2023 SHCTF-校外赛道 Crypto—Wp
WEEK1
立正
wl hgrfhg 4gNUx4NgQgEUb4NC64NHxZLg636V6CDBiDNUHw8HkapH :jdoi vl vlkw ~xrb wd nrrT Y:凯撒解密,偏移量为3得到:
ti edoced 4dKRu4KdNdBRy4KZ64KEuWId636S6ZAYfAKREt8EhxmE :galf si siht ~uoy ta kooQ V:发现edoced并结合题目提示:注意要 正,意识到要把它逆序:V Qook at you~ this is flag: EmxhE8tERKAfYAZ6S636dIWuEK46ZK4yRBdNdK4uRKd4 decode it
这个题还是有点脑洞的,观察中间的密文EmxhE8tERKAfYAZ6S636dIWuEK46ZK4yRBdNdK4uRKd4,对比一下flag{的base64密文:ZmxhZ3s
可知道,大写字母后移21位因为E–>Z,而小写字母不动,数字前移5位,因为Qook at you–>Look at you
exp:
import base64
c = "EmxhE8tERKAfYAZ6S636dIWuEK46ZK4yRBdNdK4uRKd4"
m = ""
for i in range(len(c)):
if c[i].isupper():
mm = 65 + (ord(c[i]) - 65 + 21) % 26
m += chr(mm)
if c[i].isdigit():
mm = ord('0') + ((ord(c[i]) - ord('0') -5) % 10)
m += chr(mm)
if c[i].islower():
m += c[i]
flag = base64.b64decode(m.encode())
print(flag)
#flag{Y0U_MU57_5t4nd_uP_r1gHt_n0W}Crypto_Checkin
QZZ|KQbjRRS8QZRQdCYwR4_DoQ7~jyO>0t4R4__aQZQ9|Rz+k_Q!r#mR90+NR4_4NR%>ipO>0s{R90|SQhHKhRz+k^S8Q5JS5|OUQZO}CQfp*dS8P&9R8>k?QZYthRz+k_O>0#>Cyber一把梭: base85 –> base64 –> base32 –> base16
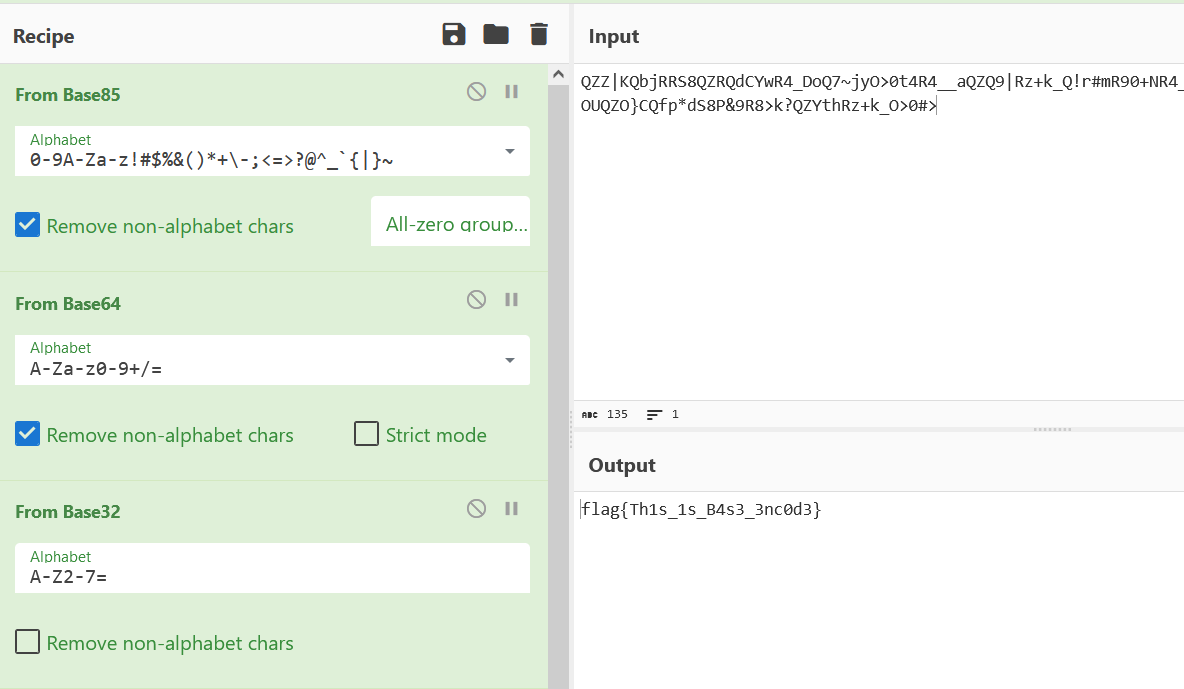
残缺的md5
苑晴在路边捡到了一张纸条,上面有一串字符串:KCLWG?K8M9O3?DE?84S9
问号是被污染的部分,纸条的背面写着被污染的地方为大写字母,还给了这串字符串的md5码值:F0AF????B1F463????F7AE???B2AC4E6
请提交完整的md5码值并用flag{}包裹提交爆破
exp:
import string
import hashlib
s = "KCLWG?K8M9O3?DE?84S9"
table = string.ascii_letters + string.digits
for i in range(128):
for j in range(128):
for k in range(128):
ss = "KCLWG" + chr(i) + "K8M9O3" + chr(j) + "DE" + chr(k) + "84S9"
hash = hashlib.md5(ss.encode()).hexdigest().upper()
if hash[:4] == "F0AF" and hash[-7:] == "B2AC4E6" and "B1F463" in hash:
flag = "flag{" + hash + "}"
flag1 = "flag{" + ss + "}"
print(flag)
print(flag1)
#flag{F0AF1443B1F463EAFFF7AEBB8B2AC4E6}
#flag{KCLWGXK8M9O3KDED84S9}凯撒大帝
pvkq{mredsrkyxkx}凯撒解码
key1 #10: flag{chutihaonan}进制
好熟悉的进制,但不知道加密了几层
3636366336313637376236313638363636623661366336383662363136383764
okk
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook! Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook. Ook? Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook! Ook! Ook! Ook!
Ook! Ook! Ook? Ook. Ook? Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook. Ook? Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook!
Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook! Ook! Ook! Ook? Ook. Ook? Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook. Ook. Ook. Ook! Ook. Ook. Ook. Ook! Ook. Ook. Ook. Ook! Ook. Ook. Ook.
Ook! Ook. Ook. Ook. Ook! Ook. Ook. Ook. Ook! Ook. Ook. Ook. Ook! Ook. Ook.
Ook. Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook.
Ook? Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook. Ook?
Ook. BrainFuck解码: ★ flag{123456789}熊斐特
熊斐特博士发现了一种新的密码。
uozt{zgyzhs xrksvi}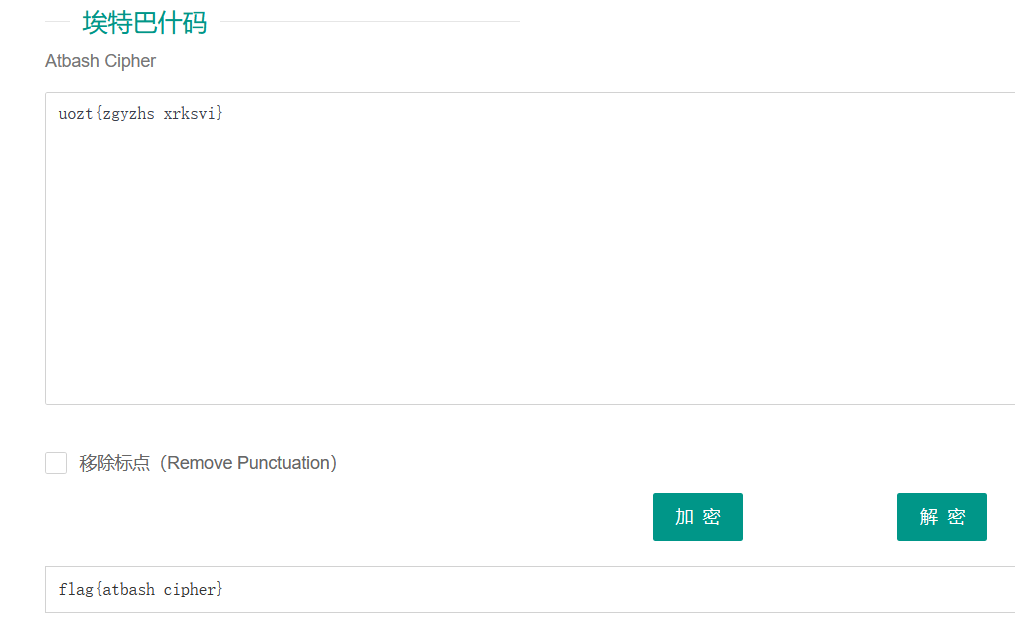
黑暗之歌
密文:
⠴⡰⡭⡳⠴⡰⡭⡰⡷⡲⡢⡩⡭⡡⠯⡩⡭⡡⡺⡩⡭⡡⠳⡩⡭⡡⡺⡩⡭⡡⡶⡩⡭⡡⡶⡩⡭⡡⡲⡩⡭⡡⡺⡩⡭⡡⠯⡩⡧⡊⡢⡩⡭⡡⠯⡩⡭⡡⡺⡃⡰⠫⡋⡚⡲⡍⡋⡮⠴⡰⡭⡶⡷⡲⡢⡩⡧⡊⡢⡃⡴⡵⡋⡁⡬⡵⡋⡁⡬⡵⡋⡁⡬⡳⡋⠲⠴⡯⡃⡗⠴⡰⡭⡴⠴⡰⡭⡶⡷⡲⡢⡩⡧⡊⡢⡩⡭⡡⡺⡩⡭⡡⡺⡩⡭⡡⠳⡩⡧⡊⡢⡩⡭⡡⠯⡩⡧⡊⡢⡃⡴⡵⡋⡚⡱⠫⡋⡚⡱⠫⡋⡚⡲⠵⠲⡺⠰⠽一眼丁真,盲文解码
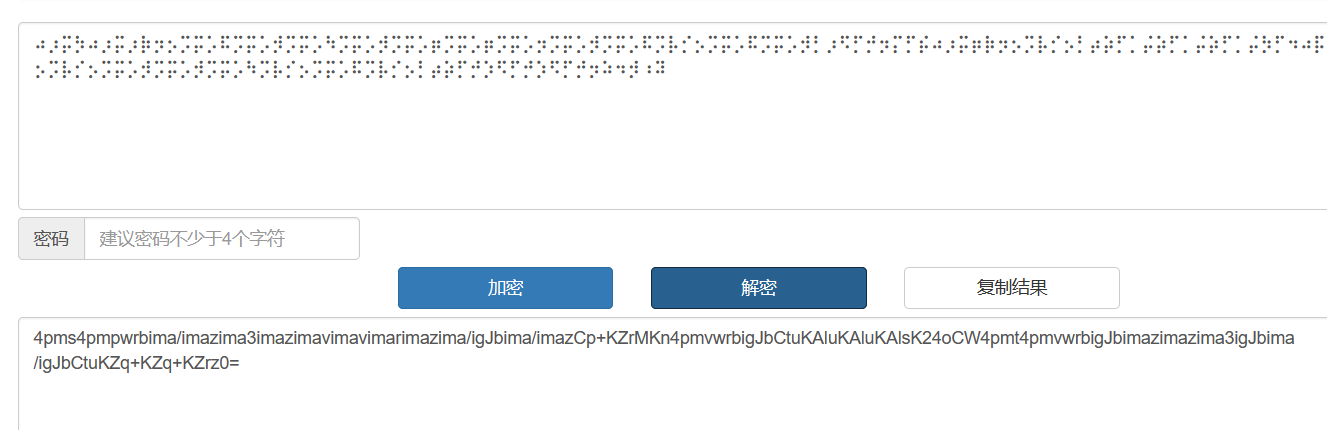
4pms4pmpwrbima/imazima3imazimavimavimarimazima/igJbima/imazCp+KZrMKn4pmvwrbigJbCtuKAluKAluKAlsK24oCW4pmt4pmvwrbigJbimazimazima3igJbima/igJbCtuKZq+KZq+KZrz0=base64解码
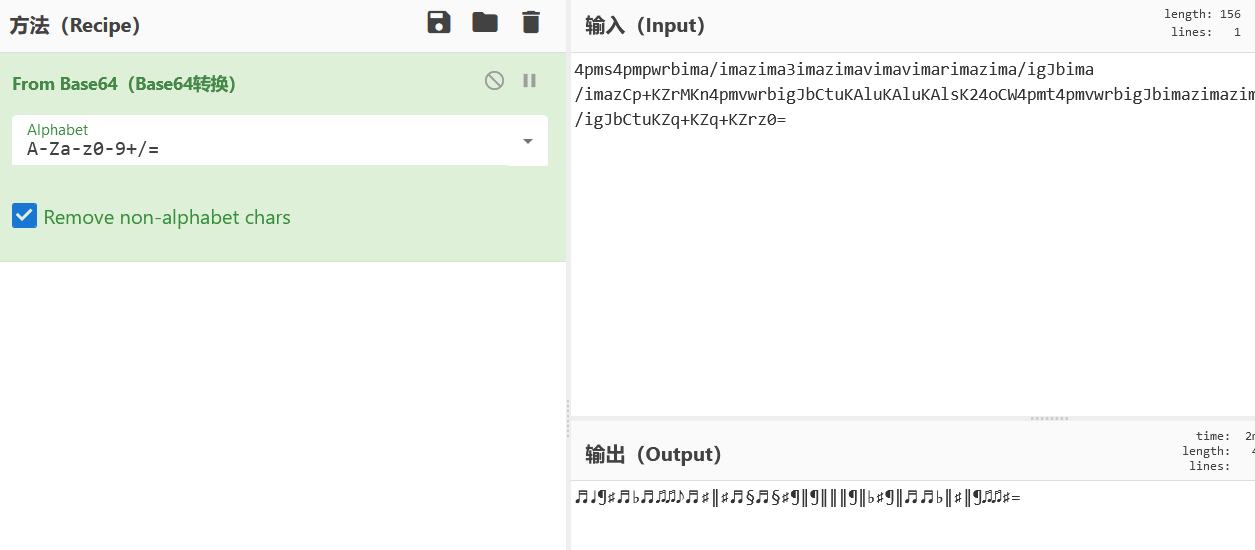
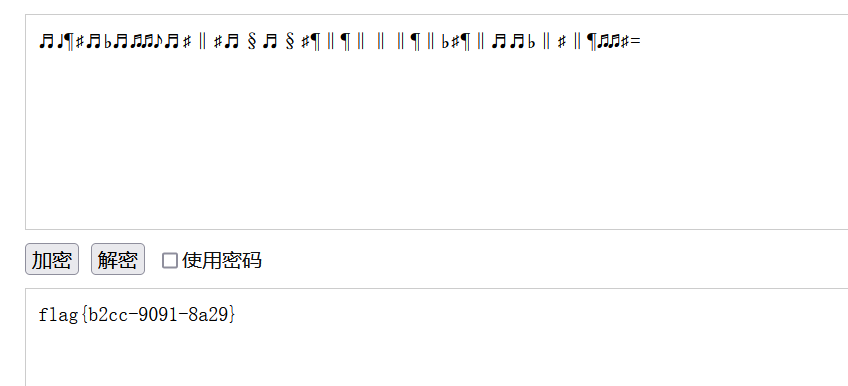
♬♩¶♯♬♭♬♫♫♪♬♯‖♯♬§♬§♯¶‖¶‖‖‖¶‖♭♯¶‖♬♬♭‖♯‖¶♫♫♯=音符解码
迷雾重重
题目描述:
morse?ASCII?
密文:
0010 0100 01 110 1111011 11 111 010 000 0 001101 00 000 001101 0001 0 010 1011 001101 0010 001 10 1111101摩斯解码
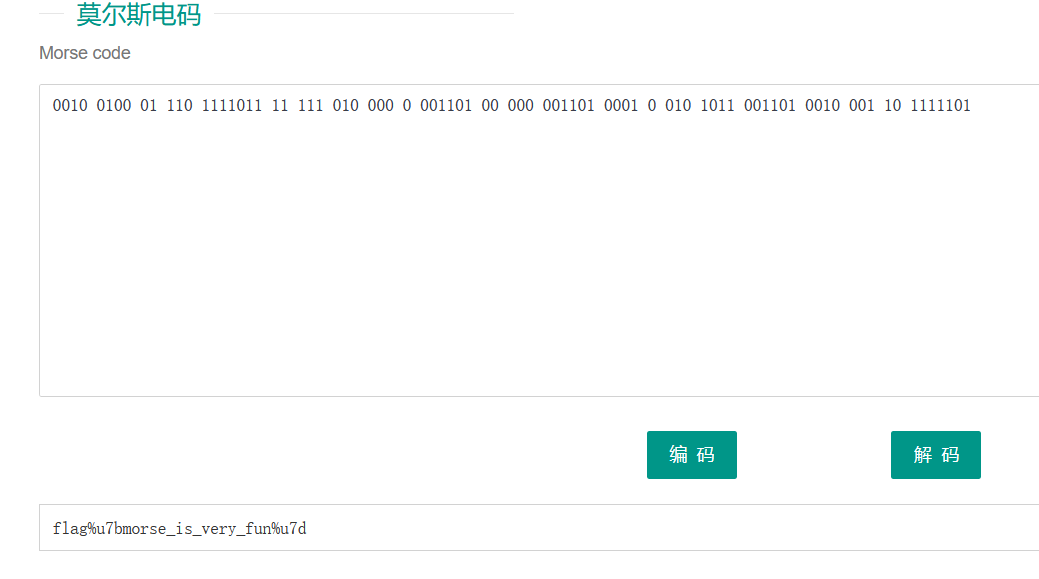
flag{morse_is_very_fun}难言的遗憾
题目描述:
我们本可以早些进入信息化时代的,但是清政府拒不采纳那份编码规则。 (注:flag为中文,使用flag{}包裹提交)
密文:
000111310008133175592422205314327609650071810649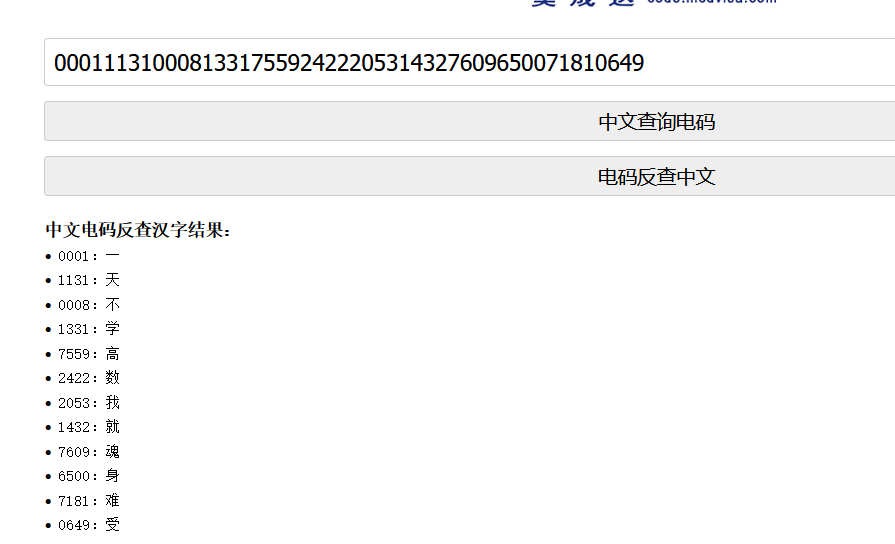
小兔子可爱捏
题目描述:宇宙的终极答案是什么?
U2FsdGVkX1/lKCKZm7Nw9xHLMrKHsbGQuFJU5QeUdASq3Ulcrcv9
你可能会需要一把钥匙,钥匙就是问题的答案。宇宙的终极答案是42,作为密钥,Rabbit解码
flag{i_love_technology}电信诈骗
050f000a7e407151537802540b747176075178027552756d0256726262627c
你好,我是秦始皇,我并没有死,我得到了长生不老药,但是药效有副作用,现在才醒。我刚花了一年在互联网上了解现在的时代,现在我要利用我地宫第四行第七列的无敌兵马俑军队卷土重来,但是我需要启动资金,vivo50作为启动资金,待我横扫天下,封你为大将军,赏你黄金万两!先16进制转字节
c = "050f000a7e407151537802540b747176075178027552756d0256726262627c"
cc = []
for i in bytes.fromhex(c):
cc.append(i)
print(cc)得到这个数组[5, 15, 0, 10, 126, 64, 113, 81, 83, 120, 2, 84, 11, 116,
113, 118, 7, 81, 120, 2, 117, 82, 117, 109, 2, 86, 114, 98, 98, 98, 124]
提示给出47和50两个数字,拿部分明文flag{进行各种运算,最后发现每个明文字符和密文字符异或50的差值都是47,即47 = m[i] - (cc[i] ^ 50)
m = b"flag{"
for i in range(5):
print(m[i] - (cc[i] ^ 50))所以通过m[i] = cc[i] ^ 50,就能恢复明文
但是!这样操作的话,得到的是:flag{¡ry_hursdy_vv_o},很明显有一些字符没有打出来
有一些明文的值是超出范围的,因为我们需要的值是在33~126中
所以要对超出126的值进行处理,把每个m的值打印出来
找一下规律发现,vv此处应该是vivo或者v1v0或者viv0或者v1vo,通过这样来找寻规律,最后通过v1v0找到了规律,要把超过126的值减去94
exp:
c = "050f000a7e407151537802540b747176075178027552756d0256726262627c"
cc = []
for i in bytes.fromhex(c):
cc.append(i)
print(cc)
flag = ''
for i in range(len(cc)):
mm = 47 + (cc[i] ^ 50)
if mm > 126:
mm -= 94
flag += chr(mm)
else:
flag += chr(mm)
print(flag)
#flag{Cr42y_7hursd4y_v1v0_5o!!!}what is m
from Crypto.Util.number import bytes_to_long
from secret import flag
m = bytes_to_long(flag)
print("m =",m)
# m = 7130439814059477365344643052269091933115903919817062018703864255164601096190338334430644132726759917910603893760972905213460376105525821771466384179562302119417654102079238248438835476382333白给了
from Crypto.Util.number import *
m = 7130439814057451234816276827985624426378225444820448794672983850703174510423869748080084641434692304059989810437801952820137016591528446065914779069356815372089481476999952029232464963781245
print(long_to_bytes(m))
#flag{Th3r3_ar3_53vEraL_a1terNAtIvEs_7o_tHe_1ON9_T0_6YteS_1UNCti0N_dCGb796e3dSB}really_ez_rsa
from Crypto.Util.number import getPrime, bytes_to_long
e = 65537
m = b''
p = getPrime(128)
q = getPrime(128)
n = p * q
m = bytes_to_long(m)
c = pow(m, e, n)
print("p =", p)
print("q =", q)
print("c =", c)
print("e =", e)
# p = 217873395548207236847876059475581824463
# q = 185617189161086060278518214521453878483
# c = 6170206647205994850964798055359827998224330552323068751708721001188295410644
# e = 65537p,q都给了,又白给了
exp:
from Crypto.Util.number import *
import gmpy2
p = 217873395548207236847876059475581824463
q = 185617189161086060278518214521453878483
c = 6170206647205994850964798055359827998224330552323068751708721001188295410644
e = 65537
d = gmpy2.invert(e,(p-1)*(q-1))
m = pow(c,d,p*q)
print(long_to_bytes(m))
#flag{Y0ung_meiyou_xiaojj}WEEK2
XOR
n = 20810298530643139779725379335557687960281905096107101411585220918672653323875234344540342801651123667553812866458790076971583539529404583369246005781146655852295475940942005806084842620601383912513102861245275690036363402134681262533947475193408594967684453091957401932685922178406769578067946779033282889429596341714417295489842047781388337010440309434639274398589029236213499110100040841426995862849012466514170374143655264739023758914247116354182164550612494432327931655944868705959874670536031052370968354394583880324756639698871918124498442308334232127034553164826483441746719644515097123067550594588348951855987
c = 15294238831055894095745317706739204020319929545635634316996804750424242996533741450795483290384329104330090410419090776738963732127756947425265305276394058773237118310164375814515488333015347737716139073947021972607133348357843542310589577847859875065651579863803460777883480006078771792286205582765870786584904810922437581419555823588531402681156158991972023042592179567351862630979979989132957073962160946903567157184627177910380657091234027709595863061642453096671316307805667922247180282486325569430449985678954185611299166777141304330040782500340791721548519463552822293017606441987565074653579432972931432057376
e = 65537
p⊕q = 66138689143868607947630785415331461127626263390302506173955100963855136134289233949354345883327245336547595357625259526618623795152771487180400409991587378085305813144661971099363267511657121911410275002816755637490837422852032755234403225128695875574749525003296342076268760708900752562579555935703659615570剪枝,通过p^q的值和n求得p,q
exp:
import sys
import gmpy2
sys.setrecursionlimit(3000)
gift = 66138689143868607947630785415331461127626263390302506173955100963855136134289233949354345883327245336547595357625259526618623795152771487180400409991587378085305813144661971099363267511657121911410275002816755637490837422852032755234403225128695875574749525003296342076268760708900752562579555935703659615570
N = 20810298530643139779725379335557687960281905096107101411585220918672653323875234344540342801651123667553812866458790076971583539529404583369246005781146655852295475940942005806084842620601383912513102861245275690036363402134681262533947475193408594967684453091957401932685922178406769578067946779033282889429596341714417295489842047781388337010440309434639274398589029236213499110100040841426995862849012466514170374143655264739023758914247116354182164550612494432327931655944868705959874670536031052370968354394583880324756639698871918124498442308334232127034553164826483441746719644515097123067550594588348951855987
def findp(p,q):
if len(p) == 1024:
pp = int(p,2)
if N % pp == 0:
print("p = ",pp)
print("q = ",N // pp)
else:
l = len(p)
pp = int(p,2)
qq = int(q,2)
if (pp ^ qq) % (2 ** l) == gift %(2**l) and pp * qq %(2 ** l) == N % (2**l):
findp('1' + p,'1' + q)
findp('1' + p,'0' + q)
findp('0' + p,'1' + q)
findp('0' + p,'0' + q)
findp('1','1')
p = 121707024037268877853347577606022680727723421754483145354598542291389059730952536897407296725631390435306824149329251450428520017032068370905491236371588783551854860933656246846861645834009102275363106544337746297119821339365287420703692873394398852690091625453178968493127766149991473384937200789954598163517
q = 170986832479534233007906048950464510414382588164533889416767650420928742690929190093999799507883047422413122991286355305384227808800633111611572663168246588357071419165779511128259447564377245832827901688451015954867004306626552500789867499455455629032408110167560346510245108938981288797349665759162752876911
c = 15294238831055894095745317706739204020319929545635634316996804750424242996533741450795483290384329104330090410419090776738963732127756947425265305276394058773237118310164375814515488333015347737716139073947021972607133348357843542310589577847859875065651579863803460777883480006078771792286205582765870786584904810922437581419555823588531402681156158991972023042592179567351862630979979989132957073962160946903567157184627177910380657091234027709595863061642453096671316307805667922247180282486325569430449985678954185611299166777141304330040782500340791721548519463552822293017606441987565074653579432972931432057376
e = 65537
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
m = pow(c,d,N)
print(bytes.fromhex(hex(m)[2:]))
#flag{7428fbd7-639b-11ee-b51b-64d69af3cb76}easymath
from Crypto.Util.number import *
from random import *
p = getPrime(128)
seed = randint(2, p - 1)
class prng:
n = p
a,b = [randint(2, p - 1) for _ in range(2)]
def __init__(self,seed):
self.state = seed
def next(self):
self.state = (self.state * self.a + self.b) % self.n
return self.state
def main():
gen = prng(seed)
s = [seed]
s.append(gen.next())
s.append(gen.next())
s.append(gen.next())
s.append(gen.next())
s.append(gen.next())
s.append(gen.next())
f = open("output.txt",'w')
json.dump(s,f)
f.close()
flag = "flag{"+str(gen.next())+"}"
return flag
main()LCG,已知seed,但是不知道a,b,n
参考:LCG
exp:
from Crypto.Util.number import *
import gmpy2
output = [288530505749272642500730917886204398531, 63547143998110685331032679758907988154, 15151206512028268617888756820805603406, 268092204209244869520724955865278855216, 261067075335188593563542448889694952077, 138067838531633886698552659065694918861, 201319433320428898153580935653793106657]
t = []
for i in range(1,len(output)):
t.append(output[i]-output[i-1])
T = []
for i in range(1,len(t)-1):
T.append(t[i+1]*t[i-1] - t[i]**2)
m = []
for i in range(len(T)-1):
mm = gmpy2.gcd(T[i],T[i+1])
if isPrime(mm):
m.append(int(mm))
else:
for i in range(1,100):
if isPrime(mm // i):
mm = mm // i
m.append(int(mm))
break
print(m)
for i in m:
if isPrime(i):
a = gmpy2.invert(t[0],i) * t[1] % i
b = output[1] - a*output[0] % i
a_ = gmpy2.invert(a,i)
seed = output[0]
print("seed =",seed)
for j in range(7):
seed = (a * seed + b) % i
flag = "flag{"+str(seed)+"}"
print(flag)
#flag{302184756857257140159769321021979097116}ez_rsa
# from flag import flag
from Crypto.Util.number import getPrime
from math import prod
import libnum
with open("flag.txt","rb") as f:
flag = f.read().strip()
m = int.from_bytes(flag[:19],"big")
m1 = int.from_bytes(flag[19:],"big")
e = 65537
primes = [getPrime(64) for i in range(32)]
n = prod(primes)
c = pow(m1,e,n)
print("c =",c)
print("n =",n)
p = libnum.generate_prime(1024)
q = libnum.generate_prime(1024)
e1 = 13
e2 = 15
n1 = p * q
c1 = pow(m1, e1, n1)
c2 = pow(m1, e2, n1)
print("n1 =", n1)
print("e1 =", e1)
print("c1 =", c1)
print("n2 =", n1)
print("e2 =", e2)
print("c2 =", c2)
# c = 28535916699190273475273097091422420145718978597126134891571109006456944397344856577421369324831702083810238921719657496747722337086131545474384253288151783029981352196506749672783866527948391034258269669654392993063423671431837882584570973320095601407578443348352802850496429240170710269529489900871208384711844617081275862971410246759090936379744946527813691945129059991795202769186014306943707223831130752782380563227353615164053563120572722464543812139164048342504963081408349934180883607554389607335607410546630525512019818062185681153477671373000186961748278118124044645584490544698827467815360888525822167
# n = 114107341297408283801468814470303963122122556489590451040619457052827864984505912502462030175984161431709841571908269123131659496812467145870607611968843929870716066046232009282431653653484798819370087696248364531531706249180822839879862098012984590503284615395588919199545142177727328844260380842155437987767067800740569616584597507776426572206990858918111272636507821551592564540694671795374831548677720629329358177802890287837056940407030212276399942462042866947423728888561392653713356355778914658317507319575084393752755452971007289968044006561357799908892371839922838486713582082980752194204224263283004373
# n1 = 21235204662158833223664424963408105101885570855652885953922511758363954474947609854216589644512813634294435585894296340005122907229365513346971631594453999584706013889403572150499529308966742992668850443386284277210686717652643585324255759216699733045642544284406720854291604837774882256435503827543483289606177965628162259184958789025311291796067574924595051311298594432767265114154138693108465671184854794167878031822162731921299518989845784744659944947091213703810190708463199067553747177712259911724424547999547534441790125049383068377243727588278432796727885216967953646999183906479537750330738956233695342750567
# e1 = 13
# c1 = 5640630966585093229374938575158853304507369792931959909038819773057666482368490365383634362421839045569190487785222799103423460816096797210546343809620912249021763787314569982909943181390882015170344954037813745251119237402775124991005154299085147091159741067430623420349690886728161235034687649593258746455165172528681627568611599473627285223154284756417744280966157271904828156564067870877521824545300153084830020169048653830385763172792698591998191641849931039720453035065355411394516308865955772746815765864888631258825704788352584540380169938419618543124830541663995097651872542381
# n2 = 21235204662158833223664424963408105101885570855652885953922511758363954474947609854216589644512813634294435585894296340005122907229365513346971631594453999584706013889403572150499529308966742992668850443386284277210686717652643585324255759216699733045642544284406720854291604837774882256435503827543483289606177965628162259184958789025311291796067574924595051311298594432767265114154138693108465671184854794167878031822162731921299518989845784744659944947091213703810190708463199067553747177712259911724424547999547534441790125049383068377243727588278432796727885216967953646999183906479537750330738956233695342750567
# e2 = 15
# c2 = 5481001445755770090420425478456880914921441486935672376394423326451811448703288166341447356603281843336826624725965666634194700496514262129376916108926167953996689011980280761368893884042609095616407660087448963015169181749124738976578495911295096014725354350167650232970262765851074146687931181216305972147994236689422572940877763047930111954798962097847426932730342258169023809341164876019161104439561164839132092594444017039073155506935768658830659965630065643619399324102814118128802834719820426253836317043818687888302054465994498115387703382090351794495827905499417861507007863378916334790750453883661675063377part1
yafu分解得到32各因子求φ(n)
part2
共模攻击
exp:
import gmpy2
n1 = 114107341297408283801468814470303963122122556489590451040619457052827864984505912502462030175984161431709841571908269123131659496812467145870607611968843929870716066046232009282431653653484798819370087696248364531531706249180822839879862098012984590503284615395588919199545142177727328844260380842155437987767067800740569616584597507776426572206990858918111272636507821551592564540694671795374831548677720629329358177802890287837056940407030212276399942462042866947423728888561392653713356355778914658317507319575084393752755452971007289968044006561357799908892371839922838486713582082980752194204224263283004373
c = 28535916699190273475273097091422420145718978597126134891571109006456944397344856577421369324831702083810238921719657496747722337086131545474384253288151783029981352196506749672783866527948391034258269669654392993063423671431837882584570973320095601407578443348352802850496429240170710269529489900871208384711844617081275862971410246759090936379744946527813691945129059991795202769186014306943707223831130752782380563227353615164053563120572722464543812139164048342504963081408349934180883607554389607335607410546630525512019818062185681153477671373000186961748278118124044645584490544698827467815360888525822167
primes = [10436802938040427139,12712357180113548549,11502613740816749197,10270880245559150279,13498192768855092449,17075632607344331131,10100522426677320149,10635881647150245973,15622487550947237203,11777892065426651999,10040612110882504553,13428970346605599557,9261040693807289549,16651625235320957803,10126802520926958821,14198042938738648387,16946507762934111301,9723861249937499279,15774106340553595249,16340211116882594287,13618885037077024279,9356350172425710359,11718181938374860349,16880270107514803247,9281508366366115669,15616762946597906161,10986943768724409089,17088379813205887661,11964584391817142269,14147604789494386003,10621161426185076191,10203735303764112277]
phi = 1
for i in primes:
phi *= i-1
d = gmpy2.invert(65537,phi)
m = pow(c,d,n1)
flag1 = bytes.fromhex(hex(m)[2:])
n2 = 21235204662158833223664424963408105101885570855652885953922511758363954474947609854216589644512813634294435585894296340005122907229365513346971631594453999584706013889403572150499529308966742992668850443386284277210686717652643585324255759216699733045642544284406720854291604837774882256435503827543483289606177965628162259184958789025311291796067574924595051311298594432767265114154138693108465671184854794167878031822162731921299518989845784744659944947091213703810190708463199067553747177712259911724424547999547534441790125049383068377243727588278432796727885216967953646999183906479537750330738956233695342750567
e1 = 13
c1 = 5640630966585093229374938575158853304507369792931959909038819773057666482368490365383634362421839045569190487785222799103423460816096797210546343809620912249021763787314569982909943181390882015170344954037813745251119237402775124991005154299085147091159741067430623420349690886728161235034687649593258746455165172528681627568611599473627285223154284756417744280966157271904828156564067870877521824545300153084830020169048653830385763172792698591998191641849931039720453035065355411394516308865955772746815765864888631258825704788352584540380169938419618543124830541663995097651872542381
e2 = 15
c2 = 5481001445755770090420425478456880914921441486935672376394423326451811448703288166341447356603281843336826624725965666634194700496514262129376916108926167953996689011980280761368893884042609095616407660087448963015169181749124738976578495911295096014725354350167650232970262765851074146687931181216305972147994236689422572940877763047930111954798962097847426932730342258169023809341164876019161104439561164839132092594444017039073155506935768658830659965630065643619399324102814118128802834719820426253836317043818687888302054465994498115387703382090351794495827905499417861507007863378916334790750453883661675063377
s,x,y = gmpy2.gcdext(e1,e2)
m = (pow(c1,x,n2)*pow(c2,y,n2))%n2
flag2 = bytes.fromhex((hex(m)[2:]))
flag = flag1 + flag2
print(flag)
#flag{05929ec9778ed739d94ee1a77b742714}e?
p= 70724362259337647663584082414795381346569735601816096923682814277857463878289
q= 114427188167532721707398034034072867253267857672869034942206947096293901917007
e= 1314
c= 4308122681135507736058122041934864039713319497673888928736468819190185301630702240416683093700232966794026900978699666246019059398861283337865339404916304e和φ(n)不互素
exp:
import gmpy2
p= 70724362259337647663584082414795381346569735601816096923682814277857463878289
q= 114427188167532721707398034034072867253267857672869034942206947096293901917007
e= 1314
c= 4308122681135507736058122041934864039713319497673888928736468819190185301630702240416683093700232966794026900978699666246019059398861283337865339404916304
n = p * q
phi = (p-1)*(q-1)
t = gmpy2.gcd(e,phi)
d = gmpy2.invert(e // t,phi)
M = pow(c,d,n)
m = gmpy2.iroot(M,t)[0]
print(bytes.fromhex((hex(m)[2:])))
#flag{This_e_is_real_or_not}factorizing_n
n = 226515252384227990547287743140613580056836242860947832749754689048997071950972581790210817523352001702907675581567498443649554801433663166425134375454937126656357069687274036935331269594383360450823787099121079436459236734336130768046337169817940540921822023269188752420603975467384377614321048859304185067329741055517464271746238143742661897809442359331215501438861121047081117632626097939097519866099140569819965948998542652908170134545593659233229897003698175558888336706474178958535138595687148003367152624421106553412886263257022809480187410133186189435436294593588009551451899398811758511878324326255293307347560753524372663257044426744744426759970254203341706284024734042826158828749144322843934985927079504722440497388146240627249465363931951790326885478025237643
c = 52409805591744226507807531465616894934028463651864630447934395956954575834603756391651746535033902964658694070544877880970130028487381287088425209448038533705903737694267359561133766799228825599943891152463160326583722749586721691729062524310148743637505134465210906856660867852927837112666513674858029892207902196213784902541173835447263733760225682942461048573387925463479672527491229113710629340960375692432470493054415657845868577650170648157402682163577152288432313996310562452677399267755695644659367792066311336521698894993982901657735586844358679888210537898629281625526455444811591386493005341435516094660429968084363084301878446471676122069724608083578102382181382107225473535696274374370868301830807644939881080301668756603163431000745972823980427048672732291
e = 65537n能分解成p的5次方
exp:
from Crypto.Util.number import *
import gmpy2
n = 226515252384227990547287743140613580056836242860947832749754689048997071950972581790210817523352001702907675581567498443649554801433663166425134375454937126656357069687274036935331269594383360450823787099121079436459236734336130768046337169817940540921822023269188752420603975467384377614321048859304185067329741055517464271746238143742661897809442359331215501438861121047081117632626097939097519866099140569819965948998542652908170134545593659233229897003698175558888336706474178958535138595687148003367152624421106553412886263257022809480187410133186189435436294593588009551451899398811758511878324326255293307347560753524372663257044426744744426759970254203341706284024734042826158828749144322843934985927079504722440497388146240627249465363931951790326885478025237643
c = 52409805591744226507807531465616894934028463651864630447934395956954575834603756391651746535033902964658694070544877880970130028487381287088425209448038533705903737694267359561133766799228825599943891152463160326583722749586721691729062524310148743637505134465210906856660867852927837112666513674858029892207902196213784902541173835447263733760225682942461048573387925463479672527491229113710629340960375692432470493054415657845868577650170648157402682163577152288432313996310562452677399267755695644659367792066311336521698894993982901657735586844358679888210537898629281625526455444811591386493005341435516094660429968084363084301878446471676122069724608083578102382181382107225473535696274374370868301830807644939881080301668756603163431000745972823980427048672732291
e = 65537
p = 11776588228599764849559519654482976956833367474471407292255776713760090338489966385328569279135095351660161277221351884258247731394014018172166064062551483
phi = p**4 * (p-1)
d = gmpy2.invert(e,phi)
m = pow(c,d,n)
print(long_to_bytes(m))
#flag{1f95f530f85b940db810fc917607ee22}哈希猫
import hashlib
from secret import flag
assert flag[:5] == "flag{"
assert flag[-1:] == "}"
flag = flag[5:-1]
assert len(flag) == 43
print(hashlib.md5(flag[0:3].encode()).hexdigest())
print(hashlib.sha256(flag[3:5].encode()).hexdigest())
print(hashlib.sha512(flag[5:7].encode()).hexdigest())
print(hashlib.sha256(flag[7:9].encode()).hexdigest())
print(hashlib.sha256(flag[9:11].encode()).hexdigest())
print(hashlib.sha224(flag[11:13].encode()).hexdigest())
print(hashlib.sha224(flag[13:15].encode()).hexdigest())
print(hashlib.sha224(flag[15:17].encode()).hexdigest())
print(hashlib.sha1(flag[17:20].encode()).hexdigest())
print(hashlib.sha1(flag[20:23].encode()).hexdigest())
print(hashlib.sha512(flag[23:25].encode()).hexdigest())
print(hashlib.sha1(flag[25:28].encode()).hexdigest())
print(hashlib.sha256(flag[28:30].encode()).hexdigest())
print(hashlib.md5(flag[30:33].encode()).hexdigest())
print(hashlib.sha256(flag[33:35].encode()).hexdigest())
print(hashlib.sha1(flag[35:38].encode()).hexdigest())
print(hashlib.sha224(flag[38:40].encode()).hexdigest())
print(hashlib.md5(flag[40:43].encode()).hexdigest())
# bba78e7d3d6ea696bfef6e87a26a6c03
# 894461aba3e5e2724278cfc40fa15dc1510b0cd56430fec9fc8a90d6d8ebe5f7
# 092ca0da5f25c595eae6cc725dc12ae75889a639d205733223cb9cfaeaa702a521971e57f768079b03d53c8f092bb2c597cc3adb4a98224a144c5d62461beb52
# 122c597083bd438b7f6d72af75d025948899647711b806bdd2cd82fa69713db3
# 153812ae5fea0b73a011bf28bd7cea93644437c3fe3260b7b2d7e1e2f9f46bde
# 24296a0d1555ad424b04dd5f6268c5613dae32cde8a469ca8c9065b9
# 15d46f8eae648f5945c4605b15e0507836ee1251b74de2e95bf9394d
# 9afdf5d1027172492a32833975a69a1e501e6f824d3e5a7121ad18af
# 2b7655eb53f6f92086e58da465c6733bd8d8a1a3
# a44fce0412ae28173cf036700c3f1cc8c7a279c6
# 7356ea99a4fa12c6a3ed8ecc1e78a7bb28cdc1208962848646cf34e0d836f420cf594606cde74bec1dc2efe511dff0dd07b558bd0c7d01a526de2e9c25d47a6f
# cc5c3fe6e7356a26a134cff5633349f597c40a9d
# 757d22f85733770bae59cc857dcfc369db29031459421b808377cf06bc9881ad
# a2c7bdf97e3c761c431f8891dcc39fa9
# 0606c0e8f78de4d7a78522a5ae2f7b70e31e669e6e2a16e11c393e4443069813
# cb6c6c7cc8189868e1feaae773f947908233cdcc
# 2cb5169af85bd3122276f8b0a731ed2ea30c8bef366bfafe76b5e7db
# d1de3eac41792a7f498dae8f439bf16d一堆hash
exp:
import hashlib
from itertools import product
c = ["bba78e7d3d6ea696bfef6e87a26a6c03",
"894461aba3e5e2724278cfc40fa15dc1510b0cd56430fec9fc8a90d6d8ebe5f7",
"092ca0da5f25c595eae6cc725dc12ae75889a639d205733223cb9cfaeaa702a521971e57f768079b03d53c8f092bb2c597cc3adb4a98224a144c5d62461beb52",
"122c597083bd438b7f6d72af75d025948899647711b806bdd2cd82fa69713db3",
"153812ae5fea0b73a011bf28bd7cea93644437c3fe3260b7b2d7e1e2f9f46bde",
"24296a0d1555ad424b04dd5f6268c5613dae32cde8a469ca8c9065b9",
"15d46f8eae648f5945c4605b15e0507836ee1251b74de2e95bf9394d",
"9afdf5d1027172492a32833975a69a1e501e6f824d3e5a7121ad18af",
"2b7655eb53f6f92086e58da465c6733bd8d8a1a3",
"a44fce0412ae28173cf036700c3f1cc8c7a279c6",
"7356ea99a4fa12c6a3ed8ecc1e78a7bb28cdc1208962848646cf34e0d836f420cf594606cde74bec1dc2efe511dff0dd07b558bd0c7d01a526de2e9c25d47a6f",
"cc5c3fe6e7356a26a134cff5633349f597c40a9d",
"757d22f85733770bae59cc857dcfc369db29031459421b808377cf06bc9881ad",
"a2c7bdf97e3c761c431f8891dcc39fa9",
"0606c0e8f78de4d7a78522a5ae2f7b70e31e669e6e2a16e11c393e4443069813",
"cb6c6c7cc8189868e1feaae773f947908233cdcc",
"2cb5169af85bd3122276f8b0a731ed2ea30c8bef366bfafe76b5e7db",
"d1de3eac41792a7f498dae8f439bf16d"]
flag = "flag{"
table = [chr(i) for i in range(32,128)]
for i in product(table,repeat=3):
m = "".join(i)
hash = hashlib.md5(m.encode()).hexdigest()
if hash == c[0]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha256(m.encode()).hexdigest()
if hash == c[1]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha512(m.encode()).hexdigest()
if hash == c[2]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha256(m.encode()).hexdigest()
if hash == c[3]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha256(m.encode()).hexdigest()
if hash == c[4]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha224(m.encode()).hexdigest()
if hash == c[5]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha224(m.encode()).hexdigest()
if hash == c[6]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha224(m.encode()).hexdigest()
if hash == c[7]:
flag += m
print(flag)
for i in product(table,repeat=3):
m = "".join(i)
hash = hashlib.sha1(m.encode()).hexdigest()
if hash == c[8]:
flag += m
print(flag)
for i in product(table,repeat=3):
m = "".join(i)
hash = hashlib.sha1(m.encode()).hexdigest()
if hash == c[9]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha512(m.encode()).hexdigest()
if hash == c[10]:
flag += m
print(flag)
for i in product(table,repeat=3):
m = "".join(i)
hash = hashlib.sha1(m.encode()).hexdigest()
if hash == c[11]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha256(m.encode()).hexdigest()
if hash == c[12]:
flag += m
print(flag)
for i in product(table,repeat=3):
m = "".join(i)
hash = hashlib.md5(m.encode()).hexdigest()
if hash == c[13]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha256(m.encode()).hexdigest()
if hash == c[14]:
flag += m
print(flag)
for i in product(table,repeat=3):
m = "".join(i)
hash = hashlib.sha1(m.encode()).hexdigest()
if hash == c[15]:
flag += m
print(flag)
for i in product(table,repeat=2):
m = "".join(i)
hash = hashlib.sha224(m.encode()).hexdigest()
if hash == c[16]:
flag += m
print(flag)
for i in product(table,repeat=3):
m = "".join(i)
hash = hashlib.md5(m.encode()).hexdigest()
if hash == c[17]:
flag += m
flag += "}"
print(flag)
#flag{YOU'vE_c0m3_To_UNDerS7anD_Ha5H_GDIbgdF3EocT}WEEK3
Classical Master
import math
from secret import s
s = s.lower()
keyM = [?]
l = len(keyM)
assert(math.gcd(l,26)==1)
for i in range(len(s)):
print(chr((ord(s[i])*l-97+(keyM[i % l]))%26+97),end="")
#exp:
import collections
import string
max_lenth = 20
enc = ''
def group_text(ciphertext, key_length):
# 根据密钥长度将密文分组
groups = ['' for _ in range(key_length)]
for i, char in enumerate(ciphertext):
groups[i % key_length] += char
return groups
def frequency_analysis(text):
# 统计字母出现频率
freq_counter = collections.Counter(text)
total_chars = len(text)
return {char: freq / total_chars for char, freq in freq_counter.items()}
def guess_key_length(ciphertext):
max_key_length = min(len(ciphertext), max_lenth) # 假设密钥最大长度为20
best_key_length = 1
best_index_of_coincidence = 0.0
for key_length in range(1, max_key_length + 1):
groups = group_text(ciphertext, key_length)
index_of_coincidence_sum = 0.0
for group in groups:
freq_analysis = frequency_analysis(group)
index_of_coincidence_sum += sum(freq ** 2 for freq in freq_analysis.values())
average_index_of_coincidence = index_of_coincidence_sum / key_length
if average_index_of_coincidence > best_index_of_coincidence:
best_index_of_coincidence = average_index_of_coincidence
best_key_length = key_length
return best_key_length
key_length = guess_key_length(enc)
print(key_length)
# plain to cipher
ptoc = [["" for i in range(26)] for j in range(26)]
for i in range(26):
for key in range(26):
ptoc[i][key] = chr((ord(string.ascii_lowercase[i]) * key_length - 97 + (key)) % 26 + 97)
ctop = [["" for i in range(26)] for j in range(26)]
for i in range(26):
for key in range(26):
temp1 = ord(string.ascii_lowercase[i]) - 97
while (1):
if ((temp1 - key + 97) % key_length == 0):
chr1 = (temp1 - key + 97) // key_length
if (chr1 >= 97 and chr1 <= 122):
ctop[i][key] = chr(chr1)
break
temp1 += 26
list_usual = [0.082, 0.015, 0.028, 0.043, 0.127, 0.022, 0.020, 0.061, 0.070, 0.002, 0.008, 0.040, 0.024, 0.067, 0.075, 0.019, 0.001, 0.060, 0.063, 0.091, 0.028, 0.010, 0.023, 0.001, 0.020, 0.001]
def guess_key(ciphertext, key_length, list_usual):
groups = group_text(ciphertext, key_length)
key = []
for group in groups:
freq_analysis = frequency_analysis(group)
# 计算每个密钥字母的偏移量
max_correlation = 0
best_shift = 0
for shift in range(26):
correlation = sum(freq_analysis.get(letter, 0) * list_usual[string.ascii_lowercase.index(ctop[idx][shift])] for idx, letter in enumerate(string.ascii_lowercase))
if correlation > max_correlation:
max_correlation = correlation
best_shift = shift
key.append(best_shift)
return key
key = guess_key(enc,key_length,list_usual)
print(key)
c = ''
for i in range(len(enc)):
temp1 = ord(enc[i]) - 97
tkey = key[i%key_length]
while (1):
if ((temp1 - tkey + 97) % key_length == 0):
chr1 = (temp1 - tkey + 97) // key_length
if (chr1 >= 97 and chr1 <= 122):
c += chr(chr1)
break
temp1 += 26
print(c)
#flag{youaretherealmaster}e=3
from Crypto.Util.number import *
import random
from secret import flag
M = 2**54
k = 6
def gen_prime(M, k):
while True:
prime = sum([random.getrandbits(16) * M**i for i in range(k)])
if isPrime(prime) and (prime-1) % 3 == 0:
return prime
p, q, r = [gen_prime(M, k) for i in range(3)]
N = p * q * r
e = 3
m = bytes_to_long(flag)
c = pow(m, e, N)
print(f'N = {N}')
print(f'c = {c}')
"""
N = 3298593732762513945346583663585189774036688951059270517149719979434109398447628726951796006700754759352430339647168415338320547665794785951232342902233013221132246450312038122695046634624323814318286314664160113738299465643128504110932989263063331290006313
c = 869489491924953293290699796392271834401780578884556874640489836779925847562085802848542382525324081900560761299059365684697233025590164192409062717942292142906458498707677300694595072310705415037345581289469698221468377159605973403471463296806900975548438
"""p,q,r都可以表示为M进制,于是可以用多项式来分解N,因为e和phi不互素,所以用有限域开根,再用中国剩余定理
exp:
from Crypto.Util.number import *
import gmpy2
N = 3298593732762513945346583663585189774036688951059270517149719979434109398447628726951796006700754759352430339647168415338320547665794785951232342902233013221132246450312038122695046634624323814318286314664160113738299465643128504110932989263063331290006313
c = 869489491924953293290699796392271834401780578884556874640489836779925847562085802848542382525324081900560761299059365684697233025590164192409062717942292142906458498707677300694595072310705415037345581289469698221468377159605973403471463296806900975548438
M = 2^54
poly = sum(e * x^i for i,e in enumerate(Integer(N).digits(M)))
# poly = 483094776500*x^15 + 67737188732830*x^14 + 124085394790974*x^13 + 195683246513428*x^12 + 273742579935809*x^11 + 458380068952801*x^10 + 592623629284873*x^9 + 582132325688443*x^8 + 685453135920467*x^7 + 720971197330040*x^6 + 597860219518539*x^5 + 434712532854786*x^4 + 332870394840336*x^3 + 251268756615643*x^2 + 110730229142998*x + 17535693800233
(p,_),(q,_),(r,_) = poly.factor_list()
p, q ,r = p(x=M),q(x=M),r(x=M)
# print(p)
# print(q)
# print(r)
# 103574226729554375480512668967949133854292403117507474988278388756193462602107352821951
# 47963432552002818180880760250824590058982930733941748241661938238195705638187268342813
# 663998156522471100999941798165706402858681862228017448075268472245282758965006970051
e = 3
R.<x> = Zmod(p)[]
f = x^e-c
f = f.monic()
res1 = f.roots()
R.<x> = Zmod(q)[]
f = x^e-c
f = f.monic()
res2 = f.roots()
R.<x> = Zmod(r)[]
f = x^e-c
f = f.monic()
res3 = f.roots()
for i in res1:
for j in res2:
for k in res3:
m = crt([int(i[0]),int(j[0]),int(k[0])],[int(p),int(q),int(r)])
flag = long_to_bytes(int(m))
if b"flag" in flag:
print(flag)
break
# flag{e1b7d2c2-e265-11eb-b693-98fa9b5bc5fe}撤退!
from Crypto.Util.number import *
flag = *******
p = getPrime(1024)
q = getPrime(1024)
n = p * q
hb = len(flag)//2
hb1 = bytes_to_long(flag[:hb])
hb2 = bytes_to_long(flag[hb:])
D = 117
x = *******
y = *******
assert x**2 - D * y**2 == 1
enc1 = pow(334 * n ** 2 + 1, hb1, n ** 3)
enc2 = pow(y * n + 1, hb2, n ** 3)
print(n)
print(enc1)
print(enc2)
'''
22970461944771505344360312103272646796516672838005008112295760406393062653512719537671401409823031480497512491850701737384621917068068328814717390355072928714618936469722031401433712342846780800586803218279291870162605299119904016959036663767093191710796830156169925350938267584422752300171293262391805105435418210827517225439398971437884496416502510866914857269951072184669675339439115587325754431761172634305242650221404868035624879538862880516438147301289746375407945908866907822940285764276956194031840381838253923392794376568293056359058519233175242523219646628321609305890926063856400793680641992567798104042179
26380574883568223071748995929433720836641856899148821439556557592284999544802260386919172895274884666117488851000353221957579311943624258651646692068406462392980585841604755021251430357273933800209194484692955106014890051223465745443628784077844452303995642424661442978294757109040081050794398646640530714904683097650259060507908334791761124660725589404056356987726993518057050112725483482660202442987346646160168856264312557595890710521723067518303906942469282527855551751244126251698491010628369012024332666619702895796133780038584346428759785302542637171018926824843416176876077558936427399803328577151066597396550597352625005028261156114571696860700477410270949916316951150072218466374341394892405947793726872954497972795793421222424616005278493704125169150432275472846871295341469911428057621028515874978272004775903906188556908968810828510069826724631700523623584802605889173266453916347583720706846630531082266742377818663000322817114065116737931523412220137972079139507877669106470150742546914051556747087768279286696519700220233815812834114117581332234344024169109786527295900675653245014343393093832478814567179131966404207553408747774003319241150221488231674711614902743345516888975702483348011349617017294004761259419165663633915672647187482242462163420462987034240805524991
21190674872507845600786632640969893237129139877891071648594239906632201421611954626926407751780936578853046780585253060958265549804784845192757301417173404074965693840282568701968464564320290763073618132775799910356101999797720378313304899173154753858674284071499775857913937184713024788245068426198878834805943703426673512761178072458895973672088230653246356764681418231485563287856188079274727706554037799748595877069143254516390328019381867648697880975670688337068196993846986940286056873616919629721264139576692806770826129279380704466982862393203486037890448173834315360975464927583664991534571518159777852793416869350127023692816051992183670690315184731534611966603509867722931839839084915943647295195314171688904055674915382434841320612108023531722571519492067471405656160804893645713608592561788743509876384862097871840094582513721456962354498561006793609200187065931433827465455037397503619844768415369973322759940610358415184510344945559838007474725413347675347453443583610217539704055467297318282309867987435252614428856515259899385689971172417660178761139941056839133998928898528744331662995956041897599276732929020537698559927654297185422925737241274711904687894411308774527520523946951208805307060323875839353707549772052299847176824964552693112658495961070555882583739017417359463576705453026824255338859618053086622031941
'''
exp:
#sage
n =
enc1 =
enc2 =
numTry = 1500
def solve_pell(N, numTry):
cf = continued_fraction(sqrt(N))
for i in range(numTry):
denom = cf.denominator(i)
numer = cf.numerator(i)
if numer^2 - N * denom^2 == 1:
return numer, denom
return None, None
x,y = solve_pell(N,numTry)
# print(x,y)
# x = 649
# y = 60
var('m')
f = 334*m*n^2 + 1 == enc1
ans = solve(f,m)
# print(ans)
m1 = 149691910197777805350862530703771372803641869951585
flag1 = long_to_bytes(int(m1))
c1 = (enc2-1) // n
var('m')
f = m*y + (m*(m-1)/2) * y^2*n - c1
ans = solve(f,m)
# print(ans)
m2 = 149371042625025154522769720206540986718252215526781
flag2 = long_to_bytes(int(m2))
print(flag1+flag2)
#flag{6c6eb27a-061b-baf4-4cae26-5a609588ce}好好好!
***EGK*MAPZ**3TISLXYHW*B4*R*6CQV
e=65537
dp=89183181604123417010894108474901628410408206538085478807758137668201829058797702838603939730356798163745078443656032825128645105954284119126609502005130005399692420386460970318283171848176434285488698019425286328269756591931253074416895028845240978211030365697435579850343911269163064228581083838914477473793
n=17133884272385326910236146208723169235592379139078245324256146697759098524213354087333170410075813764497353656874360657828668202585141557095326829141561993608634568037533128091918704136052835609732443342167341276983343070200953604216445186924411131823487594273213380078485528148801722039459601896275130691200206027353715109606722659553700867073796386669768748305283547862565020499794358571741903375812063001390288166187510171105241363677243530996160649133253643422391688399573703498726489248479978887237752214015456924632092625018668632234215462091314384917176427670194819828555385014264912614752917792278216214856001
c=7297673446200396117470312266735704951424121735299327785232249350567349180167473433806232931862684106388722088953786183522191592452252650217579986150373463901393038386627370305688040315665037164819432754099421229466379901436696822022518438390977543864543590936753547325597766614648063328562516667604171990354928485383191174966274941678597887943784661684719053108281896697098991347034225406718530599672101743303723470910913422462764406680309933367328977341637394665138995676573466380198978810546689819954949832833954061771415463198737542769848298258925680570823701939997224167603657418270886620562332895947413332492672dp泄露求解得到base32的密文7U25DUJJ7USYATEN5SREOFFG5NY57FPS77U5DFPY54JEG3NYKWSYA3YD5CXYTTNW53QS====,然后爆破base32的表完成求解
exp:
from Crypto.Util.number import long_to_bytes
import gmpy2
e=65537
dp=
n=
c=
def dp_leak(dp,c,n,e):
for i in range(1,e):
t = (dp * e - 1) % i
if t == 0:
p = (dp * e - 1) // i + 1
if n % p == 0:
q = n // p
d = gmpy2.invert(e,(p-1)*(q-1))
print(long_to_bytes(pow(c,d,n)))
dp_leak(dp,c,n,e)
#7U25DUJJ7USYATEN5SREOFFG5NY57FPS77U5DFPY54JEG3NYKWSYA3YD5CXYTTNW53QS====爆破base32的表
import base64
cipher = "7U25DUJJ7USYATEN5SREOFFG5NY57FPS77U5DFPY54JEG3NYKWSYA3YD5CXYTTNW53QS===="
table1 = "ABCDEFGHIJKLMNOPQRSTUVWXYZ234567" #这是base32的表
table2 = "EGKMAPZ3TISLXYHWB4R6CQV"
list = []
for i in table1:
if not (i in table2):
list.append(i)
print(list)
for i in list:
for j in list:
if i != j:
for k in list:
if i != k and j != k:
for n in list:
if i != n and j != n and k != n:
for t in list:
if i != t and j != t and k != t and n != t:
for tt in list:
if i != tt and j != tt and k != tt and n != tt and t !=tt:
for ttt in list:
if i != ttt and j != ttt and k != ttt and n != ttt and t !=ttt and tt != ttt:
for tttt in list:
if i != tttt and j != tttt and k != tttt and n != tttt and t !=tttt and tt != tttt and ttt != tttt:
for ttttt in list:
if i != ttttt and j != ttttt and k != ttttt and n != ttttt and t !=ttttt and tt != ttttt and ttt != ttttt and tttt != ttttt:
pad1 = '' + i + j + k
table2 = pad1 + "EGK" + n + "MAPZ" + t + tt +"3TISLXYHW" + ttt + "B4" + tttt + "R" + ttttt + "6CQV"
flag = base64.b32decode(cipher.translate(str.maketrans(table2,table1)))
if b"flag" in flag:
print(flag)
#flag{fa48a440-d0ff-0c2a-366243-a46b7e7853}easyrsa
from Crypto.Util.number import *
from flag import flag
p1 = getPrime(512)
q1 = getPrime(512)
n1 = p1 * q1
e = 65537
p2 = getPrime(1024)
q2 = getPrime(1024)
n2 = p2 * q2
leak1 = (p2+q2) >> 400
leak2 = (p1 & ((1 << 350) - 1)) >> 5
enc = pow(leak2,e,n2)
c = pow(bytes_to_long(flag),e,n1)
f = open(f'output.txt','w')
f.write(f'n1 = {n1}\n')
f.write(f'n2 = {n2}\n')
f.write(f'leak1 = {leak1}\n')
f.write(f'enc = {enc}\n')
f.write(f'c = {c}')
f.close()通过leak1来求leak2,leak2即是p1的低350位(但是被抹去了低5位,后面要爆破一下)
参考文章:2023 贵阳大数据安全精英赛 --- Crypto childrsa wp
联立leak1 = (p2 + q2) >> 400和n2 = p2 * q2求解的结果和p2的高位一样,只是低400位不一样
有了p2的高位后,利用coppersmith进行求解p2
exp:
n2 =
leak1 =
enc =
RF = RealField(2048)
X = polygen(RF)
f = X * ((leak1 << 400)-X) - n2
# 求p2
sol = int(f.roots()[0][0])
p_high = (sol >> 430) << 430
PR.<x> = PolynomialRing(Zmod(n2))
f1 = x + p_high
x0 =f1.small_roots(X=2^430, beta=0.4)[0]
p2 = p_high + x0
print(f"p2 = {p2}")
# 求leak2
q2 =N // int(p2)
print(f"q2 = {q2}")
phi = (p2-1)*(q2-1)
d = gmpy2.invert(e,gmpy2.mpz(phi))
leak2 = pow(enc,d,n2)
print(f"leak2 = {leak2}")
# leak2 = 17360313144717510037537355688628643303848718125498770246433419674664931177802009718523022408554028650268575473276776652325042704063954902971874624580258429965610657615998701297143056706693836430020853673136823114239697815838085813271681130436537239288366997343978169099703086258100321964287523989425007035962983601510451873274120392974576079344343289173636686941721922540549894873583626722606223542204019760103801900148734981271526662512960432004374861666967746492254621730914184468921861371761515561318710135049915102041347748291394096585038509541586487535668372772139517571028910559303129731751631963650606704284688再通过leak2求解flag
exp:
from Crypto.Util.number import *
import gmpy2
e = 65537
n =
c =
leak2 = 22334810767801800995021872014176778873829048161801414909315794486047873481911273730826962574216771288781
leak2 = leak2 << 5
for i in range(2^5):
plow = leak2 + i
R.<x> = PolynomialRing(Zmod(n))
f = x * 2^350 + plow
f = f.monic()
roots = f.small_roots(X = 2^162,beta=0.4)
if roots:
p = int(roots[0]) * 2^350 + plow
print(p)
q = n // p
d = gmpy2.invert(e,(int(p)-1)*(int(q)-1))
m = pow(c,d,n)
print(long_to_bytes(int(m)))
break
# flag{9995eae8acaac286c7b72e50e5258dc3}ECC
from Crypto.Util.number import bytes_to_long ,getPrime
from random import randint
from secret import flag , p, A, B
class LCG:
def __init__(self, seed, multiplier, increment, modulus):
self.state = seed
self.multiplier = multiplier
self.increment = increment
self.modulus = modulus
def round(self):
self.state = (self.state * self.multiplier + self.increment) % self.modulus
return self.state
LcG = LCG(p, A, B, getPrime(300))
hint = []
rounds = randint(9,999)
for i in range(rounds):
hint.append(LcG.round())
print('N =', LcG.modulus)
print('hint =', hint[rounds-3:])
print('rounds =',rounds)
m = bytes_to_long(flag)
E = EllipticCurve(GF(p),[A,B])
P = E.random_point()
Q = m*P
print ('P:',P)
print ('Q:',Q)
# N = 1394352669118552710431836954956199165049966552966771775234358569430031450944715218123897207
# hint = [1355490957378506208208697701592950672672094387068804168531572728350762596829890135826003351, 112984469981193183570958290700584499305718437364882160259618096856045410765383317657942333, 116900480821095370484396815088833958436491607704440051600260019545590977856114612401304297]
# rounds = 39
# P:(25557735861606771704777704605284674181045459246221320438838413903928959660565 : 75510453815577804349033849040800841183099607056251418172827154938451453589656 : 1)
# Q:(56046292811652277371790197347740341815488809388747680953471201733291992185794 : 23661917912317435018072803232589214290695988219345248858537157579403272314 : 1)先解LCG得到椭圆曲线的参数,然后发现椭圆曲线的阶和p一样,运用SmartAttack即可
exp:
from Crypto.Util.number import long_to_bytes
import gmpy2
n =
output =
rounds = 39
p1 = output[-1] - output[-2]
p2 = output[-2] - output[-3]
Ani = gmpy2.invert(p2,n)
a = p1 * Ani % n
b = (output[-1] - a*output[-2]) % n
ani = gmpy2.invert(a,n)
seed = output[-1]
for i in range(rounds):
seed = ani * (seed-b) % n
p = seed
print("p =",p)
print("A =",a)
print("B =",b)
E = EllipticCurve(GF(p),[a,b])
print(E.order())
P =
Q =
def SmartAttack(P,Q,p):
E = P.curve()
Eqp = EllipticCurve(Qp(p, 2), [ ZZ(t) + randint(0,p)*p for t in E.a_invariants() ])
P_Qps = Eqp.lift_x(ZZ(P.xy()[0]), all=True)
for P_Qp in P_Qps:
if GF(p)(P_Qp.xy()[1]) == P.xy()[1]:
break
Q_Qps = Eqp.lift_x(ZZ(Q.xy()[0]), all=True)
for Q_Qp in Q_Qps:
if GF(p)(Q_Qp.xy()[1]) == Q.xy()[1]:
break
p_times_P = p*P_Qp
p_times_Q = p*Q_Qp
x_P,y_P = p_times_P.xy()
x_Q,y_Q = p_times_Q.xy()
phi_P = -(x_P/y_P)
phi_Q = -(x_Q/y_Q)
k = phi_Q/phi_P
return ZZ(k)
m = SmartAttack(P,Q,p)
print(long_to_bytes(int(m)))
# flag{7H4T5_e4sye5T_ECc_o9b8E3}2023 SHCTF-校外赛道 Crypto—Wp的更多相关文章
- bugku crypto wp上半部分汇总
1.滴答~滴 摩斯码,在线解开. 2. 栅栏密码,在线解就出flag了. 3. Ook解密,由.?!Ook组成密文,在线网站解密 4.这不是摩斯密码 有点像jsfuck,发现又不是,因为不会出现大于号 ...
- BUUCTF Crypto
BUUCTF 几道crypto WP [AFCTF2018]Morse 简单的莫尔斯密码,最直观的莫尔斯密码是直接采用空格分割的点和划线,这题稍微绕了一下使用的是斜杠来划分 所以首先将斜杠全部替换为空 ...
- 2021羊城杯比赛复现(Crypto)
bigrsa 题目: from Crypto.Util.number import * from flag import * n1 = 10383529640908175186077053551474 ...
- BUUCTF Crypto_WP(2)
BUUCTF Crypto WP 几道密码学wp [GXYCTF2019]CheckIn 知识点:Base64,rot47 下载文件后,发现一个txt文件,打开发现一串base64,界面之后出现一串乱 ...
- DawgCTF wp(re和crypto)
简单写写思路,想看详解的..我脚本有些丢失了..师傅请移步. 挂了个vpn,算正式打这种国际赛,全是英文.上去打了两天,昨晚晚上划水了一晚上补作业...,re那时候写出来三道,Potentially ...
- MRCTF (re和crypto)wp
RE: 一.PixelShooter(这题比赛我居然没看,靠,血亏,所以做不出来就不要一直死怼,这题挺好写的,) unity一般是用c#写的,刚好又是apk,可以用dnspy来反编译看看,在源码中找到 ...
- 第二届 BJD wp(reverse和crypto)
re 1.第一题拖入ida,flag就是直接明文摆着 2.第二题是8086的程序,拖入ida,发现有个jmp无限跳转,可能是段寄存器被修改了,ida无法将后面的汇编识别出来,所以后面才有很多无效数据, ...
- HGAME 2023 WP week1
WEEK1 web Classic Childhood Game 一眼顶真,直接翻js文件,在Events.js中找到mota(),猜测是获取flag,var a = ['\x59\x55\x64\x ...
- BUUCTF CRYPTO部分题目wp
对密码学了解不多,做一下熟悉熟悉 1,看我回旋踢 给的密文synt{5pq1004q-86n5-46q8-o720-oro5on0417r1} 简单的凯撒密码,用http://www.zjslove. ...
- CG-CTF CRYPTO部分wp
1,easybase64解密得flag 2,keyboard键盘码,在键盘上画画得flag:areuhack 3,异性相吸根据提示,写脚本 with open('密文.txt')as a: a=a.r ...
随机推荐
- 关于ChatGPT与机器时代的展望
关于 ChatGPT 与机器时代的展望 机器人这一概念,最初不是出自计算机科学家或工程师之手,而是来自于捷克的戏剧家卡雷尔·恰佩克(Karl Capek)在 1920 年编排的一出名为"罗森 ...
- 新版Google浏览器跨域Cookie解决方案
一.前言 针对Chrome版本67及以上 不能将其他域的Cookie传递过来 注意,这个里面的SameSite不能设为null,设空的话,还是会走默认值Lax 其中,SameSite的值可以填3个:S ...
- python添加水印
# coding:utf-8 from PIL import Image, ImageDraw, ImageFont def add_text_to_image(image, text): font ...
- OpenCV4之特征提取与对象检测
1.图像特征概述 图像特征的定义与表示 图像特征表示是该图像唯一的表述,是图像的DNA 图像特征提取概述 传统图像特征提取 - 主要基于纹理.角点.颜色分布.梯度.边缘等 深度卷积神经网络特征提取 - ...
- C++子类的构造函数
子类的构造函数 子类可以有自己的构造函数 子类没有构造函数,默认系统会调用父类的构造函数 子类有自己的构造函数,系统会先运行父类的构造函数,随后运行子类的构造函数,对子类对象进行覆盖和拓展 即不论子类 ...
- Vue错误:Cannot read properties of undefined (reading '$router')
解决方案 这是由于this的指向有问题,我们只需要重新声明一下this就可以重新调用了
- 从原理聊JVM(四):JVM中的方法调用原理
1 引言 多态是Java语言极为重要的一个特性,可以说是Java语言动态性的根本,那么线程执行一个方法时到底在内存中经历了什么,JVM又是如何确定方法执行版本的呢? 2 栈帧 JVM中由栈帧存储方法的 ...
- 文心一言 VS 讯飞星火 VS chatgpt (72)-- 算法导论7.1 3题
三.请简要地证明:在规模为 n 的子数组上,PARTITION 的时间复杂度为 Θ(n). 文心一言: 首先,我们需要明确PARTITION函数的具体定义.PARTITION函数通常用于快速排序算法中 ...
- [grpc]双向tls加密认证
前言 假设gRPC服务端的主机名为qw.er.com,需要为gRPC服务端和客户端之间的通信配置tls双向认证加密. 生成证书 生成ca根证书.生成过程会要求填写密码.CN.ON.OU等信息,记住密码 ...
- linux设置信号量系统参数
前言 信号量是IPC(进程间通信)机制的一种,用于协调多个进程或线程对共享数据的读写操作,本质上是一个计数器.类似于锁,主要用于保护共享资源,控制同时访问资源的进程数. 信号量只允许调用者对它进行等待 ...
