POJ - 1107 W's Cipher
POJ - 1107 W's Cipher
Time Limit: 1000MS |
Memory Limit: 10000KB |
64bit IO Format: %I64d & %I64u |
Description
Weird Wally's Wireless Widgets, Inc. manufactures an eclectic assortment of small, wireless, network capable devices, ranging from dog collars, to pencils, to fishing bobbers. All these devices have very small memories. Encryption algorithms like Rijndael, the candidate for the Advanced Encryption Standard (AES) are demonstrably secure but they don't fit in such a tiny memory. In order to provide some security for transmissions to and from the devices, WWWW uses the following algorithm, which you are to implement.
Encrypting a message requires three integer keys, k1, k2, and k3. The letters [a-i] form one group, [j-r] a second group, and everything else ([s-z] and underscore) the third group. Within each group the letters are rotated left by ki positions in the message. Each group is rotated independently of the other two. Decrypting the message means doing a right rotation by ki positions within each group.
Consider the message the_quick_brown_fox encrypted with ki values of 2, 3 and 1. The encrypted string is _icuo_bfnwhoq_kxert. The figure below shows the decrypting right rotations for one character in each of the three character groups.
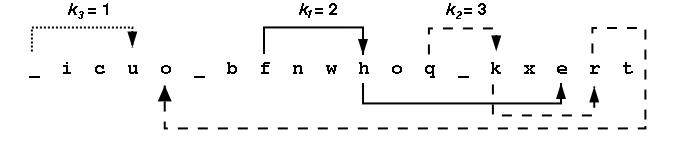
Looking at all the letters in the group [a-i] we see {i,c,b,f,h,e} appear at positions {2,3,7,8,11,17} within the encrypted message. After a right rotation of k1=2, these positions contain the letters {h,e,i,c,b,f}. The table below shows the intermediate strings that come from doing all the rotations in the first group, then all rotations in the second group, then all the rotations in the third group. Rotating letters in one group will not change any letters in any of the other groups.
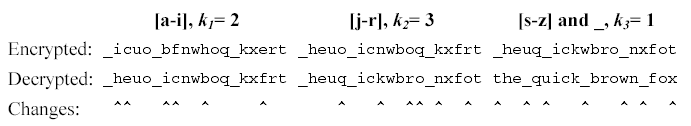
All input strings contain only lowercase letters and underscores(_). Each string will be at most 80 characters long. The ki are all positive integers in the range 1-100.
Input
Input consists of information for one or more encrypted messages. Each problem begins with one line containing k1, k2, and k3 followed by a line containing the encrypted message. The end of the input is signalled by a line with all key values of 0.
Output
For each encrypted message, the output is a single line containing the decrypted string.
Sample Input
2 3 1
_icuo_bfnwhoq_kxert
1 1 1
bcalmkyzx
3 7 4
wcb_mxfep_dorul_eov_qtkrhe_ozany_dgtoh_u_eji
2 4 3
cjvdksaltbmu
0 0 0
Sample Output
the_quick_brown_fox
abcklmxyz
the_quick_brown_fox_jumped_over_the_lazy_dog
ajsbktcludmv
Source
#include<stdio.h>
#include<string.h>
char str[] = {};
char str1[] = {};
char str2[] = {};
char str3[] = {}; int main()
{
int a, b, c, len, alen, blen, clen;
while(scanf("%d%d%d", &a, &b, &c)) {
if(a == && b == && c == ) {
break;
}
scanf("%s", str);
len = strlen(str);
alen = blen = clen = ;
for(int i = ; i < len; i++) {
if(str[i] >= 'a' && str[i] <= 'i') {
str1[alen] = str[i];
alen++;
}
else if(str[i] >= 'j' && str[i] <= 'r') {
str2[blen] = str[i];
blen++;
}
else {
str3[clen] = str[i];
clen++;
}
}
// puts(str1);
// puts(str2);
// puts(str3); if(alen != ) a = a % alen;//这一步是关键
if(blen != ) b = b % blen;//这一步是关键
if(clen != ) c = c % clen;//这一步是关键
int t1 = , t2 = , t3 = ;
for(int i = ; i < len; i++) {
if(str[i] >= 'a' && str[i] <= 'i') {
printf("%c", str1[(t1-a+alen)%alen]);
t1++;
}
else if(str[i] >= 'j' && str[i] <= 'r') {
printf("%c", str2[(t2-b+blen)%blen]);
t2++;
}
else {
printf("%c", str3[(t3-c+clen)%clen]);
t3++;
}
}
printf("\n");
} return ;
}
POJ - 1107 W's Cipher的更多相关文章
- poj 2159 D - Ancient Cipher 文件加密
Ancient Cipher Description Ancient Roman empire had a strong government system with various departme ...
- ZOJ 1042 W’s Cipher
原题链接 题目大意:按照规则解码.26个字母分成三组,每一组按照顺时针移位编码.现在已知移动的位数,要求解码. 解法:以前看过一本古典密码学的书,百度贴吧密码吧也有很多经典的加密方法,想什么凯撒移位. ...
- POJ 1107
水题一道,注意取模时不能为0 #include <iostream> #include <algorithm> #include <cstring> #includ ...
- POJ题目细究
acm之pku题目分类 对ACM有兴趣的同学们可以看看 DP: 1011 NTA 简单题 1013 Great Equipment 简单题 102 ...
- 【转】POJ百道水题列表
以下是poj百道水题,新手可以考虑从这里刷起 搜索1002 Fire Net1004 Anagrams by Stack1005 Jugs1008 Gnome Tetravex1091 Knight ...
- HOJ题目分类
各种杂题,水题,模拟,包括简单数论. 1001 A+B 1002 A+B+C 1009 Fat Cat 1010 The Angle 1011 Unix ls 1012 Decoding Task 1 ...
- PHP的AES加密类
PHP的AES加密类 aes.php <?php /* - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - ...
- ethereumjs/ethereumjs-wallet
Utilities for handling Ethereum keys ethereumjs-wallet A lightweight wallet implementation. At the m ...
- SSIS 学习之旅 FTP文件传输-脚本任务
这一章主要讲解一下用脚本怎么把CSV文件抛送到FTP服务器上 设计: 通过Demon库的Users表数据生成CSV文件. 生成后的CSV文件抛送到FTP指定目录下. 控件的使用这里就不做详细讲 ...
随机推荐
- [CareerCup] 16.4 A Lock Without Deadlocks 无死锁的锁
16.4 Design a class which provides a lock only if there are no possible deadlocks. 有很多方法可以避免死锁的发生,一个 ...
- 我爱记单词(iWords)之NABC by张恿
1) N (Need 需求) 我们组的项目是做一个英语学习助手,前人的基础上开发新的功能,修改原来功能的bug等等.之前的版本只提供了主动“看单词”和单词测试的功能,我们希望增加背单词的功能,以便更好 ...
- js再学习笔记
#js再学习笔记 ##基本 1.js严格区分大小写 2.js末尾的分号可加,也可不加 3.六种数据类型(使用typeof来检验数据的类型) `typeof` - undefined: `var ...
- bzoj4514: [Sdoi2016]数字配对--费用流
看了一眼题目&数据范围,觉得应该是带下界的费用流 原来想拆点变成二分图,能配对的连边,跑二分图,可行性未知 后来看到另外一种解法.. 符合匹配要求的数要满足:质因子的个数相差为1,且两者可整除 ...
- Empire C:Basic 4
一.变量名 1.名字由字母和数字组成,但其第一个字符必须为字母. 2.变量名不要以下划线开头. 3.变量名使用小写字母,符号常量名全部使用大写字母. 二.数据类型及长度 1.char 字符型 占用一个 ...
- ExtJS笔记 Ext.Loader
Ext.Loader is the heart of the new dynamic dependency loading capability in Ext JS 4+. It is most co ...
- wpf 属性变更通知接口 INotifyPropertyChanged
在wpf中将控件绑定到对象的属性时, 当对象的属性发生改变时必须通知控件作出相应的改变, 所以此对象需要实现 INotifyPropertyChanged 接口 例: //实现属性变更通知接口 INo ...
- UML聚合与组合
http://www.cnblogs.com/shanwenbin/archive/2012/10/24/2737229.html UML聚合与组合 2012-10-24 15:35 by DayDa ...
- Vim ide for shell development
Source : This article is part of the ongoing Vi / Vim Tips and Tricks Series. As a Linux sysadmin or ...
- Golang之sdl2学习之路(零) -- 环境工具准备
学习Golang有一段时间了,从毫无头绪到四处乱撞,再到如今静下心来安心学习sdl2也有小半年了. 今晚重构之前的学习代码,发现如果不写该文,可能会在以后回顾这段时间写的代码上花费时间,故以此文做一点 ...
