USING KERBEROS
3.1. About Kerberos
3.1.1. How Kerberos Works
kinitprogram after the user logs in.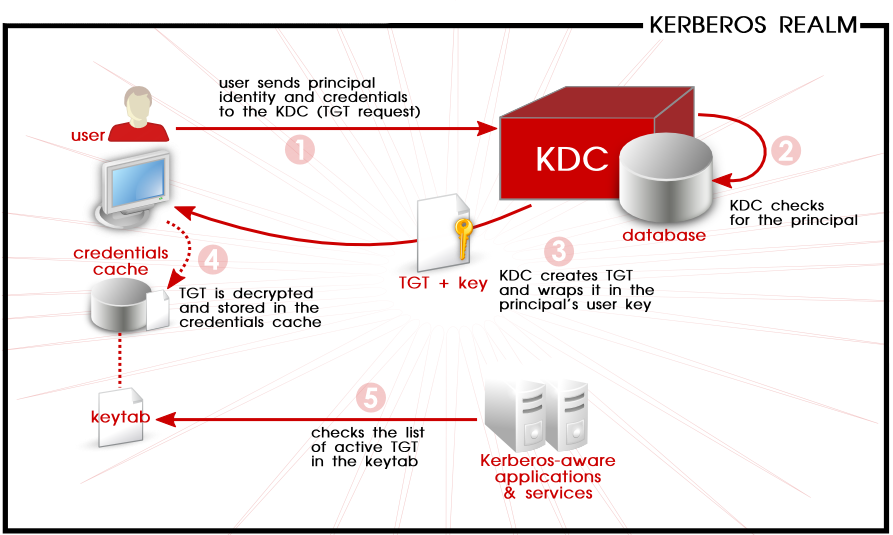
Figure 3.1. Kerberos Authentication, in Steps
kinit program on the client then decrypts the TGT using the user's key, which it computes from the user's password. The user's key is used only on the client machine and is not transmitted over the network. The ticket (or credentials) sent by the KDC are stored in a local file, the credentials cache, which can be checked by Kerberos-aware services.kinit; this is kept in a keytab.Warning
- Approximate clock synchronization between the machines on the network can be set up using a service such as
ntpd, which is documented in/usr/share/doc/ntp-version-number/html/index.html. - Both DNS entries and hosts on the network must be properly configured, which is covered in the Kerberos documentation in
/usr/share/doc/krb5-server-version-number.
3.1.2. Considerations for Deploying Kerberos
- Migrating user passwords from a standard UNIX password database, such as
/etc/passwdor/etc/shadow, to a Kerberos password database can be tedious. There is no automated mechanism to perform this task. This is covered in question 2.23 in the online Kerberos FAQ for the US Navy. - Kerberos assumes that each user is trusted but is using an untrusted host on an untrusted network. Its primary goal is to prevent unencrypted passwords from being transmitted across that network. However, if anyone other than the proper user has access to the one host that issues tickets used for authentication — the KDC — the entire Kerberos authentication system are at risk.
- For an application to use Kerberos, its source must be modified to make the appropriate calls into the Kerberos libraries. Applications modified in this way are considered to be Kerberos-aware, or kerberized. For some applications, this can be quite problematic due to the size of the application or its design. For other incompatible applications, changes must be made to the way in which the server and client communicate. Again, this can require extensive programming. Closed-source applications that do not have Kerberos support by default are often the most problematic.
- Kerberos is an all-or-nothing solution. If Kerberos is used on the network, any unencrypted passwords transferred to a non-Kerberos aware service are at risk. Thus, the network gains no benefit from the use of Kerberos. To secure a network with Kerberos, one must either use Kerberos-aware versions of all client/server applications that transmit passwords unencrypted, or not use that client/server application at all.
3.1.3. Additional Resources for Kerberos
Table 3.1. External Kerberos Documentation
| Documentation | Location |
|---|---|
| Kerberos V5 Installation Guide (in both PostScript and HTML) | /usr/share/doc/krb5-server-version-number |
| Kerberos V5 System Administrator's Guide (in both PostScript and HTML) | /usr/share/doc/krb5-server-version-number |
| Kerberos V5 UNIX User's Guide (in both PostScript and HTML) | /usr/share/doc/krb5-workstation-version-number |
| "Kerberos: The Network Authentication Protocol" webpage from MIT | http://web.mit.edu/kerberos/www/ |
| The Kerberos Frequently Asked Questions (FAQ) | http://www.cmf.nrl.navy.mil/CCS/people/kenh/kerberos-faq.html |
| Designing an Authentication System: a Dialogue in Four Scenes, originally by Bill Bryant in 1988, modified by Theodore Ts'o in 1997. This document is a conversation between two developers who are thinking through the creation of a Kerberos-style authentication system. The conversational style of the discussion makes this a good starting place for people who are completely unfamiliar with Kerberos. | http://web.mit.edu/kerberos/www/dialogue.html |
| A how-to article for kerberizing a network. | http://www.ornl.gov/~jar/HowToKerb.html |
man command_name.Table 3.2. Important Kerberos Manpages
| Manpage | Description |
|---|---|
| Client Applications | |
| kerberos | An introduction to the Kerberos system which describes how credentials work and provides recommendations for obtaining and destroying Kerberos tickets. The bottom of the man page references a number of related man pages. |
| kinit | Describes how to use this command to obtain and cache a ticket-granting ticket. |
| kdestroy | Describes how to use this command to destroy Kerberos credentials. |
| klist | Describes how to use this command to list cached Kerberos credentials. |
| Administrative Applications | |
| kadmin | Describes how to use this command to administer the Kerberos V5 database. |
| kdb5_util | Describes how to use this command to create and perform low-level administrative functions on the Kerberos V5 database. |
| Server Applications | |
| krb5kdc | Describes available command line options for the Kerberos V5 KDC. |
| kadmind | Describes available command line options for the Kerberos V5 administration server. |
| Configuration Files | |
| krb5.conf | Describes the format and options available within the configuration file for the Kerberos V5 library. |
| kdc.conf | Describes the format and options available within the configuration file for the Kerberos V5 AS and KDC. |
USING KERBEROS的更多相关文章
- Kerberos简介
Kerberos协议: Kerberos协议主要用于计算机网络的身份鉴别(Authentication), 其特点是用户只需输入一次身份验证信息就可以凭借此验证获得的票据(ticket-grantin ...
- [Kerberos] Java client访问kerberos-secured cluster
使用java client访问kerberos-secured cluster,最重要的是先从admin那里拿到可用的keytab文件,用来作认证.接下来就是调整连接的配置.以下先用连接hdfs为例进 ...
- [Kerberos] Kerberos 认证过程整理
Kerberos是一种安全认证协议,意在提供 more secure authentication simplified management of password convenience of s ...
- [Kerberos] User Ticket Management
Kerberos客户端常用命令包括 kinit, klist, kdestroy, and kpasswd,用户使用这些命令管理自己的 ticket. 此外,每台运行Kerberos的机器应该都配置/ ...
- Kerberos
一.Kerberos Concept Kerberos是一种网络认证协议,其设计目标是通过密钥系统为客户机/服务器应用程序提供强大的认证服务,为通信双方提供双向身份认证. Kerberos关键术语: ...
- Kerberos是怎么工作的?
Kerberos是一种计算机网络授权协议,用来在非安全网络中,对个人通信以安全的手段进行身份认证. 采用客户端/服务器结构,并且能够进行相互认证,即客户端和服务器端均可对对方进行身份认证. 关键要素 ...
- ldap + kerberos + google authentication 实现两步验证
第一步:ldap + kerberos 整合 ,参考之前的文章 第二步:google authentication 安装配置,参考之前的文章 第三步:整合 ldap + kerberos + goo ...
- ldap + kerberos 整合
第一部分:ldap1. 安装ldap yum install -y openldap openldap-clients openldap-servers openldap-devel 2. 配置lda ...
- Kerberos简介及常见问题
基本描述 Kerberos使用Needha-Schroeder协议作为它的基础.它使用了一个由两个独立的逻辑部分:认证服务器和票据授权服务器组成的"可信赖的第三方",术语称为密钥分 ...
- 在 Java 代码中对 Kerberos 主体进行身份验证
转载请注明出处:http://www.cnblogs.com/xiaodf/ 本文举例说明如何使用 org.apache.hadoop.security.UserGroupInformation 类在 ...
随机推荐
- asp.net core系列 32 EF查询数据 必备知识(1)
一.查询的工作原理 Entity Framework Core 使用语言集成查询 (LINQ) 来查询数据库中的数据. 通过 LINQ 可使用 C#(或你选择的其他 .NET 语言)基于派生上下文和实 ...
- VueJs 源码分析 ---(二)实力化生命周期,以及解析模版和监听数据变化
Vue 源码第二步 当前 Vue 的版本 V2.2.2 生命周期 相关介绍 我们可以从 setp1 中 去看到那张 vue 的生命周期图中看到,vue 的生命周期钩子. 具体的钩子时干什么的? 以及在 ...
- 使用mpvue开发小程序教程(三)
在上一篇文章中,我们熟悉了一下通过vue-cli生成的mpvue工程代码骨架的基本结构,大致了解了每一个部分的代码到底要放到何处.从本文起我们就开始涉及真正的编码部分,学习使用Vue的语法去编写小程序 ...
- 【ASP.NET Core快速入门】(九) RoutingMiddleware介绍以及MVC引入
前言 前面我们介绍了使用app.Map来配置路由,但是对于一般不是特别大的项目来说,我们不使用Map来进行路由配置. 配置路由 我们首先需要在Startup.cs文件中的ConfigureServic ...
- 修改sql数据库名称
USE master; GO DECLARE @SQL VARCHAR(MAX); SET @SQL='' SELECT @SQL=@SQL+'; KILL '+RTRIM(SPID) FROM ma ...
- [四] JavaIO之类层次体系结构横向比对
IO家族类层次体系结构横向匹配 上一篇文章中主要介绍了JavaIO流家族的整体设计思路,简单回顾下 基本逻辑涉及数据源 流的方向,以及流的数据形式这三个部分的组合 按照流的数据形式和流的方向, ...
- 痞子衡嵌入式:ARM Cortex-M文件那些事(7)- 反汇编文件(.s/.lst/.dump)
大家好,我是痞子衡,是正经搞技术的痞子.今天痞子衡给大家讲的是嵌入式开发里的反汇编文件(.s, .lst, .dump). 痞子衡在第四.五.六节课分别介绍了编译器/链接器生成的3种output文件( ...
- Docker搭建MongoDB
1. Docker搭建Mongodb 1.1 获取docker镜像 docker pull mongo 1.2 创建mongodb容器 docker run --name my-mongo -p 27 ...
- Java开发笔记(十八)上下求索的while循环
循环是流程控制的又一重要结构,“白天-黑夜-白天-黑夜”属于时间上的循环,古人“年复一年.日复一日”的“日出而作.日落而息”便是每天周而复始的生活.计算机程序处理循环结构时,给定一段每次都要执行的代码 ...
- 41.Odoo产品分析 (四) – 工具板块(10) – 问卷(1)
查看Odoo产品分析系列--目录 在该模块下,可以创建问卷,收集答案,打印统计. 安装"问卷"模块,首页显示当前各个阶段中的问卷: 打开"开发者模式",能对 ...
