IPSec的链路和设备备份
链路备份的IPSec VPN和设备备份的IPSec VPN:
首先实验的是链路备份的 IPSec VPN,下面是实验拓扑: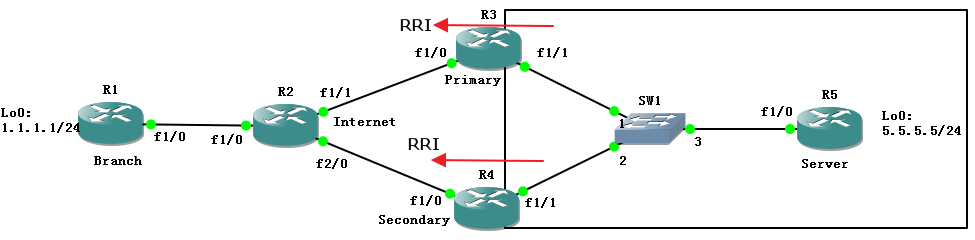
IP地址配置:
R1(Branch):
Branch(config-if)#ip add 12.1.1.1 255.255.255.0
Branch(config-if)#no shu
Branch(config-if)#int lo0
Branch(config-if)#ip add 1.1.1.1 255.255.255.0
Branch#conf t
Branch(config)#ip route 0.0.0.0 0.0.0.0 12.1.1.2
R2(Internet):
R2(config)#int f1/0
R2(config-if)#ip add 12.1.1.2 255.255.255.0
R2(config-if)#no shu
R2(config)#int f1/1
R2(config-if)#ip add 23.1.1.2 255.255.255.0
R2(config-if)#no shu
R2(config-if)#int f2/0
R2(config-if)#ip add 24.1.1.2 255.255.255.0
R2(config-if)#no shu
R2(config-if)#int lo0
R2(config-if)#ip add 2.2.2.2 255.255.255.0
R3(Primary):
R3(config)#int f1/0
R3(config-if)#ip add 23.1.1.3 255.255.255.0
R3(config-if)#no shu
R3(config-if)#int f1/1
R3(config-if)#ip add 10.1.1.3 255.255.255.0
R3(config-if)#no shu
R3(config-if)#int l0
R3(config-if)#ip add 3.3.3.3 255.255.255.0
R3(config-if)#end
R3(config)#router os 1
R3(config-router)#router-id 3.3.3.3
R3(config-router)#net 10.1.1.0 0.0.0.255 a 0
Primary(config)#ip route 0.0.0.0 0.0.0.0 23.1.1.2
R4(Secondary):
R4(config)#int f1/0
R4(config-if)#ip add 24.1.1.4 255.255.255.0
R4(config-if)#no shu
R4(config-if)#int f1/1
R4(config-if)#ip add 10.1.1.4 255.255.255.0
R4(config-if)#no shu
R4(config-if)#int l0
R4(config-if)#ip add 4.4.4.4 255.255.255.0
R4(config-if)#router os 1
R4(config-router)#router-id 4.4.4.4
R4(config-router)#net 10.1.1.0 0.0.0.255 a 0
R4(config)#ip route 0.0.0.0 0.0.0.0 24.1.1.2
R5(Server):
R5(config)#int f1/0
R5(config-if)#ip add 10.1.1.5 255.255.255.0
R5(config-if)#no shu
R5(config-if)#int l0
R5(config-if)#ip add 5.5.5.5 255.255.255.0
R5(config-if)#router os 1
R5(config-router)#router-id 5.5.5.5
R5(config-router)#net 0.0.0.0 255.255.255.255 a 0
链路备份的IPSec VPN配置:
Branch(config)#crypto is po 10
Branch(config-isakmp)#authentication pre-share
Branch(config-isakmp)#exi
Branch(config)#crypto isakmp key 0 cisco address 23.1.1.3
Branch(config)#crypto isakmp key 0 cisco address 24.1.1.4 //密钥可以不一样
Branch(config)#crypto isakmp keepalive 10 periodic //启用DPD
Branch(config)#ip access-list extended vpn
Branch(config-ext-nacl)#permit ip 1.1.1.0 0.0.0.255 5.5.5.0 0.0.0.255
Branch(config-ext-nacl)#exi
Branch(config)#crypto ipsec transform-set trans esp-des esp-md5-hmac
Branch(cfg-crypto-trans)#exi
Branch(config)#crypto map cisco 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Branch(config-crypto-map)#match address vpn
Branch(config-crypto-map)#set peer 23.1.1.3 //先配置23.1.1.3为主用网关,后配置的24.1.1.4为备用的网关
Branch(config-crypto-map)#set peer 24.1.1.4
Branch(config-crypto-map)#set transform-set trans
Branch(config-crypto-map)#int f1/0
Branch(config-if)#crypto map cisco
Primary(config)#crypto isakmp po 10
Primary(config-isakmp)#au pre-share
Primary(config-isakmp)#exi
Primary(config)#crypto isakmp key 0 cisco address 12.1.1.1
Primary(config)#crypto isakmp keepalive 10 periodic //开启DPD
Primary(config)#ip access-list extended vpn
Primary(config-ext-nacl)#permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
Primary(config-ext-nacl)#exi
Primary(config)#crypto ipsec transform-set trans esp-des esp-md5-hmac
Primary(cfg-crypto-trans)#exi
Primary(config)#crypto map cisco 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Primary(config-crypto-map)#match address vpn
Primary(config-crypto-map)#set peer 12.1.1.1
Primary(config-crypto-map)#set transform-set trans
Primary(config-crypto-map)#reverse-route
Primary(config-crypto-map)#set reverse-route tag 10//启用RRI,并解决回包问题
This will remove previously installed VPN routes and SAs
Primary(config-crypto-map)#int f1/0
Primary(config-if)#crypto map cisco
*Apr 23 14:15:21.343: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Primary(config-if)#router os 1
Primary(config-router)#redistribute static route-map RRI subnets
Primary(config-router)#exi
Primary(config)#route-map RR1
Primary(config-route-map)#match tag 10
Primary(config-route-map)#exi
Secondary(config)#crypto isakmp po 10
Secondary(config-isakmp)#authentication pre-share
Secondary(config)#crypto isakmp key 0 cisco address 12.1.1.1
Secondary(config)#exi
Secondary(config)#ip access-list extended vpn
Secondary(config-ext-nacl)#permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
Secondary(config-ext-nacl)#exi
Secondary(config)#crypto isakmp keepalive 10 periodic
Secondary(config)#crypto ipsec transform-set trans esp-des esp-md5-hmac
Secondary(cfg-crypto-trans)#exi
Secondary(config)#crypto map cisco 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Secondary(config-crypto-map)#match address vpn
Secondary(config-crypto-map)#set peer 12.1.1.1
Secondary(config-crypto-map)#set transform-set trans
Secondary(config-crypto-map)#reverse-route
Secondary(config-crypto-map)#set reverse-route tag 10
This will remove previously installed VPN routes and SAs
Secondary(config-crypto-map)#int f1/0
Secondary(config-if)#crypto map cisco
*Apr 23 14:17:47.915: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Secondary(config-if)#router os 1
Secondary(config-router)#redistribute static subnets route-map RRI
Secondary(config-router)#exi
Secondary(config)#route-map RRI
Secondary(config-route-map)#match tag 10
Secondary(config-route-map)#exi
Primary(config)#int f1/0
Primary(config-if)#shu
Secondary#sho crypto en connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 0 26 31 24.1.1.4
2 IPsec DES+MD5 26 0 0 24.1.1.4
1001 IKE SHA+DES 0 0 0 24.1.1.4
这里说一下,当Primary这边的接口down了的话,随着安全关联的消失,反向注入产生的路由也跟随者消失了。还有,链路备份的高可用性IPSec VPN是不支持抢占的。
Server#sho ip ro ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is not set
1.0.0.0/24 is subnetted, 1 subnets
O E2 1.1.1.0 [110/20] via 10.1.1.4, 00:01:22, FastEthernet1/0
现在来做一下设备的备份,设备备份的IPSec VPN(Redundancy VPN):
redundancy VPN主要是使用HSRP来提供设备级别的备份,实验拓扑如下: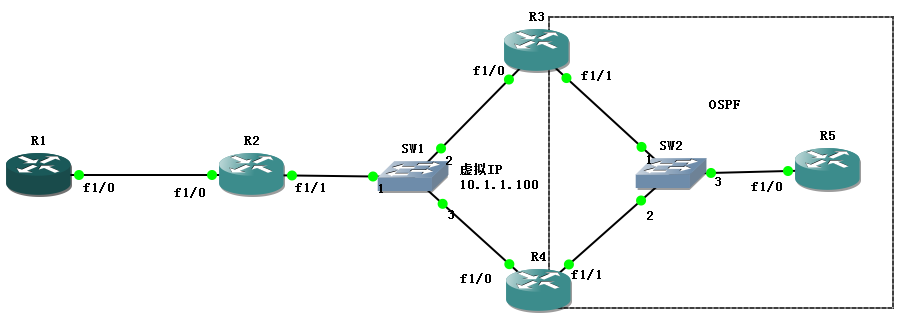
设备IP地址配置:
R1:
interface Loopback0
ip address 1.1.1.1 255.255.255.0
interface FastEthernet1/0
ip address 12.1.1.1 255.255.255.0
duplex auto
speed auto
crypto map cisco
!
ip route 0.0.0.0 0.0.0.0 12.1.1.2
R2:
interface Loopback0
ip address 2.2.2.2 255.255.255.0
!
interface FastEthernet1/0
ip address 12.1.1.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/1
ip address 10.1.1.2 255.255.255.0
duplex auto
speed auto
R3:
interface Loopback0
ip address 3.3.3.3 255.255.255.0
!
interface FastEthernet1/0
ip address 10.1.1.3 255.255.255.0
duplex auto
speed auto
standby 1 ip 10.1.1.100
standby 1 priority 105
standby 1 preempt
standby 1 name cisco
crypto map cisco redundancy cisco
!
!
interface FastEthernet1/1
ip address 20.1.1.3 255.255.255.0
duplex auto
speed auto
!
!
router ospf 1
router-id 3.3.3.3
log-adjacency-changes
redistribute static subnets route-map RRI
network 20.1.1.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 10.1.1.2
!
ip access-list extended vpn
permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
!
route-map RRI permit 10
match tag 10
R4
interface Loopback0
ip address 4.4.4.4 255.255.255.0
!
interface FastEthernet1/0
ip address 10.1.1.4 255.255.255.0
duplex auto
speed auto
standby 1 ip 10.1.1.100
standby 1 preempt
standby 1 name cisco
crypto map cisco
!
!
interface FastEthernet1/1
ip address 20.1.1.4 255.255.255.0
duplex auto
speed auto
!
!
router ospf 1
router-id 4.4.4.4
log-adjacency-changes
redistribute static subnets route-map RRI
network 20.1.1.0 0.0.0.255 area 0
ip route 0.0.0.0 0.0.0.0 10.1.1.2
!
route-map RRI permit 10
match tag 10
interface Loopback0
ip address 5.5.5.5 255.255.255.0
!
interface FastEthernet1/0
ip address 20.1.1.5 255.255.255.0
duplex auto
speed auto
!
router ospf 1
router-id 5.5.5.5
log-adjacency-changes
network 5.5.5.0 0.0.0.255 area 0
network 20.1.1.0 0.0.0.255 area 0
HSRP配置:
R3:
interface FastEthernet1/0
ip address 10.1.1.3 255.255.255.0
duplex auto
speed auto
standby 1 ip 10.1.1.100
standby 1 priority 105
standby 1 preempt
standby 1 name cisco
R4:
interface FastEthernet1/0
ip address 10.1.1.4 255.255.255.0
duplex auto
speed auto
standby 1 ip 10.1.1.100
standby 1 preempt
standby 1 name cisco
crypto map cisco
IPSec VPN配置:
R1:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 10.1.1.100
crypto isakmp keepalive 10 periodic
!
!
crypto ipsec transform-set trans esp-des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 10.1.1.100
set transform-set trans
match address vpn
!
ip access-list extended vpn
permit ip 1.1.1.0 0.0.0.255 5.5.5.0 0.0.0.255
!
R3:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 12.1.1.1
crypto isakmp keepalive 10 periodic
!
!
crypto ipsec transform-set trans esp-des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1.1
set transform-set trans
set reverse-route tag 10
match address vpn
reverse-route static //若没有这个关键字,必须要有IPSec SA才会产生反向路由,主要,active路由器才会产生反向路由
interface FastEthernet1/0
crypto map cisco redundancy cisco //只用redundancy关键字调用HSRP的名字,哪台为活动的路由器就会使用虚拟IP和远端的peer建立IPSec VPN
ip access-list extended vpn
permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
!
Redundancy VPN是支持抢占的,因为HSRP支持抢占(当然前提是要开启preempt)
R4:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 12.1.1.1
crypto isakmp keepalive 10 periodic
!
!
crypto ipsec transform-set trans esp-des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1.1
set transform-set trans
set reverse-route tag 10
match address vpn
reverse-route static
interface FastEthernet1/0
crypto map cisco redundancy cisco
ip access-list extended vpn
permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
R1#ping 5.5.5.5 so 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!.!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 288/523/748 ms
R3#sho cry en conn active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 0 5 5 10.1.1.100
2 IPsec DES+MD5 5 0 0 10.1.1.100
1001 IKE SHA+DES 0 0 0 10.1.1.100
R5#sho ip ro ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is not set
1.0.0.0/24 is subnetted, 1 subnets
O E2 1.1.1.0 [110/20] via 20.1.1.3, 00:23:00, FastEthernet1/0
R3#sho ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 10.1.1.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 10.1.1.2
1.0.0.0/24 is subnetted, 1 subnets
S 1.1.1.0 [1/0] via 12.1.1.1
3.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 3.3.3.0/24 is directly connected, Loopback0
L 3.3.3.3/32 is directly connected, Loopback0
5.0.0.0/32 is subnetted, 1 subnets
O 5.5.5.5 [110/2] via 20.1.1.5, 00:27:56, FastEthernet1/1
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.1.1.0/24 is directly connected, FastEthernet1/0
L 10.1.1.3/32 is directly connected, FastEthernet1/0
20.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 20.1.1.0/24 is directly connected, FastEthernet1/1
L 20.1.1.3/32 is directly connected, FastEthernet1/1
测试一下设备切换:
可以将R3重启reload或者将接口shutdown
R3(config)#int f1/0
R3(config-if)#shu
R4#
*Apr 23 19:21:43.491: %HSRP-5-STATECHANGE: FastEthernet1/0 Grp 1 state Standby -> Active
R1#ping 5.5.5.5 so 1.1.1.1 repeat 1000
Type escape sequence to abort.
Sending 1000, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!!!!!...........!!!!!!!!!!!.!!!!!!.
Success rate is 66 percent (26/39), round-trip min/avg/max = 236/432/644 ms
IPSec的链路和设备备份的更多相关文章
- [杂] 将高版本iTunes备份恢复到低版本iOS设备中
除非开发测试用设备,自用设备不要随便升iOS beta,不要随便升iOS beta,不要随便升iOS beta. 对于升级了高版本iOS的用户,默认情况下重刷低版本iOS时,iTunes不允许向低版本 ...
- Cisco设备自动定时备份配置
前言 当我们管理的网络设备为个位数的时候,手动的把配置通过tftp方式copy出来还是可以的.但是当我们管理几十台甚至上百台(有点夸张,都这个级别了肯定用专业的运维软件或者开发运维平台进行管理)的时候 ...
- 如何使用iMazing编辑iOS设备的备份
乍一看,编辑iPhone或iPad的备份似乎是一个奇怪的命题,但实际上这样做的原因有很多,例如在备份数据损坏时进行修复,又如合并来自不同设备的数据. iMazing对备份文件编辑的支持非常全面,即使备 ...
- 高可用性GRE+IPSEC中心—分支
在实际网络运用中我们时常跑GRE+IPSEC来实现我们中心到分支的远程访问回话,这样以来容易配置,而来可用性高,我们知道L2L无论是链路备份还是设备备份,都不是状态备份,当一个点断掉后,用经过几十秒甚 ...
- linux_rsync定时备份
在linux系统中,需要注意空格使用,有着整体性原则,并且注意大小写问题 Rsync数据同步工具 开源.快速.多功能.可实现全量和增量的本地或远程 具有本地和远程两台主机之间数据快速同步镜像.远程备份 ...
- 《TCP/IP 详解 卷1:协议》第 3 章:链路层
在体系结构中,我们知道:链路层(或数据链路层)包含为共享相同介质的邻居建立连接的协议和方法,同时,设计链路层的目的是为 IP 模块发送和接受 IP 数据报,链路层可用于携带支持 IP 的辅助性协议,例 ...
- Eth-Trunk链路聚合配置
Eth-Trunk概述 Eth-Trunk接口能够实现负载分担.增加带宽和提高可靠性 Eth-Trunk接口把多个物理接口捆绑成一个逻辑接口 Eth-Trunk接口的链路聚合模式 链路聚合模式 应用场 ...
- 配置交换机之间直连链路聚合-LACP模式
组网图形 LACP模式链路聚合简介 以太网链路聚合是指将多条以太网物理链路捆绑在一起成为一条逻辑链路,从而实现增加链路带宽的目的.链路聚合分为手工模式和LACP模式. LACP模式需要有链路聚合控制协 ...
- HCNP Routing&Switching之链路聚合
前文我们了解了MSTP相关话题,回顾清参考https://www.cnblogs.com/qiuhom-1874/p/16268682.html:今天我们来聊一聊链路聚合相关话题: 链路聚合是链路高可 ...
随机推荐
- crontab实践
1.crontab概要 2.crontab使用 3.关键配置信息 3.1如何配置定时任务 4.注意事项 参考 https://www.cnblogs.com/keithtt/p/6946498.htm ...
- codeforce D. Shortest Cycle(floyd求最短环)
题目链接:http://codeforces.com/contest/1206/problem/D 给n个点,如果点a[ i ] &a[ j ] 不为0,则点a[ i ] 和 a[ j ] 直 ...
- 剑指offer 面试题35.复杂链表的复制
时间O(N),空间O(N) /* struct RandomListNode { int label; struct RandomListNode *next, *random; RandomList ...
- Redis04——Redis五大数据类型 key
key keys * 查看当前库的所有键 exists <key> 判断某个键是否存在 type <key> 查看键的类型 del<key> 删除 ...
- Django框架-模型层
Django框架-模型层 一.单表查询之必知必会13条 1.时间字段中的两个关键性参数 create_time = models.DateField() # 年月日 create_time = mod ...
- Linux实现树莓派3B的国密SM9算法交叉编译——(三)国密SM9算法实现
先参考这篇文章 Linux实现树莓派3B的国密SM9算法交叉编译——(二)miracl库的测试与静态库的生成 进行miracl库的交叉编译测试,并生成miracl静态链接库. 这篇文章主要介绍基于mi ...
- HttpServer性能比较
在自己的本子上随便测了下几款HttpServer,环境信息就不贴出来了,主要是比对下差距. 测试内容是输出 text/plain 的 hello, world. 先说结论:Netty > Joo ...
- jquer_shijian 增加初始化 年月日 及 结束时间 年月日
增加了插件 在初始化的时候,控制 年月日,和结束 年月日 $(time_createobj).siblings(".xtw_budget_userdatafn_hide").shi ...
- 一文搞懂vim复制粘贴
转载自本人独立博客https://liushiming.cn/2020/01/18/copy-and-paste-in-vim/ 概述 复制粘贴是文本编辑最常用的功能,但是在vim中复制粘贴还是有点麻 ...
- blg_统考,打印准考证 网页代码!
<html xmlns="http://www.w3.org/1999/xhtml"><head> <title>打印准考证</title ...
