PIX防火墙配置A/S故障切换
PIX防火墙配置A/S故障切换
1、基本命令
failover
show failover
failover lan enable
failover lan interface zwish e2
failover interface ip zwish 172.17.9.1 255.255.255.0 standby 172.17.9.2
failover lan unit primary
failover lan unit secondary
2、示例
拓扑:
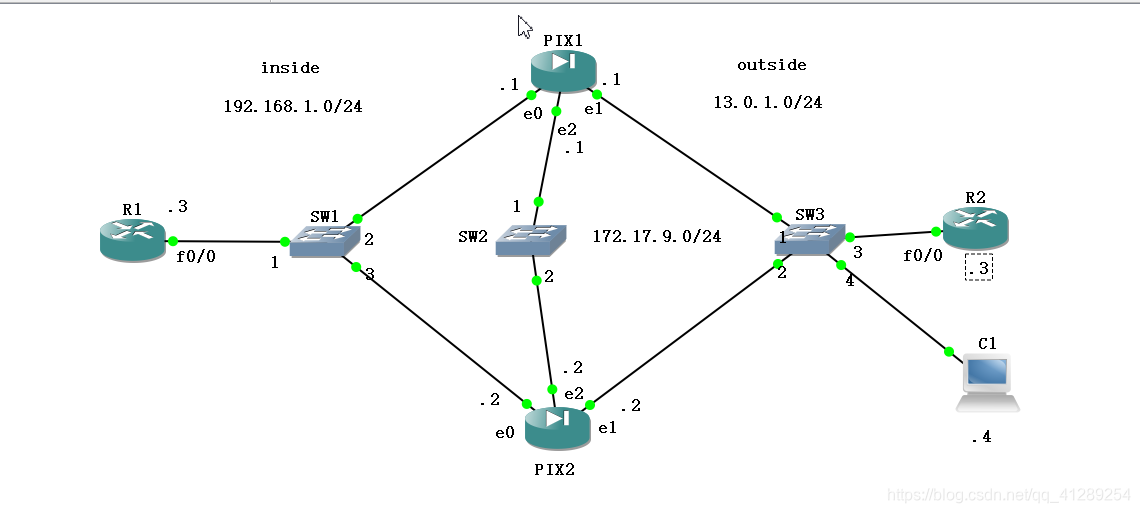
1)配置命令
PIX1主防火墙配置:
pixfirewall> en
Password:
pixfirewall# show mode
Security context mode: single
pixfirewall# show version
Cisco PIX Security Appliance Software Version 7.2(2)
Compiled on Wed 22-Nov-06 14:16 by builders
System image file is "Unknown, monitor mode tftp booted image"
Config file at boot was "startup-config"
pixfirewall up 20 secs
Hardware: PIX-525, 128 MB RAM, CPU Pentium II 1 MHz
Flash E28F128J3 @ 0xfff00000, 16MB
BIOS Flash AM29F400B @ 0xfffd8000, 32KB
0: Ext: Ethernet0 : address is 00ab.bffb.c400, irq 9
1: Ext: Ethernet1 : address is 00ab.bffb.c401, irq 11
2: Ext: Ethernet2 : address is 00ab.bffb.c402, irq 11
3: Ext: Ethernet3 : address is 0000.abfe.0f03, irq 11
4: Ext: Ethernet4 : address is 0000.ab52.1504, irq 11
The Running Activation Key is not valid, using default settings:
Licensed features for this platform:
Maximum Physical Interfaces : 6
Maximum VLANs : 25
Inside Hosts : Unlimited
Failover : Disabled
VPN-DES : Disabled
VPN-3DES-AES : Disabled
Cut-through Proxy : Enabled
Guards : Enabled
URL Filtering : Enabled
Security Contexts : 0
GTP/GPRS : Disabled
#发现这里没有激活防火墙,不支持failover
pixfirewall# activ
pixfirewall# activation-key 0xd2390d2c 0x9fc4b36d 0x98442d99 0xeef7d8b1
The following features available in flash activation key are NOT
available in new activation key:
Failover is different.
flash activation key: Restricted(R)
new activation key: Unrestricted(UR)
Proceed with update flash activation key? [confirm]
The following features available in running activation key are NOT
available in new activation key:
Failover is different.
running activation key: Restricted(R)
new activation key: Unrestricted(UR)
WARNING: The running activation key was not updated with the requested key.
The flash activation key was updated with the requested key, and will
become active after the next reload.
#激活后开始配置pix1主防火墙,(这里做的时候没有使用hostname命名,不过最好有这么一步后面才有对比)
pixfirewall# conf t
pixfirewall(config)# int e0
pixfirewall(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
pixfirewall(config-if)# ip address 192.168.1.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# int e1
pixfirewall(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
pixfirewall(config-if)# ip address 13.0.1.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# int e2
pixfirewall(config-if)# ip address 172.17.9.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# exit
pixfirewall(config)# static (inside,outside) 13.0.1.10 192.168.1.3
#允许13.0.1.3 telnet 13.0.1.10(192.168.1.3)
pixfirewall(config)# access-list test1 permit tcp host 13.0.1.3 host 13.0.1.10 eq telnet
pixfirewall(config)# access-group test1 in int outside
###后面发现使用telnet对比主备防火墙切换不明显,就想换一下ping来对比,这是额外添加的规则###
pixfirewall(config)# access-list test1 extended permit icmp host 13.0.1.10 host 13.0.1.4 echo-reply
pixfirewall(config)# access-list test1 extended permit icmp host 13.0.1.4 host 13.0.1.10 echo
#设置故障切换ip的步骤,这里其实可以与上面的配置接口ip一起做了
pixfirewall(config-if)# int e0
pixfirewall(config-if)# ip address 192.168.1.1 255.255.255.0 standby 192.168.1$
pixfirewall(config-if)# int e1
pixfirewall(config-if)# ip address 13.0.1.1 255.255.255.0 standby 13.0.1.2
pixfirewall(config-if)# exit
pixfirewall(config)# failover lan enable
pixfirewall(config)# failo
pixfirewall(config)# failover lan interface zwish e2
INFO: Non-failover interface config is cleared on Ethernet2 and its sub-interfaces
pixfirewall(config)# failover interface ip zwish 172.17.9.1 255.255.255.0 standby 172.17.9.2
pixfirewall(config)# failover lan unit
pixfirewall(config)# failover lan unit pri
pixfirewall(config)# failover lan unit primary
pixfirewall(config)# failover
pixfirewall(config)# show failover
Failover On
Cable status: N/A - LAN-based failover enabled
Failover unit Primary
Failover LAN Interface: zwish Ethernet2 (up)
Unit Poll frequency 15 seconds, holdtime 45 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 2 of 250 maximum
Version: Ours 7.2(2), Mate Unknown
Last Failover at: 07:26:16 UTC Apr 24 2020
This host: Primary - Negotiation
Active time: 0 (sec)
Interface inside (192.168.1.1): Normal (Waiting)
Interface outside (13.0.1.1): Normal (Waiting)
Other host: Secondary - Not Detected
Active time: 0 (sec)
Interface inside (192.168.1.2): Unknown (Waiting)
Interface outside (13.0.1.2): Unknown (Waiting)
Stateful Failover Logical Update Statistics
Link : Unconfigured.
pixfirewall(config)# .
No Response from Mate
Failover LAN Failed
No switchover
Failover LAN became OK
Switchover enabled
Beginning configuration replication: Sending to mate.
End Configuration Replication to mate
#这里可能需要等一下,再来一次show failover,可以看到主防火墙配置成功
pixfirewall(config)# show failover
Failover On
Cable status: N/A - LAN-based failover enabled
Failover unit Primary
Failover LAN Interface: zwish Ethernet2 (up)
Unit Poll frequency 15 seconds, holdtime 45 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 2 of 250 maximum
Version: Ours 7.2(2), Mate 7.2(2)
Last Failover at: 07:46:05 UTC Apr 24 2020
This host: Primary - Active
Active time: 135 (sec)
Interface inside (192.168.1.1): Normal
Interface outside (13.0.1.1): Normal
Other host: Secondary - Standby Ready
Active time: 0 (sec)
Interface inside (192.168.1.2): Normal
Interface outside (13.0.1.2): Normal
Stateful Failover Logical Update Statistics
Link : Unconfigured.
pixfirewall(config)#
PIX2备份防火墙配置:
pixfirewall> en
Password:
pixfirewall# conf t
pixfirewall(config)# int e0
pixfirewall(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
pixfirewall(config-if)# ip address 192.168.1.2 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# int e1
pixfirewall(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
pixfirewall(config-if)# ip address 13.0.1.2 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# int e2
pixfirewall(config-if)# ip address 172.17.9.2 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# exit
pixfirewall(config)# failover lan enable
pixfirewall(config)# failover lan interface zwish e2
INFO: Non-failover interface config is cleared on Ethernet2 and its sub-interfaces
pixfirewall(config)# failover interface ip zwish 172.17.9.1 255.255.255.0 stan$
pixfirewall(config)# failover lan unit sec
pixfirewall(config)# failover lan unit secondary
pixfirewall(config)# failover
pixfirewall(config)# show failover
Failover On
Cable status: N/A - LAN-based failover enabled
Failover unit Secondary
Failover LAN Interface: zwish Ethernet2 (up)
Unit Poll frequency 15 seconds, holdtime 45 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 2 of 250 maximum
Version: Ours 7.2(2), Mate 7.2(2)
Last Failover at: 07:40:21 UTC Apr 24 2020
This host: Secondary - Negotiation
Active time: 0 (sec)
Interface inside (192.168.1.2): No Link (Waiting)
Interface outside (13.0.1.2): No Link (Waiting)
Other host: Primary - Active
Active time: 0 (sec)
Interface inside (0.0.0.0): Unknown (Waiting)
Interface outside (0.0.0.0): Unknown (Waiting)
Stateful Failover Logical Update Statistics
Link : Unconfigured.
pixfirewall(config)# .
Detected an Active mate
Beginning configuration replication from mate.
End configuration replication from mate.
pixfirewall(config)# show failover
Failover On
Cable status: N/A - LAN-based failover enabled
Failover unit Secondary
Failover LAN Interface: zwish Ethernet2 (up)
Unit Poll frequency 15 seconds, holdtime 45 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 2 of 250 maximum
Version: Ours 7.2(2), Mate 7.2(2)
Last Failover at: 07:40:21 UTC Apr 24 2020
This host: Secondary - Standby Ready
Active time: 0 (sec)
Interface inside (192.168.1.2): Normal
Interface outside (13.0.1.2): Normal
Other host: Primary - Active
Active time: 90 (sec)
Interface inside (192.168.1.1): Normal
Interface outside (13.0.1.1): Normal
Stateful Failover Logical Update Statistics
Link : Unconfigured.
pixfirewall(config)#
原本是打算用R2 telnet R1的,但发现对比不明显,所以临时在拓扑中加了一个PC(ip为13.0.1.4,为了简单,和不打乱前面的配置,就直接接在了交换机)
2)测试
故障切换前主防火墙和备份防火墙的故障切换配置在上面的命令行中
然后用PC ping R1,设置为50次,然后把主防火墙断电(这里应该还可以使用shutdown关闭接口)
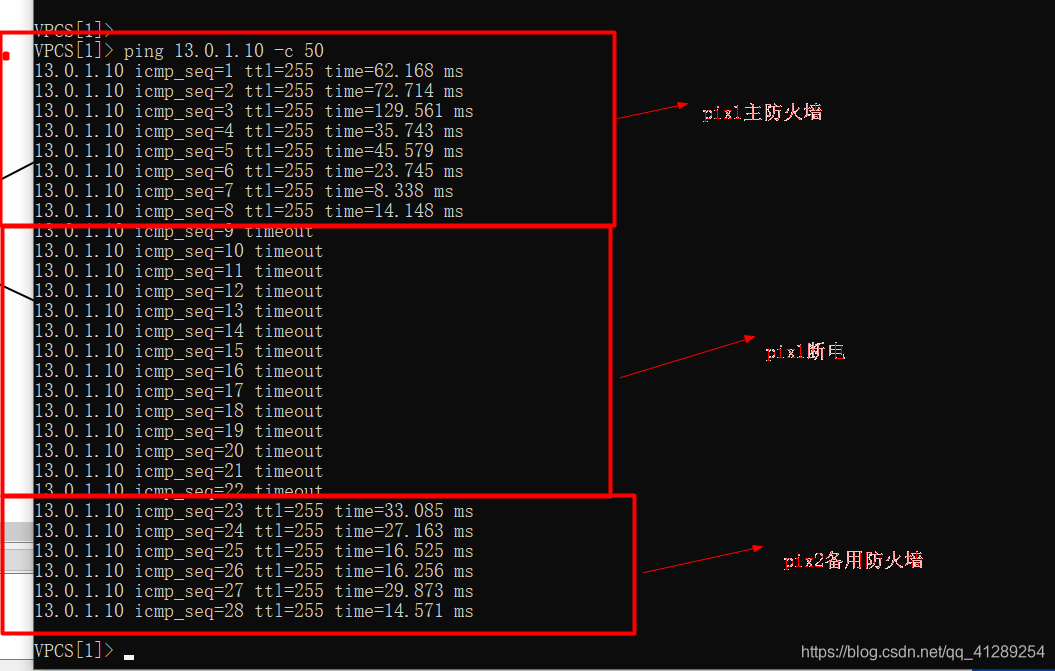
从ping的情况可以看出切换成功了
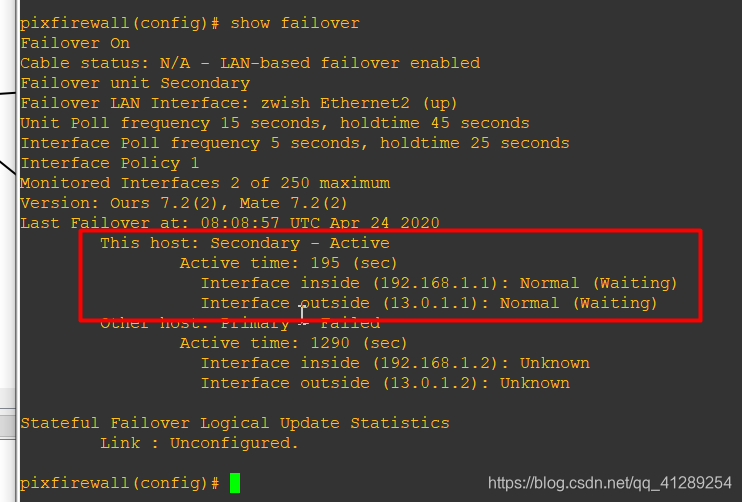
看一下切换后的PIX2,发现状态为Active,inside和outside的ip是原来主防火墙PIX1,证明试验成功:
PIX防火墙配置A/S故障切换的更多相关文章
- PIX 防火墙
---恢复内容开始--- 一 , PIX 防火墙的认识 PIX 是cisco 的硬件防火墙 硬件防火墙的工作速度快,使用方便. PIX 有很多型号,并发连接数是PIX防火墙的重要参数 PIX 25 ...
- Cisco PIX防火墙PPPoE拨号配置视频教学
Cisco PIX防火墙PPPoE拨号配置视频教学 本文出自 "李晨光原创技术博客" 博客,请务必保留此出处http://chenguang.blog.51cto.com/35 ...
- 6. Samba服务和防火墙配置笔记
Samba文件服务器 (一)简介 内网文件服务器 windows-windows 文件共享服务 网络邻居linux-linux NFS windows-linux Samba (二)端口 smbd: ...
- CentOS7下Firewall防火墙配置用法详解
官方文档地址: https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/7/html/Security_Guide ...
- [转] Linux下防火墙iptables用法规则详及其防火墙配置
from: http://www.cnblogs.com/yi-meng/p/3213925.html 备注: 排版还不错,建议看以上的链接. iptables规则 规则--顾名思义就是规矩和原则,和 ...
- Linux 学习之防火墙配置
1.安装iptables防火墙 yum install iptables 2. 清除已有的iptables规则 iptables -F iptables -X iptables -Z 3.显 ...
- Linux防火墙配置—SNAT2
1.实验目标 以实验"Linux防火墙配置-SNAT1"为基础,为网关增加外网IP地址,为eth1创建虚拟接口,使外网测试主机在Wireshark中捕获到的地址为eth1虚拟接口的 ...
- Linux防火墙配置—SNAT1
1.实验目标 以实验"防火墙配置-访问外网WEB"为基础,在WEB服务器上安装Wireshark,设置Wireshark的过滤条件为捕获HTTP报文,在Wireshark中开启捕获 ...
- CentOSv6.8 修改防火墙配置、修改SSH端口
查看防火墙目前使用状况: service iptables status 修改防火墙配置: vi /etc/sysconfig/iptables 重启防火墙,让刚才修改的配置生效: service i ...
随机推荐
- 网络流最小割 H - Internship I - Friendship
我觉得这两个最小割都还比较难. 第一个题目大意是给你一个网络,这个网络是由城市和中转站组成,终点是0,给你每一条边的流量, 问,从城市到终点最大流流完之后,是否可以增加一条路上的一条边的容量,使得最大 ...
- P2762 太空飞行计划问题 网络流
题目描述 W 教授正在为国家航天中心计划一系列的太空飞行.每次太空飞行可进行一系列商业性实验而获取利润.现已确定了一个可供选择的实验集合E={E1,E2,…,Em},和进行这些实验需要使用的全部仪器的 ...
- python 读取矢量文件
#导入包 from osgeo import ogr #打开文件(False - read only, True - read/write) filename = "文件名.shp" ...
- 一文教你如何在ubuntu上快速搭建STM32 CubeIDE环境(图文超详细+文末有附件)
在快速ubuntu上安装cubeide你值得拥有:适合对linux系统还不是很熟悉的同学: 文章目录 1 下载 cubeide 2 找到软件 3 安装 4 附件 5 总结 1 下载 cubeide 登 ...
- Linux 内核工作队列之work_struct 学习总结
前言 编写Linux驱动的时候对于work_struct的使用还是很普遍的,很早之前就在阅读驱动源码的时候就看到了它的踪影,根据其命名大概知道了它的具体作用,但是仍然不知所以,同时,伴随出现的还有de ...
- Java 多线程启动为什么调用 start() 方法而不是 run() 方法?
多线程在工作中多多少少会用到,我们知道启动多线程调用的是 start() 方法,而不是 run() 方法,你知道原因吗? 在探讨这个问题之前,我们先来了解一些多线程的基础知识~ 线程的状态 Java ...
- 5.7.17版本mysqlbinlog实时拉取的二进制日志不完整的原因分析
问题描述: 同事使用mysqlbinlog工具的--read-from-remote-server --raw选项,从远程实例实时拉取二进制日志时,发现得到的二进制日志文件大小与远程实例上的源文件大小 ...
- HMM-维特比算法理解与实现(python)
HMM-前向后向算法理解与实现(python) HMM-维特比算法理解与实现(python) 解码问题 给定观测序列 \(O=O_1O_2...O_T\),模型 \(\lambda (A,B,\pi) ...
- printf小结
下午健身前和lxt兄弟讨论了一个关于 printf 输出的问题,恰巧以前见过类似的,回来写一个收获总结. 首先看一个这样一个例子 #include<cstdio> int i; int m ...
- C#winform跨窗体传值和调用事件的办法
有三个窗体,分别是Main主窗体,Form1窗体1,From2窗体2,其中Main是主窗体,Form1窗体1是一个消息通知窗体,Form2窗体2主窗体的一个子窗体,程序启动时,消息框窗体1弹出,通过消 ...
