Internet Technologe
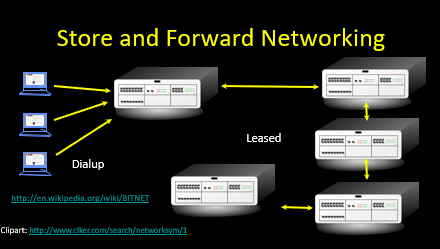
Store and Forward Networking
Efficient Message Transmission:Packet Switching(分组交换)
- Challenge: in a simple approach, like store-and-forward, large messages block small ones(延迟问题)
- Break each message into packets(大化小)
- Can allow the packets from a single message to travel over different paths, dynamically adjusting for use(可不同路径)
- Use special-purpose computers, called routers, for the traffic control(路由器来控制数据移动)
Shared Network

- In order to keep cost low and the connections short geographically - data would be forwarded through several routers.
- Network Connection
- Host A-->Router-->Router-->Host B
- Getting across the country usually takes about 10 “hops”
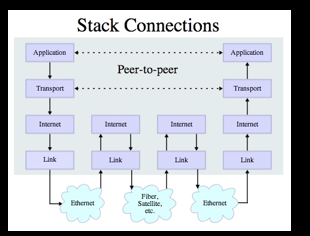
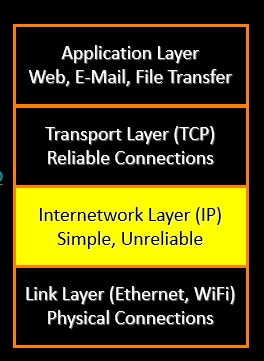
Layered Network Model
- A layered approach allows the problem of designing a network to be broken into more manageable sub problems(大问题拆分为小问题)
- Best-known model: TCP/IP—the “Internet Protocol Suite”(TCP/IP模型)
- There was also a 7 layer OSI: Open System Interconnection Model(7层模型)

Internet Standards
- The standards for all of the Internet protocols (inner workings) are developed by an organization——Internet Engineering Task Force (IETF)
- Standards are called “RFCs” - “Request for Comments”(个人可以查看RFC并提出建议,建议-->草案-->审核通过-->新标准)
Layered Architecture
- The Physical and Internet Layers are like trucks and trains - they haul stuff and get it to the right loading dock - it takes multiple steps
- The Transport layer checks to see if the trucks made it and send the stuff again if necessary
Link Layer(aka Physical Layer)
- phisical
- the lowest layer in the Internet Protocol Suite
- described in RFC 1122 and RFC 1123
- Link Layer Addresses
- Many physical layer devices have addresses built in to them by the manufacturer(制造时就有)
- Wireless Ethernet (Wifi)

Sharing Nicely - Avoiding Chaos
- To avoid garbled messages, systems must observe “rules” (Protocols)
- Ethernet rules are simple
- steps(步骤 !!!)
- Wait for silence
- Begin Transmitting data
- Listen for your own data
- If you cannot hear your own data clearly, assume a collision, stop and wait before trying again
- Each system waits a different amount of time to avoid “too much politeness”
Ethernet(第一个本地计算机网络)
- Invented at PARC (Xerox)
- The first Local-Area-Network
- Connected PC's to laser printers
- Inspired by an earlier wireless network called Aloha from the University of Hawaii
Internetwork Layer(IP)
Internet Protocol Layer(实际移动)
- Goal: Gets your data from this computer to the other computer half way across the world
- Each router knows about nearby routers
- IP Is best effort - it is OK to drop data if things go bad...(丢弃)
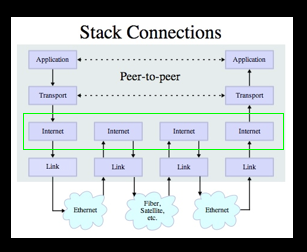
IP Addresses
- The IP address is the worldwide number which is associated with one particular workstation or server(全球性)
- network number(6 bit) + computer number within network(6 bit)
Router tables
The best outbound route for each router record to reach another router, dynamic update, an index
DHCP(dynamic host configuraton protocol动态主机配置协议)
- is given a temporary address (被给了临时地址)
- it can not run in the Internet network. It only applies to local network,
- such as 192.168.xxx.xxxx and so on.
- the non-routable website.(不可路由地址)
TTL(Time-to-live)
- to control the count of hop
- Abandoned from 255 to 0(减到0时认为无法到达,便舍弃)
Transport Layer(负责移动的可靠性)
TCP(Transport Protocol)
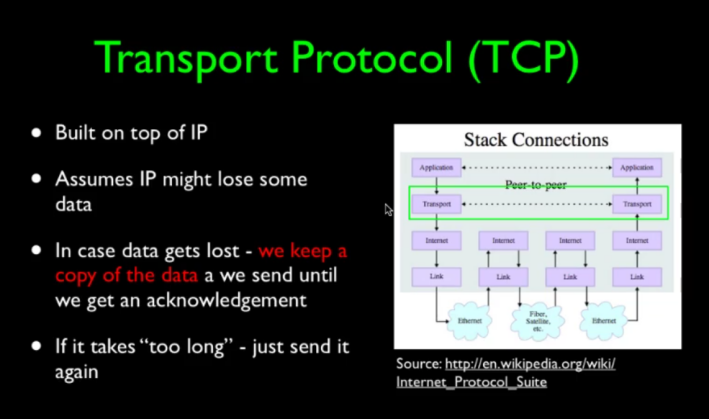
- built on the IP Layer.
- function:to solve some problems that may arise in the IP layer.(弥补Link Layer的不足)
- steps(过程):
- Send and receive feedback(先确认一下)
- acknowledged --> Discard acknowledged packets(确认接受后丢弃)
- Not confirmed --> again(未确认则再发知道成功确认)
Slow Start Algorithm(慢启动算法)(看不太懂)
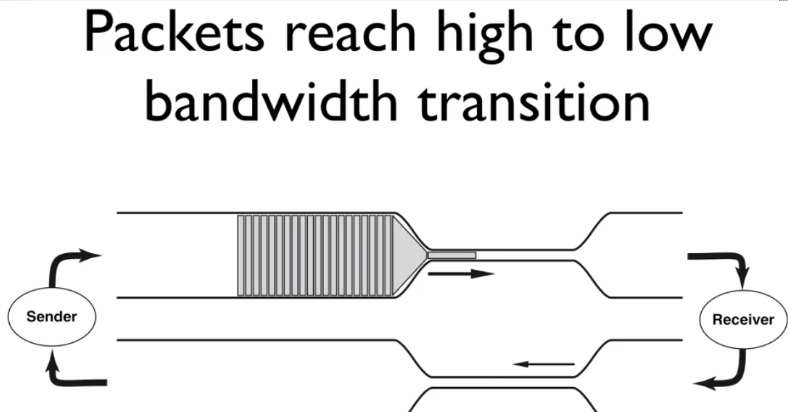
- First send slowly, then slowly increase the speed.
DNS(Domain Name System)(域名系统)
- A way to remember more easily than an IP address.
- IP:left to right : DNS:right to left
- such as:www.si.umich.edu

Application Layer(应用层)
Application Protocol

port
- Ports are dependent on IP, similar to branch paths of IP addresses. Different ports correspond to different functions and services.
- such as:80 , 45
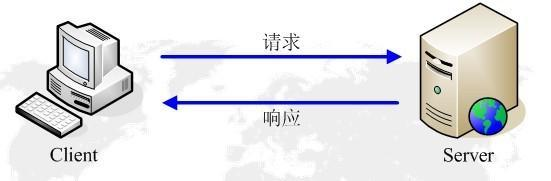
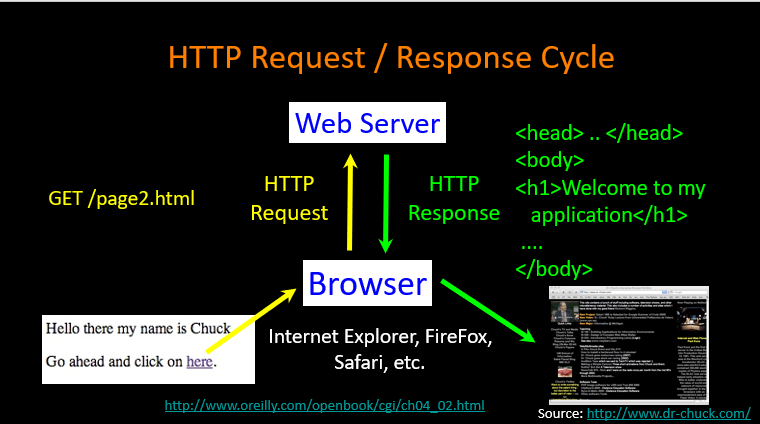
HTTP(Hyper Text Transfer Protocol)
- base on TCP/IP
- client --> click link--> generate links to server --> look up server --> show
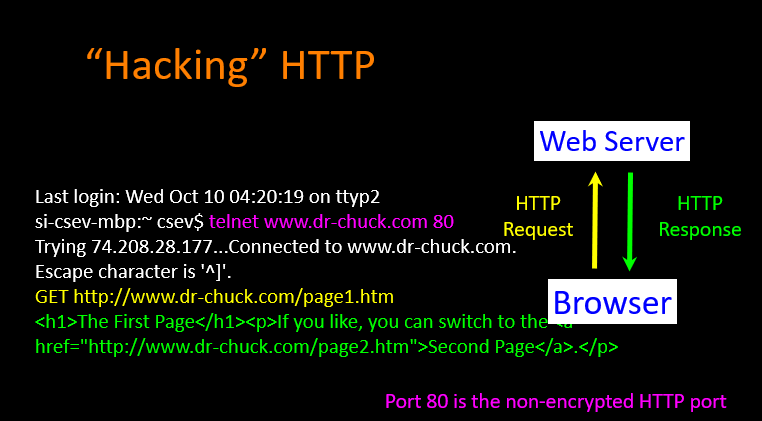
- "Hacking" HTTP:pretend browers ,ues "get" commond
Internet Technologe的更多相关文章
- Internet History,Tecchnology and Security
Internet History Internet Technologe Internet Secure
- internet协议入门
前言 劳于读书,逸于作文. 原文地址:internet协议入门 博主博客地址:Damonare的个人博客 博主之前写过一篇博客:网络协议分析,在这篇博客里通过抓包,具体的分析了不同网络协议的传送的数据 ...
- DOS下命令符开启wifi无internet访问解决办法
先按win+R 输入cmd netsh wlan set host mode=allow ssid=nothing key=323435435 (ssid后面的可以任意,key后面最少8个字符) 我的 ...
- 三星首次更新Gear VR虚拟现实浏览器Samsung Internet
通过VR浏览网页不是问题,不过你需要一个专门的VR浏览器,而GearVR的虚拟现实应用名为"Samsung Internet for Gear VR".继去年12月份上线后,迎来了 ...
- 企业IT管理员IE11升级指南【1】—— Internet Explorer 11增强保护模式 (EPM) 介绍
企业IT管理员IE11升级指南 系列: [1]—— Internet Explorer 11增强保护模式 (EPM) 介绍 [2]—— Internet Explorer 11 对Adobe Flas ...
- 企业IT管理员IE11升级指南【2】—— Internet Explorer 11 对Adobe Flash的支持
企业IT管理员IE11升级指南 系列: [1]—— Internet Explorer 11增强保护模式 (EPM) 介绍 [2]—— Internet Explorer 11 对Adobe Flas ...
- 企业IT管理员IE11升级指南【6】—— Internet Explorer 11面向IT专业人员的常见问题
企业IT管理员IE11升级指南 系列: [1]—— Internet Explorer 11增强保护模式 (EPM) 介绍 [2]—— Internet Explorer 11 对Adobe Flas ...
- ASP.NET MVC - 创建Internet 应用程序
为了学习 ASP.NET MVC,我们将构建一个 Internet 应用程序. 第 1 部分:创建应用程序. 我们将构建什么 我们将构建一个支持添加.编辑.删除和列出数据库存储信息的 Internet ...
- Internet网
Internet网是世界上最大的基于IP的网络.它是世界上所有计算机使用IP相互对话的一个无组织的集合.Internet上每台计算机都至少有一个IP地址来标识该计算机. 节点与主机 连接到Intern ...
随机推荐
- 继续深入更新shell脚本容易出错的地方
一.在shell中用到如果需要输入某些值,需要用到read -p命令 这是我写的猜数字游戏,一开始在输出的时候,屏幕上总会打印输出 "INT" 经过反复的练习才发现 双引号后面应 ...
- 【Spark】Spark2.x版的新特性
一.API 1. 出现新的上下文接口:SparkSession,统一了SQLContext和HiveContext,并且为SparkSession开发了新的流式调用的configuration API ...
- flume搭建新手测试环境
硬件环境: 腾讯云,两台服务器8G 双核 软件环境: flume1.8.jdk1.8,centos6 第一次搭建也是各种找文件,只知道flume是日志抓取服务,也听说了非常稳定强大的服务,正好公司需要 ...
- uCOS-II中的任务切换-图解多种任务调度时机与问题
[@.1 任务调度时机] 之前的一篇文章分析了具体的uCOS-II中的任务切换机制,是从函数调用的角度上分析的.这次我具体从整个程序运行的时间上来看,分析多种任务调度发生的时机.以下所有图片均可点击放 ...
- 20154327 Exp1 PC平台逆向破解
一.实践目标 1.运行原本不可访问的代码片段 2.强行修改程序执行流 3.以及注入运行任意代码 二.基础知识 1.直接修改程序机器指令,改变程序执行流程 2.通过构造输入参数,造成BOF攻击,改变程序 ...
- dubbo之注册管理中心
一.在dubbo的框架中注册中心是必要的一个环节,这个也是分布式部署的一个必要环节.在dubbo的架构基本图中可以看出,基本上所有的服务都是通过注册中心进行注册,然后在通过注册中心,暴露出接口来. 二 ...
- PHP中strtotime()的使用
strtotime是一个非常强大的函数. 传入的参数,详见官网的介绍 本月最后一个周日 echo date('Y-m-d',strtotime('last sunday of this month') ...
- STM32F746G-DISCO官方例程烧写
1. 首先安装STM32 ST-LINK Utility v3.9.0.exe,必须V3.9版本(官方说的) 2. 打开软件,选择External Loader,选择N25Q128A_STM32F74 ...
- Maven项目配置tomcat插件实现项目自动部署到远程服务器
1.tomcat配置 在tomcat目录中的conf目录下找到tomcat-users.xml配置文件,然后搜索tomcat-users,进行tomcat用户的角色和权限配置,如下: <tomc ...
- 一个体验好的Windows 任务栏缩略图开发心得
本文来自网易云社区 作者:孙有军 前言: 对于一个追求极致体验的软件来说,利用好系统的每一点优秀的特性,将会大大提高软件的品质. Windows vista以来任务栏缩略图,及Win + TAB的程序 ...
