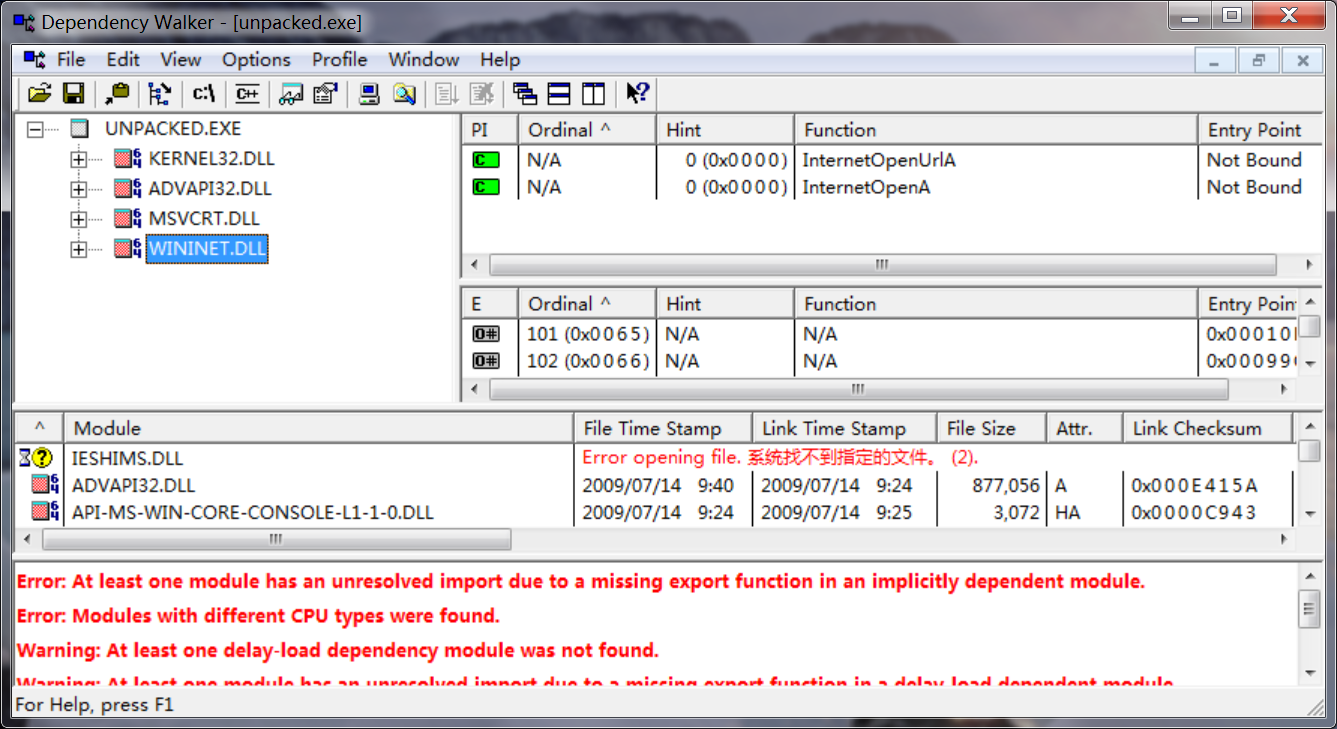
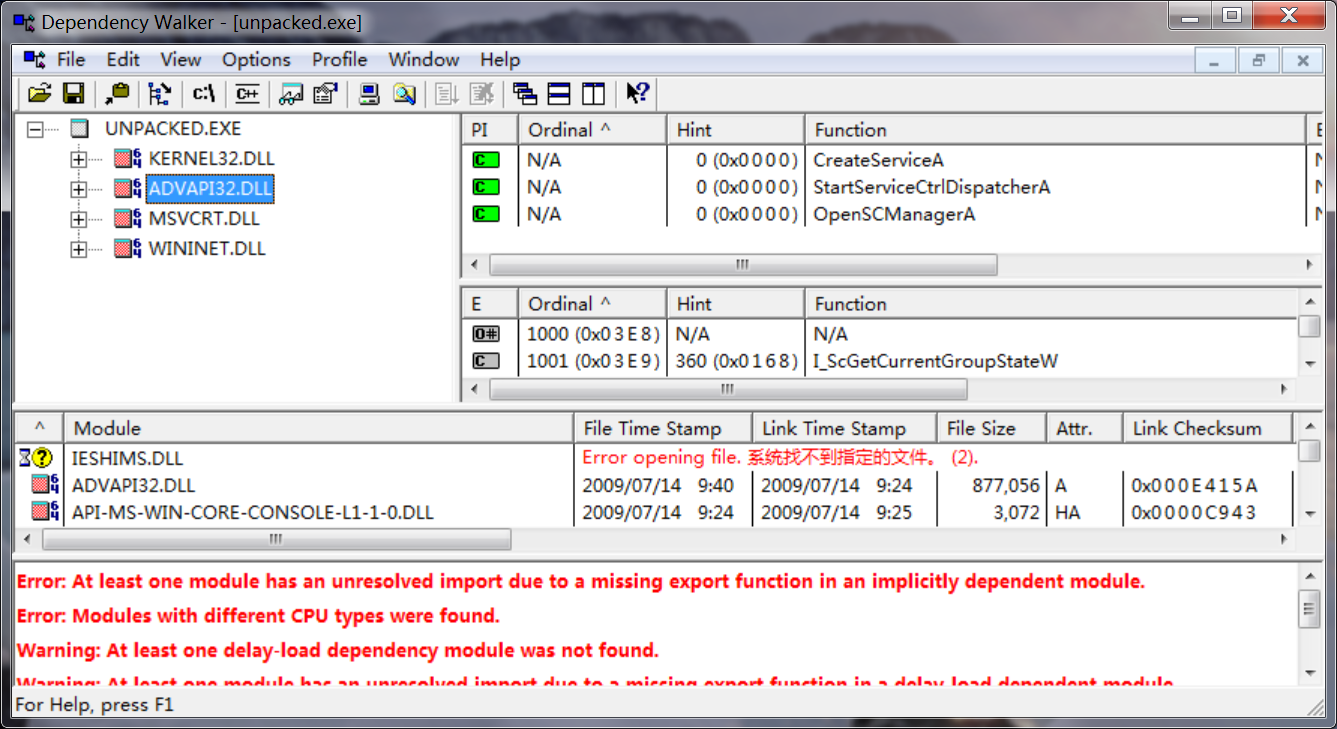
IDA -> View -> Opensubviews -> Strings :
We can’t be sure what this program is doing, but we’ve found some indicators to help search for this malware across a network.
Preference
Lab 1-2的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- topcoder srm 550 div1
problem1 link 因为数据比较小,直接开一个二维数组记录哪些格子已经遍历,哪些还没有.进行模拟即可. problem2 link 模拟一些小数据,可以发现,AB的形状以及要求的区间是下面的样 ...
- 用uniGUI做B/S下业务系统的产品原型体验
从10月份到重庆工作后,一直忙于工作,感兴趣的几个方面的技术都处于暂停. 一个多月来,按照公司要求在做B/S集中式基卫产品的原型,主要是画原型图,开始是用Axure,弄来弄去感觉功能还是弱了些,尤其是 ...
- js插入排序
插入排序 平均时间复杂度O(n*n) 最差情况O(n*n) 最好情况O(n) 空间复杂度O(1) 稳定性:稳定 function insertSort (arr) { var len = arr.le ...
- Bytom交易说明(UTXO用户自己管理模式)
比原项目仓库: Github地址:https://github.com/Bytom/bytom Gitee地址:https://gitee.com/BytomBlockchain/bytom 该部分主 ...
- cron,linux定时脚本
Linux的cron和crontab Cron定时执行工具详解 Linux下的crontab定时执行任务命令详解 Linux上启动Cron任务 [linux]解析crontab cron表达式详解 c ...
- Leetcode118_Pascal's Triangle_Easy
Given a non-negative integer numRows, generate the first numRows of Pascal's triangle. In Pascal's t ...
- vue中click阻止事件冒泡,防止触发另一个事件
在使用el-upload组件时,在其中放置了一个删除按钮的图片. 当点击图片,本想只删除上传的视频,但是意外触发了el-upload中的事件 解决办法:用stop,结果只删除当前预览,不触发上传事件. ...
- Select2 添加默认值
折腾很久才解决问题 $.ajax({ url: '@Url.Action("GetSystemSzzdItem", "CangpinGushi")', type ...
- 生存分析与R--转载
生存分析与R 生存分析是将事件的结果和出现这一结果所经历的时间结合起来分析的一类统计分析方法.不仅考虑事件是否出现,而且还考虑事件出现的时间长短,因此这类方法也被称为事件时间分析(time-to-ev ...
- Mysql 函数使用记录(三)——UNIX_TIMESTAMP() 、UNIX_TIMESTAMP(date)
参考资料:https://dev.mysql.com/doc/refman/5.7/en/date-and-time-functions.html#function_unix-timestamp UN ...
