weblogic解密工具
import org.bouncycastle.jce.provider.BouncyCastleProvider;
import sun.misc.BASE64Decoder; import javax.crypto.*;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.PBEKeySpec;
import javax.crypto.spec.PBEParameterSpec;
import javax.crypto.spec.SecretKeySpec;
import java.io.FileInputStream;
import java.io.IOException;
import java.io.InputStream;
import java.security.InvalidAlgorithmParameterException;
import java.security.InvalidKeyException;
import java.security.NoSuchAlgorithmException;
import java.security.Security;
import java.security.spec.InvalidKeySpecException; public class WebLogicPasswordDecryptor { public static void main(String args[]) throws IOException, NoSuchPaddingException, NoSuchAlgorithmException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException, InvalidKeySpecException, InvalidAlgorithmParameterException { Security.addProvider(new BouncyCastleProvider());
String serializedSystemIniPath = args[0];
String ciphertext = args[1];
String cleartext = ""; if (ciphertext.startsWith("{AES}")){
ciphertext = ciphertext.replaceAll("^[{AES}]+", "");
cleartext = decryptAES(serializedSystemIniPath,ciphertext);
} else if (ciphertext.startsWith("{3DES}")){
ciphertext = ciphertext.replaceAll("^[{3DES}]+", "");
cleartext = decrypt3DES(serializedSystemIniPath, ciphertext);
} System.out.println(cleartext);
} public static String decryptAES(String SerializedSystemIni, String ciphertext) throws NoSuchAlgorithmException, InvalidKeySpecException, NoSuchPaddingException, InvalidAlgorithmParameterException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException, IOException { byte[] encryptedPassword1 = new BASE64Decoder().decodeBuffer(ciphertext);
byte[] salt = null;
byte[] encryptionKey = null; String key = "0xccb97558940b82637c8bec3c770f86fa3a391a56"; char password[] = new char[key.length()]; key.getChars(0, password.length, password, 0); FileInputStream is = new FileInputStream(SerializedSystemIni);
try {
salt = readBytes(is); int version = is.read();
if (version != -1) {
encryptionKey = readBytes(is);
if (version >= 2) {
encryptionKey = readBytes(is);
}
}
} catch (IOException e) { } SecretKeyFactory keyFactory = SecretKeyFactory.getInstance("PBEWITHSHAAND128BITRC2-CBC"); PBEKeySpec pbeKeySpec = new PBEKeySpec(password, salt, 5); SecretKey secretKey = keyFactory.generateSecret(pbeKeySpec); PBEParameterSpec pbeParameterSpec = new PBEParameterSpec(salt, 0); Cipher cipher = Cipher.getInstance("PBEWITHSHAAND128BITRC2-CBC");
cipher.init(Cipher.DECRYPT_MODE, secretKey, pbeParameterSpec);
SecretKeySpec secretKeySpec = new SecretKeySpec(cipher.doFinal(encryptionKey), "AES"); byte[] iv = new byte[16];
System.arraycopy(encryptedPassword1, 0, iv, 0, 16);
int encryptedPasswordlength = encryptedPassword1.length - 16 ;
byte[] encryptedPassword2 = new byte[encryptedPasswordlength];
System.arraycopy(encryptedPassword1, 16, encryptedPassword2, 0, encryptedPasswordlength);
IvParameterSpec ivParameterSpec = new IvParameterSpec(iv);
Cipher outCipher = Cipher.getInstance("AES/CBC/PKCS5Padding");
outCipher.init(Cipher.DECRYPT_MODE, secretKeySpec, ivParameterSpec); byte[] cleartext = outCipher.doFinal(encryptedPassword2); return new String(cleartext, "UTF-8"); } public static String decrypt3DES(String SerializedSystemIni, String ciphertext) throws NoSuchAlgorithmException, InvalidKeySpecException, NoSuchPaddingException, InvalidAlgorithmParameterException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException, IOException { byte[] encryptedPassword1 = new BASE64Decoder().decodeBuffer(ciphertext);
byte[] salt = null;
byte[] encryptionKey = null; String PW = "0xccb97558940b82637c8bec3c770f86fa3a391a56"; char password[] = new char[PW.length()]; PW.getChars(0, password.length, password, 0); FileInputStream is = new FileInputStream(SerializedSystemIni);
try {
salt = readBytes(is); int version = is.read();
if (version != -1) {
encryptionKey = readBytes(is);
if (version >= 2) {
encryptionKey = readBytes(is);
}
} } catch (IOException e) { } SecretKeyFactory keyFactory = SecretKeyFactory.getInstance("PBEWITHSHAAND128BITRC2-CBC"); PBEKeySpec pbeKeySpec = new PBEKeySpec(password, salt, 5); SecretKey secretKey = keyFactory.generateSecret(pbeKeySpec); PBEParameterSpec pbeParameterSpec = new PBEParameterSpec(salt, 0); Cipher cipher = Cipher.getInstance("PBEWITHSHAAND128BITRC2-CBC");
cipher.init(Cipher.DECRYPT_MODE, secretKey, pbeParameterSpec);
SecretKeySpec secretKeySpec = new SecretKeySpec(cipher.doFinal(encryptionKey),"DESEDE"); byte[] iv = new byte[8];
System.arraycopy(salt, 0, iv, 0, 4);
System.arraycopy(salt, 0, iv, 4, 4); IvParameterSpec ivParameterSpec = new IvParameterSpec(iv);
Cipher outCipher = Cipher.getInstance("DESEDE/CBC/PKCS5Padding");
outCipher.init(Cipher.DECRYPT_MODE, secretKeySpec, ivParameterSpec); byte[] cleartext = outCipher.doFinal(encryptedPassword1);
return new String(cleartext, "UTF-8"); } public static byte[] readBytes(InputStream stream) throws IOException {
int length = stream.read();
byte[] bytes = new byte[length];
int in = 0;
int justread;
while (in < length) {
justread = stream.read(bytes, in, length - in);
if (justread == -1) {
break;
}
in += justread;
}
return bytes;
}
}
代码如上(https://github.com/sevck/WebLogicPasswordDecryptor)
还需要:需要下载一个bcprov-ext-jdk16-146.jar包,拷贝到$PATH\jre\lib\ext\
环境配置:修改C:\Program Files\Java\jdk1.7.0_55\jre\lib\security\java.security文件,增加一行
security.provider.11=org.bouncycastle.jce.provider.BouncyCastleProvider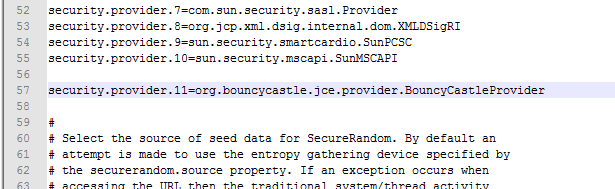
然后就是编译JAVA文件,输入bat和密钥:
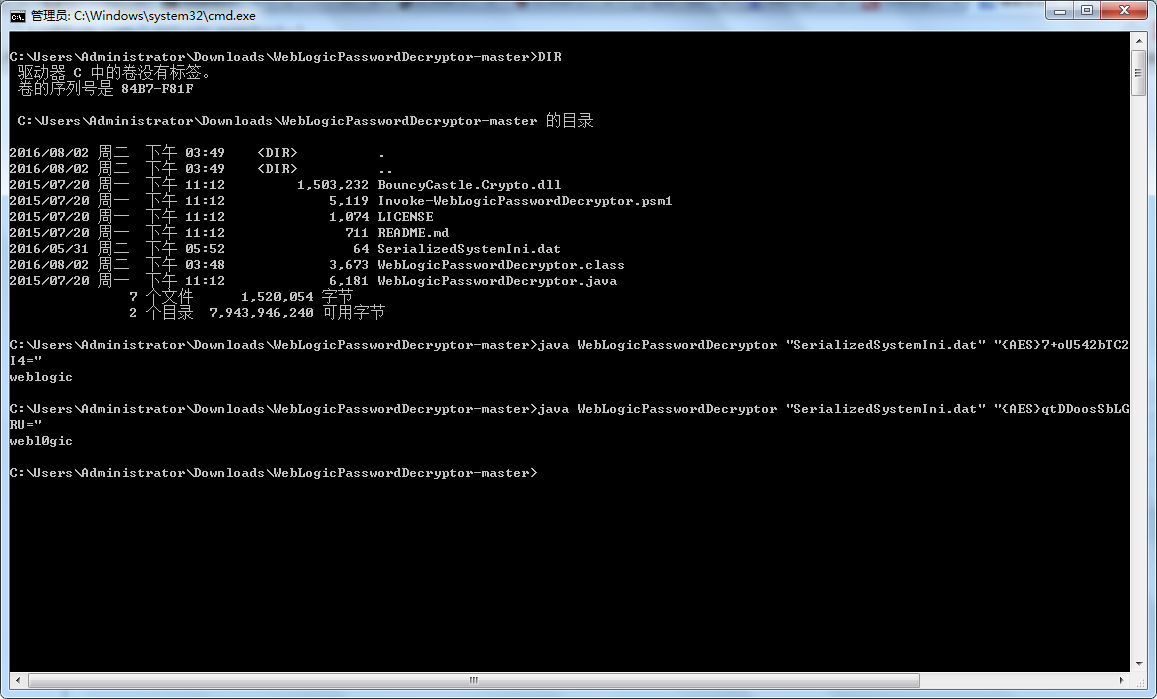
weblogic解密工具的更多相关文章
- 自己写的AES和RSA加密解密工具
package com.sdyy.common.utils; import java.security.Key; import java.security.KeyFactory; import jav ...
- 【Java】通过DES加密和解密工具,对字符串进行加密和解密操作
分享一个非常不错的字符串加密和解密的程序. 可以指定不同的密钥对同一字符串进行不同的加密操作,增强加密性能. Java代码如下: package com.app; import java.securi ...
- RSA加解密工具类RSAUtils.java,实现公钥加密私钥解密和私钥解密公钥解密
package com.geostar.gfstack.cas.util; import org.apache.commons.codec.binary.Base64; import javax.cr ...
- RSA加密和解密工具类
import org.apache.commons.codec.binary.Base64; import javax.crypto.Cipher; import java.security.*; i ...
- 使用jframe编写一个base64加密解密工具
该工具可以使用exe4j来打包成exe工具(如何打包自己百度) 先上截图功能 运行main方法后,会弹出如下窗口 输入密文 然后点击解密,在点格式化 代码分享 package tools;import ...
- Base64加密解密工具类
使用Apache commons codec类Base64进行加密解密 maven依赖 <dependency> <groupId>commons-codec</grou ...
- PHP 神盾解密工具
前两天分析了神盾的解密过程所用到的知识点,昨晚我把工具整理了下,顺便用神盾加密了.这都是昨天说好的,下面看下调用方法吧. 先下载 decryption.zip然后解压放到一个文件夹里,把你要解密的文件 ...
- Java中的AES加解密工具类:AESUtils
本人手写已测试,大家可以参考使用 package com.mirana.frame.utils.encrypt; import com.mirana.frame.constants.SysConsta ...
- Java中的RSA加解密工具类:RSAUtils
本人手写已测试,大家可以参考使用 package com.mirana.frame.utils.encrypt; import com.mirana.frame.utils.log.LogUtils; ...
随机推荐
- SQL Server数据库的三种恢复模式:简单恢复模式、完整恢复模式和大容量日志恢复模式(转载)
SQL Server数据库有三种恢复模式:简单恢复模式.完整恢复模式和大容量日志恢复模式: 1.Simple 简单恢复模式, Simple模式的旧称叫”Checkpoint with truncate ...
- Intent跳转传list集合
先把List<>改为ArrayList<> ArrayList<Good> list=new ArrayList<Good>(); Intent int ...
- 战舰的STM32的SPI的逻辑分析仪设置
- Akka.NET
https://github.com/akkadotnet Akka是什么? 可扩展的分布式实时事务处理 编写正确的并发,容错和可扩展的应用程序是太难了.大多数时候,这是因为我们使用了错误的工具和错误 ...
- jQuery 遍历函数(w3school)
jQuery 遍历函数包括了用于筛选.查找和串联元素的方法. 函数 描述 .add() 将元素添加到匹配元素的集合中. .andSelf() 把堆栈中之前的元素集添加到当前集合中. .childr ...
- Hibernate,JPA注解@OneToMany_Map
用例代码如下: 数据库DDL语句 1,CAT表 create table CAT ( id VARCHAR2(32 CHAR) not null, create_time TIMESTAMP(6), ...
- iOS开发 爱特开发技术bug总结
#pragma mark 每天总结学习两小时 效率 和 每天学习 研究底层 多进去看看 // .................................................... ...
- Winform知识
文档界面 分类: 1.单文档界面应用程序(SDI) 特点: 1.应用程序中SDI的所有窗体都彼此独立 2.多文档界面应用程序(MDI) 特点: 1.每个应用程序中只能有一个MDI父窗体,在父窗体中可以 ...
- SQL-表链接
查询两张表中相匹配的数据显示,不匹配的忽略 1.简单表连接 select * from 表1,表2 where 表1.字段=表2.字段 2.内链接 select * from 表1 inner joi ...
- 这题实在不知道起啥名好了 分类: sdutOJ 2015-06-22 17:17 19人阅读 评论(0) 收藏
这题实在不知道起啥名好了 Time Limit: 1000ms Memory limit: 65536K 有疑问?点这里^_^ 题目描述 懒得想背景故事了,开门见山. 有一个长度为n的整数数列A ...
