HTTPS SSL & TLS
HTTPS (HTTP Secure) is an adaptation of the Hypertext Transfer Protocol (HTTP) for secure communication over a computer network, and is widely used on the Internet.
In HTTPS, the communication protocol is encrypted by Transport Layer Security (TLS), or formerly, its predecessor, Secure Sockets Layer (SSL). The protocol is therefore also often referred to as HTTP over TLS, or HTTP over SSL.
1. Latest Version
TLS1.2 : SSL 2.0 was prohibited in 2011 by RFC 6176, and SSL 3.0 was also later prohibited in June 2015 by RFC 7568.
2. Introduce Encryption Algorithm
2.1 Symmetric encryption algorithm
- DES(Data Encryption Standard)
- 3DES(Triple DES)
- AES(Advanced Encryption Standard)
2.2 Asymmetric encryption algorithm
- RSA(Rivest–Shamir–Adleman)
- DSA(Digital Signature Algorithm)
- ECC(Elliptic Curves Cryptography)
2.3 Hash algorithm
- MD5(Message Digest Algorithm 5)
- SHA(Secure Hash Algorithm)
3. Digital Certificate
The following diagram shows the process of obtaining a Digital Certificate from a CA.
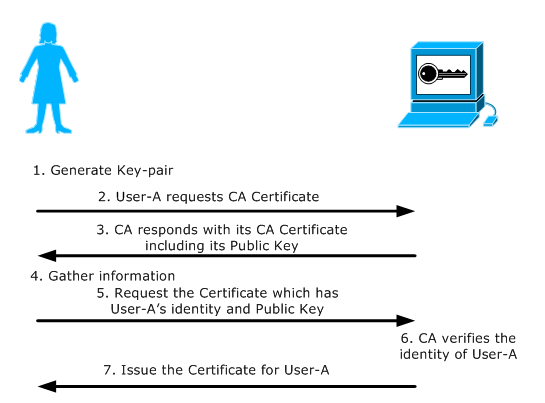
1. Generate Key-pair: User-A generates a Public and Private key-pair or is assigned a key-pair by some authority in their organization.
2. Request CA Certificate: User-A first requests the certificate of the CA Server.
3. CA Certificate Issued: The CA responds with its Certificate. This includes its Public Key and its Digital Signature signed using its Private Key.
4. Gather Information: User-A gathers all information required by the CA Server to obtain its certificate. This information could include User-A email address, fingerprints, etc. that the CA needs to be certain that User-A claims to be who she is.
5. Send Certificate Request: User-A sends a certificate request to the CA consisting of her Public Key and additional information. The certificate request is signed by CA's Public Key.
6. CA verifies User-A: The CA gets the certificate request, verifies User-A's identity and generates a certificate for User-A, binding her identity and her Public Key. The signature of CA verifies the authenticity of the Certificate.
7. CA issues the Certificate: The CA issues the certificate to User-A.
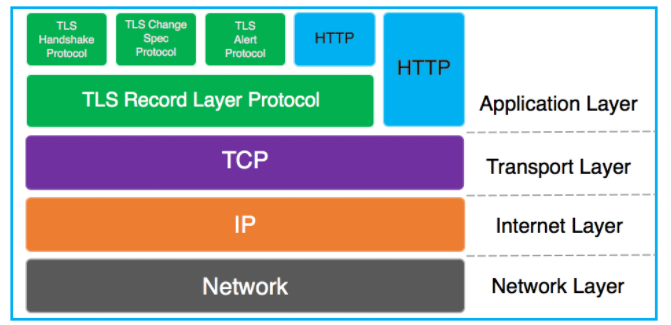
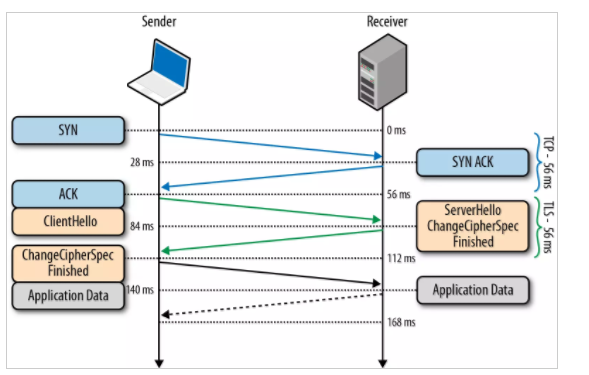
4. TLS Handshake
As we know TLS/SSL is an application layer protocol. Below is a diagram depicting the TCP/IP model:
Below is a diagrammatic representation of the SSL Handshake:
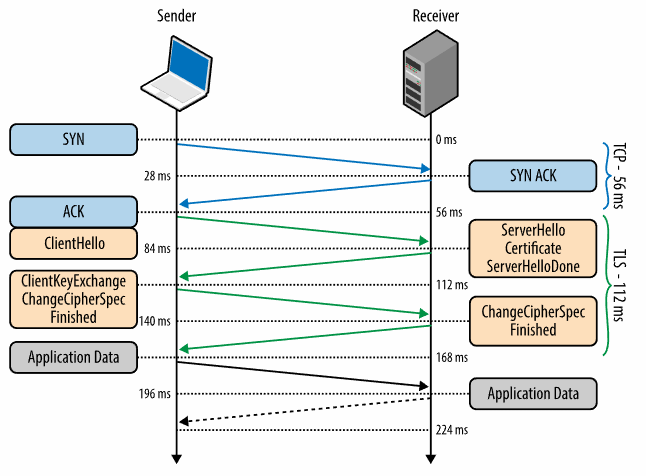
0 ms
TLS runs over a reliable transport (TCP), which means that we must first complete the TCP three-way handshake, which takes one full roundtrip.
56 ms
With the TCP connection in place, the client sends a number of specifications in plain text, such as the version of the TLS protocol it is running, the list of supported ciphersuites, and other TLS options it may want to use.
84 ms
The server picks the TLS protocol version for further communication, decides on a ciphersuite from the list provided by the client, attaches its certificate, and sends the response back to the client. Optionally, the server can also send a request for the client’s certificate and parameters for other TLS extensions.
112 ms
Assuming both sides are able to negotiate a common version and cipher, and the client is happy with the certificate provided by the server, the client initiates either the RSA or the Diffie-Hellman key exchange, which is used to establish the symmetric key for the ensuing session.
140 ms
The server processes the key exchange parameters sent by the client, checks message integrity by verifying the MAC, and returns an encrypted Finished message back to the client.
168 ms
The client decrypts the message with the negotiated symmetric key, verifies the MAC, and if all is well, then the tunnel is established and application data can now be sent.
5. Certificate-Chain
When you receive the certificate for another entity, you might need to use a certificate chain to obtain the root CA certificate.
The certificate chain, also known as the certification path, is a list of certificates used to authenticate an entity. The chain, or path, begins with the certificate of that entity, and each certificate in the chain is signed by the entity identified by the next certificate in the chain. The chain terminates with a root CA certificate. The root CA certificate is always signed by the certificate authority (CA) itself. The signatures of all certificates in the chain must be verified until the root CA certificate is reached.
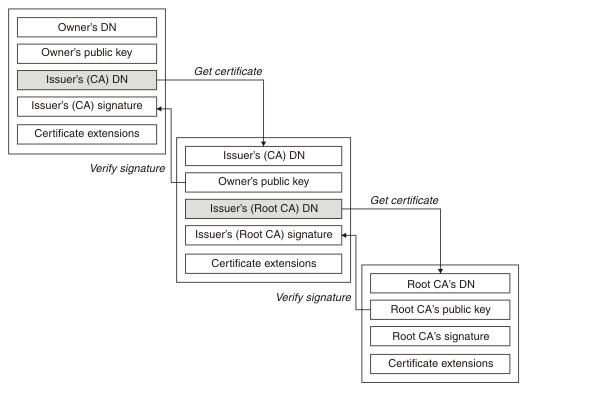
Each certificate can contain one or more extensions. A certificate belonging to a CA typically contains a BasicConstraints extension with the isCA flag set to indicate that it is allowed to sign other certificates.
6. When will TSL handshake happen
A connection starts with a handshake, and ends when either party states it by sending a close_notify alert message. Typical Web browsers and servers will maintain connections open for some time, closing them after one or two minutes of inactivity; one or several HTTP requests and responses are sent over that connection. In normal HTTPS contexts, there is a one-to-one mapping between the SSL connections and the underlying TCP connections: for each TCP connection (to port 443), there will be a single SSL connection, and when the SSL connection ends, the underlying TCP connection is closed.
A session relates to the asymmetric cryptography which occurs in a "full handshake". The handshake process, which occurs at the beginning of a connection, is about establishing the cryptographic algorithms and keys which will be used to protect the data for that connection. There are two sorts of handshakes:
The full handshake is what a client and server do when they don't know each other (they have not talked previously, or that was long ago). In the full handshake, certificates are sent, and asymmetric cryptography (RSA, Diffie-Hellman...) occurs.
The abbreviated handshake is what a client and server remember each other; more accurately, they remember the algorithms and keys that they established in a previous full handshake, and agree to reuse them (technically, they reuse the "master secret" and derive from it fresh encryption keys for this connection).
A connection with a full handshake, and the set of connections with abbreviated handshake who reuse that full handshake, constitute together the session.
7. TLS handshake Performance Optimise
7.1 Session Resumption
Resuming an encrypted session through a session ID means that the server keeps track of recent negotiated sessions using unique session IDs. This is done so that when a client reconnects to a server with a session ID, the server can quickly look up the session keys and resume the encrypted communication.
7.2 OCSP Stapling
OCSP stapling resolves both problems in a fashion reminiscent of the Kerberos ticket. In a stapling scenario, the certificate holder queries the OCSP server themselves at regular intervals, obtaining a signed time-stamped OCSP response. When the site's visitors attempt to connect to the site, this response is included ("stapled") with the TLS/SSL handshake via the Certificate Status Request extension response (note: the TLS client must explicitly include a Certificate Status Request extension in its ClientHello TLS/SSL handshake message). While it may appear that allowing the site operator to control verification responses would allow a fraudulent site to issue false verification for a revoked certificate, the stapled responses can't be forged as they need to be directly signed by the certificate authority, not the server. If the client does not receive a stapled response, it will just contact the OCSP server by itself. However, if the client receives an invalid stapled response, it will abort the connection. The only increased risk of OCSP stapling is that the notification of revocation for a certificate may be delayed until the last-signed OCSP response expires.
As a result, clients continue to have verifiable assurance from the certificate authority that the certificate is presently valid (or was quite recently), but no longer need to individually contact the OCSP server. This means that the brunt of the resource burden is now placed back on the certificate holder. It also means that the client software no longer needs to disclose users' browsing habits to any third party.
Overall performance is also improved: When the client fetches the OCSP response directly from the CA, it usually involves the lookup of the domain name of the CA's OCSP server in the DNS as well as establishing a connection to the OCSP server. When OCSP stapling is used, the certificate status information is delivered to the client through an already established channel, reducing overhead and improving performance.
Refers:
https://en.wikipedia.org/wiki/Certificate_signing_request
https://blogs.msdn.microsoft.com/kaushal/2013/08/02/ssl-handshake-and-https-bindings-on-iis/
https://sites.google.com/site/amitsciscozone/home/security/digital-certificates-explained
https://tools.ietf.org/html/rfc5246
https://hpbn.co/transport-layer-security-tls/
https://en.wikipedia.org/wiki/Transport_Layer_Security#TLS_handshake
HTTPS SSL & TLS的更多相关文章
- 在 ASP.NET MVC 中使用 HTTPS (SSL/TLS) -- 学习
在 ASP.NET MVC 中使用 HTTPS (SSL/TLS) IS 7如何实现http重定向https HTTPS 升级指南
- 简而意赅 HTTP HTTPS SSL TLS 之间有什么不同
HTTP HTTPS SSL TLS 之间有什么不同? SSL是Secure Sockets Layer的缩写.SSL的作用是为网络上的两台机器或设备提供了一个安全的通道. TLS是SSL的一个新的名 ...
- HTTPS SSL TLS 相关理解
1,在理解 HTTPS SSL TLS 之前先对常用的加密方式进行一个简述: (1),对称加密: 采用一个密钥,对明文进行加密生成密文,相反采用此密钥可对加密后的密文进行解密还原成明文. 代表算法有, ...
- HTTPS(SSL/TLS) 原理之深入浅出
注:本文参考自网络上的多篇HTTPS相关文章,本人根据自己的理解,进行一些修改,综合. 1. 必要的加密解密基础知识 1)对称加密算法:就是加密和解密使用同一个密钥的加密算法.因为加密方和解密方使用的 ...
- 在 ASP.NET MVC 中使用 HTTPS (SSL/TLS)
某些安全性较高的网页,如网上支付或用户登陆页面,可能会使用到https(SSL/TLS)来提高安全性.本文介绍了如何在ASP.NET MVC中强制某action使用https和如何进行向https页面 ...
- HTTPS SSL/TLS协议
要说清楚 HTTPS 协议的实现原理,至少需要如下几个背景知识.1. 大致了解几个基本术语(HTTPS.SSL.TLS)的含义2. 大致了解 HTTP 和 TCP 的关系(尤其是“短连接”VS“长连接 ...
- [skill][https][ssl/tls] HTTPS相关知识汇总
结论前置: A 身份验证 证书, 服务器证书 B 密钥协商 RSA DHE / ECDHE PSK C 加密通信 加密通信采用对称加密,使用B阶段协商出来的密钥. B 阶段如果使用 RSA 协 ...
- https ssl(tls)为什么不直接用公钥加密数据?
很多人都提到了非对称加密速度慢,但这只是一个原因,但不是主要原因,甚至是微不足道的原因. SSL协议到3.0后就已经到头了,取而代之的是TLS,相较于SSL的"安全套接字层"的命名 ...
- win10系统iis下部署搭建https (ssl/tls)本地测试环境
有时想要把公司的某些XX项目部署成https站点,是为了在传输层加密传输,防止他人嗅探站点重要数据信息,平常我们使用的http方式都是明文方式传输的很不安全,容易被他人窃取.而有些时候要在本地搭建ht ...
随机推荐
- Java学习笔记(2)
int 和 booleam 不能直接转换,如下语法是不能通过的: boolean b = true; int i = (int) b; int j = 1; boolean a = (boolean) ...
- jcifs windows 域账户单点登录(转)
1.首先从http://jcifs.samba.org 这个站点下载 jcifs-1.3.2.jar包. 2.把这个包放到相应的lib文件下面. 3.对web.xml文件进行配置,添加如下内容 < ...
- vue 线上不支持put方法
在app.js中加上 // Vue.http.options.emulateHTTP = true Vue.http.options.timeout = 15000
- nginx和resin一二三
最近听我们这边的开发讲解了一小下nginx和resin,现在Mark一下,可能不专业,但是对于我来说通俗易懂就好哈哈哈. 首先说服务器,服务器这个东西吧它是干啥的呢,你写的页面只能在你自己的电脑上打开 ...
- 利用python执行shell脚本 并动态传参 及subprocess基本使用
最近工作需求中 有遇到这个情况 在web端获取配置文件内容 及 往shell 脚本中动态传入参数 执行shell脚本这个有多种方法 最后还是选择了subprocess这个python标准库 su ...
- imeiimsi生成规则
添加SMI 和 IMSI修改 添加模拟器名修改(MEmu_ 修改成其他的名字,不支持批量修改) IMSI第十位:7代表是145卡,6代表186卡,3代表156,0代表130,其他的可以自己找 预 ...
- centos7 - mongodb3.6.5-配置文件
创建Linux管理员账号admin, 并加入wheel组,对mongodb, php等进行统一管理~ systemLog:destination: filelogAppend: truepath: / ...
- 文档资源搜索小工具 - 支持PDF,DOC,PPT,XLS
最近做了一个文档搜索小工具,当然不是网盘搜索工具,这个工具支持四种文件格式搜索(pdf,doc,ppt,xls),你只需要在搜索框中输入你想要搜索资源的关键词,点击搜索按钮即可获取相关资源,点击下载按 ...
- Web 建站技术中,HTML、HTML5、XHTML、CSS、SQL、JavaScript、PHP、ASP.NET、Web Services 是什么(转)
Web 建站技术中,HTML.HTML5.XHTML.CSS.SQL.JavaScript.PHP.ASP.NET.Web Services 是什么?修改 建站有很多技术,如 HTML.HTML5.X ...
- linux配置服务器
梳理一下这次配置服务器的思路. 1,挂载磁盘 Java和neigx上传到根目录下,tomcat放在data目录下,数据库新建文件夹也在data下, 2,配置环境变量 3,nginx修改域名 4,数据库 ...
