Metasploit (二)
1、测试一台搭建的主机
msf > db_nmap -n -A 10.140.110.16
[*] Nmap: Starting Nmap 7.60 ( https://nmap.org ) at 2018-09-04 20:19 CST
[*] Nmap: Nmap scan report for 10.140.110.16
[*] Nmap: Host is up (0.093s latency).
[*] Nmap: Not shown: 982 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 135/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 139/tcp open netbios-ssn Microsoft Windows netbios-ssn
[*] Nmap: 443/tcp open ssl/http VMware VirtualCenter Web service
[*] Nmap: |_http-title: Site doesn't have a title (text; charset=plain).
[*] Nmap: | ssl-cert: Subject: commonName=VMware/countryName=US
[*] Nmap: | Not valid before: 2017-03-12T12:26:45
[*] Nmap: |_Not valid after: 2018-03-12T12:26:45
[*] Nmap: |_ssl-date: 2018-09-04T12:23:06+00:00; +17s from scanner time.
[*] Nmap: | vmware-version:
[*] Nmap: | Server version: VMware Workstation 10.0.3
[*] Nmap: | Build: 1895310
[*] Nmap: | Locale version: INTL
[*] Nmap: | OS type: win32-x86
[*] Nmap: |_ Product Line ID: ws
[*] Nmap: 445/tcp open microsoft-ds Windows 7 Ultimate 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
[*] Nmap: 514/tcp filtered shell
[*] Nmap: 902/tcp open nagios-nsca Nagios NSCA
[*] Nmap: 912/tcp open vmware-auth VMware Authentication Daemon 1.0 (Uses VNC, SOAP)
[*] Nmap: 1688/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 3011/tcp open http Tridium Niagara httpd 3.0 (Platform: Windows 7)
[*] Nmap: | http-robots.txt: 1 disallowed entry
[*] Nmap: |_/
[*] Nmap: |_http-server-header: Niagara Web Server/3.0
[*] Nmap: |_http-title: Site doesn't have a title (text/html).
[*] Nmap: 3306/tcp open mysql MySQL (unauthorized)
[*] Nmap: 3389/tcp open ms-wbt-server?
[*] Nmap: 8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
[*] Nmap: |_ajp-methods: Failed to get a valid response for the OPTION request
[*] Nmap: 8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
[*] Nmap: |_http-favicon: Apache Tomcat
[*] Nmap: |_http-open-proxy: Proxy might be redirecting requests
[*] Nmap: |_http-server-header: Apache-Coyote/1.1
[*] Nmap: |_http-title: Apache Tomcat/7.0.37
[*] Nmap: 49152/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49153/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49154/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49156/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49163/tcp open msrpc Microsoft Windows RPC
[*] Nmap: Device type: general purpose
[*] Nmap: Running: Microsoft Windows XP|7|2012
[*] Nmap: OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2012
[*] Nmap: OS details: Microsoft Windows XP SP3, Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012
[*] Nmap: Network Distance: 2 hops
[*] Nmap: Service Info: Host: MS-20160714YUJH; OS: Windows; Device: specialized; CPE: cpe:/o:microsoft:windows
[*] Nmap: Host script results:
[*] Nmap: |_clock-skew: mean: 17s, deviation: 0s, median: 16s
[*] Nmap: |_nbstat: NetBIOS name: MS-20160714YUJH, NetBIOS user: <unknown>, NetBIOS MAC: 34:97:f6:90:9e:c9 (Asustek Computer)
[*] Nmap: | smb-os-discovery:
[*] Nmap: | OS: Windows 7 Ultimate 7601 Service Pack 1 (Windows 7 Ultimate 6.1)
[*] Nmap: | OS CPE: cpe:/o:microsoft:windows_7::sp1
[*] Nmap: | Computer name: MS-20160714YUJH
[*] Nmap: | NetBIOS computer name: MS-20160714YUJH\x00
[*] Nmap: | Workgroup: WORKGROUP\x00
[*] Nmap: |_ System time: 2018-09-04T20:23:07+08:00
[*] Nmap: | smb-security-mode:
[*] Nmap: | account_used: guest
[*] Nmap: | authentication_level: user
[*] Nmap: | challenge_response: supported
[*] Nmap: |_ message_signing: disabled (dangerous, but default)
[*] Nmap: | smb2-security-mode:
[*] Nmap: | 2.02:
[*] Nmap: |_ Message signing enabled but not required
[*] Nmap: | smb2-time:
[*] Nmap: | date: 2018-09-04 20:23:06
[*] Nmap: |_ start_date: 2018-09-04 08:28:38
[*] Nmap: TRACEROUTE (using port 80/tcp)
[*] Nmap: HOP RTT ADDRESS
[*] Nmap: 1 0.18 ms 192.168.142.2
[*] Nmap: 2 0.14 ms 10.140.110.16
[*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 233.14 seconds
查询开启的服务
msf > service
[*] exec: service
Usage: service < option > | --status-all | [ service_name [ command | --full-restart ] ]
msf > services
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
10.140.110.16 135 tcp msrpc open Microsoft Windows RPC
10.140.110.16 139 tcp netbios-ssn open Microsoft Windows netbios-ssn
10.140.110.16 443 tcp ssl/http open VMware VirtualCenter Web service
10.140.110.16 445 tcp microsoft-ds open Windows 7 Ultimate 7601 Service Pack 1 microsoft-ds workgroup: WORKGROUP
10.140.110.16 514 tcp shell filtered
10.140.110.16 902 tcp nagios-nsca open Nagios NSCA
10.140.110.16 912 tcp vmware-auth open VMware Authentication Daemon 1.0 Uses VNC, SOAP
10.140.110.16 1688 tcp msrpc open Microsoft Windows RPC
10.140.110.16 3011 tcp http open Tridium Niagara httpd 3.0 Platform: Windows 7
10.140.110.16 3306 tcp mysql open MySQL unauthorized
10.140.110.16 3389 tcp ms-wbt-server open
10.140.110.16 8009 tcp ajp13 open Apache Jserv Protocol v1.3
10.140.110.16 8080 tcp http open Apache Tomcat/Coyote JSP engine 1.1
10.140.110.16 49152 tcp msrpc open Microsoft Windows RPC
10.140.110.16 49153 tcp msrpc open Microsoft Windows RPC
10.140.110.16 49154 tcp msrpc open Microsoft Windows RPC
10.140.110.16 49156 tcp msrpc open Microsoft Windows RPC
10.140.110.16 49163 tcp msrpc open Microsoft Windows RPC
202.201.39.51 22 tcp ssh open OpenSSH 5.3 protocol 2.0
202.201.39.51 80 tcp http open Apache httpd 2.2.15 (CentOS)
202.201.39.51 135 tcp msrpc filtered
202.201.39.51 139 tcp netbios-ssn filtered
202.201.39.51 445 tcp microsoft-ds filtered
202.201.39.51 514 tcp shell filtered
202.201.39.51 3306 tcp mysql open MySQL unauthorized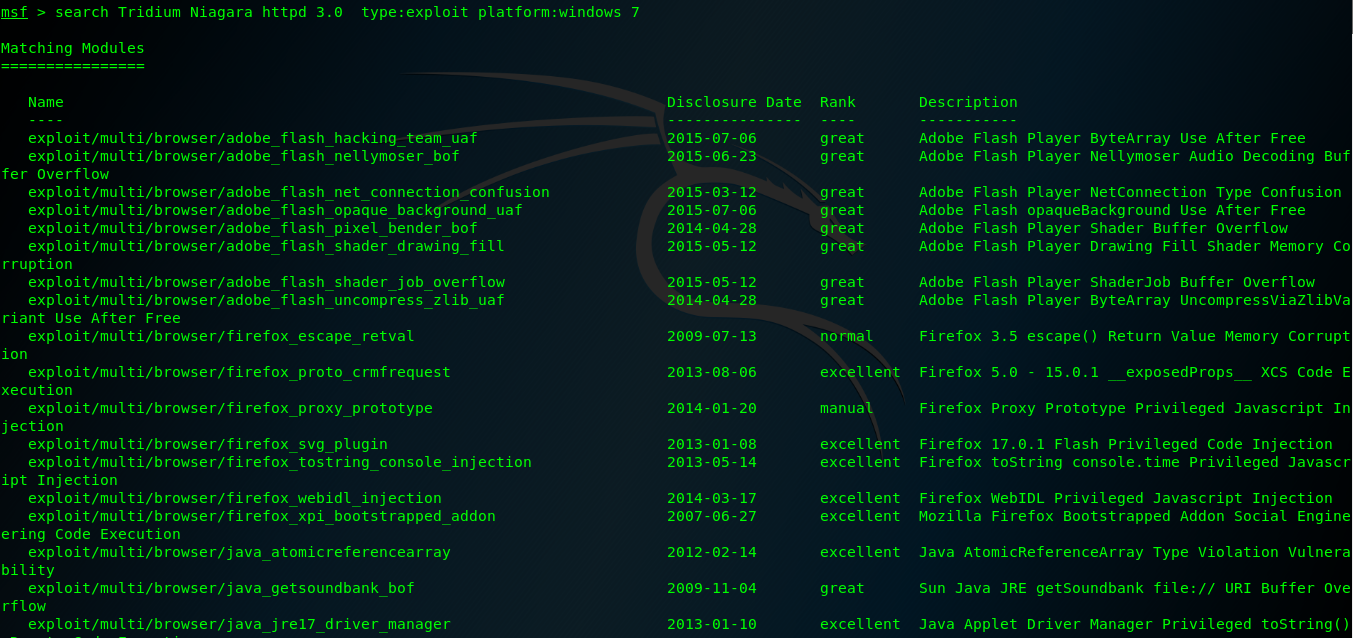
Metasploit (二)的更多相关文章
- Metasploit是一款开源的安全漏洞检测工具,
Metasploit是一款开源的安全漏洞检测工具,可以帮助安全和IT专业人士识别安全性问题,验证漏洞的缓解措施,并管理专家驱动的安全性进行评估,适合于需要核实漏洞的安全专家,同时也适合于强大进攻能力的 ...
- HW弹药库之红队作战手册
红方人员实战手册 声明 Author : By klion Date : 2020.2.15 寄语 : 愿 2020 后面的每一天都能一切安好 分享初衷 一来, 旨在为 "攻击" ...
- ApacheCN Kali Linux 译文集 20211020 更新
Kali Linux 秘籍 中文版 第一章 安装和启动Kali 第二章 定制 Kali Linux 第三章 高级测试环境 第四章 信息收集 第五章 漏洞评估 第六章 漏洞利用 第七章 权限提升 第八章 ...
- 羽翼metasploit第一,二季学习笔记
-----------------第一季-------------------- 启动Metasploit:msfconsole 升级和更新:./msfupdate 直接退出:exit 退回上一级:q ...
- 使用Metasploit渗透攻击windows系统(二)
后渗透攻击: 介绍常用的一些命令: 查看进程:ps 查看当前进程号:getpid 查看系统信息:sysinfo 查看目标机是否为虚拟机:run post/windows/gather/checkvm ...
- metasploit framework(十二):sql server扫描
mssql_ping模块,如果1433端口开放的话,直接连接这个1433端口,如果没开放,就通过UDP的1434去查询TCP的sql server端口 run,就扫描出来了数据库的tcp端口 得到tc ...
- metasploit framework(二):记一次入侵
msfconsole use 其中一个 exploit前台执行注入 后台执行shell 加-j 通过sessions查看后台执行的shell,可以看到这个会话的id号为2 进入会话,sessions ...
- chapter1 渗透测试与metasploit
网络对抗技术课程学习 chapter1 渗透测试与metasploit 一.读书笔记 二.渗透测试 通过模拟恶意攻击者的技术与方法进行攻击,挫败目标系统安全控制措施,取得访问控制权,并发现具备业务影响 ...
- Kali Linux Web 渗透测试— 第十二课-websploit
Kali Linux Web 渗透测试— 第十二课-websploit 文/玄魂 目录 Kali Linux Web 渗透测试— 第十二课-websploit..................... ...
随机推荐
- HashMap的源码,实现原理,底层结构
转载一遍不错的文章,让你深入了解HashMap http://www.cnblogs.com/ITtangtang/p/3948406.html
- Delphi线程定时器TThreadedTimer及用法--还有TThreadList用法可以locklist
Delphi线程定时器 - -人生如歌- - 博客园http://www.cnblogs.com/zhengwei0113/p/4192010.html (* 自己编写的线程计时器,没有采用消息机制, ...
- Linux下安装PCRE
原文链接:https://www.linuxidc.com/Linux/2015-03/114986.htm PCRE(Perl Compatible Regular Expressions)是一个轻 ...
- Nginx系列1:ubuntu16.04编译出适合自己的nginx服务器
1.下载nginx nginx官网:nginx.org tar.gz文件 解压缩命令: wget https://nginx.org/download/nginx-1.14.2.tar.gz #下载n ...
- openstack Q版部署-----网络服务(neutron)安装部署(7)
一.数据库配置(控制节点) 控制节点创建数据库: CREATE DATABASE neutron; GRANT ALL PRIVILEGES ON neutron.* TO 'neutron'@'lo ...
- quartz定时任务的简单使用
开发环境: springmvc quartz-2.2.3在官网下载的. 步骤: 1.首先在web.xml中加入以下代码: <servlet> <servlet-name>Qua ...
- 二、Java神经网络框架Neuroph的使用和架构分析
一.使用Neuroph Studio构造感知机处理逻辑与 新建项目 接着,输入名字和地址,点击“完成” 在工程的神经网络文件下新建神经网络 准备训练数据 开始训练 误差展示 也可以测试神经元 或者输入 ...
- [Harbor]Docker登录Harbor仓库(HTTP方式)
Docker登录到Harbor仓库时,不管是使用http协议还是使用https协议,都需要修改一些配置. 这篇文章来介绍一下,在使用http协议时,需要进行什么哪些配置. 首先,确定自己的Harbor ...
- 【OpenGL】【计算机图形学原理】撸课本系列一
P13 简单二维图元的生成方法 #include <GL/glut.h> //用于表示openGL允许采用 glClear(GL_COLOR_BUFFER_BIT); //清除颜色缓存 g ...
- 组合权限查询 SQL,UniGUI
组合权限查询 SQL,UniGUI: name ,View, New, Edit, Dele 表 获取 name 的 授权. 项目 1 0 0 ...
