Lab 6-3
In this lab, we’ll analyze the malware found in the file Lab06-03.exe.
Questions and Short Answers
Compare the calls in main to Lab 6-2’s main method. What is the new function called from main?
A: The functions at 0x401000 and 0x401040 are the same as those in Lab 6-2. At 0x401271 is printf. The 0x401130 function is new to this lab.
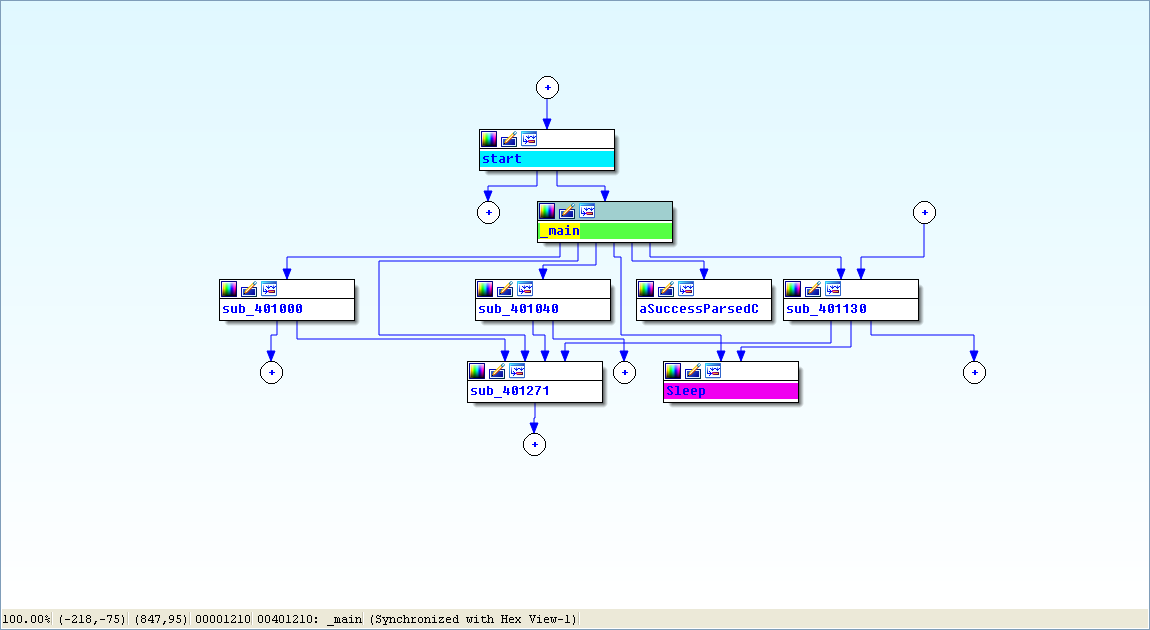
View -> Graphs -> Flow chart :
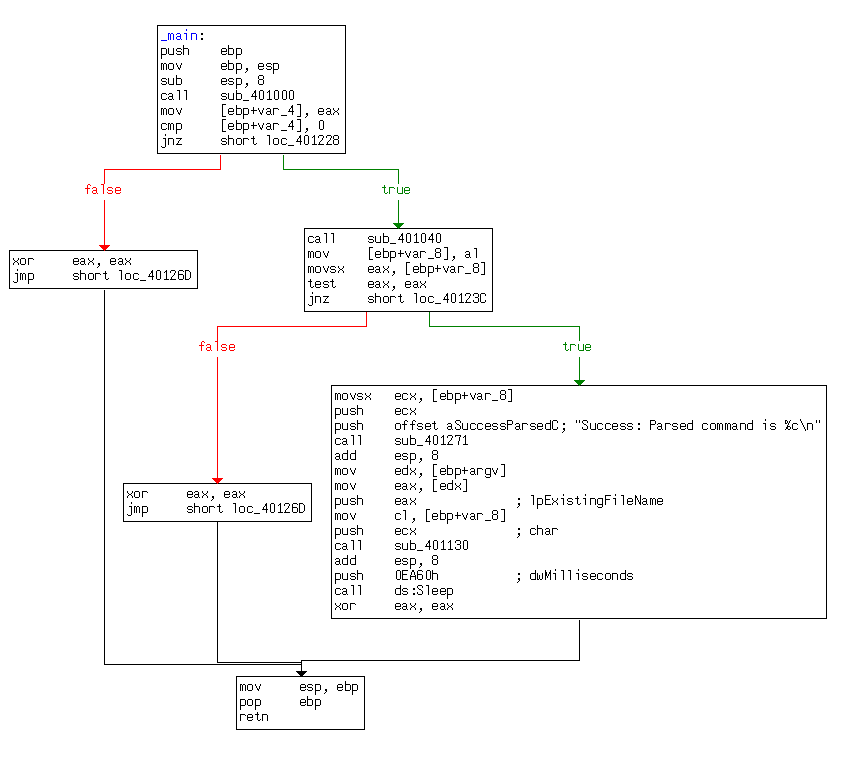
What parameters does this new function take?
A: The new function takes two parameters. The first is the command character parsed from the HTML comment, and the second is the program name argv[0], the standard main parameter.
What major code construct does this function contain?
A: The new function contains a switch statement with a jump table.
What can this function do?
A: The new function can print error messages, delete a file, create a directory, set a registry value, copy a file, or sleep for 100 seconds.
Are there any host-based indicators for this malware?
A: The registry key Software\Microsoft\Windows\CurrentVersion\Run\Malware
and the file location C:\Temp\cc.exe can both be host-based indicators.What is the purpose of this malware?
A: The program first checks for an active Internet connection. If no Internet connection is found, the program terminates. Otherwise, the program will attempt to download a web page containing an embedded HTML comment beginning with
<!--. The first character of the comment is parsed and used in a switch statement to determine which action to take on the local system, including whether to delete a file, create a directory, set a registry run key, copy a file, or sleep for 100 seconds.
Detailed Analysis
We begin by performing basic static analysis on the binary and find several new strings of interest, as shown in Listing 6-6L.

Listing 6-6L: Interesting new strings contained in Lab 6-3
These error messages suggest that the program may be able to modify the registry. Software\Microsoft\Windows\CurrentVersion\Run is a common auto-run location in the registry. C:\Temp\cc.exe is a directory and filename that may be useful as a host-based indicator.
Looking at the imports, we see several new Windows API functions not found in Lab 6-2, as shown in Listing 6-7L.
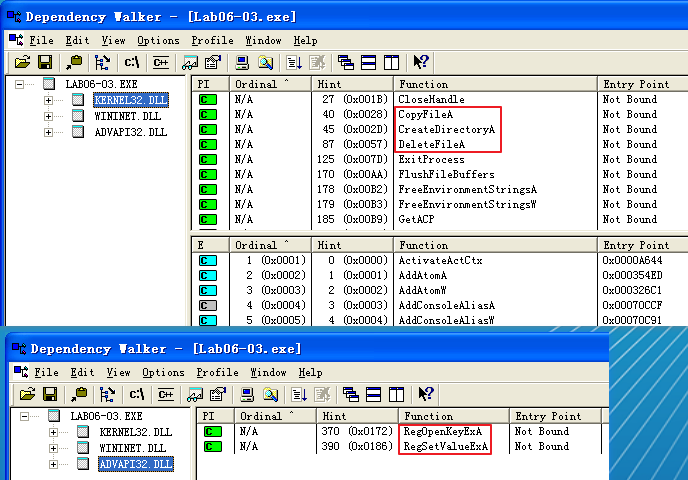
Listing 6-7L: Interesting new import functions contained in Lab 6-3
The first three imports are self-explanatory. The RegOpenKeyExA function is typically used with RegSetValueExA to insert information into the registry, usually when the malware sets itself or another program to start on system boot for the sake of persistence. (We discuss the Windows registry in depth in Chapter 7.)
Next, we perform dynamic analysis, but find that it isn’t very fruitful (not surprising based on what we discovered in Lab 6-2). We could connect the malware directly to the Internet or use INetSim to serve web pages to the malware, but we wouldn’t know what to put in the HTML comment. Therefore, we need to perform more in-depth analysis by looking at the disassembly.
ApateDNS 点击 Stop Server,服务器 Ubuntu 端快捷键 control + c 结束服务。会产生日志文件,查看日志文件内容如下:
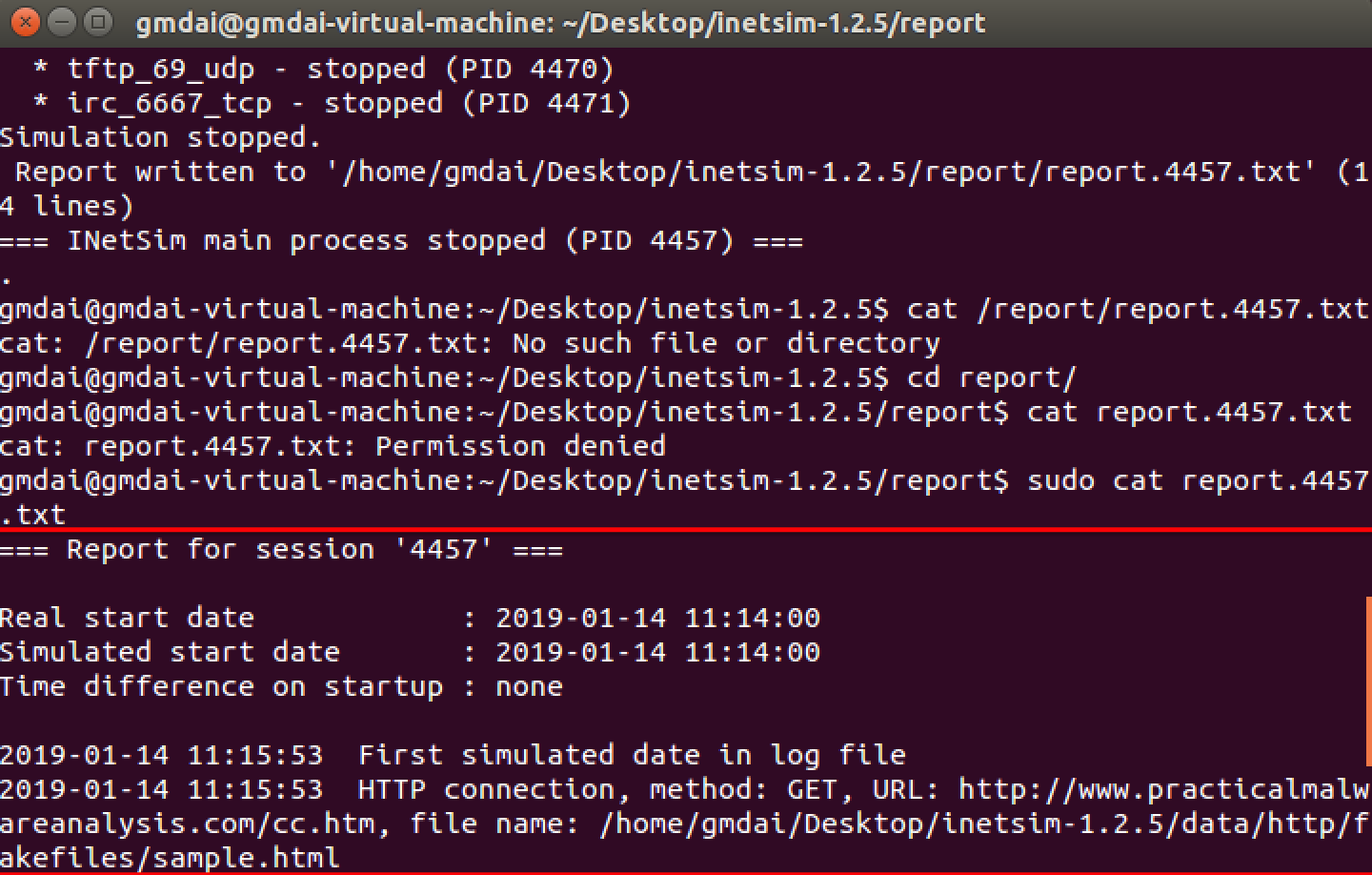
Finally, we load the executable into IDA Pro. The main method looks nearly identical to the one from Lab 6-2, except there is an extra call to 0x401130. The calls to 0x401000 (check Internet connection) and 0x401040 (download web page and parse HTML comment) are identical to those in Lab 6-2.
Next, we examine the parameters passed to 0x401130. It looks like argv and var_8 are pushed onto the stack before the call. In this case, argv is Argv[0], a reference to a string containing the current program’s name, Lab06-03.exe. Examining the disassembly, we see that var_8 is set to AL at 0x40122D. Remember that EAX is the return value from the previous function call, and that AL is contained within EAX. In this case, the previous function call is 0x401040 (download web page and parse HTML comment). Therefore, var_8 is passed to 0x401130 containing the command character parsed from the HTML comment.
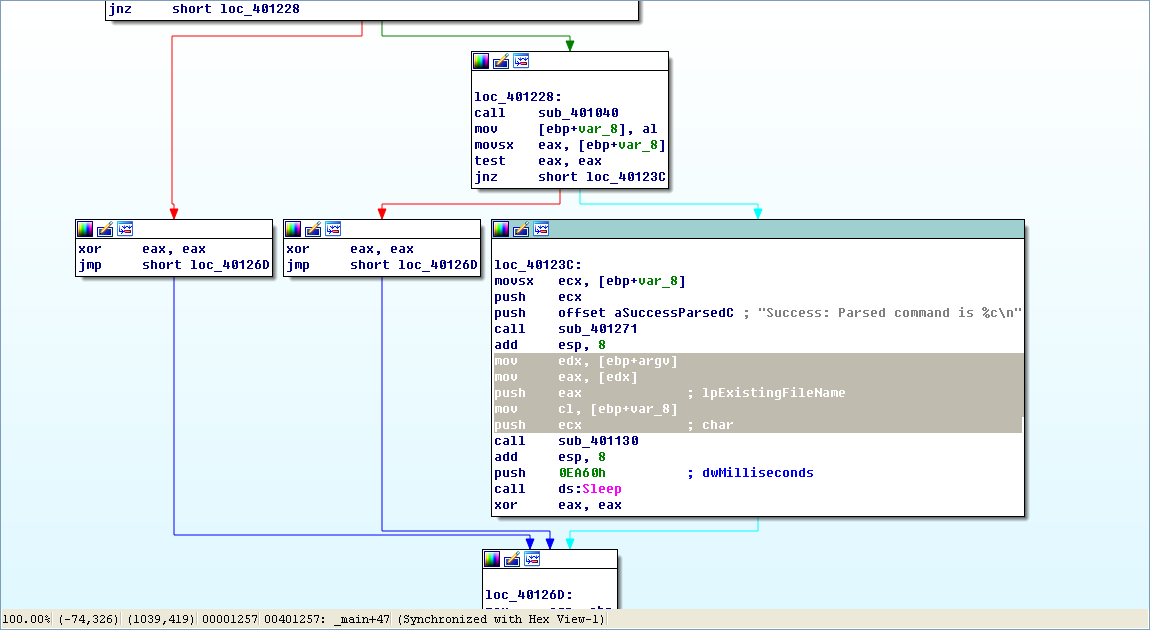
Now that we know what is passed to the function at 0x401130, we can analyze it. Listing 6-8L is from the start of the function.
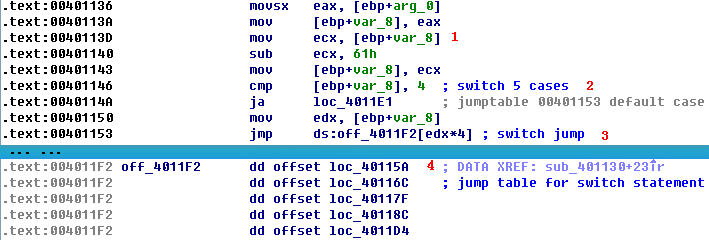
Listing 6-8L: Analyzing the function at 0x401130
arg_0 is an automatic label from IDA Pro that lists the last parameter pushed before the call; therefore, arg_0 is the parsed command character retrieved from the Internet. The parsed command character is moved into var_8 and eventually loaded into ECX at \({\color{red} 1}\). The next instruction subtracts 0x61 (the letter a in ASCII) from ECX. Therefore, once this instruction executes, ECX will equal 0 when arg_0 is equal to a.
Next, a comparison to the number 4 at \({\color{red} 2}\) checks to see if the command character (arg_0) is a, b, c, d, or e. Any other result will force the ja instruction to leave this section of code. Otherwise, we see the parsed command character used as an index into the jump table at \({\color{red} 3}\).
The EDX is multiplied by 4 at \({\color{red} 3 }\) because the jump table is a set of memory addresses referencing the different possible paths, and each memory address is 4 bytes in size. The jump table at \({\color{red} 4}\) has five entries, as expected. A jump table like this is often used by a compiler when generating assembly for a switch statement, as described in Chapter 6.
Graphical View of Command Character Switch
Now let’s look at the graphical view of this function, as shown in Figure 6-3L. We see six possible paths through the code, including five cases and the default. The “jump above 4” instruction takes us down the default path; otherwise, the jump table causes an execution path of the a through e branches. When you see a graph like the one in the figure (a single box going to many different boxes), you should suspect a switch statement. You can confirm that suspicion by looking at the code logic and jump table.
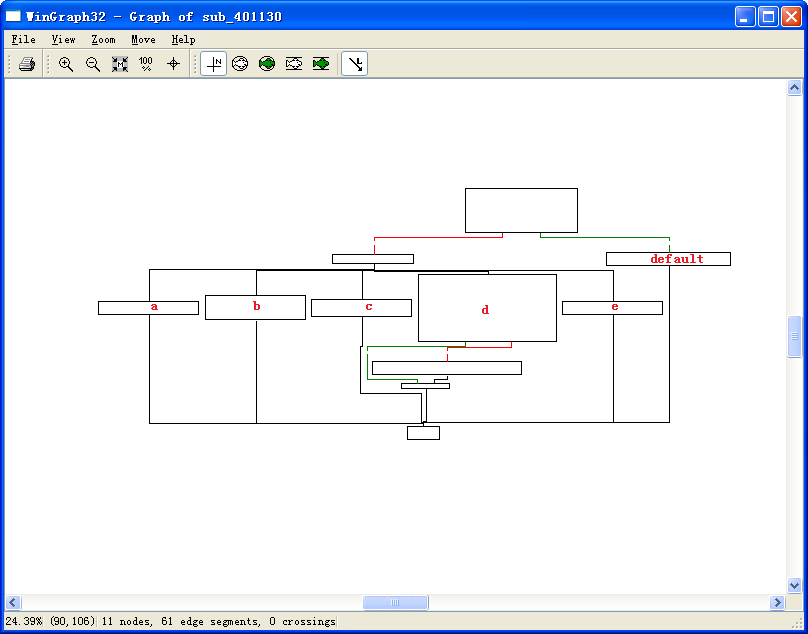
Figure 6-3L: The switch statement from function 0x401130 shown in graphical mode, labeled with the switch options
Switch Options
Next, we will examine each of the switch options (a through e) individually.
- The a option calls CreateDirectory with the parameter C:\\Temp, to create the path if it doesn’t already exist.
- The b option calls CopyFile, which takes two parameters: a source and a destination file. The destination is C:\\Temp\\cc.exe. The source is a parameter passed to this function, which, based on our earlier analysis, we know to be the program name (Argv[0]). Therefore, this option would copy Lab06-03.exe to C:\Temp\cc.exe.
- The c option calls DeleteFile with the parameter C:\\Temp\\cc.exe, which deletes that file if it exists.
- The d option sets a value in the Windows registry for persistence. Specifically, it sets Software\Microsoft\Windows\CurrentVersion\Run\Malware to C:\Temp\cc.exe, which makes the malware start at system boot (if it is first copied to the Temp location).
- The e option sleeps for 100 seconds.
- Finally, the default option prints “Error 3.2: Not a valid command provided.”
Having analyzed this function fully, we can combine it with our analysis from Lab 6-2 to gain a strong understanding of how the overall program operates.
We now know that the program checks for an active Internet connection using the if construct. If there is no valid Internet connection, the program terminates. Otherwise, the program attempts to download a web page that contains an embedded HTML comment starting with <!--. The next character is parsed from this comment and used in a switch statement to determine which action to take on the local system: delete a file, create a directory, set a registry run key, copy a file, or sleep for 100 seconds.
Preference
Lab 6-3的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- 手机连接wamp网页
1.改变wamp的put online 状态 Right click Wampmanager -> WAMPSetting -> Menu Item: Online/Offline
- Linux之cat的使用
基本介绍 工作原理 从标准输入读入要 cat 的文件列表,然后逐个打开,读入文件内容,再将内容输出到标准输出上. 使用场景 一次显示整个文件 从键盘创建一个文件 将几个文件合并为一个文件 将一个或多个 ...
- php 与mysql 数据库
新手上路,php刚学,数据库刚学,花了两天终于读到数据库的数据了. 一路上的坎坷我在这里吐槽吐槽: <?php $mysql_server_name='localhost'; //改成自己的my ...
- ajax验证用户名是否被注册 ; ajax提交form表单
register.html 文件代码: <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" &quo ...
- SQL SERVER查询的临时文件路径
C:\Users\用户\Documents\SQL Server Management Studio\Backup Files C:\Users\用户\AppData\Local\Temp\
- IIC - 【转载】对I2C总线的时钟同步和总线仲裁的深入理解
对I2C总线的时钟同步和总线仲裁的深入理解 每一个IIC总线器件内部的SDA.SCL引脚电路结构都是一样的,引脚的输出驱动与输入缓冲连在一起.其中输出为漏极开路的场效应管.输入缓冲为一只高输入阻抗的同 ...
- 16.3-uC/OS-III同步 (事件标志组实验)
事件标志组,顾名思义,就是若干个事件标志的组合,代表若干个事件是否发生,通常用于集合两个或两个以上事件的状态 . 1.如果想要使用事件标志组,就必须事先使能事件标志组.消息队列的使能位于“os_cfg ...
- mybatis BindingException: Invalid bound statement (not found)
错误截图 解决措施 此异常的原因是由于mapper接口编译后在同一个目录下没有找到mapper映射文件而出现的. 通常我们在配置SqlSessionFactory时会有如配置 <!-- 配置Sq ...
- Linux下安装pymysql
直接使用pip进行安装: [root@mycentos ~]#pip install pymysql
- 基于容器与微服务架构的Web应用示例eShopOnContainers
简介 微软官方提供了一个基于Docker和微服务的示例应用eShopOnContainers:它使用了面向服务的架构并且从服务端到客户端都是跨平台的:该架构使用通过http作为客户端与服务端直接的通信 ...
