转:Uncovering Drupalgeddon 2(cve-2018-7600)漏洞深度解析(附漏洞利用代码地址)
转:https://research.checkpoint.com/uncovering-drupalgeddon-2/
By Eyal Shalev, Rotem Reiss and Eran Vaknin
Abstract
Two weeks ago, a highly critical (25/25 NIST rank) vulnerability, nicknamed Drupalgeddon 2 (SA-CORE-2018-002 / CVE-2018-7600), was disclosed by the Drupal security team. This vulnerability allowed an unauthenticated attacker to perform remote code execution on default or common Drupal installations.
Drupal is an open-source content management system (CMS) that is used by more than one million sites around the world (including governments, e-retail, enterprise organizations, financial institutions and more), all of which are vulnerable unless patched.
Until now details of the vulnerability were not available to the public, however, Check Point Research can now expand upon this vulnerability and reveal exactly how it works.
In brief, Drupal had insufficient input sanitation on Form API (FAPI) AJAX requests. As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication. By exploiting this vulnerability an attacker would have been able to carry out a full site takeover of any Drupal customer.
The vulnerability existed on all Drupal versions from 6 to 8, though has since been patched to those who manually update their site. In this document we will showcase real life attack scenarios around an out-of-the-box installation of Drupal’s flagship product, Drupal 8.
Technical Details
The Vulnerability
To provide some background, Drupal’s Form API was introduced in Drupal 6 and allowed alteration of the form data during the form rendering process. This revolutionized the way markup processing was done.
In Drupal 7 the Form API was generalized to what is now known as “Renderable Arrays”. This extended API is used to represent the structure of most of the UI elements in Drupal, such as pages, blocks, nodes and more.
Renderable arrays contain metadata that is used in the rendering process. These renderable arrays are a key-value structure in which the property keys start with a hash sign (#). Please see below for an example:
[
‘#type’ => ‘markup’,
‘#markup’ => ‘<em>some text</em>’,
‘#prefix’ => ‘<div>’,
‘#suffix’ => ‘</div>’
]
Drupal’s Patch
The patch that Drupal published adds a single class called RequestSanitizer with a stripDangerousValues method that unsets all the items in an input array for keys that start with a hash sign. This method sanitizes input data in $_GET, $_POST & $_COOKIES during the very early stages of Drupal’s bootstrap (immediately after loading the site configurations).
We assume that one of the reasons that the patch was done in this way was to make it harder to find and exploit the vulnerability.
Finding an Attack Vector
Because of the above we focused on forms that are exposed to anonymous users.
There are a few of those forms available, one of which is the user registration form. This form contains multiple fields, as can be seen in the screenshot below.
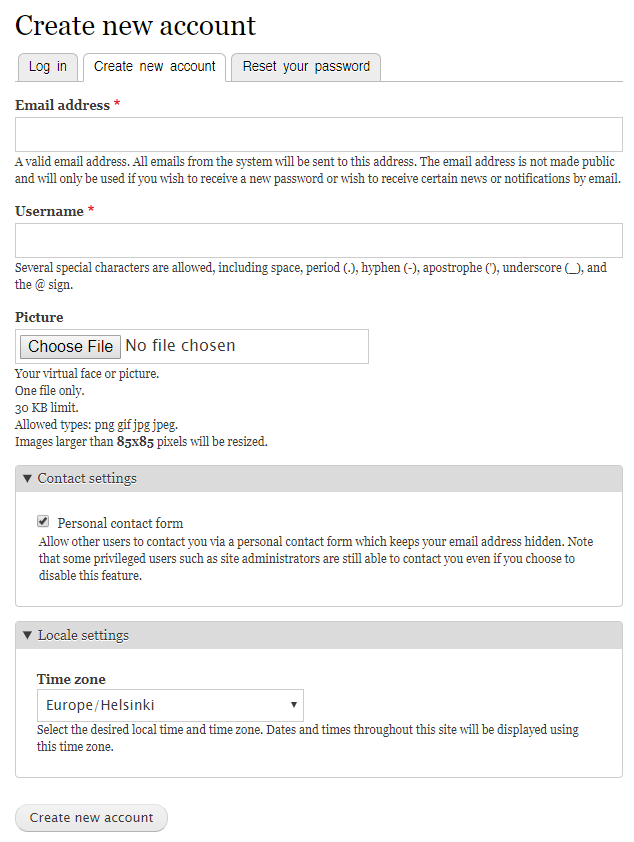
Figure 1: The Drupal registration form.
We knew that we needed to inject a renderable array somewhere in the form structure, we just had to find out where.
As it happens, the “Email address” field does not sanitize the type of input that it receives. This allowed us to inject an array to the form array structure (as the value of the email field).
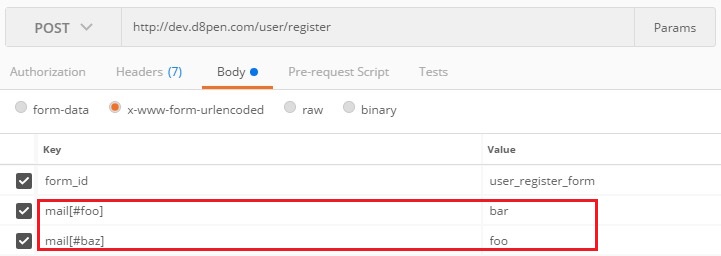
Figure 2: Injecting our renderable array into the mail input of the registration form.
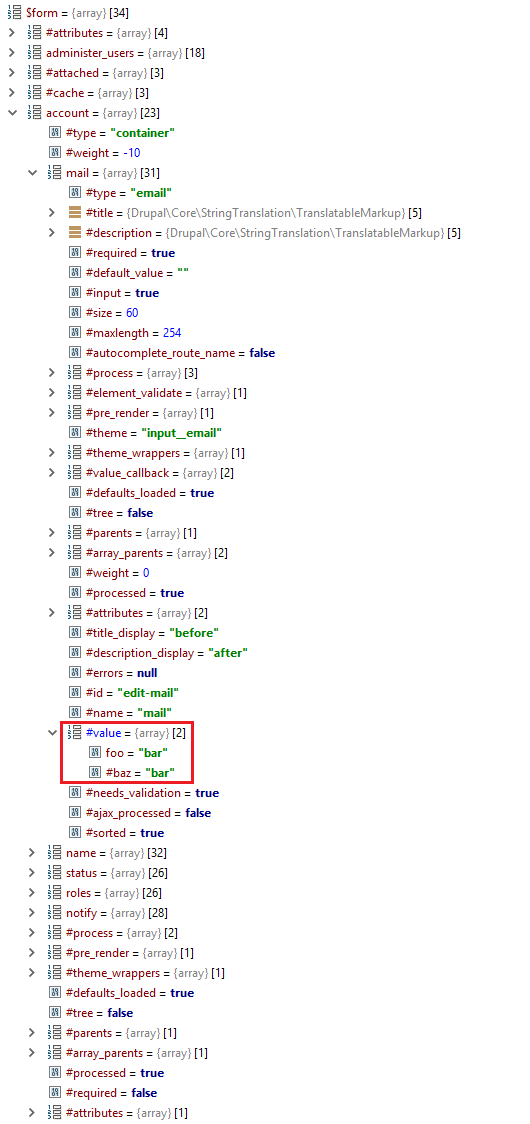
Figure 3: Example of injected form renderable array.
Now all we needed was for Drupal to render our injected array. Since Drupal treats our injected array as a value and not as an element, we needed to trick Drupal into rendering it.
The situations in which Drupal renders arrays are as follows:
- Page load
- Drupal AJAX API – i.e. when a user fills an AJAX form, a request is made to Drupal which renders an HTML markup and updates the form.
After investigating possible attack vectors surrounding the above functionalities, because of the post-submission rendering process and the way Drupal implements it, we came to the conclusion that an AJAX API call is our best option to leverage an attack.
As part of the user registration form, the “Picture” field uses Drupal’s AJAX API to upload a picture into the server and replace it with a thumbnail of the uploaded image.
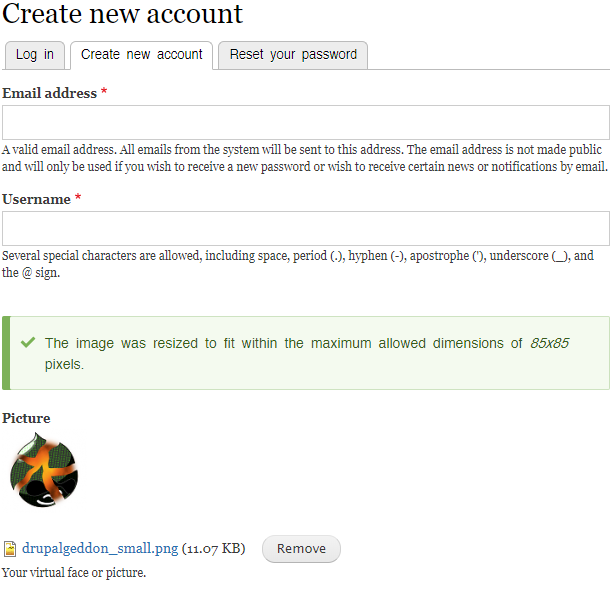
Figure 4: Form used to upload a picture using AJAX API.
Diving into the AJAX file upload callback revealed that it uses a GET parameter to locate the part of the form that needs to be updated in the client.
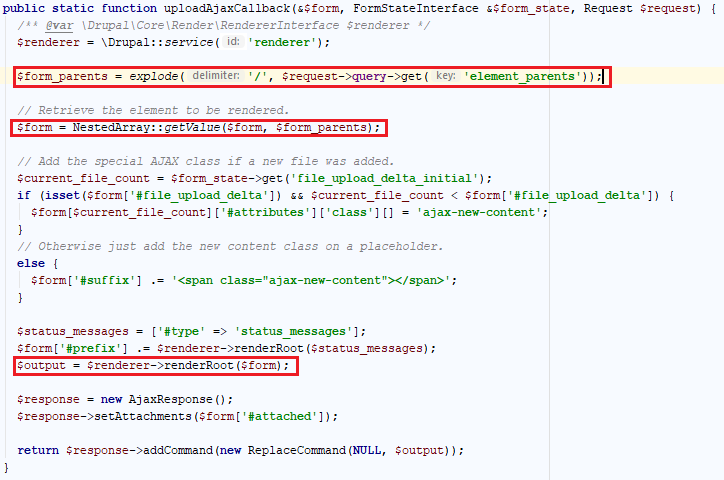
Figure 5: The AJAX ‘upload file’ callback function code.
After pointing element_parents to the part of the form that contained our injected array, Drupal successfully rendered it.
Weaponizing Drupalgeddon 2
Now, all we had to do is to inject a malicious render array that uses one of Drupal’s rendering callback to execute code on the system.
There were several properties we could have injected:
- #access_callback
Used by Drupal to determine whether or not the current user has access to an element. - #pre_render
Manipulates the render array before rendering. - #lazy_builder
Used to add elements in the very end of the rendering process. - #post_render
Receives the result of the rendering process and adds wrappers around it.
For our POC to work, we chose the #lazy_builder element as the one being injected into the mail array. Combined with the AJAX API callback functionality, we could direct Drupal to render our malicious array.
This allowed us to take control over the administrator’s account, install a malicious backdoor module and finally execute arbitrary commands on the server.
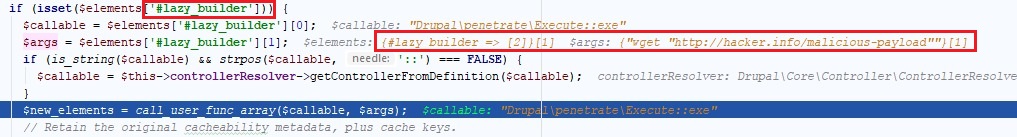
Figure 6: injecting malicious command into one of Drupal’s rendering callbacks.
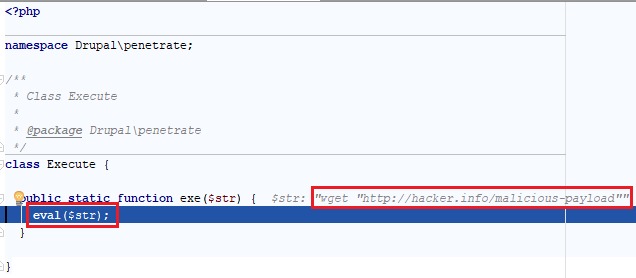
Figure 7: Successfully executing shell commands using the malicious module.
Conclusion
After seeing earlier publications on Twitter and several security blogs, it was apparent that there was much confusion among the community regarding this vulnerability announcement, with some even doubting the severity of it. As a result, we considered it worthwhile to looking deeper into.
The research however was challenging as we were starting from a very large attack surface since the patch blurred the real attack vectors. To expedite our findings, we were fortunate to be joined by experts in the Drupal platform. The final results highlight how easy it is for organization to be exposed through no fault of their own, but rather through the third party platforms they use every day.
漏洞利用代码地址:https://github.com/g0rx/CVE-2018-7600-Drupal-RCE
转:Uncovering Drupalgeddon 2(cve-2018-7600)漏洞深度解析(附漏洞利用代码地址)的更多相关文章
- WordPress Backdoor未授权访问漏洞和信息泄露漏洞
漏洞名称: WordPress Backdoor未授权访问漏洞和信息泄露漏洞 CNNVD编号: CNNVD-201312-497 发布时间: 2013-12-27 更新时间: 2013-12-27 危 ...
- 【阿里聚安全·安全周刊】Intel芯片级安全漏洞事件|macOS存在漏洞
关键词:Intel漏洞丨mac OS漏洞丨三星漏洞丨安卓安全丨CPU漏洞丨phpMyAdmin漏洞丨iOS设备|安卓恶意软件检测|Burpsuite 本周资讯top3 [Intel漏洞]芯片级安全 ...
- 【漏洞复现】Tomcat CVE-2017-12615 远程代码执行漏洞
漏洞描述 [漏洞预警]Tomcat CVE-2017-12615远程代码执行漏洞/CVE-2017-12616信息泄漏 https://www.secfree.com/article-395.html ...
- 20145330 《网络对抗》 Eternalblue(MS17-010)漏洞复现与S2-045漏洞的利用及修复
20145330 <网络对抗> Eternalblue(MS17-010)漏洞利用工具实现Win 7系统入侵与S2-045漏洞的利用及修复 加分项目: PC平台逆向破解:注入shellco ...
- CVE-2015-7547漏洞分析从原因到利用到补丁(非常适合小白)【转】
本文转载自:http://blog.csdn.net/u012406115/article/details/72232535 一. 漏洞概述 CVE漏洞链接:http://www.cv ...
- Apache Tomcat 远程代码执行漏洞(CVE-2019-0232)漏洞复现
Apache Tomcat 远程代码执行漏洞(CVE-2019-0232)漏洞复现 一. 漏洞简介 漏洞编号和级别 CVE编号:CVE-2019-0232,危险级别:高危,CVSS分值:官方 ...
- Windows SMBv3 CVE-2020-0796 漏洞分析和l漏洞复现
0x00 漏洞描述 漏洞公告显示,SMB 3.1.1协议中处理压缩消息时,对其中数据没有经过安全检查,直接使用会引发内存破坏漏洞,可能被攻击者利用远程执行任意代码.攻击者利用该漏洞无须权限即可实现远 ...
- 【Android漏洞复现】StrandHogg漏洞复现及原理分析_Android系统上的维京海盗
文章作者MG1937 CNBLOG博客:ALDYS4 QQ:3496925334 0x00 StrandHogg漏洞详情 StrandHogg漏洞 CVE编号:暂无 [漏洞危害] 近日,Android ...
- Nikto是一款Web安全扫描工具,可以扫描指定主机的web类型,主机名,特定目录,cookie,特定CGI漏洞,XSS漏洞,SQL注入漏洞等,非常强大滴说。。。
Nikto是一款Web安全扫描工具,可以扫描指定主机的web类型,主机名,特定目录,cookie,特定CGI漏洞,XSS漏洞,SQL注入漏洞等,非常强大滴说... root@xi4ojin:~# cd ...
随机推荐
- DHCP及DHCP多作用域服务器工作原理
一.DHCP服务是什么 DHCP称为动态主机配置协议.DHCP服务允许工作站连接到网络并且自动获取一个IP地址.配置DHCP服务的服务器可以为每一个网络客户提供一个IP地址.子网掩码.缺省网关.一个W ...
- form:select form:options 标签数据回显
在jsp页面中经常会使用到 form:select form:options 遍历后台List集合生成 select 下拉选择器,但是 form:options 标签并没有提供一个可以回显数据的属性. ...
- rabbitmq常见运维命令和问题总结
常见运维命令作用: yum安装erlang的环境配置: ERLANG_HOME=/usr/lib64/erlang export PATH=$PATH:$ERLANG_HOME/bin 常见rabbi ...
- JAVA多线程提高十三:同步集合类的应用
1.引言 在多线程的环境中,如果想要使用容器类,就需要注意所使用的容器类是否是线程安全的.在最早开始,人们一般都在使用同步容器(Vector,HashTable),其基本的原理,就是针对容器的每一个操 ...
- 那些相见恨晚的 JavaScript 技巧
JavaScript 的成功让人津津乐道,为 Web 网页编写 JavaScript 代码已经是所有 Web 设计师的基本功,这门有趣的语言蕴藏着许多不为人熟知的东西,即使多年的 JavaScript ...
- Global.asax文件—ASP.NET细枝末节(1)
说明 Global的解释是全局的.全球的. Global.asax 文件,有时候叫做 ASP.NET 应用程序文件,提供了一种在一个中心位置响应应用程序级或模块级事件的方法.你可以使用这个文件实现应用 ...
- 源自人脑的神奇算法 -- 读《How to make your own neural network》有感
最近读到了一本很好的关于机器学习-深度学习的书值得推荐下并特意做了这个学习总结. 为什么推荐 在我认为好书(计算机类)的评判有几个标准: 试图以通俗的语言阐述,并在引入任何新概念的时候都讲述来龙去脉, ...
- Batch Gradient Descent vs. Stochastic Gradient Descent
梯度下降法(Gradient Descent)是用于最小化代价函数的方法. When $a \ne 0$, there are two solutions to \(ax^2 + bx + c = 0 ...
- 多维尺度变换MDS(Multidimensional Scaling)
流形学习(Manifold Learning)是机器学习中一大类算法的统称,流形学习是非线性的降维方法(an approach to non-linear dimensionality reducti ...
- Tomcat 调优及 JVM 参数优化
Tomcat 本身与 JVM 优化 Tomcat:调整Server.xml JVM:bat启动服务方式的话修改catalina.bat 服务式启动的话参考:http://www.cnblogs.com ...
