swpu新生赛ctf wp
WEB:gift_F12
没啥好说的 直接F12得了

NSSCTF{We1c0me_t0_WLLMCTF_Th1s_1s_th3_G1ft}
RE
简简单单的解密
import base64, urllib.parse
def e():
key = "HereIsFlagggg"
flag = "xxxxxxxxxxxxxxxxxxx"
s_box = list(range(256))
j = 0
# 打乱s_box 和flag无关
for i in range(256):
j = (j + s_box[i] + ord(key[i % len(key)])) % 256
s_box[i], s_box[j] = s_box[j], s_box[i]
res = []
i = j = 0
for s in flag:
i = i + 1
j = (j + s_box[i]) % 256
s_box[i], s_box[j] = s_box[j], s_box[i]
t = (s_box[i] + s_box[j]) % 256
k = s_box[t]
res.append(chr(ord(s) ^ k))
enc = "".join(res)
#原来这里有个b64加密再解密 就等于没变 所以改了一下
enc = urllib.parse.quote(enc)
print(enc)
def d():
enc = "%C2%A6n%C2%87Y%1Ag%3F%C2%A01.%C2%9C%C3%B7%C3%8A%02%C3%80%C2%92W%C3%8C%C3%BA"
enc = urllib.parse.unquote(enc)#倒着往回做呗
key = "HereIsFlagggg"
s_box = list(range(256))
j = 0
r=[]
# 获得s_box
for i in range(256):
j = (j + s_box[i] + ord(key[i % len(key)])) % 256
s_box[i], s_box[j] = s_box[j], s_box[i]
i,j=0,0
for s in enc:
i = i + 1
j = (j + s_box[i]) % 256
s_box[i], s_box[j] = s_box[j], s_box[i]
t = (s_box[i] + s_box[j]) % 256
k = s_box[t]
r.append(chr(ord(s)^k))#基本直接复制就行 异或的逆运算就是再异或一次
print("".join(r))
if __name__ == '__main__':
e()
d()
脚本运行得到结果
NSSCTF{REAL_EZ_RC4}
简简单单的逻辑
先上脚本
def e():
flag = 'xxxxxxxxxxxxxxxxxx'
list = [47, 138, 127, 57, 117, 188, 51, 143, 17, 84, 42, 135, 76, 105, 28, 169, 25]
result = ''
for i in range(len(list)):
key = (list[i] >> 4) + ((list[i] & 0xf) << 4)
a = hex(ord(flag[i]) ^ key)
result += str(a)[2:].zfill(2)
#分析得知 这是16进制补全两位 所以是一个flag字符对应两位
print(result)
def d():
list = [47, 138, 127, 57, 117, 188, 51, 143, 17, 84, 42, 135, 76, 105, 28, 169, 25]
result = "bcfba4d0038d48bd4b00f82796d393dfec"
nums = []
#截取 转换 得到原来十进制
for i in range(0,len(result),2):
nums.append("0x" + result[i:i+ 2])
for index in range(len(nums)):
nums[index]=int(nums[index],16)
#直接加密里面复制key的计算 然后再异或一次即可
for i in range(len(list)):
key = (list[i] >> 4) + ((list[i] & 0xf) << 4)
print(chr(nums[i]^key),end="")
if __name__ == '__main__':
# e()
d()
这看脚本就行了
NSSCTF{EZEZ_RERE}
非常简单的逻辑题
def e():
flag = 'xxxxxxxxxxxxxxxxxxxxx'
s = 'wesyvbniazxchjko1973652048@$+-&*<>'
result = ''
for i in range(len(flag)):
s1 = ord(flag[i]) // 17
s2 = ord(flag[i]) % 17
#就 没啥好讲的 一点点拆开打断点调试就能看懂计算过程
#还是flag一个字符转换对应result的两个字符
a = s[(s1 + i) % 34]
b = s[-(s2 + i + 1) % 34]
result += a + b
print(result)
def d():
result = 'v0b9n1nkajz@j0c4jjo3oi1h1i937b395i5y5e0e$i'
s = 'wesyvbniazxchjko1973652048@$+-&*<>'
#套这么多层循环 主要是我不知道 取余怎么更方便的算回去
for x in range(-5, 5):
for y in range(-5, 5):
r = ""
for j in range(0, len(result), 2):
a = result[j]
b = result[j + 1]
#根据数学知识可得(
s1 = int(s.index(a) + 34 * x - j / 2)
s2 = -1*int(s.index(b) + 34 * y + j / 2 + 1)
#去除没啥意义的结果
if 32 < s1 * 17 + s2 < 130:
r += chr(s1 * 17 + s2)
else:
break
if len(r)==len('xxxxxxxxxxxxxxxxxxxxx'):
print(r)
if __name__ == '__main__':
# e()
d()
NSSCTF{Fake_RERE_QAQ}
fakerondom
import random
def e():
flag = 'xxxxxxxxxxxxxxxxxxxx'
#别的都不重要 就是这个随机数种子
#同样的随机数种子生成的一定是相同的数字
random.seed(1)
l = []
for i in range(4):
l.append(random.getrandbits(8))
result = []
for i in range(len(l)):
random.seed(l[i])
for n in range(5):
result.append(ord(flag[i * 5 + n]) ^ random.getrandbits(8))
print(result)
def d():
result = [201, 8, 198, 68, 131, 152, 186, 136, 13, 130, 190, 112, 251, 93, 212, 1, 31, 214, 116, 244]
random.seed(1)
ran=[]
t=[]
for x in range(4):
ran.append(random.getrandbits(8))
l=ran[0:4]
for i in range(len(l)):
random.seed(l[i])
for n in range(5):
#异或题最好写了 基本原样复制代码就行
print(chr(result[i * 5 + n]^ random.getrandbits(8)),end="")
if __name__ == '__main__':
e()
d()
NSSCTF{FakeE_random}
fakebase
def e():
flag = 'xxxxxxxxxxxxxxxxxxx'
s_box = 'qwertyuiopasdfghjkzxcvb123456#$'
tmp = ''
for i in flag:
x = bin(ord(i))
tmp += str(x)[2:].zfill(8)
b1 = int(tmp, 2)
s = ''
while b1 // 31 != 0:
c = b1 % 31
s += s_box[c]
b1 = b1 // 31
print(b1)
print(s)
def d():
s = "u#k4ggia61egegzjuqz12jhfspfkay"
# s="j3d4h1$6ggrouxktrgky5sxv6bk6i5"#测试
s_box = 'qwertyuiopasdfghjkzxcvb123456#$'
l = []
for x in s:
l.append(s_box.index(x))
l=l[::-1]
for n in range(0,31):
for x in l:
n=x+31*n
t=str(bin(n))[2:]
for j in range(0,len(t),8):
#这题最让我迷惑 我觉得我写的是对的
#但是拿上面的加密结果再解密出来的ascii值总差一倍
#但最后一个字符的ascii值又是对应的 所以只能除以2看看
#所以就 现在挺迷茫的
print(chr(int(int(t[j:j+8],2)/2)),end="")
print()
if __name__ == '__main__':
# e()
d()
NSSCTF{WHAt_BASe31}
astjs
经过查资料知道 这是把js文件转换为ast 但是我不知道怎么转回去
解不出 我太菜了
简 单 的 逻 辑
我是 san兵
我真看不出
出题人说少给条件了 但可以琼剧
密码
带rsa的都不会 萌新还没学呢
crypto6
var="************************************"
flag='NSSCTF{' + base64.b16encode(base64.b32encode(base64.b64encode(var.encode()))) + '}'
print(flag)
小明不小心泄露了源码,输出结果为:4A5A4C564B36434E4B5241544B5432454E4E32465552324E47424758534D44594C4657564336534D4B5241584F574C4B4B463245365643424F35485649534C584A5A56454B4D4B5049354E47593D3D3D,你能还原出var的正确结果吗?
会用base64库就行
import base64
x="4A5A4C564B36434E4B5241544B5432454E4E32465552324E47424758534D44594C4657564336534D4B5241584F574C4B4B463245365643424F35485649534C584A5A56454B4D4B5049354E47593D3D3D"
a=base64.b16decode(x)
a=base64.b32decode(a)
a=base64.b64decode(a)
print(a)
NSSCTF{5e110989-dc43-1bd3-00b4-9009206158fe}
Crypto7
69f7906323b4f7d1e4e972acf4abfbfc
直接md5解密
NSSCTF{md5yyds}
crypto8
介绍pyhton库:ciphey库! 人工智能 yyds
直接一把梭
终端执行命令
ciphey -t "73E-30U1&>V-H965S95]I<U]P;W=E<GT`"

这个题用了uuencode
crypto9
题干脚本直接python执行
letter_list = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ' # 字母表
# 根据输入的key生成key列表
def Get_KeyList(key):
key_list = []
for ch in key:
key_list.append(ord(ch.upper()) - 65)
return key_list
# 加密函数
def Encrypt(plaintext, key_list):
ciphertext = ""
i = 0
for ch in plaintext: # 遍历明文
if 0 == i % len(key_list):
i = 0
if ch.isalpha(): # 明文是否为字母,如果是,则判断大小写,分别进行加密
if ch.isupper():
ciphertext += letter_list[(ord(ch) - 65 + key_list[i]) % 26]
i += 1
else:
ciphertext += letter_list[(ord(ch) - 97 + key_list[i]) % 26].lower()
i += 1
else: # 如果密文不为字母,直接添加到密文字符串里
ciphertext += ch
return ciphertext
# 解密函数
def Decrypt(ciphertext, key):
plaintext = ""
i = 0
for ch in ciphertext: # 遍历密文
if 0 == i % len(key_list):
i = 0
if ch.isalpha(): # 密文为否为字母,如果是,则判断大小写,分别进行解密
if ch.isupper():
plaintext += letter_list[(ord(ch) - 65 - key_list[i]) % 26]
i += 1
else:
plaintext += letter_list[(ord(ch) - 97 - key_list[i]) % 26].lower()
i += 1
else: # 如果密文不为字母,直接添加到明文字符串里
plaintext += ch
return plaintext
if __name__ == '__main__':
print("加密请按D,解密请按E:")
user_input = input();
while (user_input != 'D' and user_input != 'E'): # 输入合法性判断
print("输入有误!请重新输入:")
user_input = input()
print("请输入密钥:")
key = input()
while (False == key.isalpha()): # 输入合法性判断
print("输入有误!密钥为字母,请重新输入:")
key = input()
key_list = Get_KeyList(key)
if user_input == 'D':
# 加密
print("请输入明文:")
plaintext = input()
ciphertext = Encrypt(plaintext, key_list)
print("密文为:\n%s" % ciphertext)
else:
# 解密
print("请输入密文:")
ciphertext = input()
plaintext = Decrypt(ciphertext, key_list)
print("明文为:\n%s" % plaintext)
试了试密码NSS解密成功
Crypto10
当然你可以接着用这个
ciphey -t "AFFPGS{pbatenghyngvbaf!!!}"

NSSCTF{congratulations!!!}
ez_caesar
def caesar(plaintext):
str_list = list(plaintext)
i = 0
while i < len(plaintext):
if not str_list[i].isalpha():
str_list[i] = str_list[i]
else:
a = "A" if str_list[i].isupper() else "a"
str_list[i] = chr((ord(str_list[i]) - ord(a) + 5) % 26 + ord(a) or 5)
i = i + 1
return ''.join(str_list)
if __name__ == '__main__':
small = [chr(i) for i in range(97, 123)]
big = [chr(i) for i in range(65, 91)]
alpha = small + big
dic = {}
for flag in alpha:
str = caesar(flag)
dic[str] = flag
str = "SXXHYK{dtzmfajpstbhfjxfw}"
for x in str:
if x.isalpha():
print(dic[x], end="")
else:
print(x, end="")
分析代码知道 这是个静态加密 所以直接先把所有字母对应的密文加到字典里面 然后一一对应
NSSCTF{youhaveknowcaesar}
ez_rsa
为数不多我会写的rsa了

工具算个d 然后再md5加密即可
d=104550CB8E2144921
pigpig
看名字就知道了 所以不想写
traditional
题目:
西方的二进制数学的发明者莱布尼茨,从中国的八卦图当中受到启发,演绎并推论出了数学矩
阵,
最后创造的二进制数学。二进制数学的诞生为计算机的发明奠定了理论基础。而计算机现在改
变
了我们整个世界,改变了我们生活,而他的源头却是来自于八卦图。现在,给你一组由八卦图
方位
组成的密文,你能破解出其中的含义吗?
震坤艮 震艮震 坤巽坤 坤巽震 震巽兑 震艮震 震离艮 震离艮
格式:NSSCTF{}
我想说 差不多得了(
八卦从内向外看 --代表0 —代表1
inp= "震坤艮 震艮震 坤巽坤 坤巽震 震巽兑 震艮震 震离艮 震离艮"
dic={"震":"100","离":"101","兑":"110","乾":"111","坤":"000","艮":"001","坎":"010","巽":"011"}
results= ""
for result in inp:
if result in dic.keys():
results+= dic[result][::-1]+""
else:
results+= " "
print(results)
results=results.split()
for index in range(0,len(results)):
print(chr(int(results[index], 2)), end="")
写成二进制 然后转十进制 然后ascii码
NSSCTF{Da01sall}
misc
你喜欢osu吗?
我喜欢 但不至强行安利 真的(
OSU是一个windows的音游 要是想玩这个谱的话 可以去songs文件夹新建一个文件夹 然后把两个文件扔进去 你就能玩了
复制底下的铺面信息 对 就那一堆数字
224,224,0,5,0,0000
224,160,500,1,8,0000
224,160,1000,1,8,0000
224,160,1500,1,8,0000
224,160,2000,1,8,0000
224,224,2500,1,0,0000
224,160,3000,5,8,0000
224,160,3500,1,8,0000
224,224,4000,1,0,0000
224,224,4500,1,0,0000
224,160,5000,1,8,0000
224,224,5500,1,0,0000
224,224,6000,5,0,0000
224,224,6500,1,0,0000
224,224,7000,1,0,0000
224,160,7500,1,8,0000
224,224,8000,1,0,0000
224,160,8500,1,8,0000
224,160,9000,5,8,0000
224,160,9500,1,8,0000
224,224,10000,1,0,0000
224,160,10500,1,8,0000
224,224,11000,1,0,0000
224,160,11500,1,8,0000
224,224,12000,5,0,0000
224,160,12500,1,8,0000
224,160,13000,1,8,0000
224,160,13500,1,8,0000
224,224,14000,1,0,0000
224,224,14500,1,0,0000
224,160,15000,5,8,0000
224,160,15500,1,8,0000
224,224,16000,1,0,0000
224,160,16500,1,8,0000
224,160,17000,1,8,0000
224,224,17500,1,0,0000
224,160,18000,5,8,0000
224,160,18500,1,8,0000
224,160,19000,1,8,0000
224,160,19500,1,8,0000
224,224,20000,1,0,0000
224,160,20500,1,8,0000
224,224,21000,5,0,0000
224,160,21500,1,8,0000
224,160,22000,1,8,0000
224,160,22500,1,8,0000
224,160,23000,1,8,0000
224,160,23500,1,8,0000
224,224,24000,5,0,0000
224,160,24500,1,8,0000
224,160,25000,1,8,0000
224,224,25500,1,0,0000
224,224,26000,1,0,0000
224,160,26500,1,8,0000
224,224,27000,5,0,0000
224,160,27500,1,8,0000
224,224,28000,1,0,0000
224,160,28500,1,8,0000
224,160,29000,1,8,0000
224,224,29500,1,0,0000
224,160,30000,5,8,0000
224,224,30500,1,0,0000
224,160,31000,1,8,0000
224,160,31500,1,8,0000
224,224,32000,1,0,0000
224,160,32500,1,8,0000
224,160,33000,5,8,0000
224,224,33500,1,0,0000
224,160,34000,1,8,0000
224,224,34500,1,0,0000
224,224,35000,1,0,0000
224,160,35500,1,8,0000
224,224,36000,5,0,0000
224,160,36500,1,8,0000
224,160,37000,1,8,0000
224,224,37500,1,0,0000
224,160,38000,1,8,0000
224,160,38500,1,8,0000
224,224,39000,5,0,0000
224,224,39500,1,0,0000
224,224,40000,1,0,0000
224,160,40500,1,8,0000
224,224,41000,1,0,0000
224,160,41500,1,8,0000
224,160,42000,5,8,0000
224,160,42500,1,8,0000
224,160,43000,1,8,0000
224,160,43500,1,8,0000
224,224,44000,1,0,0000
224,160,44500,1,8,0000
224,160,45000,5,8,0000
224,160,45500,1,8,0000
224,224,46000,1,0,0000
224,160,46500,1,8,0000
224,224,47000,1,0,0000
224,160,47500,1,8,0000
224,224,48000,5,0,0000
224,160,48500,1,8,0000
224,160,49000,1,8,0000
224,224,49500,1,0,0000
224,160,50000,1,8,0000
224,160,50500,1,8,0000
224,160,51000,5,8,0000
224,160,51500,1,8,0000
224,224,52000,1,0,0000
224,160,52500,1,8,0000
224,160,53000,1,8,0000
224,160,53500,1,8,0000
224,160,54000,5,8,0000
224,224,54500,1,0,0000
224,224,55000,1,0,0000
224,160,55500,1,8,0000
224,224,56000,1,0,0000
224,160,56500,1,8,0000
224,224,57000,5,0,0000
224,160,57500,1,8,0000
224,160,58000,1,8,0000
224,160,58500,1,8,0000
224,160,59000,1,8,0000
224,160,59500,1,8,0000
224,224,60000,5,0,0000
224,160,60500,1,8,0000
224,160,61000,1,8,0000
224,160,61500,1,8,0000
224,224,62000,1,0,0000
224,160,62500,1,8,0000
224,160,63000,5,8,0000
224,160,63500,1,8,0000
224,224,64000,1,0,0000
224,160,64500,1,8,0000
224,160,65000,1,8,0000
224,224,65500,1,0,0000
224,160,66000,5,8,0000
224,160,66500,1,8,0000
224,160,67000,1,8,0000
224,160,67500,1,8,0000
224,224,68000,1,0,0000
224,160,68500,1,8,0000
224,160,69000,5,8,0000
224,224,69500,1,0,0000
224,160,70000,1,8,0000
224,160,70500,1,8,0000
224,160,71000,1,8,0000
224,224,71500,1,0,0000
224,224,72000,5,0,0000
224,160,72500,1,8,0000
224,160,73000,1,8,0000
224,224,73500,1,0,0000
224,160,74000,1,8,0000
224,224,74500,1,0,0000
224,160,75000,5,8,0000
224,160,75500,1,8,0000
224,224,76000,1,0,0000
224,160,76500,1,8,0000
224,224,77000,1,0,0000
224,160,77500,1,8,0000
224,160,78000,5,8,0000
224,160,78500,1,8,0000
224,160,79000,1,8,0000
224,160,79500,1,8,0000
224,224,80000,1,0,0000
224,160,80500,1,8,0000
224,160,81000,5,8,0000
224,224,81500,1,0,0000
224,160,82000,1,8,0000
224,224,82500,1,0,0000
224,224,83000,1,0,0000
224,160,83500,1,8,0000
224,224,84000,5,0,0000
224,160,84500,1,8,0000
224,160,85000,1,8,0000
224,160,85500,1,8,0000
224,160,86000,1,8,0000
224,160,86500,1,8,0000
224,224,87000,5,0,0000
224,160,87500,1,8,0000
224,224,88000,1,0,0000
224,160,88500,1,8,0000
224,224,89000,1,0,0000
224,224,89500,1,0,0000
224,224,90000,5,0,0000
224,160,90500,1,8,0000
224,160,91000,1,8,0000
224,224,91500,1,0,0000
224,224,92000,1,0,0000
224,160,92500,1,8,0000
224,224,93000,5,0,0000
224,160,93500,1,8,0000
224,224,94000,1,0,0000
224,160,94500,1,8,0000
224,224,95000,1,0,0000
224,224,95500,1,0,0000
224,224,96000,5,0,0000
224,160,96500,1,8,0000
224,224,97000,1,0,0000
224,224,97500,1,0,0000
224,224,98000,1,0,0000
224,224,98500,1,0,0000
224,160,99000,5,8,0000
224,160,99500,1,8,0000
224,224,100000,1,0,0000
224,160,100500,1,8,0000
224,224,101000,1,0,0000
224,160,101500,1,8,0000
然后观察嘛 第二个数字 224转为0 160转为1 然后8位转换一个十进制 当ascii码用 最后来个翻转
import re
if __name__ == '__main__':
with open("a.txt", "r")as file:
s = file.read()
s = s.split("\n")
for index in range(0, len(s)):
s[index] = s[index].split(",")[1]
if s[index] == "224":
s[index] = "0"
else:
s[index] = "1"
s="".join(s)
zero_one=re.findall(".{8}",s)
r=[]
for x in zero_one:
r.append(chr(int(x,2)))
print("".join(r[::-1]))
here_is_a_bug
真的 我一定是非预期解
右键文件夹 使用杀毒软件杀毒(

打开得知flag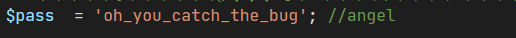
NSSCTF{oh_you_catch_the_bug}
原来你也玩原神
异世相遇 尽享美味!
file命令知道是个mp3
看了频谱文件 不是摩斯啥的
用MP3stego解密 密码留空就行
解密出一个txt文件 看内容有PK
后缀名改为.zip
里面一个txt

NSSCTF{So_you_also_play_Genshin_impact}
Mooooooooooorse
AU打开 你拿别的音频软件打开也行 敲个摩斯码
解密就行了
文件已经忘了 不想再敲了
Bill
看提示应该是个excel表格
后缀改为.xlsx 但是有密码
说不要被表象迷惑 猜测可能是有隐写或者伪加密
foremost分离得到压缩包
后缀名再改xlsx打开文件
然后修改一下excel表格 把所有的都换成中文大写数字之后 把脚本拿出来
(上次DAS也有算钱的题...那个表格还比这个长
import openpyxl
import re
def trad_to_int(money):
# 转换字典
trad_dict = {
'零':0,
'壹':1,
'贰':2,
'叁':3,
'肆':4,
'伍':5,
'陆':6,
'柒':7,
'捌':8,
'玖':9,
'拾':10,
'佰':100,
'仟':1000,
'万':10000,
'亿':100000000,
'角':0.1,
'分':0.01
}
trad = re.search(r"[零壹贰叁肆伍陆柒捌玖拾佰仟亿角分]+", money)
if trad is not None:
num = 0
add = 0
sum = 0
for i in money:
if i in ['零','壹','贰','叁','肆','伍','陆','柒','捌','玖']:
add = trad_dict[i]
sum = sum + add
elif i in ['拾','佰','仟','亿','角','分']:
num = add * trad_dict[i]
sum = sum - add
sum = sum + num
add = num
elif i == '万' or i == '亿':
sum = sum * trad_dict[i]
return float(sum)
else:
return money
def main():
submoneyCN = ["", "拾", "佰", "仟"]
numsCN = {"零": 0, "壹": 1, "贰": 2, "叁": 3, "肆": 4, "伍": 5, "陆": 6, "柒": 7, "捌": 8, "玖": 9}
w = openpyxl.open("00000025.xlsx")
ws = w.active
# 获取第一列 即单件商品金额
t = ws['A']
t1=[]
for x in range(1,len(t)):
t1.append(trad_to_int(t[x].value))
print(t1)
# 获取第二列并处理
t = ws['B']
t2=[]
for x in range(1,len(t)):
t2.append(trad_to_int(t[x].value))
print(t2)
r=0
for index in range(0,len(t2)):
r+=float(t1[index])*float(t2[index])
print(r)
if __name__ == '__main__':
main()
跑脚本
NSSCTF{5030782.26}
ZIPBOMB
我也不知道他为啥没炸 反正我直接解压了
010中得flag
NSSCTF{Z1p_B00m_d1sp0sal}
gif好像有点大
那确实挺大得 最开始以为是隐写
看了看gif发现他只是长而已...
拆分gif脚本
from PIL import Image
import os
pic=Image.open("CTF.gif")
try:
i=0
while True:
pic.seek(i)#搜寻文件帧数
pic.save(str(i)+".png")
i+=1
except:
pass
然后有一帧里面有个二维码 扫描即可
swpu新生赛ctf wp的更多相关文章
- SCNU ACM 2016新生赛初赛 解题报告
新生初赛题目.解题思路.参考代码一览 1001. 无聊的日常 Problem Description 两位小朋友小A和小B无聊时玩了个游戏,在限定时间内说出一排数字,那边说出的数大就赢,你的工作是帮他 ...
- SCNU 2015ACM新生赛决赛【F. Oyk闯机关】解题报告
题目大意:一个$N$$\times$$N$的阵列,每个格子有$X_{ij}$个调和之音,若每次只能选择走右边或下边,从左上角出发走到右下角,问最多能收集到多少个调和之音? ...
- Codeforces 801 A.Vicious Keyboard & Jxnu Group Programming Ladder Tournament 2017江西师大新生赛 L1-2.叶神的字符串
A. Vicious Keyboard time limit per test 2 seconds memory limit per test 256 megabytes input standard ...
- [ACTF2020 新生赛]BackupFile && [ACTF2020 新生赛]Upload &&[GYCTF2020]Blacklist
[ACTF2020 新生赛]BackupFile 尝试找到源代码,加上题目是备份文件,猜测备份文件里面有网站的源代码,御剑扫描一下,就扫到index.php 访问index.php.bak 下载源代码 ...
- [BUUCTF]REVERSE——[ACTF新生赛2020]Oruga
[ACTF新生赛2020]Oruga 附件 步骤: 例行检查,64位程序,无壳 64位ida载入,检索字符串,根据提示来到关键函数 14行~18行就是让字符串的前5位是 actf{ ,sub_78A( ...
- [BUUCTF]REVERSE——[ACTF新生赛2020]usualCrypt
[ACTF新生赛2020]usualCrypt 附件 步骤: 例行检查,无壳,32位程序 32位ida载入,直接看main函数 逻辑很简单,一开始让我们输入一个字符串,然后该字符串经过sub_4010 ...
- [BUUCTF]REVERSE——[ACTF新生赛2020]rome
[ACTF新生赛2020]rome 附件 步骤 无壳,32位程序 32位ida载入,根据提示字符串"You are correct!",找到关键函数func v15 = 'Q'; ...
- [BUUCTF]REVERSE——[ACTF新生赛2020]easyre
[ACTF新生赛2020]easyre 附件 步骤 查壳,32位程序,upx壳儿 脱完壳儿,扔进ida 分析 一开始给我们定义了一个数组, v4=[42,70,39,34,78,44,34,40,73 ...
- SCNU ACM 2016新生赛决赛 解题报告
新生初赛题目.解题思路.参考代码一览 A. 拒绝虐狗 Problem Description CZJ 去排队打饭的时候看到前面有几对情侣秀恩爱,作为单身狗的 CZJ 表示很难受. 现在给出一个字符串代 ...
随机推荐
- 自动化怎么判断anndroid.listview是否包含某个指定的元素或内容
做自动化的时候,定位元素时,会发现整屏的内容都是放在一个列表,在多层嵌套其他控件组成 如柠檬班的题库,里面会有很多分类 那么在做自动化的时候,怎么判断页面有没有包含指定的分类呢? 整体思路: 1.找到 ...
- Jenkins_构建任务提示找不到命令的处理方法
问题现象 部署pytest环境后,在linux上能执行命令,但是使用jenkins构建就提示找不到命令. 问题分析 可能是...jenkins中执行时,默认使用的是linux中的jenkins用户权限 ...
- spring cloud --- 使用 actuator 热更新【刷新】单机配置文件
1.前言 分布式微服务想要热更新配置文件,还需要 消息中间件 配合使用 ,一般使用 rabbitMQ 或 Kafka ,这里不解释 . 这篇随笔 只讲解 底层的 单机热更新配置文件 2.环境 spri ...
- Linux上天之路(十)之Linux磁盘管理
主要内容 磁盘介绍 磁盘管理 磁盘限额 逻辑卷管理 磁盘阵列 1. 磁盘介绍 硬盘最基本的组成部分是由坚硬金属材料制成的涂以磁性介质的盘片,不同容量硬盘的盘片数不等.每个盘片有两面,都可记录信息.盘片 ...
- 离线下载第三方Python包
1.进入Python第三方包下载地(https://pypi.org/)搜索自己需要的包 2.下载需要的包的版本 3.将.whl格式的文件更改为.zip文件,并且解压 4.将解压的2个文件放到Pyth ...
- vue3代码setup中this为什么无效
结论:setup并没有通过各种方式去绑定this 在vue2中,我们可以在optionsApi中调用this来指向当前组件的实例,但是在vue3的setup中并不能这样做,因为setup位于组件创建成 ...
- 如何管理leader对你的能力预期?
在内网看到一个讨论帖,原文如下: 如何管理leader对你的能力预期? 你一个项目做得好,之后类似项目,leader认为你也就是合格水平,而且认为你只会做这种项目. SAD.. 思考 在开始之前先想下 ...
- eclipse导入项目jdk版本不一样
一:eclipse导入项目jdk版本不一样解决方案 参考博文: https://www.cnblogs.com/chenmingjun/p/8472885.html 选中项目右键 --> Pro ...
- 【刷题-PAT】A1101 Quick Sort (25 分)
1101 Quick Sort (25 分) There is a classical process named partition in the famous quick sort algorit ...
- 【解决了一个小问题】golang xorm中使用where id in (xxx),没办法使用参数替换
代码中使用XORM来从数据库查询数据,有类似如下的代码: session.Where("id in (?)", strings,Join(arr, ",")) ...
