新版本wireshark tshark使用
Wireshark-tshark
wireshark 指令模式 => tshark
Windows 及Linux 可至安裝目錄執行>tshark
tshark.exe -i 7(利用-D找要的介面代號)
輸出json版本需要2.2以上,Centos需要原碼安裝
ubuntu===============================================================
sudo apt-add-repository ppa:wireshark-dev/stable
sudo apt-get update
sudo apt-get install wireshark
sudo dpkg-reconfigure wireshark-common
Centos7===============================================================
SUDO YUM INSTALL BISON FLEX GTK3-DEVEL QT-DEVEL GCC-C++ LIBPCAP-DEVEL C-ARES-DEVEL LIBSMI-DEVEL GNUTLS-DEVEL LIBGCRYPT-DEVEL KRB5-DEVEL GEOIP-DEVEL ORTP-DEVEL PORTAUDIO-DEVEL AUTOMAKE AUTOCONF LIBTOOL
TAR XF WIRESHARK*
CD /WIRESHARK*
./AUTOGEN.SH
./CONFIGURE –ENABLE-SETCAP-INSTALL
MAKE
SUDO MAKE INSTALL
===============================================================
tshark command
TShark (Wireshark) 2.2.4 (v2.2.4-0-gcc3dc1b)
Dump and analyze network traffic.
See https://www.wireshark.org for more information.
Usage: tshark [options] …
Capture interface:
-i name or idx of interface (def: first non-loopback) #擷取介面 ex. -i ens160
-f packet filter in libpcap filter syntax #wireshark的capture 相同,可直接參考string指令
-s packet snapshot length (def: 65535)
-p don’t capture in promiscuous mode
-I capture in monitor mode, if available
-B size of kernel buffer (def: 2MB)
-y link layer type (def: first appropriate)
-D print list of interfaces and exit
-L print list of link-layer types of iface and exit
Capture stop conditions:
-c stop after n packets (def: infinite) #ex.-c 10 抓十個包
-a … duration:NUM – stop after NUM seconds
filesize:NUM – stop this file after NUM KB
files:NUM – stop after NUM files
Capture output:
-b … duration:NUM – switch to next file after NUM secs
filesize:NUM – switch to next file after NUM KB
files:NUM – ringbuffer: replace after NUM files
RPCAP options:
-A : use RPCAP password authentication
Input file:
-r set the filename to read from (- to read from stdin) #讀pcap檔
Processing:
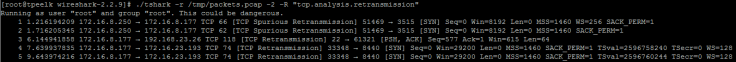
-2 perform a two-pass analysis #參考下面例子
-R packet Read filter in Wireshark display filter syntax#與wireshark Filter功能相同,與其他分析結合需要加-2
EX:查RTO的封包: ./tshark -r /tmp/packets.pcap -2 -R “tcp.analysis.retransmission"
-Y packet displaY filter in Wireshark display filter
syntax #與-R相同功能更強大?
-n disable all name resolutions (def: all enabled)
-N enable specific name resolution(s): “mnNtCd"
-d ==, …
“Decode As", see the man page for details
Example: tcp.port==8888,http
-H read a list of entries from a hosts file, which will
then be written to a capture file. (Implies -W n)
–disable-protocol disable dissection of proto_name
–enable-heuristic
enable dissection of heuristic protocol
–disable-heuristic
disable dissection of heuristic protocol
Output:
-w <outfile|-> write packets to a pcap-format file named “outfile" #存檔成pcap,相關-T
(or to the standard output for “-“)
-C start with specified configuration profile
-F set the output file type, default is pcapng
an empty “-F" option will list the file types
-V add output of packet tree (Packet Details) #顯示封包樹狀詳細內容
-O Only show packet details of these protocols, comma
separated
-P print packet summary even when writing to a file
-S the line separator to print between packets
-x add output of hex and ASCII dump (Packet Bytes)
-T pdml|ps|psml|json|ek|text|fields #存檔成其他格式,相關-w
format of text output (def: text)
-j protocols layers filter if -T ek|pdml|json selected,
(e.g. “http tcp ip",
-e field to print if -Tfields selected (e.g. tcp.port,
_ws.col.Info)
this option can be repeated to print multiple fields
-E= set options for output when -Tfields selected:
bom=y|n print a UTF-8 BOM
header=y|n switch headers on and off
separator=/t|/s| select tab, space, printable character as separator
occurrence=f|l|a print first, last or all occurrences of each field
aggregator=,|/s| select comma, space, printable character as
aggregator
quote=d|s|n select double, single, no quotes for values
-t a|ad|d|dd|e|r|u|ud output format of time stamps (def: r: rel. to first) #轉時間格式 EX: ad是 2017-09-05 14:28:08
-u s|hms output format of seconds (def: s: seconds)
-l flush standard output after each packet
-q be more quiet on stdout (e.g. when using statistics) #配合-z 可只顯示分析結果
-Q only log true errors to stderr (quieter than -q)
-g enable group read access on the output file(s)
-W n Save extra information in the file, if supported.
n = write network address resolution information
-X : eXtension options, see the man page for details
-U tap_name PDUs export mode, see the man page for details
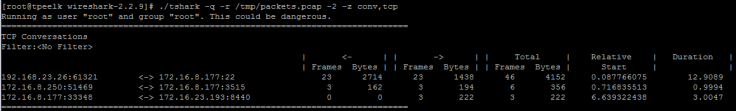
-z various statistics, see the man page for details #使用內建的統計分析
EX統計IP: -z conv,ip
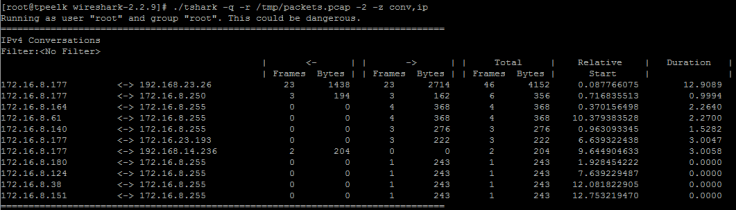
EX2統計tcp Conversations status: -z conv,tcp
–capture-comment
add a capture comment to the newly created
output file (only for pcapng)
Miscellaneous:
-h display this help and exit
-v display version info and exit
-o : … override preference setting
-K keytab file to use for kerberos decryption
-G [report] dump one of several available reports and exit
default report="fields"
use “-G ?" for more help
Reference:
新版本wireshark tshark使用的更多相关文章
- wireshark自动化之tshark命令行
tshark是wireshark安装目录下命令行工具 使用tshark可以通过自动化方式调用wireshark tshark -a duration:30 抓包30秒-w cap.cap 保存为cap ...
- centos Linux系统日常管理2 tcpdump,tshark,selinux,strings命令, iptables ,crontab,TCP,UDP,ICMP,FTP网络知识 第十五节课
centos Linux系统日常管理2 tcpdump,tshark,selinux,strings命令, iptables ,crontab,TCP,UDP,ICMP,FTP网络知识 第十五节课 ...
- Debian 7 安装 wireshark
安装过程很简单: $ sudo apt-get install wireshark 其中会弹出一个对话框: ┌─────────────────────┤ Configuring wireshark- ...
- 抓包工具tshark使用备忘
抓包命令行工具tshark可以用于自定制,相比GUI工具可以实现一些自动化,譬如把某些关注的数据抓起下来存放到文本中,然后再分析输出. demo: std::string deco ...
- tcpdump VS tshark用法(转)
Tcpdump是网络协议分析的基本工具.tshark是大名鼎鼎的开源网络协议分析工具wireshark (原名叫ethereal)的命令行版本,wireshark可对多达千余种网络协议进行解码分析.W ...
- Lua语言在Wireshark中使用(转)
1. 检查Wireshark的版本是否支持Lua 打开Wireshark,点击“HelpàAbout Wireshark”菜单,查看弹出的对话框,如果有“with Lua 5.1”表示支持 ...
- wireshark filter manualpage
NAME wireshark-filter - Wireshark filter syntax and reference SYNOPSIS wireshark [other options] [ - ...
- python3+pyshark读取wireshark数据包并追踪telnet数据流
一.程序说明 本程序有两个要点,第一个要点是读取wireshark数据包(当然也可以从网卡直接捕获改个函数就行),这个使用pyshark实现.pyshark是tshark的一个python封装,至于t ...
- 最有用的Linux命令行使用技巧集锦
最近在Quora上看到一个问答题目,关于在高效率Linux用户节省时间Tips.将该题目的回答进行学习总结,加上自己的一些经验,记录如下,方便自己和大家参考. 下面介绍的都是一些命令行工具,这些工具在 ...
随机推荐
- Guava 3: 集合Collections
一.引子 Guava 对JDK集合的拓展,是最成熟且最受欢迎的部分.本文属于Guava的核心,需要仔细看. 二.Guava 集合 2.1 Immutable Collections不可变集合 1.作用 ...
- CenterOS7.5中搭建wordpress
centeros7.5中搭建wordpress 1.环境 云平台:华为云 服务器操作系统:CentOS7.: 博客部署的服务器:Apache HTTP: 数据库:mysql: 框架:wordpress ...
- Win7系统安装Centos7.0双系统(三)
4.6语言选择 4.7安装信息设置,除以下几项改动其他都可默认. 软件选择(默认最小):带GUI的服务器或GNOME桌面,可根据使用需要选择安装软件. 磁盘分区:Linux默认可分为3个分区,分别是b ...
- workerman相关
(1)workerman linxu 内核优化 http://doc.workerman.net/315302 (2)workerman 安装环境配置 http://doc.workerman.ne ...
- mmap映射区和shm共享内存的区别总结
[转载]原文链接:https://blog.csdn.net/hj605635529/article/details/73163513 linux中的两种共享内存.一种是我们的IPC通信System ...
- Python【每日一问】03
问:请给出下列代码的执行结果,并解释 a = dict.fromkeys([6, 7, 8], ["testing", {"name": "ken&q ...
- .NET自动化测试工具:Selenium Grid
在生产环境,QA会同时跑几十个上百个的test case.如果用单机串行的话,是一件非常耗时的事情,估计比手点快不了多少.使用并行方案的话,有两种方法,一个是自己写并行框架,一个是用现成的Seleni ...
- 经典技术之URL
SpringBoot入门 (十) 发送邮件 图表算法—最短路径 三个好用的并发工具类 跨应用Session共享: https://www.cnblogs.com/websharing/p/849586 ...
- leetcode208
class TrieNode { public: // Initialize your data structure here. TrieNode() { words=; prefixs=; ;i&l ...
- 20165304 2017-2018-2《Java程序设计》学习总结
20165304 2017-2018-2<Java程序设计>学习总结 一.每周作业及实验报告链接汇总 1.我期望的师生关系 2.20165304学习基础和C语言基础调查 3.linux系统 ...
