Populating Next Right Pointers in Each Node
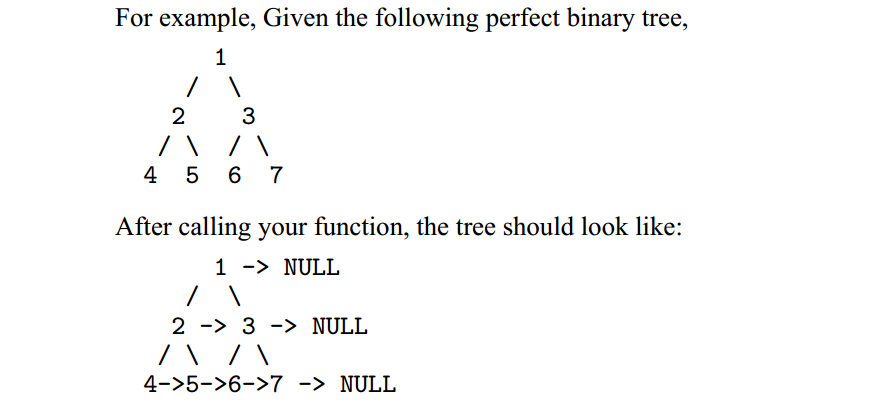
这题代码简单,不过不容易想到。
void connect(TreeLinkNode *root)
{
if (root == nullptr ||root->left==nullptr)return; root->left->next = root->right; //关键
if (root->next != nullptr)
root->right->next = root->next->left; connect(root->left);
connect(root->right); }
Populating Next Right Pointers in Each Node的更多相关文章
- Leetcode 笔记 117 - Populating Next Right Pointers in Each Node II
题目链接:Populating Next Right Pointers in Each Node II | LeetCode OJ Follow up for problem "Popula ...
- Leetcode 笔记 116 - Populating Next Right Pointers in Each Node
题目链接:Populating Next Right Pointers in Each Node | LeetCode OJ Given a binary tree struct TreeLinkNo ...
- [LeetCode] Populating Next Right Pointers in Each Node II 每个节点的右向指针之二
Follow up for problem "Populating Next Right Pointers in Each Node". What if the given tre ...
- [LeetCode] Populating Next Right Pointers in Each Node 每个节点的右向指针
Given a binary tree struct TreeLinkNode { TreeLinkNode *left; TreeLinkNode *right; TreeLinkNode *nex ...
- LEETCODE —— Populating Next Right Pointers in Each Node
Populating Next Right Pointers in Each Node Given a binary tree struct TreeLinkNode { TreeLinkNode * ...
- LeetCode - Populating Next Right Pointers in Each Node II
题目: Follow up for problem "Populating Next Right Pointers in Each Node". What if the given ...
- 【leetcode】Populating Next Right Pointers in Each Node II
Populating Next Right Pointers in Each Node II Follow up for problem "Populating Next Right Poi ...
- 【leetcode】Populating Next Right Pointers in Each Node
Populating Next Right Pointers in Each Node Given a binary tree struct TreeLinkNode { TreeLinkNode * ...
- 【leetcode】Populating Next Right Pointers in Each Node I & II(middle)
Given a binary tree struct TreeLinkNode { TreeLinkNode *left; TreeLinkNode *right; TreeLinkNode *nex ...
- 29. Populating Next Right Pointers in Each Node && Populating Next Right Pointers in Each Node II
Populating Next Right Pointers in Each Node OJ: https://oj.leetcode.com/problems/populating-next-rig ...
随机推荐
- easyUI API(version 1.5)
不分先后,只做记录. jquery+easyui培训文档下载地址: 链接: https://pan.baidu.com/s/1dFgFXk9 密码: jj5d 1 easyui-draggable(拖 ...
- 【CSU 1556】Pseudoprime numbers
题 Description Jerry is caught by Tom. He was penned up in one room with a door, which only can be op ...
- opencv笔记4:模板运算和常见滤波操作
time:2015年10月04日 星期日 00时00分27秒 # opencv笔记4:模板运算和常见滤波操作 这一篇主要是学习模板运算,了解各种模板运算的运算过程和分类,理论方面主要参考<图像工 ...
- hihocoder #1034 毁灭者问题
传送门 时间限制:10000ms 单点时限:1000ms 内存限制:256MB 描述 在 Warcraft III 之冰封王座中,毁灭者是不死族打三本后期时的一个魔法飞行单位. 毁灭者的核心技能之一, ...
- 初学JDBC,最简单示例
一.下载相应数据库驱动jar包,添加到项目中 二.注册驱动,数据库驱动只加入到classpath中是还不行的,还要在使用的时候注册一下,就像安装驱动软件,只拷贝到硬盘还不行,需要安装一下 Driver ...
- 一段代码了解Java中char和int的转换
题目要求: 将输入的大写字母转成对应小写的后5个,如A转换后为f:如果转换后大于z则从a重新计,即多出1就转成a,多出2就转成b以此类推. Java代码: ```java private static ...
- JavaScript 上万关键字瞬间匹配——借助Hash表快速匹配
来源: http://www.cnblogs.com/index-html/archive/2013/04/17/js_keyword_match.html http://www.etherdream ...
- dll劫持技术
DLL劫持技术当一个可执行文件运行时,Windows加载器将可执行模块映射到进程的地址空间中,加载器分析可执行模块的输入表,并设法找出任何需要的DLL,并将它们映射到进程的地址空间中. DLL劫持原理 ...
- 行为Behavior的使用
原文地址:http://www.it610.com/article/4918541.htm 行为就是继承yii\base\behavior,可以绑定到任意yii\base\compent实例上,然后这 ...
- IIS负载均衡-Application Request Route详解第二篇:创建与配置Server Farm(转载)
IIS负载均衡-Application Request Route详解第二篇:创建与配置Server Farm 自从本系列发布之后,收到了很多的朋友的回复!非常感谢,同时很多朋友问到了一些问题,有些问 ...
