腾讯云CVM之间配置免密钥登录
背景:
1客户A和B俩台主机之间需要实现免密钥登录,已绑定腾讯云申请的密钥对
系统:centos7.3
A:192.168.0.100
B:192.168.0.84
A主机的私钥文件:aaa
B主机的私钥文件:bbb
公钥文件:authorized_keys
/etc/ssh/sshd.conf文件修改参数,前面有“#”注释符的需要去掉
HostKey /etc/ssh/ssh_host_rsa_key
RSAAuthentication yes
PubkeyAuthentication yes
AuthorizedKeysFile .ssh/authorized_keys
PasswordAuthentication no
参考sshd_config配置文件,注意系统版本,不适用centos6.x版本,修改配置文件前做好备份
# $OpenBSD: sshd_config,v 1.93 // :: djm Exp $ # This is the sshd server system-wide configuration file. See
# sshd_config() for more information. # This sshd was compiled with PATH=/usr/local/bin:/usr/bin # The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value. # If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
#Port
#AddressFamily any
#ListenAddress 192.168.0.100
#ListenAddress 192.168.0.100 # The default requires explicit activation of protocol
#Protocol # HostKey for protocol version
#HostKey /etc/ssh/ssh_host_key
# HostKeys for protocol version
HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key # Lifetime and size of ephemeral version server key
#KeyRegenerationInterval 1h
#ServerKeyBits # Ciphers and keying
#RekeyLimit default none # Logging
# obsoletes QuietMode and FascistLogging
#SyslogFacility AUTH
SyslogFacility AUTHPRIV
#LogLevel INFO # Authentication: #LoginGraceTime 2m
#PermitRootLogin yes
#StrictModes yes
#MaxAuthTries
#MaxSessions RSAAuthentication yes
PubkeyAuthentication yes # The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys #AuthorizedPrincipalsFile none #AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody # For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#RhostsRSAAuthentication no
# similar for protocol version
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# RhostsRSAAuthentication and HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes # To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication no
#PermitEmptyPasswords no
PasswordAuthentication no # Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no # Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes # GSSAPI options
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
#GSSAPIEnablek5users no # Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
# WARNING: 'UsePAM no' is not supported in Red Hat Enterprise Linux and may cause several
# problems.
UsePAM yes #AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset
#X11UseLocalhost yes
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
UsePrivilegeSeparation sandbox # Default for new installations.
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval
#ClientAliveCountMax
#ShowPatchLevel no
UseDNS no
#PidFile /var/run/sshd.pid
#MaxStartups ::
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none # no default banner path
#Banner none # Accept locale-related environment variables
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS # override default of no subsystems
Subsystem sftp /usr/libexec/openssh/sftp-server # Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
操作步骤
1.首先把aaa和bbb私钥文件分别上传到A主机和B主机上的/root/.ssh/目录中(上传可以安装lrzsz工具,直接拖文件到服务器即可)
A主机:
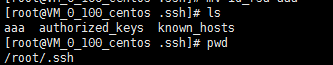
B:主机
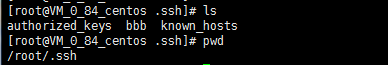
2.将A主机中的authorized_keys中的公钥拷贝到B主机的authorized_keys文件中
将B主机中的authorized_keys中的公钥保存的A主机的authorized_keys文件中
A主机的authorized_keys文件
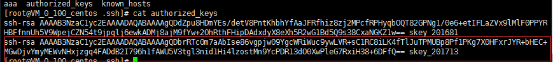
B主机的authorized_keys文件
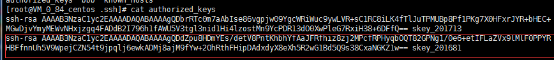
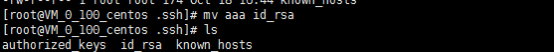
3.将A主机和B主机的私钥文件分别修改为id_rsa
A主机.ssh/目录下的内容
mv /root/.ssh/aaa /root/.ssh/id_rsa
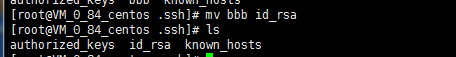
B主机.ssh/目录下的内容
mv /root/.ssh/aaa /root/.ssh/id_rsa
4.分别在A主机和B主机上执行下面授权操作
chmod 700 ~/.ssh/
chmod 600 ~/.ssh/authorized_keys
chmod 600 ~/.ssh/id_rsa
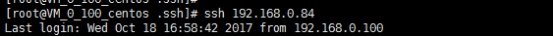
最后来验证
A主机远程B主机:
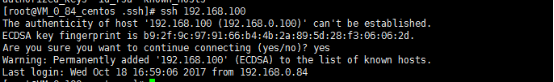
B主机远程A主机
腾讯云CVM之间配置免密钥登录的更多相关文章
- Linux机器之间SSH免密钥登录设置
SSH免密钥登录 私钥:密钥留在本机 公钥:密钥发给其他机 hadoop01 生成密钥: ssh-keygen -t rsa (密钥存放路径:/root/.ssh) id_rsa:私钥 id_rsa. ...
- linux 服务器之间配置免密登录
客户机:172.16.1.2 远程机:172.16.1.3 1.远程机 a.允许root用户通过22端口登录 vi /etc/ssh/sshd_config PORT 22 PermitRootLog ...
- 弹性配置为构建提速 - CODING & 腾讯云 CVM 最佳实践
CODING 中提供了内置云主机用来执行持续集成(CI)中的构建计划,能够胜任大部分构建任务.但如果碰上了大型项目的构建,或者需要在本地服务器生成构建成果,单个计算资源就显得有点捉急了.针对这一部分需 ...
- 集群中配置多台机器之间 SSH 免密码登录
集群中配置多台机器之间 SSH 免密码登录 问题描述 由于现在项目大多数由传统的单台机器部署,慢慢转变成多机器的集群化部署. 但是,这就涉及到机器间的 SSH 免密码互通问题. 当集群机器比较多的时候 ...
- java:Linux(简单命令,远程ssh使用hostname访问,.免密钥登录配置)
1.临时关闭防火墙: service iptables stop 临时开启防火墙: service iptables start 查看防火墙状态: service iptables sta ...
- linux系统ssh免密钥登录配置
linux主机配置ssh免密钥登录,具体配置如下: 1.执行命令ssh-keygen -t rsa,生成公钥和私钥(具体步骤详见下图) 2.会在当前用户的家目录的.ssh/生成公钥和私钥, 3.执行s ...
- 集群之间配置 SSH无密码登录
集群之间配置 SSH无密码登录 配置 ssh (1)基本语法 ssh 另一台电脑的 ip 地址 (2)ssh 连接时出现 Host key verification failed 的解决方法 # ss ...
- [CentOS] SSH 免密钥登录
一.环境说明: 操作系统:CentOS-7-x86_64-Minimal-1611 虚拟机:VMware® Workstation 12 Pro:12.5.5 build-5234757 服务器:no ...
- 014-配置SSH免密钥登录
问题:client端需要免密钥登录服务器server如何配置?1.前提:客户端已安装openssh-client;服务端已安装openssh-server;服务器端22号端口已经打开2.需要密钥登录时 ...
随机推荐
- [Java] [查找文件] [递归]]
// 工具方法 private static FilenameFilter getFilter(final String mode) { return new FilenameFilter() { P ...
- 用EditPlus和jdk写Java代码
一.安装EditPlus EditPlus: https://www.editplus.com/latest4.html EditPlus注册码在线生成: https://www.jb51.net/t ...
- 向JSP中静态导入HTML文件时,运行jsp时,html中中文产生乱码问题最简单的解决方法
在保证其他的编码格式一致的情况下 在html标签内,head标签外添加一下代码时可以完美解决 亲测 <%@page pageEncoding="UTF-8"%>
- Js调用asp.net后台代码
方法一: 1.首先建立一个按钮,在后台将调用或处理的内容写入button_click中; 2.在前台写一个js函数,内容为document.getElementById("b ...
- solr window环境安装配置和管理页面基本使用
solr介绍 来自官网http://lucene.apache.org/solr/解释: Solr is highly reliable, scalable and fault tolerant, p ...
- Git学习之连接GitHub远程仓库
在看此教程之前电脑上应该已安装好git,并且配置好基本信息,Git新手请从头开始. 第1步:创建SSH Key 在用户主目录下(Mac系统是在用户主目录下,可通过命令ll -a查看,Windows下自 ...
- this与回调函数
在c++里回调函数分2种: 全局函数:不包函在类的内部 或 类内部的静态函数 类内部函数(或叫 局部函数):需要通过实例化后的对象调用的 因c++是c的一层封装,所以类似c里struct内的函数 在传 ...
- flask的基础认识
刚开始学习flask基础知识,有了一点点的认识,所以在此大概写一下自己的理解,详细步骤和功能在代码段介绍: from flask import Flask,render_template,reques ...
- 分页插件通用处理,以asp.net mvc为例
Model: public class PaggerModel { public PaggerModel() { BarSize = ; } public PaggerModel(int total, ...
- 图片转换base64编码,点击div的时候选择文件
有时候我们希望文件上传的时候预览图片,下面插件可以实现上传前预览图片 (也可以提取文件的base64编码) max-height: 140px;max-width: 120px;可以指定图片的最大宽度 ...
