POJ1459Power Network(dinic模板)
| Time Limit: 2000MS | Memory Limit: 32768K | |
| Total Submissions: 25832 | Accepted: 13481 |
Description
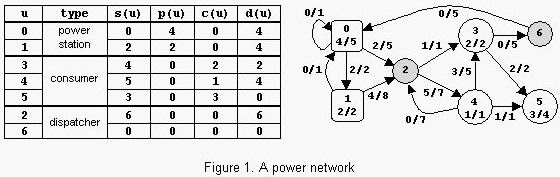
An example is in figure 1. The label x/y of power station u shows that p(u)=x and pmax(u)=y. The label x/y of consumer u shows that c(u)=x and cmax(u)=y. The label x/y of power transport line (u,v) shows that l(u,v)=x and lmax(u,v)=y. The power consumed is Con=6. Notice that there are other possible states of the network but the value of Con cannot exceed 6.
Input
Output
Sample Input
2 1 1 2 (0,1)20 (1,0)10 (0)15 (1)20
7 2 3 13 (0,0)1 (0,1)2 (0,2)5 (1,0)1 (1,2)8 (2,3)1 (2,4)7
(3,5)2 (3,6)5 (4,2)7 (4,3)5 (4,5)1 (6,0)5
(0)5 (1)2 (3)2 (4)1 (5)4
Sample Output
15
6
Hint
#include <iostream>
#include <cstring>
#include <algorithm>
#include <cstdio>
#include <stdio.h>
#include <queue>
#include <vector>
using namespace std;
const int MAX = ;
const int INF = 0x3f3f3f3f;
struct Edge
{
int to,cap;
Edge(int v,int w):to(v),cap(w) {}
};
int n,m,np,nc,s,t;
vector<int> g[MAX];
vector<Edge> edge;
int d[MAX],cur[MAX];
void AddEdge(int from,int to,int cap)
{
edge.push_back(Edge(to,cap));
edge.push_back(Edge(from,));
int id = edge.size();
g[from].push_back(id - );
g[to].push_back(id - ); }
bool bfs()
{
memset(d,,sizeof(d));
queue<int> q;
q.push(s);
d[s] = ;
while(!q.empty())
{
int x = q.front();
q.pop();
if(x == t)
return true;
int len = g[x].size();
for(int i = ; i < len; i++)
{
Edge e = edge[ g[x][i] ];
if(d[e.to] == && e.cap > )
{
d[e.to] = d[x] + ;
q.push(e.to);
}
}
}
return false;
}
int dfs(int x, int a)
{
if(x == t || a == )
return a;
int flow = ,f;
for(int& i = cur[x]; i < (int) g[x].size(); i++)
{
Edge& e = edge[ g[x][i] ]; //这里要是引用
if(d[x] + == d[e.to] && (f = dfs(e.to,min(a,e.cap))) > )
{
e.cap -= f;
edge[ g[x][i] ^ ].cap += f;
flow += f;
a -= f;
if(a == )
{
break;
}
}
}
return flow;
}
int MaxFlow()
{
int flow = ;
while(bfs())
{
memset(cur,,sizeof(cur));
flow += dfs(s,INF);
}
return flow;
}
int main()
{
char str[];
int u,v,w;
while(scanf("%d%d%d%d",&n,&np,&nc,&m) != EOF)
{
s = n + ;
t = n + ;
for(int i = ; i < n + ; i++)
g[i].clear();
edge.clear();
for(int i = ; i <= m; i++)
{
scanf("%s",str);
sscanf(str,"%*c%d%*c%d%*c%d",&u,&v,&w);
AddEdge(u,v,w);
}
for(int i = ; i < np; i++)
{
scanf("%s",str);
sscanf(str,"%*c%d%*c%d",&u,&w);
AddEdge(s,u,w);
}
for(int i = ; i < nc; i++)
{
scanf("%s",str);
sscanf(str,"%*c%d%*c%d",&u,&w);
AddEdge(u,t,w);
}
printf("%d\n",MaxFlow());
} return ;
}
POJ1459Power Network(dinic模板)的更多相关文章
- POJ 1273 Drainage Ditches (网络流Dinic模板)
Description Every time it rains on Farmer John's fields, a pond forms over Bessie's favorite clover ...
- hdu 1532 Dinic模板(小白书)
hdu1532 输入n,m. n条边,m个点,之后给出a到b的容量,求1到m的最大流. 注意:Dinic只能调用一次,因为原理是改变cap的值,如果调用多次一样的,那么第一次会对,其余的都会是0,因为 ...
- 最大流算法 ISAP 模板 和 Dinic模板
ISAP // UVa11248 Frequency Hopping:使用ISAP算法,加优化 // Rujia Liu struct Edge { int from, to, cap, flow; ...
- 洛谷P3376【模板】网络最大流 Dinic模板
之前的Dinic模板照着刘汝佳写的vector然后十分鬼畜跑得奇慢无比,虽然别人这样写也没慢多少但是自己的就是令人捉急. 改成邻接表之后快了三倍,虽然还是比较慢但是自己比较满意了.虽然一开始ecnt从 ...
- Power Network POJ - 1459 网络流 DInic 模板
#include<cstring> #include<cstdio> #define FOR(i,f_start,f_end) for(int i=f_startl;i< ...
- HDU1532_Drainage Ditches(网络流/EK模板/Dinic模板(邻接矩阵/前向星))
Drainage Ditches Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 65536/32768 K (Java/Others) ...
- 【网络流#3】hdu 1532 - Dinic模板题
输入为m,n表示m条边,n个结点 记下来m行,每行三个数,x,y,c表示x到y的边流量最大为c 这道题的模板来自于网络 http://blog.csdn.net/sprintfwater/articl ...
- 最大流当前弧优化Dinic模板
最大流模板: 普通最大流 无向图限制:将无向图的边拆成2条方向相反的边 无源汇点有最小流限制的最大流:理解为水管流量形成循环,每根水管有流量限制,并且流入量等于流出量 有源汇点的最小流限制的最大流 顶 ...
- 网络流--最大流dinic模板
标准的大白书式模板,除了变量名并不一样……在主函数中只需要用到 init 函数.add 函数以及 mf 函数 #include<stdio.h> //差不多要加这么些头文件 #includ ...
随机推荐
- JS 浮点数运算丢失精度解决方案
除法 function accDiv(arg1,arg2){ var t1=0,t2=0,r1,r2; try{t1=arg1.toString().split(".")[1].l ...
- Linq中查询List组合相同值数量大于1
List< select g.Key).ToList();
- 【WPF】无边框窗体
之前写了一个支持尺寸变换的无边框窗体的一个基窗体,代码如下: public class LBaseWindow : Window { /// <summary> /// 基窗体 /// & ...
- web页面的回流,认识与避免
一.什么是回流? 回流是会导致页面重新渲染的一些元素,从而影响性能. 二.哪些因素会导致回流? 1.调整窗口的大小: 2.改变字体,如果用rem 设置了根目录的字体大小,这样就减少了回流的次数: 3 ...
- HashMap 中的 entrySet()使用方法 2016.12.28
package map; import java.util.HashMap; import java.util.Iterator; import java.util.Map.Entry; import ...
- C#不同窗体间通信,数据传递
在一个项目中,很多时候都需要在窗体间进行数据传递和通信,最觉见的是父子窗体之间的数据传递,比如登录ID,各个窗体都需要知道.有很多文章都写了这方面的问题,提出很多优秀的方法,鄙人不才,搜了一些资料之后 ...
- Jenkins进阶系列之——02email-ext邮件通知模板
发现一个很好的邮件通知模板,根据我的需求定制了一些.分享一下. Default Subject: 构建通知:${BUILD_STATUS} - ${PROJECT_NAME} - Build # ${ ...
- Unity发送参数给iOSNative并响应
unity想要给iOS客户端发送通知并相应.语言太苍白直接上代码. unity端创建两个C#文件 1.触发cs这个不用多说,大家估计都懂. using UnityEngine; using Syste ...
- 一头扎进EasyUI3
惯例广告一发,对于初学真,真的很有用www.java1234.com,去试试吧! 一头扎进EasyUI第11讲 .基本下拉组件 <select id="cc" style=& ...
- PHP中的日期加减方法示例
几乎所有从事程序开发的程序员都遇到时间处理问题,PHP开发也一样,幸运的是PHP提供了很多关于日期时间函数.只要经常使用这些函数,搭配使用,日期时间处理上就熟能生巧了. 今天要讲的这个例子,需求是这样 ...
