(十三)Kubernetes Dashboard
Dashboard概述
Dashboard是Kubernetes的Web GUI,可用于在Kubernetes集群上部署容器化应用、应用排障、管理集群本身及附加的资源等。常用于集群及应用速览、创建或修改单个资源(如Deployment、Jobs和DaemonSet等),以及扩展Deployment、启动滚动更新、重启Pod或使用部署向导部署一个应用等。
Dashboard的认证和授权均可由Kubernetes集群实现,它自身仅是一个代理,所有的相关操作都将发给API Server进行,而非由Dashboard自行完成。目前仅支持使用的认证方式有令牌(token)认证和kubeconfig两种,在访问之前都需要准备好相应的认证凭证。
Dashboard部署
由于用到镜像
k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1,是国外的,我们拉取不下来,这里可以使用下面两种方式。# docker pull mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1
或者是
# docker pull blwy/kubernetes-dashboard-amd64:v1.10.1
1)这里将资源清单文件下载本地,编辑使用的镜像
[root@k8s-master ~]# wget https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
2)将镜像地址进行更改
[root@k8s-master ~]# vim kubernetes-dashboard.yaml
......
spec:
containers:
- name: kubernetes-dashboard
image: blwy/kubernetes-dashboard-amd64:v1.10.1 #将镜像地址改为可以下载的地址
ports:
......
3)部署
[root@k8s-master ~]# kubectl apply -f kubernetes-dashboard.yaml
secret/kubernetes-dashboard-certs created
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created [root@k8s-master ~]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
coredns-bccdc95cf-9gsn8 1/1 Running 0 10d
coredns-bccdc95cf-x7m8g 1/1 Running 0 10d
etcd-k8s-master 1/1 Running 0 10d
kube-apiserver-k8s-master 1/1 Running 0 10d
kube-controller-manager-k8s-master 1/1 Running 0 10d
kube-flannel-ds-amd64-gg55s 1/1 Running 0 10d
kube-flannel-ds-amd64-ssr7j 1/1 Running 5 10d
kube-flannel-ds-amd64-w6f9h 1/1 Running 4 10d
kube-proxy-77pbc 1/1 Running 3 10d
kube-proxy-qs655 1/1 Running 3 10d
kube-proxy-xffq4 1/1 Running 0 10d
kube-scheduler-k8s-master 1/1 Running 0 10d
kubernetes-dashboard-d977fcf6-d25xz 1/1 Running 0 4s
4)查看svc,并将类型改为NodePort
[root@k8s-master ~]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 9d
kubernetes-dashboard ClusterIP 10.99.151.238 <none> 443/TCP 7m25s #可以像下面直接打补丁进行更改。
[root@k8s-master ~]# kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kube-system
service/kubernetes-dashboard patched
[root@k8s-master ~]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 9d
kubernetes-dashboard NodePort 10.99.151.238 <none> 443:32058/TCP 8m45s #或者也可以修改资源清单修改类型为NodePort
[root@k8s-master ~]# vim kubernetes-dashboard.yaml
......
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
type: NodePort #这里添加类型为NodePort
浏览器访问:https://192.168.1.31:32058 如下图;建议使用火狐浏览器,并在高级选项中添加信任,谷歌会禁止不安全证书访问。
token认证
集群级别的管理操作依赖于集群管理员权限,例如,内建的
cluster-admin集群角色拥有全部权限,创建ServiceAccount并将其绑定其上即完成集群管理员授权。而用户通过相应的ServiceAccount的token信息完成Dashboard认证也就能扮演起Dashboard接口上的集群管理员角色。例如,下面创建一个名为dashboard-admin的ServiceAccount,并完成集群角色绑定:
1)创建serviceaccount资源
[root@k8s-master ~]# kubectl create serviceaccount dashboard-admin -n kube-system
serviceaccount/dashboard-admin created
[root@k8s-master ~]# kubectl get sa/dashboard-admin -n kube-system
NAME SECRETS AGE
dashboard-admin 1 15s
2)创建clusterrolebinding,将角色cluster-admin与serviceaccount资源(dashboard-admin)进行绑定
[root@k8s-master ~]# kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
clusterrolebinding.rbac.authorization.k8s.io/dashboard-admin created [root@k8s-master ~]# kubectl describe clusterrolebinding/dashboard-admin #查看绑定信息
Name: dashboard-admin
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: cluster-admin
Subjects:
Kind Name Namespace
---- ---- ---------
ServiceAccount dashboard-admin kube-system
3)查看token值并进行登录验证
[root@k8s-master ~]# ADMIN_SECRET=$(kubectl -n kube-system get secret |awk '/^dashboard-admin/{print $1}') #获取上面创建的dashboard-admin生成的secret的名字
[root@k8s-master ~]# kubectl describe secrets $ADMIN_SECRET -n kube-system |grep ^token #获取上面获取到的secret的token值
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tbmZ2NGgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiOTY5MDhiMTgtYzUyYy00NWEwLWIxODEtMTM2OGM4ZGZkMGUwIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.xVHNDKiU7n8fvfN8_5RF3Z6Ppxl-ULk-zYfWywPktJ6mVgtgm4tnAX9_n8zpzHhff1tD4y04Ra7OKvnJTypkI78ELHqggrQxNLggfpbdrWnIif2qIqEbIv5Hay3s4UeOqU2p6Kex4v7UUVtdo781W4rNi7DP2yXKfV5YSTeu6ZMTQiMa3H-O6y-y4sH_ISi_UwiAtHALTJ_OX-j9BzsFIUBhryKnGbOK4ygVmlTA2tWFe8TDUI6xCTjEKSRId3iL_TpKg-uXc652JHnQPYH2ZErojWCbwGR6IqeRTH4kMlAfjvDIeDdT6sSNyjJONpgJQpdYtaGzQiHgE2CW2_q4zQ
输入上获取到的token进行登录。
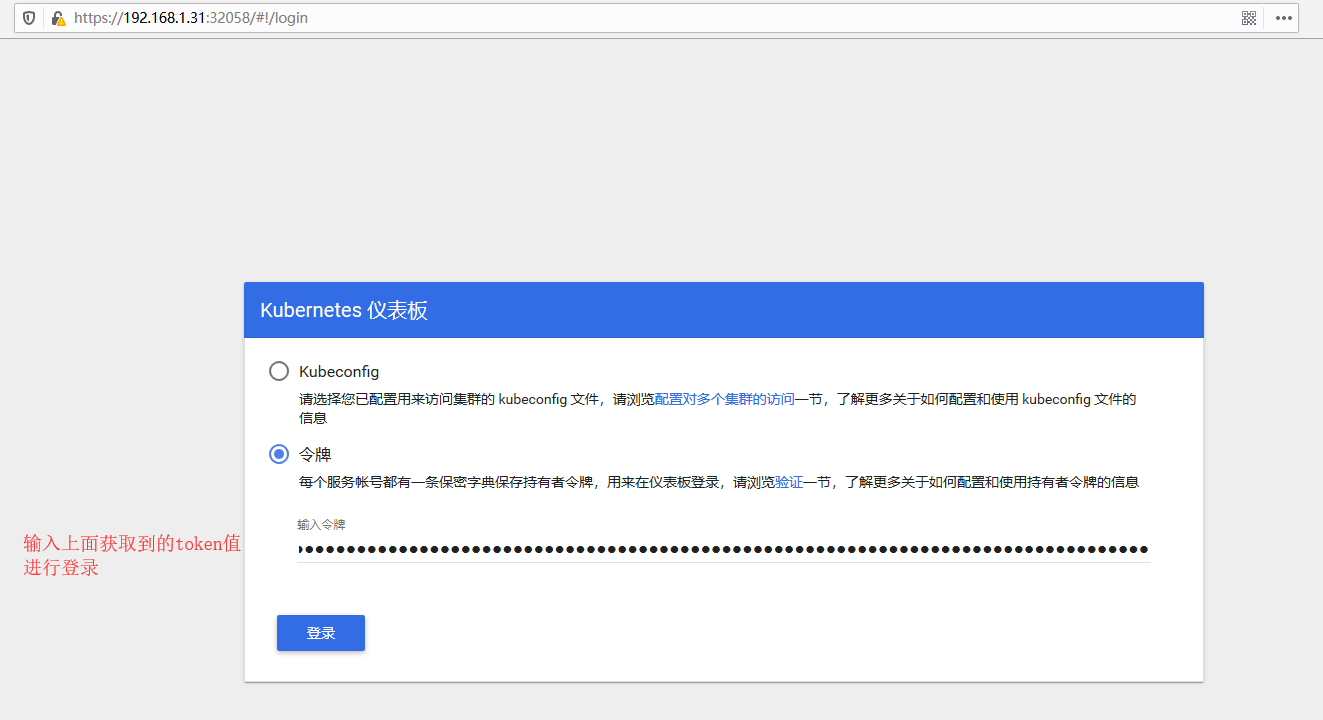
Kubeconfig认证
kubeconfig是认证信息承载工具,能够持久存入秘钥和证书,或者认证令牌等作为用户的认证配置文件。为了说明如何配置一个仅具有特定名称空间管理权限的登录账号,这里创建一个新的ServiceAccount用于管理默认的default名称空间,并将之绑定于admin集群角色。
1)创建serviceaccount资源
[root@k8s-master ~]# kubectl create serviceaccount def-ns-admin -n default #创建sa资源def-ns-admin
serviceaccount/def-ns-admin created [root@k8s-master ~]# kubectl get sa/def-ns-admin -n default #查看上面创建的sa资源
NAME SECRETS AGE
def-ns-admin 1 19s
2)创建rolebinding,将上面创建的serviceaccount与clusterrole(admin)进行绑定
[root@k8s-master ~]# kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-admin
rolebinding.rbac.authorization.k8s.io/def-ns-admin created [root@k8s-master ~]# kubectl get secret |grep def-ns #查看生成的secret
def-ns-admin-token-m2ct6 kubernetes.io/service-account-token 3 106s [root@k8s-master ~]# kubectl describe secret/def-ns-admin-token-m2ct6 #查看secret资源详细信息
Name: def-ns-admin-token-m2ct6
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: def-ns-admin
kubernetes.io/service-account.uid: f824dbcd-d661-4776-993a-921042f7e196 Type: kubernetes.io/service-account-token Data
====
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1tMmN0NiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJmODI0ZGJjZC1kNjYxLTQ3NzYtOTkzYS05MjEwNDJmN2UxOTYiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.U72TWqg3pd-zJgd0QsoYysbNm4rf8rPtEvNBDoVRpRnuX_NkJPtSniAdEIw-g_RjZXNhWHjOXOUmlQ1HwXu0FO3d_j0g6S3dX5BlEA4uPeNskgTH83T7g2BoI3XazAzLKtfGPUuOPk9F2IQQvp3m93x-D1BETOp4ga-R4CMQdVZBUl4XWqFpDxJ47pCsK_VrvP3g7LJpzJk9dnwr2i4-3ysLFwZ84x07Kbcw-1ED8jMh8LNpUGPnevpKntqwo9ghCDVN-oPdPGcXlvxrc9enDu_7gIb2H_fJbMWS_vH1pQX8SoYDhneW2gkVKg2RaW1QaF4TrcdUAabcCcfoqdiCxg
ca.crt: 1025 bytes
3)初始化集群信息,提供API Server的URL,以及验证API Server证书所用到的CA证书等
[root@k8s-master ~]# kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/pki/ca.crt --server="https://192.168.1.31:6443" --embed-certs=true --kubeconfig=/root/def-ns-admin.conf
Cluster "kubernetes" set. [root@k8s-master ~]# kubectl config view --kubeconfig=/root/def-ns-admin.conf #查看生成的配置文件信息
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.1.31:6443
name: kubernetes
contexts: []
current-context: ""
kind: Config
preferences: {}
users: []
4)获取def-ns-admin的token,并将其作为认证信息。由于直接得到的token是base64编码格式,故采用“base -d”命令将其解码
[root@k8s-master ~]# kubectl get secret -n default
NAME TYPE DATA AGE
admin-token-lc826 kubernetes.io/service-account-token 3 16d
def-ns-admin-token-m2ct6 kubernetes.io/service-account-token 3 12m [root@k8s-master ~]# kubectl -n default get secret/def-ns-admin-token-m2ct6 -o jsonpath={.data.token} |base64 -d #获取token并将其解码
eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1tMmN0NiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJmODI0ZGJjZC1kNjYxLTQ3NzYtOTkzYS05MjEwNDJmN2UxOTYiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.U72TWqg3pd-zJgd0QsoYysbNm4rf8rPtEvNBDoVRpRnuX_NkJPtSniAdEIw-g_RjZXNhWHjOXOUmlQ1HwXu0FO3d_j0g6S3dX5BlEA4uPeNskgTH83T7g2BoI3XazAzLKtfGPUuOPk9F2IQQvp3m93x-D1BETOp4ga-R4CMQdVZBUl4XWqFpDxJ47pCsK_VrvP3g7LJpzJk9dnwr2i4-3ysLFwZ84x07Kbcw-1ED8jMh8LNpUGPnevpKntqwo9ghCDVN-oPdPGcXlvxrc9enDu_7gIb2H_fJbMWS_vH1pQX8SoYDhneW2gkVKg2RaW1QaF4TrcdUAabcCcfoqdiCxg [root@k8s-master ~]# DEFNS_ADMIN_TOKEN=$(kubectl -n default get secret/def-ns-admin-token-m2ct6 -o jsonpath={.data.token} |base64 -d) #这里将上面得到的token保存为一个变量,方便调用 [root@k8s-master ~]# kubectl config set-credentials def-ns-admin --token=$DEFNS_ADMIN_TOKEN --kubeconfig=/root/def-ns-admin.conf
User "def-ns-admin" set.
5)设置cotext列表,定义一个名为def-ns-admin的context
[root@k8s-master ~]# kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.conf
Context "def-ns-admin@kubernetes" created.
6)最后指定要使用的context为前面定义的名为def-ns-admin的context
[root@k8s-master ~]# kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/def-ns-admin.conf [root@k8s-master ~]# kubectl config view --kubeconfig=/root/def-ns-admin.conf #查看最终生成的配置文件信息
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.1.31:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: def-ns-admin
name: def-ns-admin@kubernetes
current-context: def-ns-admin@kubernetes
kind: Config
preferences: {}
users:
- name: def-ns-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1tMmN0NiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJmODI0ZGJjZC1kNjYxLTQ3NzYtOTkzYS05MjEwNDJmN2UxOTYiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.U72TWqg3pd-zJgd0QsoYysbNm4rf8rPtEvNBDoVRpRnuX_NkJPtSniAdEIw-g_RjZXNhWHjOXOUmlQ1HwXu0FO3d_j0g6S3dX5BlEA4uPeNskgTH83T7g2BoI3XazAzLKtfGPUuOPk9F2IQQvp3m93x-D1BETOp4ga-R4CMQdVZBUl4XWqFpDxJ47pCsK_VrvP3g7LJpzJk9dnwr2i4-3ysLFwZ84x07Kbcw-1ED8jMh8LNpUGPnevpKntqwo9ghCDVN-oPdPGcXlvxrc9enDu_7gIb2H_fJbMWS_vH1pQX8SoYDhneW2gkVKg2RaW1QaF4TrcdUAabcCcfoqdiCxg
7)将这个配置文件保存client上,通过加装该配置文件进行登录
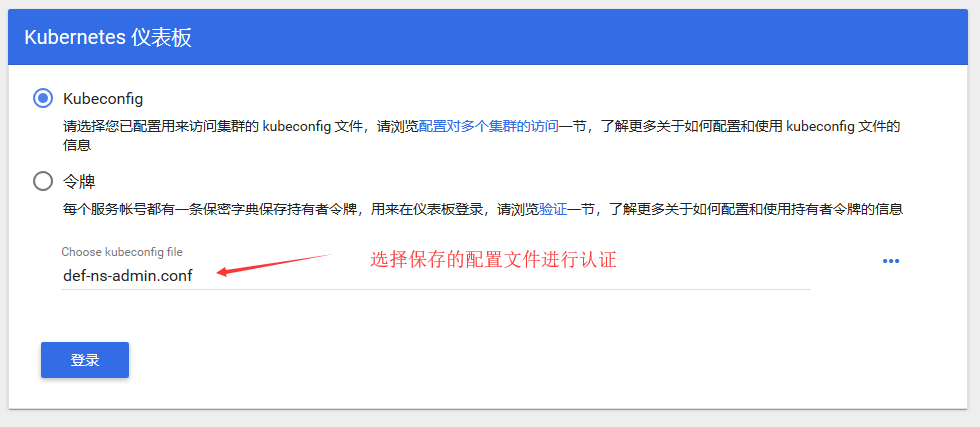
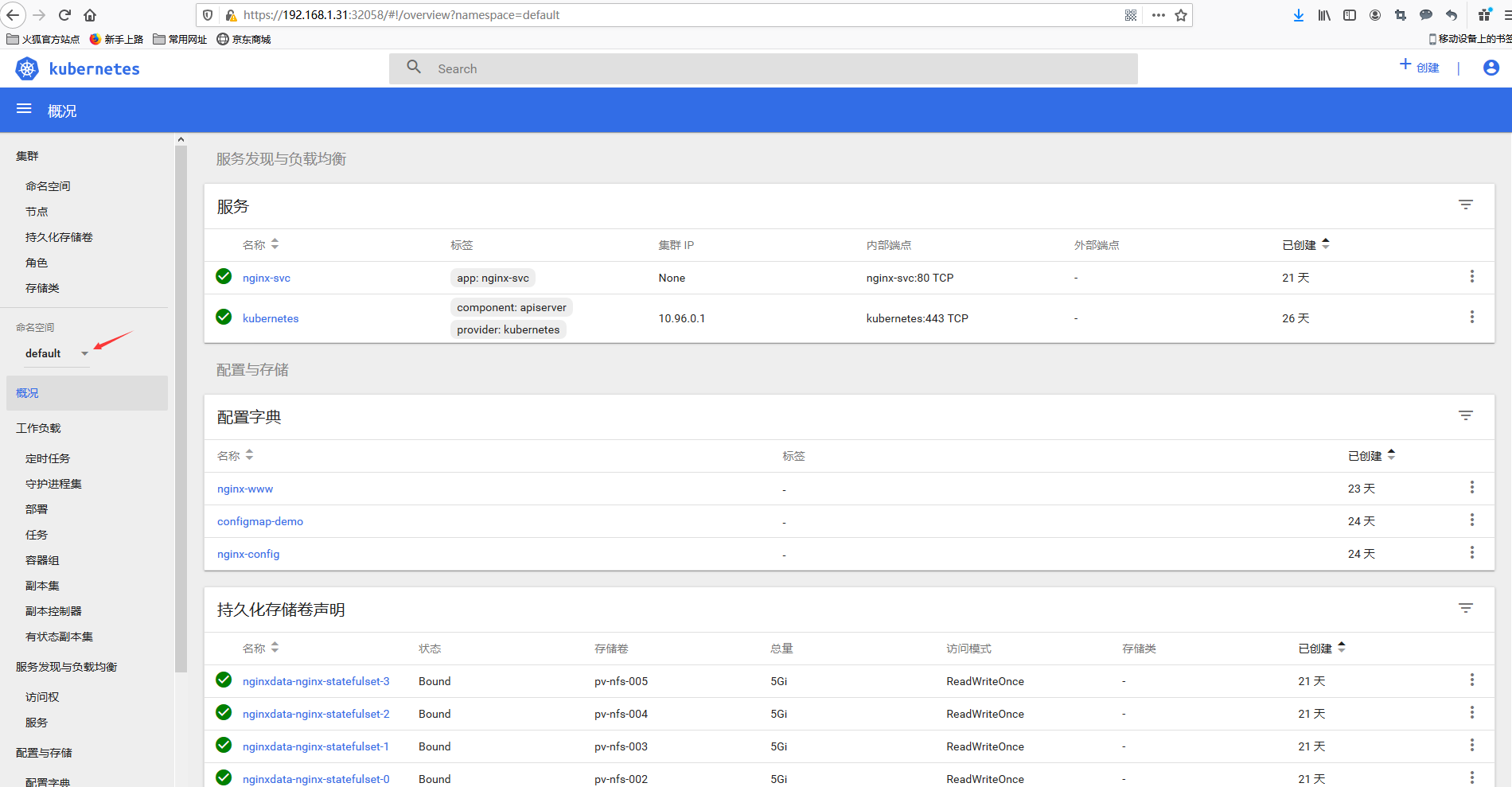
这里通过测试可以发现,这里的def-ns-admin用户登录进来只能看到default名称空间的内容。也只能对default名称空间的资源进行管理。
(十三)Kubernetes Dashboard的更多相关文章
- Kubernetes Dashboard - 每天5分钟玩转 Docker 容器技术(173)
前面章节 Kubernetes 所有的操作我们都是通过命令行工具 kubectl 完成的.为了提供更丰富的用户体验,Kubernetes 还开发了一个基于 Web 的 Dashboard,用户可以用 ...
- Kubernetes dashboard安装
1. To download Dashboard plugin deployment YAML file from internet. #cd /home #mkdir k8s #cd k8s # w ...
- centos7下kubernetes(5。部署kubernetes dashboard)
基于WEB的dashboard,用户可以用kubernetes dashboard部署容器话的应用,监控应用的状态,执行故障排查任务以及管理kubernetes各种资源. 在kubernetes da ...
- kubernetes学习笔记之十一:kubernetes dashboard认证及分级授权
第一章.部署dashboard 作为Kubernetes的Web用户界面,用户可以通过Dashboard在Kubernetes集群中部署容器化的应用,对应用进行问题处理和管理,并对集群本身进行管理.通 ...
- Mac搭建kubernetes dashboard全流程
1. 下载dashboard文件: curl -o kubernetes-dashboard.yaml https://raw.githubusercontent.com/kubernetes/das ...
- kubernetes Dashboard 使用RBAC 权限认证控制
kubernetes RBAC实战 环境准备 先用kubeadm安装好kubernetes集群,[包地址在此](https://market.aliyun.com/products/56014009/ ...
- docker for mac 安装 kubernetes、kubernetes dashboard
安装参考地址(按照此文档,安装成功):https://yq.aliyun.com/articles/508460 官方说明:https://kubernetes.io/docs/tasks/acces ...
- Kubernetes学习之路(十九)之Kubernetes dashboard认证访问
Dashboard:https://github.com/kubernetes/dashboard 一.Dashboard部署 由于需要用到k8s.gcr.io/kubernetes-dashboar ...
- Kubernetes dashboard 配置
安装前准备 下载dashboard的yaml文件 wget -O kube-dashboard.yaml https://git.io/kube-dashboard-no-rbac 这个版本是没有权限 ...
随机推荐
- K8s容器资源限制
在K8s中定义Pod中运行容器有两个维度的限制: 1. 资源需求:即运行Pod的节点必须满足运行Pod的最基本需求才能运行Pod. 如: Pod运行至少需要2G内存,1核CPU 2. 资源限额: ...
- [cf113d]Museum
传送门 Solution 设一个状态为 \((x,y)\) 表示两人在的位置,求出每个状态期望出现的次数 设一个状态为 \(u\) , \(x_u^0=[u==(a,b)]\) 所以一个状态出现的次数 ...
- 某邀请赛misc key家用完整版
目录 题目下载 提示 解题过程 1.提取RGB值 2.找到key 3.循环异或,得到flag 反思 题目下载 题目名:key 提示 提取钥匙中特殊颜色的RGB循环异或KEY值 解题过程 1.提取RGB ...
- 3 Linux性能优化之 CPU上下文
- gcd 题解
gcd Little White learned the greatest common divisor, so she plan to solve a problem: given \(x, n,\ ...
- JVM常用命令和性能调优建议 [Could not create the Java virtual machine]
一.查看jvm常用命令jinfo:可以输出并修改运行时的java 进程的opts. jps:与unix上的ps类似,用来显示本地的java进程,可以查看本地运行着几个java程序,并显示他们的进程号. ...
- [转帖]Druid介绍及入门
Druid介绍及入门 2018-09-19 19:38:36 拿着核武器的程序员 阅读数 22552更多 分类专栏: Druid 版权声明:本文为博主原创文章,遵循CC 4.0 BY-SA版权协议 ...
- Sitecore安全:访问权限
由于Sitecore使用Core数据库中的项来定义其用户界面,因此您可以对该数据库中的项应用访问权限,以控制对CMS功能的访问.最常见的是,将用户置于预定义的Sitecore客户端角色中 Siteco ...
- 螺旋折线-C++
标题:螺旋折线 如图p1.png所示的螺旋折线经过平面上所有整点恰好一次. 对于整点(X, Y),我们定义它到原点的距离dis(X, Y)是从原点到(X, Y)的螺旋折线段的长度. 例如dis(0, ...
- NOIP2018 填数游戏 搜索、DP
LOJ 感觉这个题十分好玩于是诈尸更博.一年之前的做题心得只有这道题还记得清楚-- 设输入为\(n,m\)时的答案为\(f(n,m)\),首先\(f(n,m)=f(m,n)\)所以接下来默认\(n \ ...
