国外DDoS产品的一些调研—— Akamai Arbor Networks Cloudflare DOSarrest F5 Fastly Imperva Link11 Neustar Nexusguard Oracle (Dyn) Radware Verisign
Global DDoS Threat Landscape
Q4 2017
https://www.incapsula.com/ddos-report/ddos-report-q4-2017.html,DDOS攻击的报告。
Market Guide for DDoS Mitigation Services
2018年的,from:https://www.gartner.com/doc/3873489/market-guide-ddos-mitigation-services
Summary
The DDoS market has been expanding since 2013, as many new providers have begun to offer DDoS mitigation services. Here, we outline the market segments and highlight differentiators to be considered by security and risk management leaders to select key vendors.
Table of Contents
- Market Definition
- Market Description
- Scrubbing Centers
- Content Delivery Networks
- CSPs and Hosting Providers
- IaaS
- Market Description
- Market Direction
- Market Analysis
- Scrubbing Center
- CDN
- CSPs and Hosters
- IaaS
- Representative Vendors
- Market Introduction
- Vendor Profiles
- Akamai
- Arbor Networks
- Cloudflare
- DOSarrest
- F5
- Fastly
- Imperva
- Link11
- Neustar
- Nexusguard
- Oracle (Dyn)
- Radware
- Verisign
- Market Recommendations
- Gartner Recommended Reading
某网站排名:from:https://www.itcentralstation.com/categories/ddos
一个产品目录,from:https://www.business.com/categories/best-ddos-protection-services/
List of 10 DDoS Protection Services

DOSarrest
http://www.dosarrest.com
DOSarrest's DDoS protection service can thwart application layer, volumetric and protocol attacks. To learn more, check out our review.

CloudFlare
https://www.cloudflare.com
CloudFlare Enterprise is a strong cloud-based DDoS protection service. See how it compares to other denial of service attack mitigation providers.

Neustar
https://www.neustar.biz
Neustar is designed to protect your business from volumetric, application and protocol DDoS attacks. Learn more about this DDoS protection service in our review.

Nexusguard
https://www.nexusguard.com
Nexusguard offers cloud-based mitigation services against DDoS attacks. To learn more, read our review.

Imperva Incapsula
http://www.incapsula.com
Imperva Incapsula offers always-on or on-demand DDoS protection for small to medium-size businesses. Read our full article to learn more.

Radware
http://www.radware.com
Radware's Attack Mitigation Service integrates on-premises detection with cloud-based technology. Compare it with other DDoS mitigation services in our review.

Verisign
http://www.verisigninc.com
Verisign DDoS Protection Service developed a unique mitigation platform, Athena, to mitigate complex DDoS attacks. Learn more about this service in our review.

Akamai
http://www.akamai.com
Akamai Kona Site Defender successfully mitigates denial-of-service attacks. To learn more, read our review.

F5 Networks
https://f5.com
F5's Silverline DDoS Protection uses a number of advanced mitigation techniques to protect you from attacks. Learn more in our review.

Arbor
http://www.arbornetworks.com
Arbor Networks offers cloud-based and on-premise DDoS solutions to safeguard your business from DDoS attacks. Learn more about this service in our review.
DDoS: A Comparison of Defense Approaches
注意:是2014年的结果,from:https://www.gartner.com/doc/2910217/ddos-comparison-defense-approaches
Summary
Distributed denial of service attacks have risen in complexity, bandwidth and number of occurrences targeting enterprises. Organizations must architect their defenses with both cloud and on-premises defenses along with integrating DDoS responses into the current incident response process.
Table of Contents
- Comparison
- Analysis
- Introduction
- Distributed Denial-of-Service Costs
- Unique Attributes of DDoS Attacks
- DDoS Attacks Today
- Brief Attack Taxonomy
- Commonly Seen DDoS Attack Types
- Application-Layer DDoS
- Attack Motivations
- DoS Defense
- DDoS Defense Triad: Resilience, Detection, Mitigation
- DDoS Resilience
- DDoS Detection
- DDoS Mitigation
- DoS Defense Architecture
- DoS Defense Layers and the Shared Nature of DDoS Defense
- Introduction
- Guidance
- Recommendations
- Scenario 1 — Large Enterprise With Mission-Critical Website
- Scenario 2 — Large Enterprise
- Scenario 3 — Enterprise
- Scenario 4 — SMB or Small Enterprise
- Scenario 5 — Cloud-Hosted Website
- Additional Recommendations
- Recommendations
- The Details
- Vendors by Layer Details
- A10 Networks
- Akamai/Prolexic
- Arbor Networks
- Check Point
- Corero Network Security
- F5 Networks
- Juniper Networks
- Neustar
- Radware
- RioRey
- Verisign
- Vendors by Layer Details
- Gartner Recommended Reading
Gartner Says 25 Percent of Distributed Denial of Services Attacks in 2013 Will Be Application-Based
from:https://www.gartner.com/newsroom/id/2344217
WAF 2017的,https://www.gartner.com/doc/reprints?id=1-496C4QP&ct=170807&st=sb

from:https://www.imperva.com/blog/2017/08/gartner-magic-quadrant-for-wafs-a-leader-four-consecutive-years/
Forcepoint recognized in Visionary quadrant in Gartner 2017 Magic Quadrant for Enterprise Network Firewalls
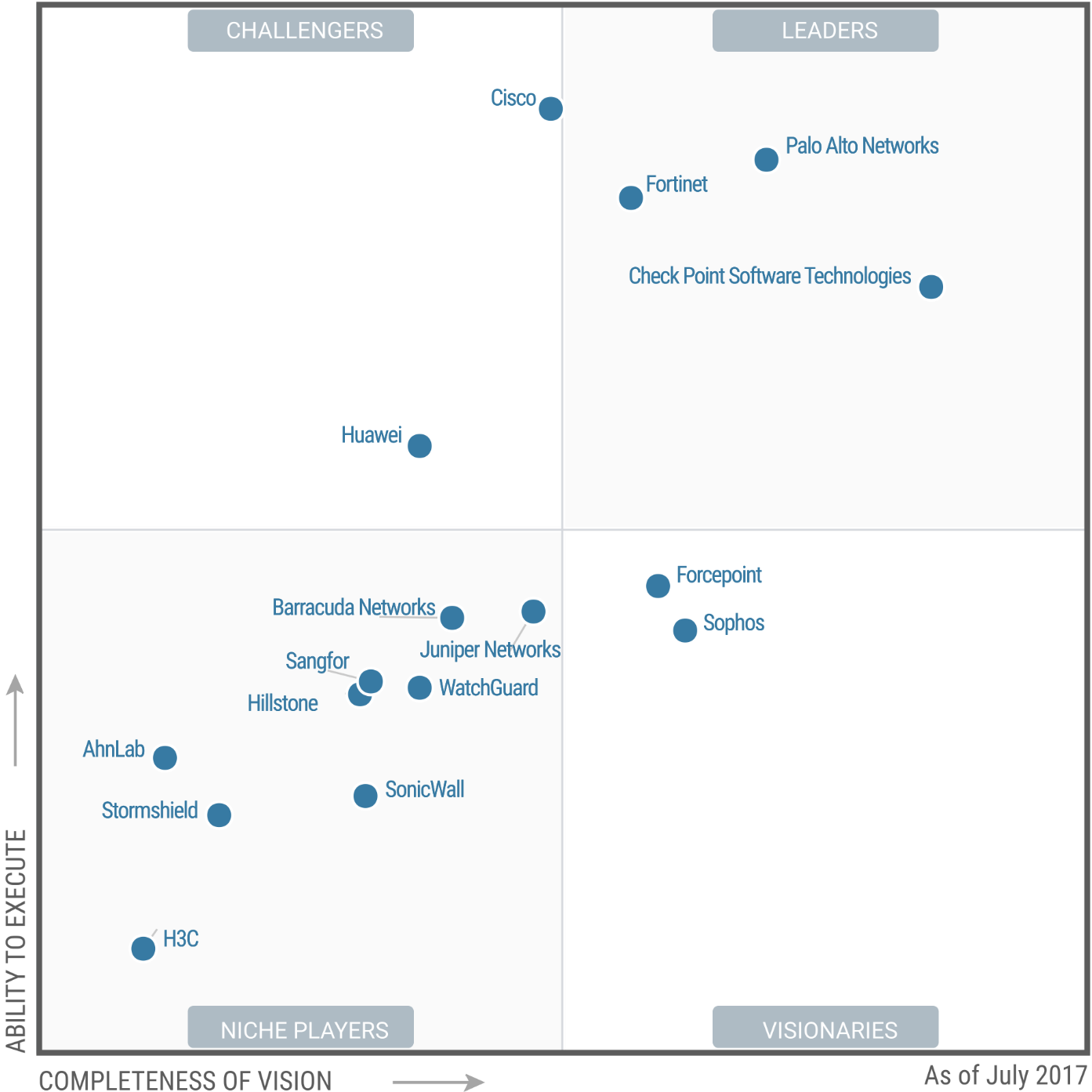
Forcepoint leaps from Niche Player in 2016 to highest for ability to execute in the Visionary quadrant in the 2017 Gartner Magic Quadrant for Enterprise Network Firewalls.
from:https://www.forcepoint.com/zh-hans/node/14171
国外DDoS产品的一些调研—— Akamai Arbor Networks Cloudflare DOSarrest F5 Fastly Imperva Link11 Neustar Nexusguard Oracle (Dyn) Radware Verisign的更多相关文章
- Backlog和冲刺结果以及产品Demo市场调研
Backlog和第一阶段冲刺结果以及产品Demo 博客停更了一段时间,但是我们团队没有闲着,现在一次性汇报团队工作进度,Backlog和第一阶段冲刺结果以及产品Demo. 在一段时间的分工合作以及调整 ...
- 国外物联网平台(4):Ayla Networks
国外物联网平台(4)——Ayla Networks 马智 定位 Ayla企业软件解决方案为全球部署互联产品提供强大的工具 功能 Ayla的IoT平台包含3个主要组成部分: (1) Ayla嵌入式代理A ...
- https ddos攻击——由于有了认证和加解密 后果更严重 看绿盟的产品目前对于https的ddos cc攻击需要基于内容做检测
如果web服务器支持HTTPS,那么进行HTTPS洪水攻击是更为有效的一种攻击方式,一方面,在进行HTTPS通信时,web服务器需要消耗更多的资源用来进行认证和加解密,另一方面,一部分的防护设备无法对 ...
- 使用多个DNS供应商以缓解DDoS攻击
随着不安全物联网(IoT)设备的激增,针对域名系统(DNS)供应商的分布式拒绝服务(DDoS)攻击在数量和规模上正在不断增加.这些攻击随之影响依赖于这些供应商进行域名解析的网站.虽然DNS供应 ...
- 放大倍数超5万倍的Memcached DDoS反射攻击,怎么破?
欢迎大家前往腾讯云+社区,获取更多腾讯海量技术实践干货哦~ 作者:腾讯游戏云 背景:Memcached攻击创造DDoS攻击流量纪录 近日,利用Memcached服务器实施反射DDoS攻击的事件呈大幅上 ...
- 做游戏的小伙伴们注意了,DDoS还可以这样破!
欢迎大家前往腾讯云+社区,获取更多腾讯海量技术实践干货哦~ 本文由腾讯游戏云发表于云+社区专栏 作者:腾讯DDoS安全专家.腾讯云游戏安全专家haroldchen 摘要:在游戏出海的过程中,DDoS攻 ...
- 12、产品经理要阅读的书籍 - IT软件人员书籍系列文章
产品经理是软件产品的主要领导者.不同于项目经理,产品经理是对产品负责,更多的是负责产品的设计定型:而项目经理则对项目负责,更多的是负责项目软件的实现.产品经理的一些工作,和项目经理是一致的,比如需求分 ...
- ERP调研之 对话
开卷语: 2009年8月6号,A公司ERP项目顺利启动,按照项目进度的安排,项目组成员立即投入到紧张而又忙碌的的业务调研之中.这次为期3周的业务调研面向企业所有业务部门,包括产品部门.采购部门.计划部 ...
- 防止 DDoS 攻击的五个「大招」!
提到 DDoS 攻击,很多人不会陌生.上周,美国当地时间 12 月 29 日,专用虚拟服务器提供商 Linode 遭到 DDoS 攻击,直接影响其 Web 服务器的访问,其中 API 调用和管理功能受 ...
随机推荐
- 004-java类保存优化
设置路径:windows→preferences→java→editer→save Actions 1.设置如下 2.可单击右侧configure配置 2.1.code organorganizing ...
- [转载]有经验的Java开发者和架构师容易犯的10个错误
首先允许我们问一个严肃的问题?为什么Java初学者能够方便的从网上找到相对应的开发建议呢?每当我去网上搜索想要的建议的时候,我总是能发现一大堆是关于基本入门的教程.书籍以及资源.同样也发现网上到处充斥 ...
- MB11 生鲜项目原料消耗发货功能
*&---------------------------------------------------------------------* *& 程序名: ZDQFI_925 * ...
- corethink功能模块探索开发(十六)后台搜索功能
效果图: 代码很简单,就是添加搜索框,搜索字段,在初始化页面查询的时候添加查询条件. 1.添加搜索框 添加到删除按钮后边. ->setSearch('请输入设备名称/MAC/宿舍号', U('i ...
- JS操作时间 - UNIX时间戳简单介绍
准备知识 GMT(Greenwich Mean Time) - 格林尼治时间.UTC(Universal Time Code) - 国际协调时间.PST(Pacific Standard Time,太 ...
- beego——控制器函数
基于beego的Controller设计,只需要匿名组合beego.Controller就可以,如下所示: type xxxController struct { beego.Controller } ...
- pycharm修改配置
恢复pycharm的初始设置
- Java面向对象—继承
概述: 1.多个类相同的属性和功能抽取成另一个类, 让具有特有功能的类继承这个类. 2.通过 extends 关键字可以实现类与类的继承 格式: class 子类名 extends 父类名 {} 特点 ...
- URAL - 1902 Neo-Venice
题目: Mars was the first planet colonized by humans. After a long terraforming process its appearance ...
- GIT如何使用:大杀器!所有常用指令整理
1 pwd 显示当前目录2 mkdir 创建目录 cd 进入文件3 git init 变成Git可以管理的仓库(千万不要修改目录下的.git隐藏文件夹)4 ls -ah 可以把.git文件显示出来5 ...





