BUGKU (Take the maze)
首先进行查壳,没有壳。
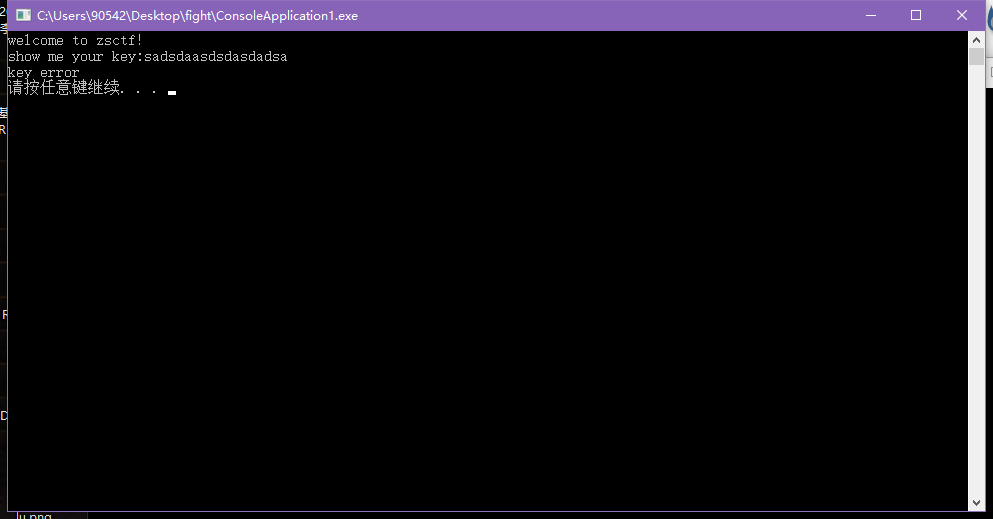
随便输入,看程序执行信息。随意输入字符串,提示key error
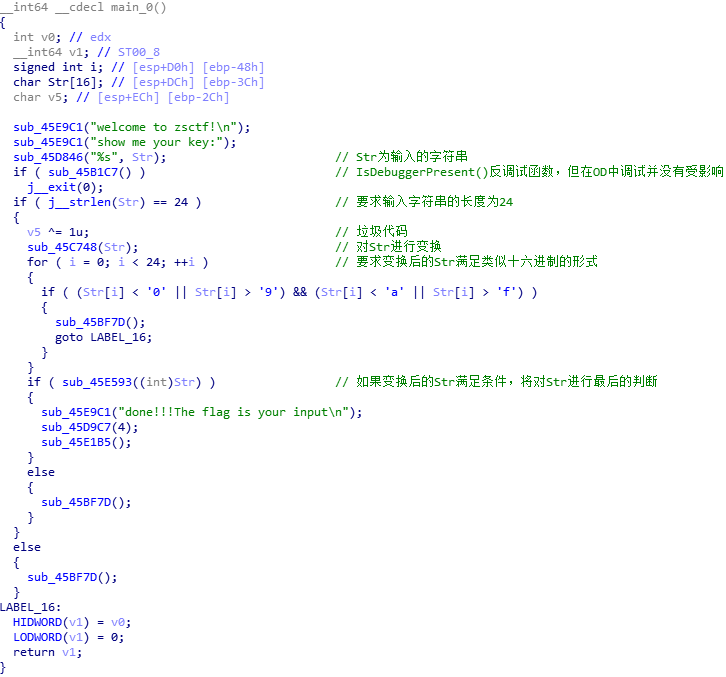
放到IDA中打开,在左侧函数窗口中找到main0,F5反编译,进行分析。具体已在分析在图中标识。
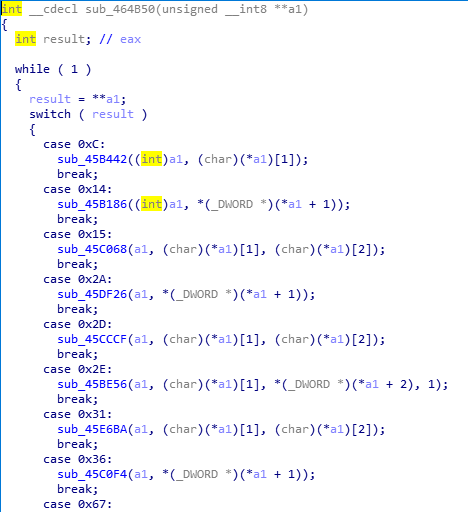
关于main函数的逻辑是很容易理解的,但是接下来可就犯难了。我首先是打开45C748(对Str进行变换的函数)。如下图,看起来应该是在进行对Str变换之前,做一些初始化工作。

整个过程不难理解,但当我打开45DCD3函数时,就一头雾水了。
这没得分析(后来才知道是VM处理过的),于是打开OD输入012345678901234567891234,试试看(之前做过一个逆向题,印象深刻,那也是对字符串进行变换的函数,再IDA中查看,根本看不明白,拿到OD里面一跑,才知道,原来就是个base64编码啊。╮(╯▽╰)╭)经过变换,如下图所示。
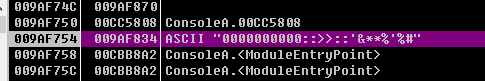
我做过的逆向题不多,根据以往的经验,在IDA中看不懂,或者是不是很理解的情况下,在OD中跟进调试一下,往往会有所收获。所以就跟进了这个函数。结果,不会就是不会,一点办法都没有。╮(╯_╰)╭。之后,也是在调试的时候偶然把上图的字符串(即0000000000::>>::'&**%'%#)当作输入,进行调试,结果发现返回的竟是012345678901234567891234。当时没有细想,没感觉有什么大不了的。后来才猛然间醒悟,如果知道了正确的输入,先输入进去,得到加密后的字符串,这不就是flag了吗?于是有了往下做下去的动力。
接着分析。
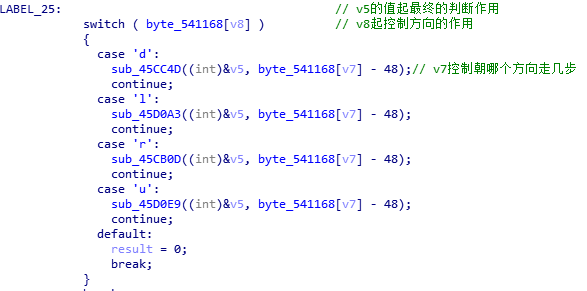
再来打开其中的45CC4D函数。(其中的注释是后来看了别人的WP加的)。

之前做过类似的迷宫逆向题,知道得有一张“地图”,可找了半天也没发现。再者这个函数里面套函数,这种return,实在绕的头疼,最后还是看了别人的WP,找了找思路。原来得在if语句这里,写一个IDC内置脚本(第一次接触)。
这个脚本很容易理解。然后的话,四个函数里面的数组都是不一样的,然后一个个把Dword中的地址改掉,dump出“地图”来就行了。
auto i;
for(i=;i<*;i++){
if(Dword(0x540548+*i)^Dword(0x540068+*i))
Message("0,");
else Message("1,");
}
我用的python,它处理字符串不能够直接修改某个位置上的值,所以用C写会舒服一些。
up='0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,0,1,0,0,0,1,0,0,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,1,1,1,0,0,0,1,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,1,1,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,1,1,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,1,1,1,1,1,1,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,1,1,1,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0'.replace(',','')
down='1,1,0,1,0,0,0,1,0,0,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,1,1,1,0,0,0,1,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,1,1,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,1,1,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,1,1,1,1,1,1,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,1,1,1,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0'.replace(',','')
left='0,1,0,0,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,0,1,0,0,0,1,0,0,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,1,1,1,0,0,0,1,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,1,1,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,1,1,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,1,1,1,1,1,1,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,1,1,1,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,1,1'.replace(',','')
right='0,0,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,0,1,0,0,0,1,0,0,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,1,1,1,0,0,0,1,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,1,1,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,1,1,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,1,1,1,1,1,1,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,1,1,1,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,1,1,1,0'.replace(',','')
tmp='~`-.'
for i in range(len(up)):
if i%26==0:
print '\n'
if up[i]=='':
tmp=tmp.replace('~','U')
if down[i]=='':
tmp=tmp.replace('`','D')
if left[i]=='':
tmp=tmp.replace('-','L')
if right[i]=='':
tmp=tmp.replace('.','R')
print tmp+' ',
tmp='~`-.'
最后在画图里面打开对应着地图,把路线画出来。
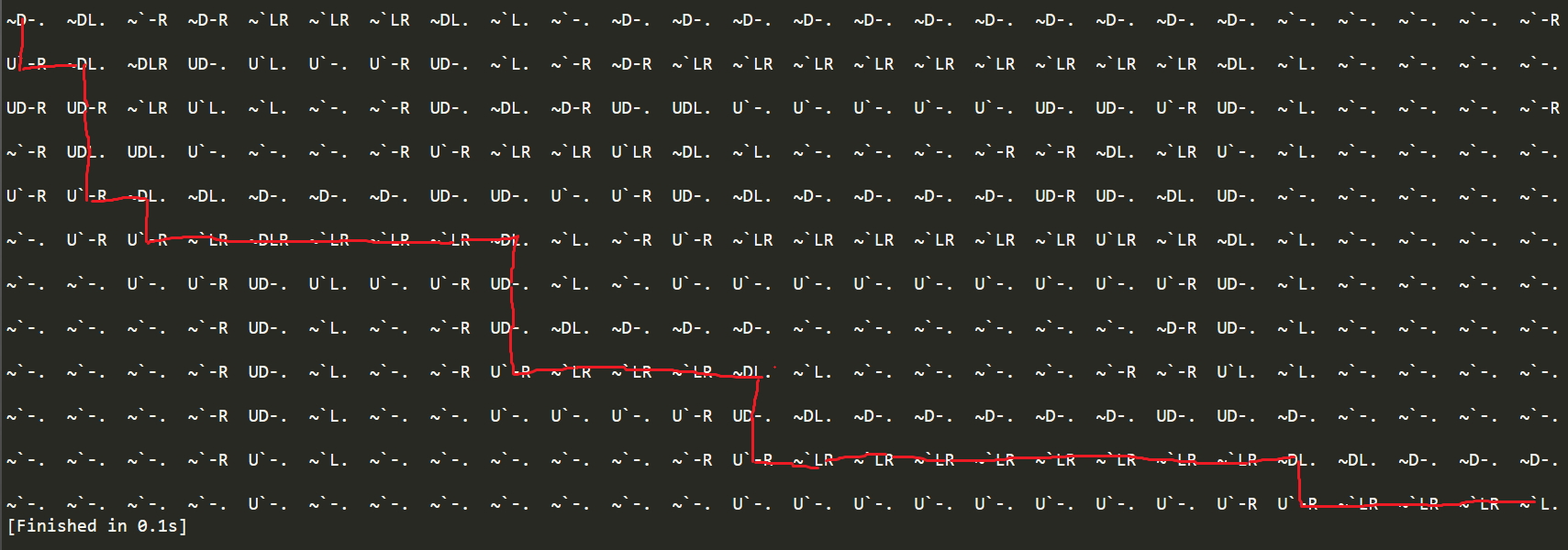
0-d
2-l
3-r
4-u
06260826062b0829072e0629
然后按照之前的想法,把06260826062b0829072e0629输进去,得到加密后的字符串,这个字符串再重新输入回去,成功,如下图。
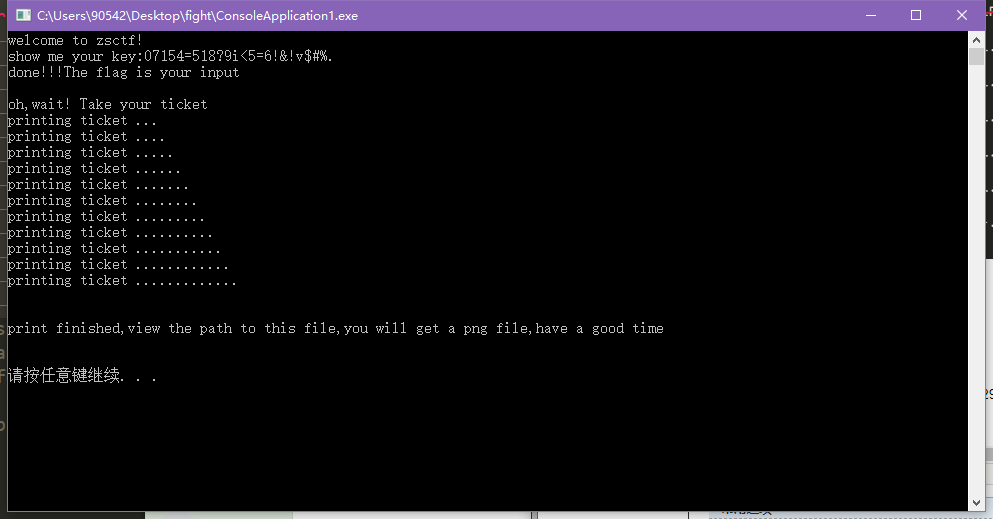
给了张二维码,说是最终flag要加作者的名字。到此结束。
最后感觉这个题,自己感觉还是挺有趣的,其实我如果之前接触过IDC的话,不看别人的WP也会自己做出来的。
BUGKU (Take the maze)的更多相关文章
- 【bugku】【ZSCTF】【迷宫RE】Take The Maze WriteUp
Take The Maze 首先拿进PEID里查一下有没有壳: 无壳,果断拖进IDA.可是Graph View中找不到主程序的位置,在函数表里寻找主函数: 函数太多阻扰了我们找到主程序,运行一下程序找 ...
- bugku 逆向 take the maze
看到如果判断正确之后 会生成一个png文件 直接用idc脚本生成: auto v,begin,end,dexbyte; v = fopen("flag.png", "wb ...
- Backtracking algorithm: rat in maze
Sept. 10, 2015 Study again the back tracking algorithm using recursive solution, rat in maze, a clas ...
- (期望)A Dangerous Maze(Light OJ 1027)
http://www.lightoj.com/volume_showproblem.php?problem=1027 You are in a maze; seeing n doors in fron ...
- 1204. Maze Traversal
1204. Maze Traversal A common problem in artificial intelligence is negotiation of a maze. A maze ...
- uva705--slash maze
/*这道题我原本是将斜线迷宫扩大为原来的两倍,但是在这种情况下对于在斜的方向上的搜索会变的较容易出错,所以参考了别人的思路后将迷宫扩展为原来的3倍,这样就变成一般的迷宫问题了*/ #include&q ...
- HDU 4048 Zhuge Liang's Stone Sentinel Maze
Zhuge Liang's Stone Sentinel Maze Time Limit: 10000/4000 MS (Java/Others) Memory Limit: 32768/327 ...
- Borg Maze(MST & bfs)
Borg Maze Time Limit: 1000MS Memory Limit: 65536K Total Submissions: 9220 Accepted: 3087 Descrip ...
- poj 3026 bfs+prim Borg Maze
Time Limit: 1000MS Memory Limit: 65536K Total Submissions: 9718 Accepted: 3263 Description The B ...
随机推荐
- Struct2的简单的CRUD配置和使用
1. 首先是Struct2使用的jar包,可以在官网下载https://struts.apache.org/ ,其中包只要下面这些就够用了. 或者点击下面链接下载 链接:https://pan.b ...
- jQuery和vue 设置ajax全局请求
一个很常见的问题,如果用户登录网站session过期,需要用户返回登录页面重新登录. 如果是http请求可以在后台设置拦截器,统一拦截并跳转.但是ajax方法并不能通过后台直接跳转. 所以我们可以写一 ...
- Chef 组件
Chef是一家自动化公司.自2008年成立以来,我们一直在将开发人员和系统管理员与我们的同名产品Chef Infra联系在一起.多年来,我们所说的自动化已经扩展了.今天,Chef为基础设施和应用程序提 ...
- TTTTTTTTTTTTTTTT hdu 5510 Bazinga 字符串+哈希
Bazinga Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 65536/65536 K (Java/Others)Total Sub ...
- CCPC-Wannafly & Comet OJ 夏季欢乐赛(2019)H
题面 被神葱安利安利了本题. 我们贪心的想,如果有那么一坨相等的学号,那么肯定是保留一个人学号不变,其余的再推到学号+1的位置(准备与那个位置的其他人合并)处理. 虽然a[i]可大至1e18,不过如果 ...
- sh_14_字符串定义和遍历
sh_14_字符串定义和遍历 str1 = "hello python" str2 = '我的外号是"大西瓜"' print(str2) print(str1[ ...
- 微信小程序_(案例)简单中国天气网首页
Demo:简单中国天气网首页 Page({ data:{ name:"CynicalGary", temp:"4", low:"-1°C", ...
- Linux-expect脚本-编写一个expect脚本
1.声明expect #!/usr/bin/expect -f 2.设置超时时间,获取参数 set ip [lindex $argv 0 ] //接收第一个参数,并设置IP set password ...
- web 新能优化
网上的东西太多了都是搜来的东西 留着自己看吧! 摘自 :http://www.cnblogs.com/50614090/archive/2011/08/19/2145620.html 打开网站慢现状分 ...
- Spring Cloud Feign声明式服务调用(转载)+遇到的问题
转载:原文 总结: 1.pom添加依赖 2.application中填写正确的eureka配置 3.启动项中增加注解 @EnableFeignClients 4.填写正确的调用接口 通过原文使用Fei ...
