Subnet Routing Examples
Routing Table
- Each row in routing table contains:
- Destination IP address
- IP address of next-hop router
- Physical address
- Statistics information
- Flags
- H=1 (0) indicates route is to a host (network)
- G=1 (0) indicates route is to a router (directly connected destination)
Routing Search and Actions
- Routing table search order & action
- Complete destination address; send as per next-hop & G flag
- Destination network ID; send as per next-hop & G flag
- Default router entry; send as per next-hop
- Declare packet undeliverable; send ICMP “host unreachable error” packet to originating host
Example 1: A packet with 150.100.15.11 arrives at R1
- Host5 want to send a packet to Rout1, it firstly searches 150.100.0.1 in the routing table, but not match.
- So it send the packet to R2 as the default IP address.
Example 1: Subnetting Scheme
- H and R find next hop in this way.
- IP address 150.100.15.11 in binary string is
10010110 01100100 00001111 00001011 - Apply subnet mask to IP addresses to find corresponding subnet
- IP address = 10010110 01100100 00001111 00001011
- Mask = 11111111 11111111 11111111 10000000
- AND = 10110110 01100100 00001111 00000000
- Subnet = 150.100.15.0
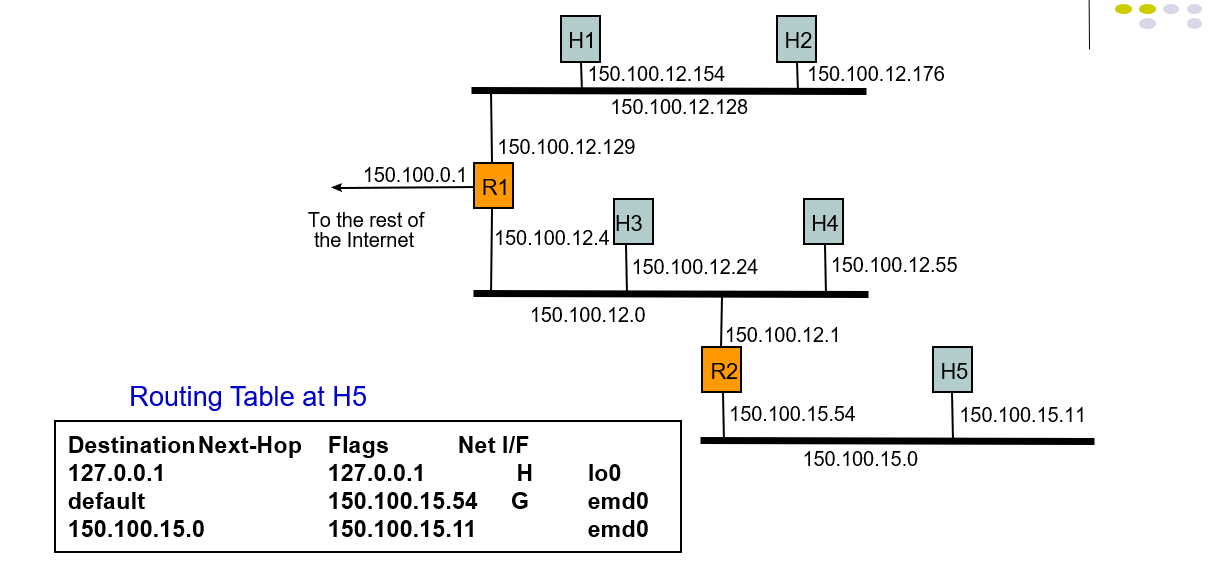
Example 2: Host H5 sends packet to host H2
- The routing table contains:destination next-hop,flags,default next-hop,physical interface.
- H5 searches the routing table but doesn't find destination next-hop, so it send the packet as the default next-hop.
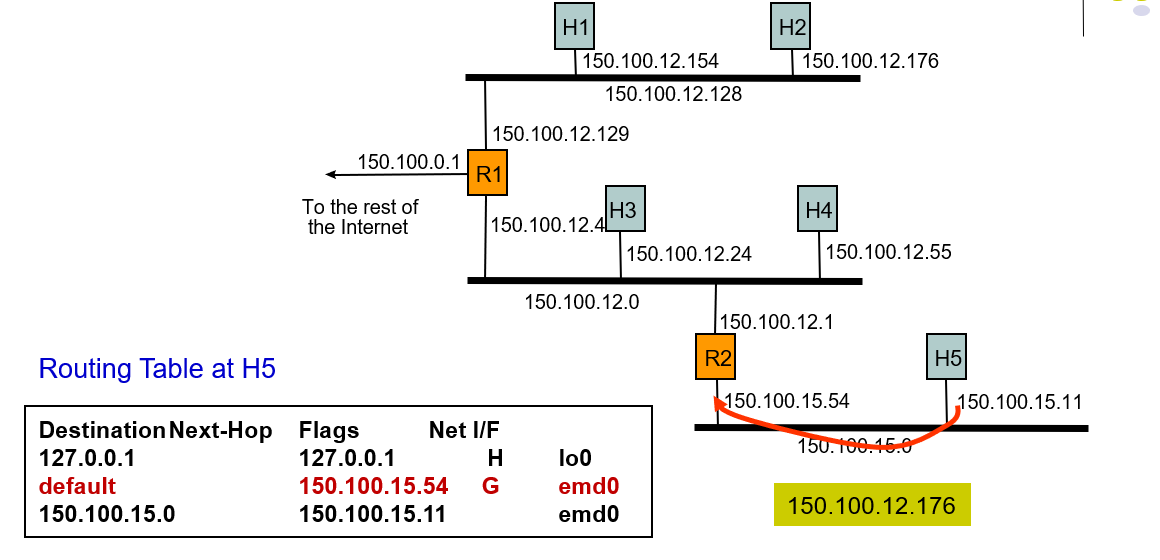
Example 2: Host H5 sends packet to host H2
- 127.0.0.1 is the native address.
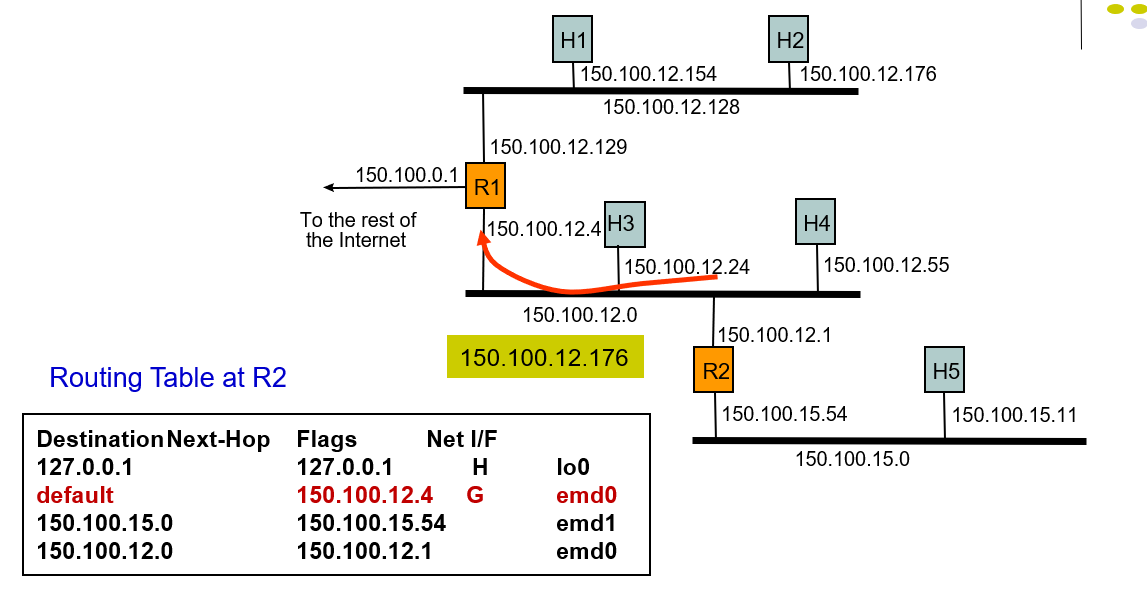
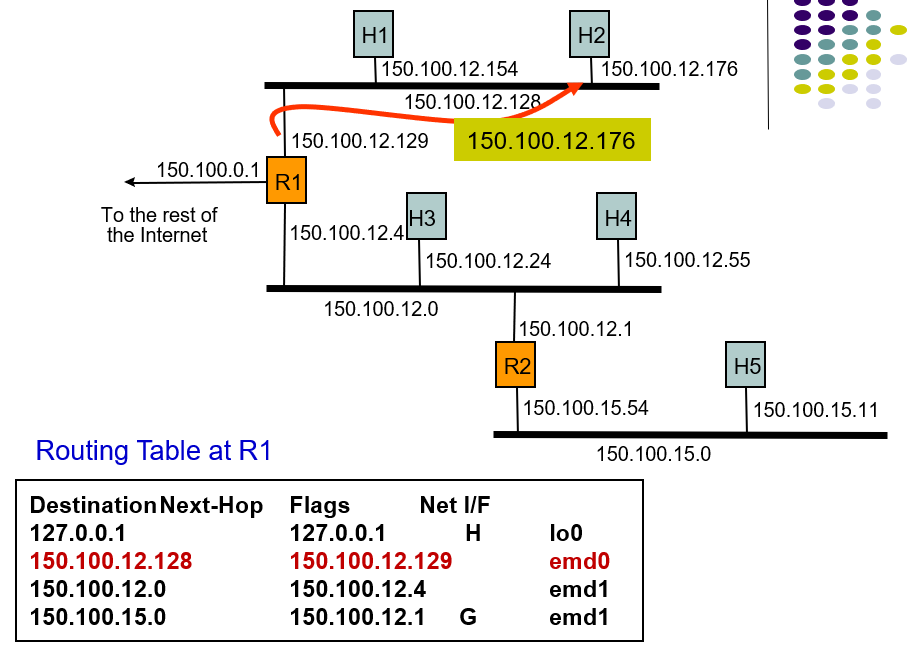
Example: Host H5 sends packet to host H2
- It sned a packet so the network interface which delivers a packet to the local are network by broadcasting and host H2 receive the packet.
Discuss
- Discuss the difficulties with using actual time in the Time-to-Live field
- TTL restricts the max hops in the network, even if it was called "Time to live", but it is hops instead of time. The distance is different in all kinds of network, and the delay time in every stops is not the same. So it difficult to confirm the actual time, using hops to stand for time to live is a better choose.
Subnet Routing Examples的更多相关文章
- ip 子网掩码 网关 DNS
这一篇文章也很好: 原文引用于: http://www.cnblogs.com/jiqing9006/p/3365939.html 内外网ip: IP地址: IPv4地址分为A.B.C.D.E五类, ...
- IP子网掩码划分及设置
IP子网掩码划分及设置 定长子网掩码: 一.子网掩码的计算 TCP/IP网间网技术产生于大型主流机环境中,它能发展到今天的规模是当初的设计者们始料未及的.网间网规模的迅速扩展对IP地址模式的威胁并不是 ...
- HCNP学习笔记之子网掩码的计算和划分详细
0x00 子网掩码的计算 TCP/IP网间网技术产生于大型主流机环境中,它能发展到今天的规模是当初的设计者们始料未及的.网间网规模的迅速扩展对IP地址模式的威胁并不是它不能保证主机地址的唯一性,而是会 ...
- Routing 功能概述 - 每天5分钟玩转 OpenStack(98)
路由服务(Routing)提供跨 subnet 互联互通功能. 例如前面我们搭建了实验环境: cirros-vm1 172.16.100.3 vlan100 cirros-vm ...
- 理解 OpenStack 高可用(HA)(3):Neutron 分布式虚拟路由(Neutron Distributed Virtual Routing)
本系列会分析OpenStack 的高可用性(HA)概念和解决方案: (1)OpenStack 高可用方案概述 (2)Neutron L3 Agent HA - VRRP (虚拟路由冗余协议) (3)N ...
- Examples of MIB Variables - SNMP Tutorial
30.5 Examples of MIB Variables Versions 1 and 2 of SNMP each collected variables together in a singl ...
- 东大OJ-1588: Routing Table
题目描述 In the computer network, a Router is a device which finds an optimal way to transmit the datagr ...
- ural 1072. Routing
1072. Routing Time limit: 1.0 secondMemory limit: 64 MB There is a TCP/IP net of several computers. ...
- Top 30 Nmap Command Examples For Sys/Network Admins
Nmap is short for Network Mapper. It is an open source security tool for network exploration, securi ...
随机推荐
- 把一个项目a生成后放在另一个项目b使用(b项目是例子中的ScreenWebPage_Tool)
a项目属性---生成事件---后期生成事件命令行 xcopy /r /y $(TargetDir)*.* $(SolutionDir)ScreenWebPage_Tool\bin\Debug\* ...
- IoDH 实现的单例模式
饿汉式单例类不能实现延迟加载,不管将来用不用始终占据内存:懒汉式单例类线程安全控制烦琐,而且性能受影响.有种更好的单例模式叫做Initialization Demand Holder (IoDH)的技 ...
- 02HTML-<img>
一.img的属性:alt/title alt属性是替换名字,是给搜索引擎抓取使用,当图片显示不出来时,就会显示出alt的内容: title 属性是提示文字,当鼠标移到图片上的时候会显示出来,大部分的标 ...
- 转动的八卦图纯css实现
这类的东西网上一搜就是大把的,看着比较空旷的博客,所以自己也来写一个. <!DOCTYPE html> <html> <head> <meta chars ...
- Linux下OCI环境配置
ORACLE调用接口(Oracle Call Interface简称OCI)提供了一组可对ORACLE数据库进行存取的接口子例程(函数),通过在第三代程序设计语言(如C语言)中进行调用可达到存取ORA ...
- beifencode
package com.hesheng.myapplication; import android.content.Context;import android.graphics.Bitmap;imp ...
- maven学习(四)maven的生命周期
官网:http://maven.apache.org/guides/introduction/introduction-to-the-lifecycle.html maven有三套相互独立的生命周期, ...
- linux普通用户使用root权限执行命令的脚本
上一篇有说到普通用户使用免密登录并使用root权限: http://www.cnblogs.com/01-single/p/8919254.html 现在使用脚本批量实现部署系统任务操作步骤: #!/ ...
- 关于cmake输出动态链接库名字的问题
使用cmake进行项目编译管理时,我们经常使用 add_library(foo SHARED foo.cpp) 这样的话,输出时,如果在win下面会得到foo.dll,linux下面会得到libfoo ...
- July 24th 2017 Week 30th Monday
The only limit to our realization of tomorrow will be our doubts of today. 实现明天理想的唯一障碍就是今天的疑虑. When ...
