PatentTips - Handling shared interrupts in bios under a virtualization technology environment
BACKGROUND
This relates to the operation of software under a virtualization technology (VT) environment.
In a VT environment, such as the Intel VT or AMD Pacifica, an infrastructure may be provided to execute applications in an isolated and protected partition, called the service partition, using the VT capability. The operating system that is visible to end users runs in another partition, called the user partition. For example, a firewall application running in service partition is forwarding the inspected/verified data packets to the user partition. A typical flow of a network packet consist of a) processing and inspection of the network packet by the firewall application in service partition, and b) subsequent forwarding of the network packet to the user partition through the inter-communication channel. The network packet eventually reaches the end-user application running in user partition (as it would happen in a non-VT environment).
In a particular VT environment, Windows CE can be used in the service partition and Windows XP in the user partition. The control flow of boot process can be summarized as follows: a) Basic input/output system passes the control to VT loader; b) VT loader loads itself and prepares the environments for the service partition and user partition for both guests Windows CE and Windows XP respectively; c) VT loader launches Windows CE in service partition, Windows CE completes its boot, and requests VT loader to launch Windows XP; d) VT loader then launches Windows XP and Windows XP starts booting.
During initial stages of a boot process, the XP operating system uses different basic input/output system services as usual. However, the XP operating system is unaware that it is running within a partition isolated and supervised by another entity. Although the control flow of the XP operating system in the VT aware environment remains identical to that of the non-VT environment, the underlying hardware environment differs as far as the device ownership is concerned.
Typically, devices are fully owned by one operating system or guest running in a particular partition (service partition or user partition), and, therefore, are isolated from one another. For example, network controllers may be owned by the Windows CE operating system running in service partition, that handles all incoming and outgoing packets, while storage devices, like hard disks, may be owned by the XP operating system running in user partition. However, some devices, like programmable interrupt controller, may be shared between the two operating systems and are thereby exposed to both guests via the underlying software models.
When an interrupt request is shared by different devices, owned by different guests, in level-triggered interrupt environments, the interrupt may be conveyed to both guests under the assumption that the service routine of both guests will be invoked; the service routine of a particular guest will check the interrupt source for the device it controls; if several devices raise a shared interrupt request simultaneously, all devices will be checked as possible interrupt sources and serviced as necessary; and if a guest detects that the interrupt source for the device it controls, it will service the interrupt or, otherwise, it will ignore the interrupt by sending an end of interrupt.
The basic input/output system (BIOS) installs a default interrupt request handler for all hardware interrupts. If no other entity installs a handler for a particular interrupt request, the basic input/output system default interrupt service routine remains as the only active interrupt handler for the concerned interrupt request. In a shared interrupt environment, when an entity installs a handler for a particular interrupt request, the concerned handler is installed in a chained fashion so that the last installed handler gets control first on the occurrence of the concerned interrupt request and the basic input/output system default interrupt service routine remains at the bottom of the interrupt handler chain. Thus, if no handler claims and services the generated interrupt request, the basic input/output system default interrupt service routine eventually gets control and finds the interrupt request that has been generated, but not claimed and, hence, not serviced by anybody, and disables the request, treating it like a spurious interrupt.
DETAILED DESCRIPTION
Some virtualization technology (VT) capabilities may expect that an interrupt request will be ignored if no owner is found, while the basic input/output system (BIOS) expects that the interrupt request will be disabled if no owner is found. The conflicting requirements regarding the handling of a shared interrupt request gives rise to a situation where the interrupt request may be disabled by the basic input/output system default interrupt service routine if no owner claims it. For example, where an interrupt request is shared by a network controller and a hard disk controller, if the interrupt is generated by the network controller in the virtualized environment when one operating system Windows XP is booting up in the user partition, the interrupt is injected into both operating system guests.
In an environment where one operating system Windows XP is booting in the user partition, the interrupt handlers that are installed by the basic input/output system (or other entities) is invoked. However, the installed interrupt handlers for the hard disk may not service the interrupt because it is not generated by a hard disk operation, but, instead, is generated by a network operation. Even though the other operating system guest Windows CE running in service partition installs a network driver and processes the interrupt as expected, no entity may install the interrupt handler for the network controller during the boot process of the operating system in the user partition. Hence, the basic input/output system default interrupt service routine is invoked as the last entry in the chained interrupt handlers, disabling the interrupt request which may subsequently result in an error while accessing the hard disk and possibly in the failure to boot the system.
This situation may be overcome by installing on demand a custom interrupt service routine. The BIOS may be requested to install the custom interrupt handler as required, allowing the basic input/output system default interrupt service routine to remain unchanged, while allowing installation of a custom interrupt service routine for a particular interrupt request as needed.
Thus, a custom interrupt service routine may be active only for a concerned shared interrupt request between two guests and existing basic input/output system default interrupt service routines will be active for all other interrupt requests. In a non-VT environment, the existing basic input/output system default interrupt service routine remains active for all interrupts as usual. This allows development of a single basic input/output system that works in both VT and non-VT environments, while maintaining the compatibility with all existing environments.
The invocation of a callback method by VT loader is illustrated in FIG. 1. The callback function 26 may be implemented in the basic input/output system in one embodiment. The basic input/output system may also implement the custom interrupt service routine that does not disable the interrupt request if no owner is found, but just issues an end of interrupt and keep the custom interrupt service routine inactive and make it active only when asked by the caller (e.g. VT loader). The basic input/output system may provide the pointer to the callback function when the basic input/output system passes the control to the VT loader (loader of VT environment), as indicated by the arrow adjacent to block 10 in FIG. 1.
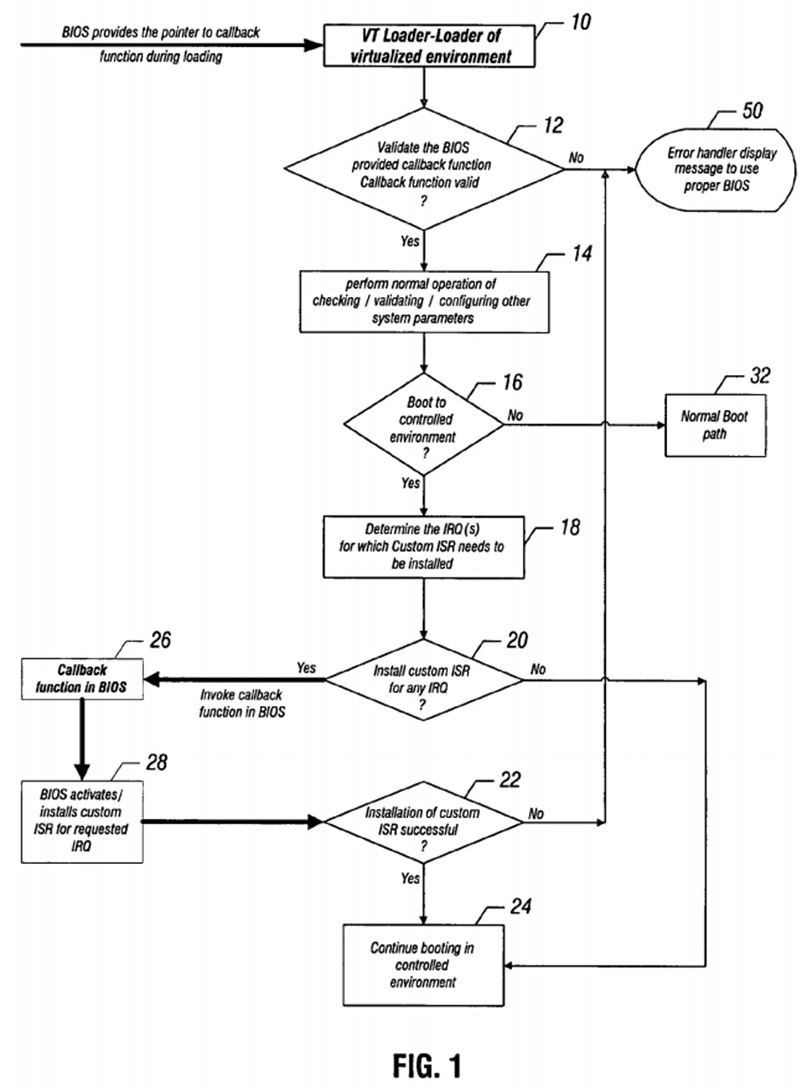
Then in diamond 12, the loader validates the basic input/output system provided callback function. If the function is not valid, an error message may be displayed, as indicated at 50. Otherwise, the loader performs the normal operation of checking and validating and configuring other system parameters as indicated in block 14.
A check at diamond 16 determines whether the boot is to a controlled environment. If not, the normal boot path is followed as indicated in block 32. Otherwise, the loader determines the interrupt request for which a custom interrupt service routine needs to be installed, as indicated in block 18. A check at diamond 20 determines whether to install custom interrupt routines to service any interrupt requests. If so, the callback function is invoked by the loader, as indicated in block 26.
The loader thus uses a callback function to install and activate the custom interrupt service routine, as indicated in block 28, for a particular interrupt request during the boot process. A check at diamond 22 determines whether the custom interrupt service routine installation was successful. If so, booting continues in the controlled environment, as indicated in block 24.
The custom interrupt service routine operates, as indicated in FIG. 2, in accordance with one embodiment. The custom interrupt service routine is invoked when no owner claims or services the generated interrupt request, as indicated in block 36. The pending interrupt request level is then identified, as indicated in block 38. If the custom interrupt service routine is active for the request, as determined in diamond 40, an end of interrupt is issued to the interrupt controller, as indicated in block 44. Then there is an exit from the interrupt service routine.
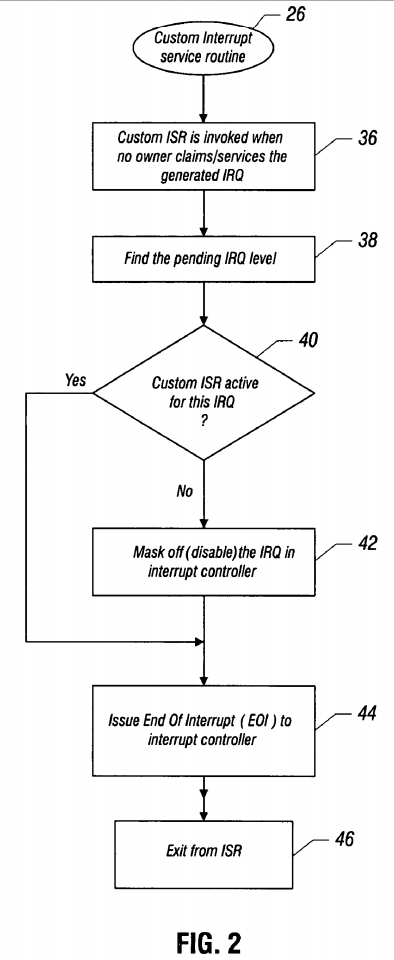
If the custom interrupt service routine is not active, the interrupt request is masked off and disabled in their interrupt controller, as indicated in block 42. Then an end of interrupt is issued to the interrupt controller, as indicated in block 44 and there is an exit from the interrupt service routine.
When active, the interrupt service routine finds the unclaimed interrupt request and whether the custom interrupt service routine has been activated for the unclaimed request. If the custom interrupt service routine has been activated for the unclaimed request, it issues an end of interrupt without disabling the interrupt request, as indicated in FIG. 2, block 44. The loader can also optionally uninstall a custom interrupt service routine when the boot process is complete. The loader may supply a new custom interrupt service routine or use a built-in custom interrupt service routine in the basic input/output system.
In some embodiments, the use of a custom interrupt service routine makes the basic input/output system compatible with various environments, including both VT and non-VT environments. A custom interrupt service routine may be installed on demand and may be installed for one or more interrupt requests. It may also be uninstalled in some embodiments.
SRC=http://www.freepatentsonline.com/7562173.html
PatentTips - Handling shared interrupts in bios under a virtualization technology environment的更多相关文章
- ThinkCentre进入BIOS,设置intel virtualization technology
VMware安装提示cpu虚拟化intel virtualization technology ThinkCentre重启长按F1 按enter,开启intel virtualization tech ...
- React-Native: bios打开VT-x选项
问题: 我在Android Studio新建一个虚拟机的时候出现如图错误: 解决方案:重启电脑,开机的时候不停的按f12(不同的主机不一样),进入bios,然后打开Virtualization Tec ...
- 安装Vmware ESX Server5.5 ——hardware virtualization is not a feature of the cpu or is not enabled in the BIOS
Error信息: hardware virtualization is not a feature of the cpu or is not enabled in the BIOS 解决方案: F2进 ...
- Android Studio创建AVD
Android Studio是专门为Android开发设计的IDE,比Eclipse开发Android更加方便.快捷. 安装Android Studio以后,想运行AVD,出现了下面的错误: 提示没有 ...
- Virtualbox中不能为虚拟机打开一个新任务的原因及解决方法
VirtualBox新建虚拟机时报错,不能为虚拟机打开一个新任务的原因 解决办法如下 1.保证bios里的virtualization technology的选项开启,不同电脑BIOS设置可能会不一样 ...
- 20145212 实验四《Andoid开发基础》
20145212 实验四<Andoid开发基础> 实验内容 安装Android Studio 运行安卓AVD模拟器 使用Android运行出模拟手机并显示自己的学号 实验过程 一.安装An ...
- 移动WebApp利用Chrome浏览器进行调试
详细的请看这个(HBuilder是我长期使用,而且值得支持的国内前端开发编辑器) http://ask.dcloud.net.cn/article/151 http://ask.dcloud.net. ...
- emulator: ERROR: x86 emulation currently requires hardware acceleration!
emulator: ERROR: x86 emulation currently requires hardware acceleration!Please ensure Intel is prop ...
- 在CentOS下源码安装 Xen并搭建Windows虚拟机
前言 首先要感谢xing的帮助,在他的指导之下才完成环境的搭建,本文档的部分内容来自他的文档.另外,还要感谢——互联网. 1. 环境介绍 Linux: CentOS 6.3 Xen: Xe ...
随机推荐
- css3新特性选择器(补充)
1.选择p标签中的第一个字符 p:first-letter{ color:red; font-size:25px; } 2.选择p标签中的第一行 p:first-line{ color:red; fo ...
- 如何监控和解决SQL Server的阻塞(1) (当前阻塞)
1. 什么是"阻塞"? 阻塞是SQL数据库应用"锁"机制的一个副作用.当一个应用请求针对某个数据库对象(例如全表,某行数据, 或者是某个数据页)加锁后,那么这个 ...
- 【Django】缓存
由于Django是动态网站,所以每次请求都会去数据库中进行响应的操作. 当程序访问量大时,耗时必然会更加明显,最简单的解决方案就是使用缓存. Django中的缓存: ==即将某一个view的返回值保存 ...
- Jquery学习总结(1)——Jquery常用代码片段汇总
1. 禁止右键点击 ? 1 2 3 4 5 $(document).ready(function(){ $(document).bind("contextmenu",fun ...
- 洛谷 P1881 绳子对折
P1881 绳子对折 题目描述 FJ 有一个长度为L(1<= L <= 10,000)的绳子. 这个绳子上有N(1 <= N <= 100)个结,包括两个端点. FJ想将绳子对 ...
- 用了Redis里面的map和set
map的操作用 hset,hget等 set的操作有 sadd sismember等 参考下面: http://blog.csdn.net/kwsy2008/article/details/48467 ...
- 怎样扩展Chromium各层的接口
加入新功能时,可能须要添加各层的接口,接口怎样加?必定须要向Chromium的原则看齐. 首先Chromium的模块设计遵循依赖倒置原则,上层模块依赖于低层模块.低层模块不会依赖上层模块的实现. 再者 ...
- VMware虚拟机XP系统安装
转载:http://jingyan.baidu.com/article/54b6b9c00e2f452d593b4762.html
- UML中的用例图
用例图构成:參与者(actor).用例(use case).子系统(subsystem) 关联(Association) 泛化(Inheritance) 就是通常理解的继承关系,子用例和父用例类似,但 ...
- Android使用蓝牙连接adb调试App
使用WiFi连接Android设备调试APP的教程非常多,可是项目中须要使用蓝牙进行通信.所以牵扯使用蓝牙调用adb. 1. 将电脑蓝牙与手机进行配对(控制面板->设备和打印机->加入 ...
