Gathering Fingerprinting
1、 Banner grabbing with Netcat
Netcat is multipurpose networking tool that can be used to perform multiple information gathering an d scanning tasks with kali linux ,this specific recipe will demonstrate how to use Netcat to acquire service banners in order to identify the service banners eto indetify the service association with open ports on a target system .
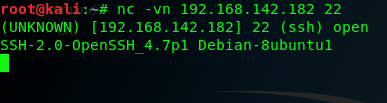
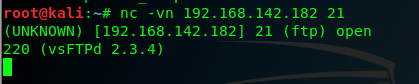
To use the Netcat to grab service banners , on must establish a socket connection to the intended port on the remote system .to quickly understand the usage of the Netcat an how it can be used for thhis purpose ,one can call upon the usage output, we can use the command nc -h option :
2、the -v opton was used to provide verbose output and the the -n option was used to connnect with the the ip address without DNS resolution , we can see the banner returned by the remote host identifies the service as SSH ,the vendor as openSSH,besides , we can use the siminal scan on port 21 of the same the system ,we can easily acqurie service and the version information ot the running TFP service .
2、Banner grabbing with Python sockets
the sockets mouule in python can be used to connect to network services running on remote ports . Once can interact directly with remote network service using the python interactive interpreter ,you can begin use the python interpreter by calling it driectly m in this here ,we can import any specific modules tha you wish to use , the specific is as follows :

the AF_INET arguments is used to indicate that the socket will employed an IPV4 address and the SOCK_STREAM argument is used to indicate that TCP transport will be used ,if an attempt is made to connect to TCP port 443 on the Metasploitable2 system ,an error will be returned indiciate taht the connection was refused , because there is no service running on this remote system
3、 use the python script to connect
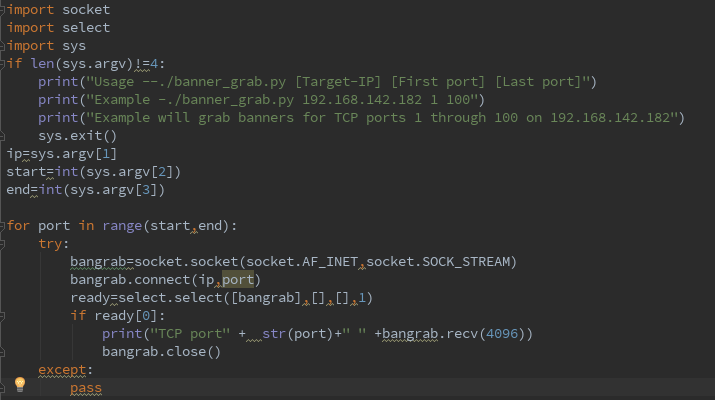
the python script what just i note by utilizing the socket library ,the script loops through each of the specified target port address an attempts to initialize a TCP connection with that pratical port ,if a connection is established and a banner is recived from the target service , the banner will then be printed in the output of the script ,of course ,if a connection cannot be established with the remote port ,the script will then move to the next port address value in the loop.
4、Banner grabbing with Dmitry
Dmitry is a simple yet streamlined tool that can be used to connect to network services running on remote ports .Dmitry can be used to run a quick TCP ports scan on 150 of the remote commonly used services , this can be done using the -p option:
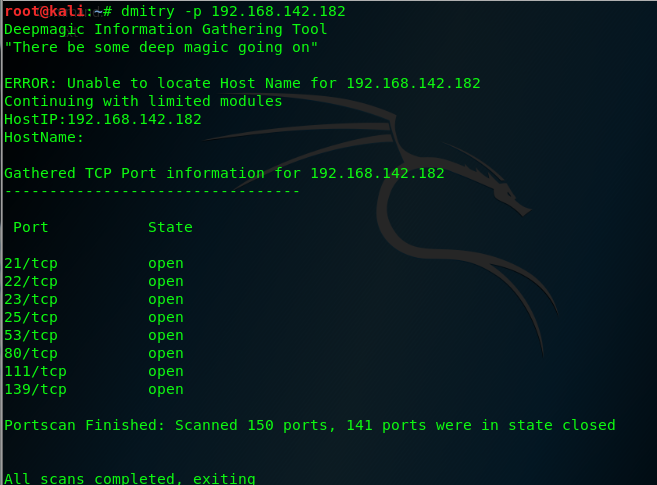
Dmitry is a simple command-line tool that can perform the task of banner grabbing with minimal overhead .Dmitry can streanline the process by only attempting banner grabbing on a small selection of predefined an dcommonly used ports, banners recived from services running on those port address are then returned in the terminal output of the script
5、Banner grabbing with Nmap NES
nmap has an intergateed Nmap Script Engrine script that can be used to read banners from network services running on remote ports , we can use the script ,use command --script option in Nmap and then specifiying the name of the descried script , for this particular script a -sT full-connect scan shjould be used as service banners can only be collected when a full TCP conection is established , the script will be applied to the same ports that are scanned by te fellows requests:
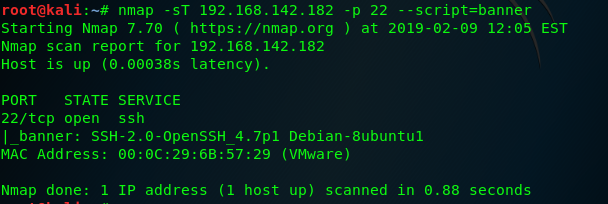
Nmap used the banner script to collect the service banner associated with the port , this same technical can be replied to a sequential range of the ports suing the --notation
the example command : nmap -sT 192.168.142.182 -p 1-100 --script=banner
6、Banner grabbing with Amap
Amap is an application-mapping tool that can be used read banners from network services running on remote ports , The -B option in Amap can be used to run the application in banner mode , this will have it collect banners for the specific IP address and service ports ,Amap can be used to collect the banner from a single service by specifying the remote IP address and service number :
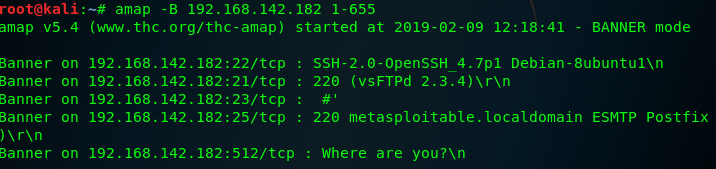
to remove the scan metadata ,we can use grep the optput for a phrase that is unique to specific output entries and does not exist in the scan's metadata . we can use the command : amap -B 192.168.142.182 1-65535 | grep "on"
7、service identification with Nmap
first we can connect with the Metasploitable2 system by TCP : nc -nv 192.168.142.182 80 then to execute an Nmap service scan on the same port ,we can use the -sV option in conjunction eith the IP and Port specification : nmap 192.168.142.182 -p 80 -sV

this service identification function can also be used against a specific sequential series of ports ,if no port specificed ,the 1000 common ports will be scanned and identification attempts will be made for all listening services that are identified .
8、Service identification with Amap
to perform service identification on a single port , run Amap, with the ip address and port number specifications : amap 192.168.142.182 80

amap can also be used to scan a senquential servies of port numbers using dash notation . amap 192.168.142.182 20-90 To supress the information about unidentified ports , the -q option can be used : amap 192.168.142.182 1-100 -q and the banners can be appended to the output associated with each port using -n option :
amap 192.168.142.182 1-100 -qb
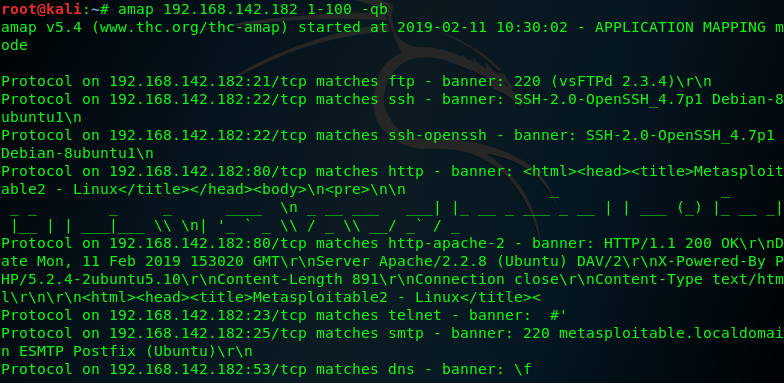
but amap is not updated and well-maintained in the same way that Nmap is ,as such, Aamp is less likely to produce reliable results
9、Operating system identification with Scapy
we know windows and linux/Unix operating systems have different TTL starting values that are used by default ,this factor can be used to attempt to fingerprint the type of operating system:
generally speaking the Windows TTL=128 and the Linux/Unix OS TTL=64 but TTL valus can modify .
and then we create both IP and ICMP layer , we need to construct the request by stacking those layse:
first construct the IP layer : linux= "192.168.142.182"
windows= "192.168.1.101"
i=IP()
i.dst=linux
ping=ICMP()
request=(i/ping)
ans=sr1(request)
the follow figure is Linux TTL

the follow figure is Windows TTL

addination , we can use the python test the TTL values
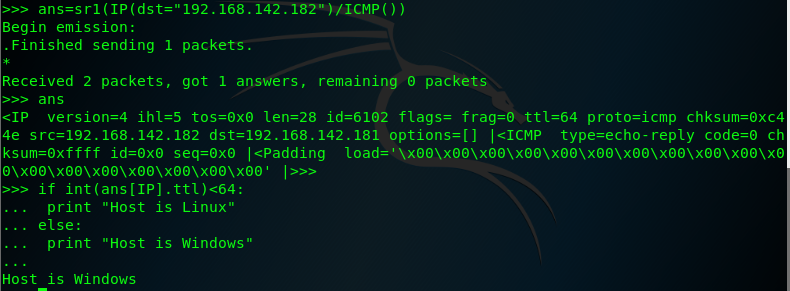
note the Scapy must use Python Version is 2.7
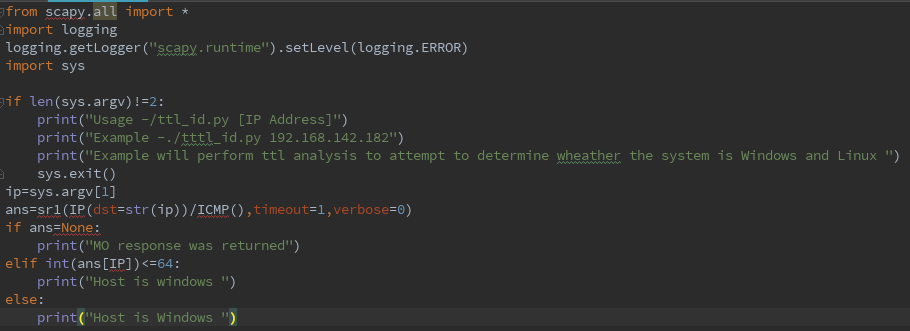
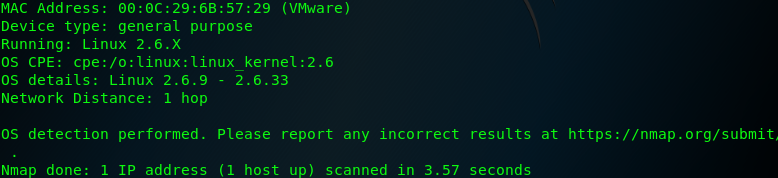
10、Operating system identification with Nmap
to perform an Nmap operating system identificatio scan , Nmap should be called with the IP adddress specificatio adn the -O option : nmap 192.168.142.182 -O
the Nmap operating system identification sends a comprehensive series of probing requests and analyzes the responses to those quests in attempt to identify the undering operating system based on Os-specific signature and expected behavior,
11、Operating System identificatio with xProbe2
the progrm needs to be passed a single argument that consists of the IP address of the system to be scanned
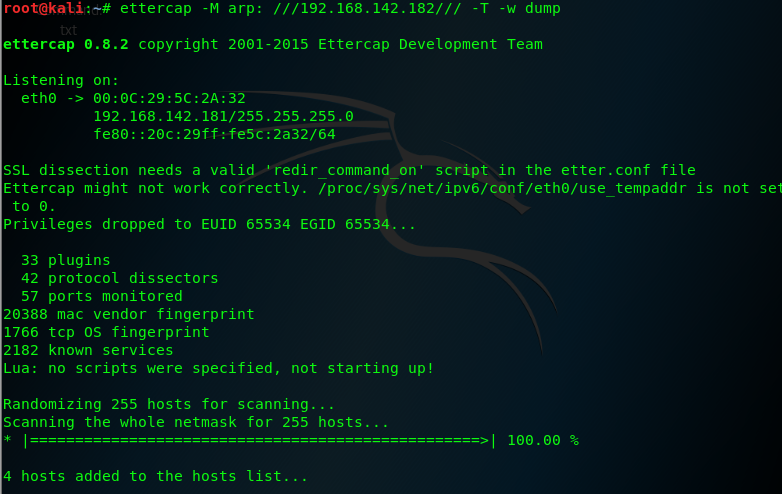
11、Passive operating system identificatio with p0f
the tool perform operating system identification passively and without drectly intercacting with the target system

12、Snmp analysis with Onesixtyone
Onesixtyone is an Snmap tool that is named for the UDP port upon with SNMP operate it is a very simple SNMP scanner that only requests the system description value for any specific IP address , SNMP is a protocol that can be used to manage netwoeked device and facilitate the sharing of information across those device , the usage of this protocol is often necessary in enterprise network environment.
additional we can use the SNMPwalk analysis the remote system device . SNmpwalk cycle througha series of request to gather as much informationas possible from the service .
13、 Firewall identification with Scapy
to perform an Nmap SCK scan ,Nmap shjould be called with the ip address sepcification , the destination port ,and the -sA option :
nmap -sA 192.168.142.182 -p 22

notice that when we scanning a range of ports , the output only includes unfiltered ports:
nmap -sA 83.166.169.228
13、 to use Metasploit ACK scan module to perform firewall and filtering identification. for more systems , 25 threads is a fast and reasonably safe number of concurrent processes .

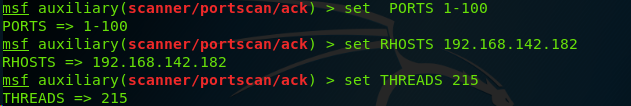
Metasploit offers auxiliary module that perform firewall identification through many of teh some techniques that have been discussed in the previous recipe ,however, metasploit also offers the capbility to perform this analysis with the context of a farmework that can be used for other information gathering and even exploitation ,as well .
Gathering Fingerprinting的更多相关文章
- 帆布指纹识别(canvas fingerprinting)
广告联盟或许网站运营者都希望能够精准定位并标识每一个个体,通过对用户行为的分析(浏览了哪些页面?搜索了哪些关键字?对什么感兴趣?点了哪些按钮?用了哪些功能?看了哪些商品?把哪些放入了购物车等等),为用 ...
- ACM ICPC 2015 Moscow Subregional Russia, Moscow, Dolgoprudny, October, 18, 2015 G. Garden Gathering
Problem G. Garden Gathering Input file: standard input Output file: standard output Time limit: 3 se ...
- Requirements Gathering
Requirements gathering is an essential part of any project and project management. Understanding ful ...
- Gathering Initial Troubleshooting Information for Analysis of ORA-4031 Errors on the Shared Pool
In this Document Purpose Troubleshooting Steps References APPLIES TO: Oracle Database - Enterp ...
- Family Gathering at Christmas(思维题)
Family Gathering at Christmas 时间限制: 1 Sec 内存限制: 128 MB提交: 13 解决: 4[提交] [状态] [讨论版] [命题人:admin] 题目描述 ...
- codechef May Challenge 2016 FORESTGA: Forest Gathering 二分
Description All submissions for this problem are available. Read problems statements in Mandarin Chi ...
- MaLoc: a practical magnetic fingerprinting approach to indoor localization using smartphones
https://www.indooratlas.com/ MaLoc: a practical magnetic fingerprinting approach to indoor localizat ...
- Magnetic Fingerprinting Approach to Indoor Localization
Magnetic Fingerprinting Approach to Indoor Localization
- HDU - 5887 2016青岛网络赛 Herbs Gathering(形似01背包的搜索)
Herbs Gathering 10.76% 1000ms 32768K Collecting one's own plants for use as herbal medicines is pe ...
随机推荐
- EChars学习之路1
引入echarts.min.js或者使用CDN https://cdn.bootcss.com/echarts/4.2.1-rc1/echarts.min.js 为ECharts准备一个具备大小(宽高 ...
- 深入Eureka/Feign/Hystrix原理学习(1)
第一步: 创建注册中心项目,引入cloud discovery相关依赖. ①在pom文件中引入相关依赖. ②在启动类上加上@EnableEurekaServer注解,标注这是一个注 册中心. ③在ap ...
- eclipse(STS)安装jd-eclipse插件实现查看API源代码功能
emmm,IDEA确实是比STS智能很多,不过适当的转化也是需要的,这里介绍一下eclipse(STS)实现查看class反编译的源文件的功能 去Java Decompiler官网下一下eclipse ...
- Python——Window启动服务
一.新建启动服务程序 # ZPF # encoding=utf-8 import win32timezone from logging.handlers import TimedRotatingFil ...
- 用Pytorch训练MNIST分类模型
本次分类问题使用的数据集是MNIST,每个图像的大小为\(28*28\). 编写代码的步骤如下 载入数据集,分别为训练集和测试集 让数据集可以迭代 定义模型,定义损失函数,训练模型 代码 import ...
- Java【第九篇】异常处理
异常概述 介绍 任何一种程序设计语言设计的程序在运行时都有可能出现错误,例如除数为0,数组下标越界,要读写的文件不存在等等.捕获错误最理想的是在编译期间,但有的错误只有在运行时才会发生.对于这些错误, ...
- Python【第三篇】文件操作、字符编码
一.文件操作 文件操作分为三个步骤:文件打开.操作文件.关闭文件,但是,我们可以用with来管理文件操作,这样就不需要手动来关闭文件. 实现原理: import contextlib @context ...
- Prometheus监控elasticsearch集群(以elasticsearch-6.4.2版本为例)
部署elasticsearch集群,配置文件可"浓缩"为以下: cluster.name: es_cluster node.name: node1 path.data: /app/ ...
- CF757E Bash Plays with Functions
题解 q<=1e6,询问非常多.而n,r也很大,必须要预处理所有的答案,询问的时候,能比较快速地查询. 离线也是没有什么意义的,因为必须递推. 先翻译$f_0(n)$ $f_0(n)=\sum_ ...
- CF914G Sum the Fibonacci
解:发现我们对a和b做一个集合卷积,对d和e做一个^FWT,然后把这三个全部对位乘上斐波那契数,然后做&FWT就行了. #include <bits/stdc++.h> , MO ...
