Zombie Scanning
1、theree -way handshake
A TCP SYN packet is sent from the device that wishes to establish a connection with a port of the device the it derires to connect with ,if the service assoicated with the receiving port accepts the connection , it will replay to the requesting system with a TCP packet that has both the SYN and ACKbits activated ,the connection is established only when the requesting system responds with the a TCP ACK response ,this therr-step process establish a TCP session between the two system. all of the TCP port scanning techniques will perform some varatio of this process to identify live service on the remote hosts.
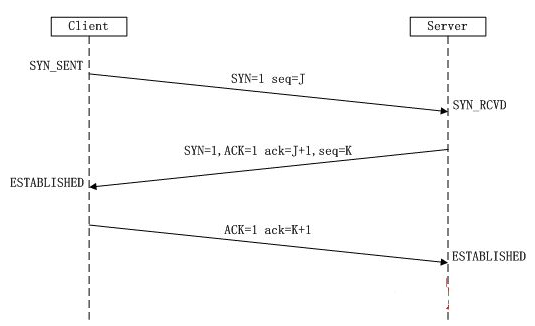
we know the Connect scanning is used to establish a full TCP connection for each port that is scanned ,Alternatively ,Stealth scanning doesn't esatblish a full connection ,it only refered to as SYN scanning or half-open scanning , for each port that is scanned , a single SYN packet is sent to the destination port ,and all ports that replay with a SYN +ACK packet are assumed to be running live service ,since no final ACK is sent from the initiating system ,the connection is left half-open ,this is referred to as stealth scanning because logging solutions that only recode established connection will not record any evidence of the scan .
2、 Zombie scanning
when we know the scanning principle , let's discussed the final method of TCP scanning , the zombie scanning is to map ope ports on the remote the system without producing any evidence that you have interavted with the system ,
then how to do carry out the process of zombie scanning : as follow
step one : identify a remote system for you zombie ,this system should have the following characteristics
- the system is idle and dose not communicate actively withe other systems on the network
- the system uses an incremental IPID sequence
step two : Send a SYN+ACK packet to this zombie host and record the initial IPID values
step three: send a SYN packet with a spoofed source ip address of the zombie system to the scan target system
setp four : depending the status of the port the scan target ,one of the following two things will happen:
- if the port is open ,the scan target will return a SYN +ACK packet to the zombie host ,which it believe sent the original SYN request , in the case the zombie host will resopnd to this unsolicited SYN+ACK packet with an RST packet and thereby incerment its IPID value by ONE
- if the port is closed , the scan target will return an RST response to the zombie host ,which it believe sent the original SYN request , this RST packet will solicit no resopnse form the zombie ,and the IPID will not be incremented
step five : send another SYN+ACK packet to the zombie host ,and evaluate the final IPID value of the return RST resopnse , if this value has incermente by ONE ,then the port on the scan target is closed ,and if the value the incermented by TWO , then the port on the scan target is open .
.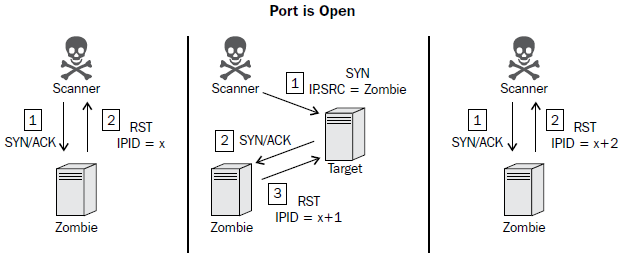
To perform a zombie scan, an initial SYN+ACK request should be sent to the zombie system to determine the current IPID value in the returned RST packet. Then, a spoofed SYN packet is sent to the scan target with a source IP address of the zombie system. If the port is open, the scan target will send a SYN+ACK response back to the zombie. Since the zombie did not actually send the initial SYN request, it will interpret the SYN+ACK response as unsolicited and send an RST packet back to the target, thereby incrementing its IPID by one. Finally, another SYN+ACK packet should be sent to the zombie, which will return an RST packet and increment the IPID one more
time. An IPID that has incremented by two from the initial response is indicative of the fact that all of these events have transpired and that the destination port on the scanned system is open. Alternatively, if the port on the scan target is closed, a different series of events will transpire, which will only cause the final RST response IPID value to increment by one.

If the destination port on the scan target is closed, an RST packet will be sent to the zombie system in response to the initially spoofed SYN packet. Since the RST packet solicits no response, the IPID value of the zombie system will not be incremented. As a result, the final RST packet returned to the scanning system in response to the SYN+ACK packet will have the IPID incremented by only one. This process can be performed for each port that is to be scanned, and it can be used to map open ports on a remote system without leaving any evidence that a scan was performed by the scanning system.
Zombie Scanning的更多相关文章
- kali linux networking scanning Cookbok (第三章结尾笔记)
1.Zombie Scanning with Nmap Zombie scans can also be performed with an option in Namp , we can find ...
- Connet Scanning
1.connect scanning with Scapy, Tools that perform Tcp scans operate by performing a full there-wa ...
- XCode一直显示"scanning for working copies"的解决办法
一个SVN上的项目,在本地重新CheckOut打开后,一直提示"scanning for working copies"且不能使用SVN的更新.提交等功能,当时想着晾它一晚上,看能 ...
- 避免产生僵尸进程的N种方法(zombie process)
http://blog.csdn.net/duyiwuer2009/article/details/7964795 认识僵尸进程 1.如果父进程先退出 子进程自动被 init 进程收养,不会产生僵尸进 ...
- 专注docker安全:Security Scanning
导读 Docker毫无疑问是近期运维同学们的热点话题,Docker安全也由此倍受重视,Docker Security Scanning 是一款Docker镜像扫描的安全工具,目前已经在Docker C ...
- OC内存管理--zombie对象
当我们对于内存进行手动管理的时候,会出现两种错误:一种是野指针错误,一种则为内存泄露.这两点也是我们去管理内存时最终要解决的问题. 内存泄漏是指:不在使用的对象,一直保留在内存中未被销毁,一直占有着内 ...
- Spring Filter components in auto scanning
In this Spring auto component scanning tutorial, you learn about how to make Spring auto scan your c ...
- Spring Auto scanning components
Normally you declare all the beans or components in XML bean configuration file, so that Spring cont ...
- h.264 scanning process for transform coefficients
宏块在经过变换.量化后,得到大小为4x4或者8x8的矩阵,矩阵中的数据被称为transform coefficient levels.这些level在后面会被用于熵编码,因此我们需要把矩阵按照一定顺序 ...
随机推荐
- Timer类的常见使用方法
System.Timers名称空间中的Timer类的构造函数只需要一个时间间隔,经过该时间间隔后应该调用的方法用Elapsed事件指定,这个事件需要一个ElapsedEventHandler类型的委托 ...
- 其它综合-运维老鸟分享linux运维发展路线规划
运维老鸟分享linux运维发展路线规划 linux 运维发展路线常见的就是下面两条路线: 第一条:运维应用-->系统架构-->运维开发-->系统开发 第二条:运维应用-->应用 ...
- qrcode & vue
qrcode & vue $ yarn add qrcode.vue # OR $ npm i -S qrcode.vue https://www.npmjs.com/package/qrco ...
- A Java Runtime Environment (JRE) or Java Development Kit (JDK) must be available in order to run Eclipse.
cp -r /home/cuthead/android-studio/jre /home/cuthead/adt-bundle-linux-x86_64-20131030/eclipse/jre 使用 ...
- Building Forms with PowerShell – Part 1 (The Form)
For those of you familiar with Scripting languages you are probably used to using alternate applicat ...
- Javascript初识之数据类型
一.JavaScript概述 1.ECMAScript和JavaScript的关系 1996年11月,JavaScript的创造者--Netscape公司,决定将JavaScript提交给国际标准化组 ...
- 【dp】求最长上升子序列
题目描述 给定一个序列,初始为空.现在我们将1到N的数字插入到序列中,每次将一个数字插入到一个特定的位置.我们想知道此时最长上升子序列长度是多少? 输入 第一行一个整数N,表示我们要将1到N插入序列中 ...
- C/C++ const
一 含义 const修饰的变量在C和C++中的含义是什么?一样吗? 在C中用const修饰的变量仅仅表示这个符合表示的变量不能被赋值,是只读的,那么它与常量有啥区别呢?区别就是一个是常量,一个是变量. ...
- nginx 返回数据被截断
nignx 代理 buffer proxy_buffers 16 512k; proxy_buffer_size 512k; fastcgi buffer fastcgi_buffers 4 64 ...
- 用expect实现SCP/SSH自动输入密码登录
在命令行ssh远程登录服务器和scp远程传输文件都需要交互式输入密码,无法像mysql登录数据库 mysql -uroot -p123456一样直接完成. 其实可以用脚本依赖expect来达到这一目的 ...
