通过keepalived实现多主集群方案
一、 环境说明:
1、服务器列表:
proxy01:
eth0: 192.168.56.11 eth2: 192.168.156.11
proxy02:
eth0: 192.168.56.12 eth2: 192.168.156.12
proxy03:
eth0: 192.168.56.13 eth2: 192.168.156.13
2、拓扑图:
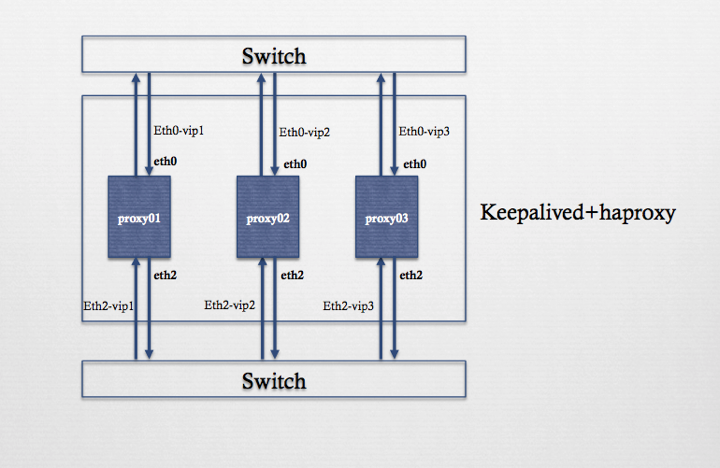
二、 实验步骤
1、 在所有节点上操作
# yum install –y keepalived haproxy
2、 proxy01节点配置
[root@proxy01 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived global_defs {
router_id LVS_DEVEL
vrrp_skip_check_adv_addr
# vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
} vrrp_sync_group VG1 {
group {
VI_1
VI_11
}
} vrrp_sync_group VG2 {
group {
VI_2
VI_12
}
} vrrp_sync_group VG3 {
group {
VI_3
VI_13
}
} vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 51
##nopreempt 启用抢占模式
priority 10
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac #启用vmac模式,会创建虚拟机接口,vip绑定到虚拟接口上
vmac_xmit_base #发送和接收VRRP包的虚拟MAC地址
unicast_src_ip 192.168.56.11
unicast_peer {
192.168.56.12
192.168.56.13
}
virtual_ipaddress {
192.168.56.101
}
} vrrp_instance VI_2 {
state BACKUP
interface eth0
virtual_router_id 52
priority 20
##nopreempt
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.56.11
unicast_peer {
192.168.56.12
192.168.56.13
}
virtual_ipaddress {
192.168.56.102
}
} vrrp_instance VI_3 {
state BACKUP
interface eth0
virtual_router_id 53
priority 30
advert_int 1
##nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.56.11
unicast_peer {
192.168.56.12
192.168.56.13
}
virtual_ipaddress {
192.168.56.103
}
} vrrp_instance VI_11 {
state BACKUP
interface eth2
virtual_router_id 51
##nopreempt
priority 10
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.156.11
unicast_peer {
192.168.156.12
192.168.156.13
}
virtual_ipaddress {
192.168.156.101
}
} vrrp_instance VI_12 {
state BACKUP
interface eth2
virtual_router_id 52
priority 20
#nopreempt
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.156.11
unicast_peer {
192.168.156.12
192.168.156.13
}
virtual_ipaddress {
192.168.156.102
}
} vrrp_instance VI_13 {
state BACKUP
interface eth2
virtual_router_id 53
priority 30
advert_int 1
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.156.11
unicast_peer {
192.168.156.12
192.168.156.13
}
virtual_ipaddress {
192.168.156.103
}
}
3、 proxy02节点配置
[root@proxy02 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived global_defs {
router_id LVS_DEVEL
vrrp_skip_check_adv_addr
# vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
} vrrp_sync_group VG1 {
group {
VI_1
VI_11
}
} vrrp_sync_group VG2 {
group {
VI_2
VI_12
}
} vrrp_sync_group VG3 {
group {
VI_3
VI_13
}
} vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 51
#nopreempt
priority 20
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.56.12
unicast_peer {
192.168.56.11
192.168.56.13
}
virtual_ipaddress {
192.168.56.101
}
} vrrp_instance VI_2 {
state BACKUP
interface eth0
virtual_router_id 52
#nopreempt
priority 30
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.56.12
unicast_peer {
192.168.56.11
192.168.56.13
}
virtual_ipaddress {
192.168.56.102
}
} vrrp_instance VI_3 {
state BACKUP
interface eth0
virtual_router_id 53
#nopreempt
priority 10
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.56.12
unicast_peer {
192.168.56.11
192.168.56.13
}
virtual_ipaddress {
192.168.56.103
}
} vrrp_instance VI_11 {
state BACKUP
interface eth2
virtual_router_id 51
#nopreempt
priority 20
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.156.12
unicast_peer {
192.168.156.11
192.168.156.13
}
virtual_ipaddress {
192.168.156.101
}
} vrrp_instance VI_12 {
state BACKUP
interface eth2
virtual_router_id 52
#nopreempt
priority 30
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.156.12
unicast_peer {
192.168.156.11
192.168.156.13
}
virtual_ipaddress {
192.168.156.102
}
} vrrp_instance VI_13 {
state BACKUP
interface eth2
virtual_router_id 53
#nopreempt
priority 10
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.156.12
unicast_peer {
192.168.156.11
192.168.156.13
}
virtual_ipaddress {
192.168.156.103
}
}
4、 proxy03节点配置
[root@proxy03 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived global_defs {
# notification_email {
# acassen@firewall.loc
# failover@firewall.loc
# sysadmin@firewall.loc
# }
# notification_email_from Alexandre.Cassen@firewall.loc
# smtp_server 192.168.200.1
# smtp_connect_timeout 30
router_id LVS_DEVEL
vrrp_skip_check_adv_addr
# vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
} vrrp_sync_group VG1 {
group {
VI_1
VI_11
}
} vrrp_sync_group VG2 {
group {
VI_2
VI_12
}
} vrrp_sync_group VG3 {
group {
VI_3
VI_13
}
} vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 51
#nopreempt
priority 30
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.56.13
unicast_peer {
192.168.56.11
192.168.56.12
}
virtual_ipaddress {
192.168.56.101
}
} vrrp_instance VI_2 {
state BACKUP
interface eth0
virtual_router_id 52
#nopreempt
priority 10
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.56.13
unicast_peer {
192.168.56.11
192.168.56.12
}
virtual_ipaddress {
192.168.56.102
}
} vrrp_instance VI_3 {
state BACKUP
interface eth0
virtual_router_id 53
#nopreempt
priority 20
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.56.13
unicast_peer {
192.168.56.11
192.168.56.12
}
virtual_ipaddress {
192.168.56.103
}
} vrrp_instance VI_11 {
state BACKUP
interface eth2
virtual_router_id 51
#nopreempt
priority 30
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.156.13
unicast_peer {
192.168.156.11
192.168.156.12
}
virtual_ipaddress {
192.168.156.101
}
} vrrp_instance VI_12 {
state BACKUP
interface eth2
virtual_router_id 52
#nopreempt
priority 10
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.156.13
unicast_peer {
192.168.156.11
192.168.156.12
}
virtual_ipaddress {
192.168.156.102
}
} vrrp_instance VI_13 {
state BACKUP
interface eth2
virtual_router_id 53
#nopreempt
priority 20
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
use_vmac
vmac_xmit_base
unicast_src_ip 192.168.156.13
unicast_peer {
192.168.156.11
192.168.156.12
}
virtual_ipaddress {
192.168.156.103
}
}
5、 启动服务
在所有节点操作
# systemctl enable keepalived.service && systemctl start keepalived.service
6、 结果验证
[root@proxy01 ~]# ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 08:00:27:4b:3e:34 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.11/24 brd 192.168.56.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fe4b:3e34/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 08:00:27:17:a2:bc brd ff:ff:ff:ff:ff:ff
inet 10.0.3.15/24 brd 10.0.3.255 scope global dynamic eth1
valid_lft 85732sec preferred_lft 85732sec
inet6 fe80::a00:27ff:fe17:a2bc/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 08:00:27:ff:0e:a8 brd ff:ff:ff:ff:ff:ff
inet 192.168.156.11/24 brd 192.168.156.255 scope global eth2
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:feff:ea8/64 scope link
valid_lft forever preferred_lft forever
5: vrrp.51@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:33 brd ff:ff:ff:ff:ff:ff
6: vrrp.52@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:34 brd ff:ff:ff:ff:ff:ff
7: vrrp.53@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:35 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.103/32 scope global vrrp.53
valid_lft forever preferred_lft forever
8: vrrp1.51@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:33 brd ff:ff:ff:ff:ff:ff
9: vrrp1.52@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:34 brd ff:ff:ff:ff:ff:ff
10: vrrp1.53@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:35 brd ff:ff:ff:ff:ff:ff
inet 192.168.156.103/32 scope global vrrp1.53
valid_lft forever preferred_lft forever [root@proxy02 ~]# ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 08:00:27:ee:7d:7e brd ff:ff:ff:ff:ff:ff
inet 192.168.56.12/24 brd 192.168.56.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:feee:7d7e/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 08:00:27:a4:ce:2f brd ff:ff:ff:ff:ff:ff
inet 10.0.3.15/24 brd 10.0.3.255 scope global dynamic eth1
valid_lft 85717sec preferred_lft 85717sec
inet6 fe80::a00:27ff:fea4:ce2f/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 08:00:27:6c:16:4d brd ff:ff:ff:ff:ff:ff
inet 192.168.156.12/24 brd 192.168.156.255 scope global eth2
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fe6c:164d/64 scope link
valid_lft forever preferred_lft forever
5: vrrp.51@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:33 brd ff:ff:ff:ff:ff:ff
6: vrrp.52@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:34 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.102/32 scope global vrrp.52
valid_lft forever preferred_lft forever
7: vrrp.53@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:35 brd ff:ff:ff:ff:ff:ff
8: vrrp1.51@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:33 brd ff:ff:ff:ff:ff:ff
9: vrrp1.52@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:34 brd ff:ff:ff:ff:ff:ff
inet 192.168.156.102/32 scope global vrrp1.52
valid_lft forever preferred_lft forever
10: vrrp1.53@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:35 brd ff:ff:ff:ff:ff:ff [root@proxy03 ~]# ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 08:00:27:87:1a:f0 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.13/24 brd 192.168.56.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fe87:1af0/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 08:00:27:6e:be:14 brd ff:ff:ff:ff:ff:ff
inet 10.0.3.15/24 brd 10.0.3.255 scope global dynamic eth1
valid_lft 85696sec preferred_lft 85696sec
inet6 fe80::a00:27ff:fe6e:be14/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 08:00:27:b0:64:83 brd ff:ff:ff:ff:ff:ff
inet 192.168.156.13/24 brd 192.168.156.255 scope global eth2
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:feb0:6483/64 scope link
valid_lft forever preferred_lft forever
5: vrrp.51@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:33 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.101/32 scope global vrrp.51
valid_lft forever preferred_lft forever
6: vrrp.52@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:34 brd ff:ff:ff:ff:ff:ff
7: vrrp.53@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:35 brd ff:ff:ff:ff:ff:ff
8: vrrp1.51@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:33 brd ff:ff:ff:ff:ff:ff
inet 192.168.156.101/32 scope global vrrp1.51
valid_lft forever preferred_lft forever
9: vrrp1.52@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:34 brd ff:ff:ff:ff:ff:ff
10: vrrp1.53@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN qlen 1000
link/ether 00:00:5e:00:01:35 brd ff:ff:ff:ff:ff:ff
7、 总结
之前我们用keepalived做集群时一般使用它构建服务器主从,也就是只有一个vip,并且这个vip只是在主节点上,当主节点宕机时,vip漂移到从节点上,从而实现高可用。但随着业务的发展,单个节点随之成为业务的性能瓶颈,及时我们使用的负载均衡再强大,服务器配置再高,也不可能单节点抗住所有流量。而通过这种方案,在keepalived的主从基础上扩展一下,通过配置多个vip,每个keepalived节点互为主从,正常情况下保证所有服务器都能拥有一个vip,然后通过dns负载均衡技术,将业务流量转发到每个vip。从而在一定程度上避免了单服务器的性能瓶颈。
通过keepalived实现多主集群方案的更多相关文章
- MySQL集群系列2:通过keepalived实现双主集群读写分离
在上一节基础上,通过添加keepalived实现读写分离. 首先关闭防火墙 安装keepalived keepalived 2台机器都要安装 rpm .el6.x86_64/ 注意上面要替换成你的内核 ...
- Redis 集群方案
根据一些测试整理出来的一份方案(转自http://www.cnblogs.com/lulu/): 1. Redis 性能 对于redis 的一些简单测试,仅供参考: 测试环境:Redhat6.2 , ...
- Redis集群方案介绍
由于Redis出众的性能,其在众多的移动互联网企业中得到广泛的应用.Redis在3.0版本前只支持单实例模式,虽然现在的服务器内存可以到100GB.200GB的规模,但是单实例模式限制了Redis没法 ...
- (转)Redis 集群方案
根据一些测试整理出来的一份方案: 1. Redis 性能 对于redis 的一些简单测试,仅供参考: 测试环境:Redhat6.2 , Xeon E5520(4核)*2/8G,1000M网卡 Redi ...
- Redis集群方案
Redis集群方案 前段时间搞了搞Redis集群,想用做推荐系统的线上存储,说来挺有趣,这边基础架构不太完善,因此需要我们做推荐系统的自己来搭这个存储环境,就自己折腾了折腾.公司所给机器的单机性能其实 ...
- Redis集群方案怎么做?大牛给你介绍五种方案!
Redis集群方案 Redis数据量日益增大,而且使用的公司越来越多,不仅用于做缓存,同时趋向于存储这块,这样必促使集群的发展,各个公司也在收集适合自己的集群方案,目前行业用的比较多的是下面几种集群架 ...
- Redis集群方案怎么做?
转载自:https://www.jianshu.com/p/1ecbd1a88924 Redis集群方案 Redis数据量日益增大,而且使用的公司越来越多,不仅用于做缓存,同时趋向于存储这块,这样必促 ...
- Redis 集群方案介绍
由于Redis出众的性能,其在众多的移动互联网企业中得到广泛的应用.Redis在3.0版本前只支持单实例模式,虽然现在的服务器内存可以到100GB.200GB的规模,但是单实例模式限制了Redis没法 ...
- Redis集群方案收集
说明: 如果不考虑客户端分片去实现集群,那么市面上基本可以说就三种方案最成熟,它们分别如下所示: 系统 贡献者 是否官方Redis实现 编程语言 Twemproxy Twitter 是 C Redis ...
随机推荐
- 当 “HTTP” 先生遇上“S”小姐
情人节的晚上,天空中淅淅沥沥的下着带有些寒意的小雨.HTTP 先生孤零零的坐在咖啡厅中,对着面前的电脑发呆.他有意的屏蔽掉了周边情侣们的窃窃私语,这对单身的他来说是狗粮,也是一阵阵伤害.这时,咖啡厅的 ...
- .netcore 模块积累
最全的 demo https://github.com/XiaoFaye/netcore-samples http://files.cnblogs.com/files/kellynic/practic ...
- 1.2环境安装「深入浅出ASP.NET Core系列」
官网 在介绍安装环境之前,先介绍周边信息,比如微软net官网. https://www.microsoft.com/net 这个网站是学习微软技术栈比较权威的地方,包括环境下载,学习,架构,文档,社区 ...
- 在线生成二维码的API接口
现在很多大网站都有这样的一个功能,使用手机扫描一下网页上的二维码便可快速在手机上访问网站.想要实现这样的功能其实很简单,下面麦布分享几个在线生成网址二维码的API接口.都是采用http协议接口,无需下 ...
- 数据结构——Java实现单链表
一.分析 单链表是一种链式存取的数据结构,用一组地址任意的存储单元存放线性表中的数据元素.链表中的数据是以结点来表示的,每个结点由元素和指针构成.在Java中,我们可以将单链表定义成一个类,单链表的基 ...
- JAVA IO流编程 实现文件的写入、写出以及拷贝
一.流的概念 流:数据在数据源(文件)和程序(内存)之间经历的路径. 输入流:数据从数据源(文件)到程序(内存)的路径. 输出流:数据从程序(内存)到数据源(文件)的路径. 以内存为参照,如果数据向内 ...
- 使用 MSIX 打包 DotNetCore 3.0 客户端程序
如何你希望你的 WPF 程序能够以 Windows 的保护机制保护起来,不被轻易反编译的话,那么这篇文章应该能帮到你. 介绍 MSIX 是微软于去年的 Windows 开发者日峰会 上推出的全新应用打 ...
- 15个常用的javaScript正则表达式
1 用户名正则 //用户名正则,4到16位(字母,数字,下划线,减号) ,}$/; //输出 true console.log(uPattern.test("iFat3")); 2 ...
- 纯CSS编写汉克狗
1,CSS中原生的变量定义语法是:--*,变量使用语法是:var(--*),其中*表示我们的变量名称:在CSS变量命名中,不能包含$,[,^,(,%等字符,普通字符局限在只要是“数字[0-9]”“字母 ...
- Linux(CentOS 7)安装测试mysql5.6服务
1.rpm -qa | grep mysql,查看原系统中是否有已经安装得mysql. 注:centos7系统在安装完成后,未安装mysql任何版本. 2. rpm -e --nodeps mysql ...
