WPScan扫描Wordpress漏洞
一、什么是Wpscan?什么是Wordpres?
1.Wpscan
WPScan是一个扫描WordPress漏洞的黑盒子扫描器,可以扫描出wordpress的版本,主题,插件,后台用户以及爆破后台用户密码等。
2.Wordpress
WordPress是一种使用PHP语言和MySQL数据库开发的博客平台,用户可以在支持PHP和MySQL数据库的服务器上架设属于自己的网站。也可以把 WordPress当作一个内容管理系统(CMS)来使用。WordPress有许多第三方开发的免费模板,安装方式简单易用。
二、Wordpress系统的搭建
1.下载Wordpress
TURNKEYLINUX是linux一站式软件站,在浏览器地址栏输入 https://www.turnkeylinux.org/ 访问官网下载Wordpress
2.Wordpress的安装配置
详细安装配置教程
https://www.cnblogs.com/WangYiqiang/p/9560325.html
注意:在虚拟机中安装Wordpress前需配置好虚拟机网络等设置
Wordpress配置好后如图所示
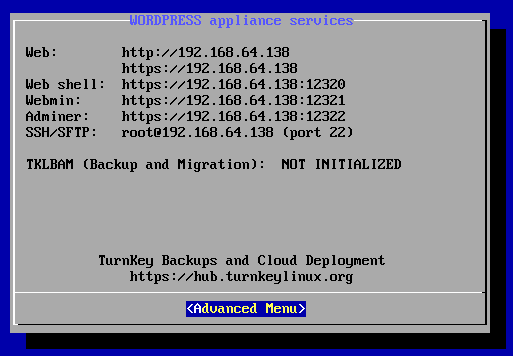
该界面显示了Wordpress应用服务的详细信息,如Web地址,Webshell地址,Webmin地址,PHPMyAdmin的地址和端口号以及SSH/SFTP地址和端口号。
出现此界面表明WordPress Turnkey Linux 搭建完成,可以使用。
三、使用Wpscsn对WordPress进行漏洞扫描
1.利用 “wpscan -h”命令,可查看Wpscan的版本,常用选项,功能介绍,例程等;
root@kali:~# wpscan -h
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team
Version 2.9.1 //Wpscan版本信息
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________ Help : Some values are settable in a config file, see the example.conf.json --update Update the database to the latest version.
#更新命令 命令“root@kali:~# wpscan --update”
--url | -u <target url> The WordPress URL/domain to scan.
#指定URL/域进行扫描 命令“root@kali:~# wpscan --url 地址”或“root@kali:~# wpscan -u 地址”
--force | -f Forces WPScan to not check if the remote site is running WordPress.
#强制Wpscan不检查远程正在运行WordPress的主机
--enumerate | -
24 option :
u usernames from id to 10
#默认用户1-用户10
u[-] usernames from id to (you must write [] chars)
#默认用户10-20([]中字符必须写)
p plugins
#插件程序
vp only vulnerable plugins
#仅漏洞插件程序
ap all plugins (can take a long time)
#所有插件程序(耗时比较长)
tt timthumbs
#小号
31 t themes#主题
32 vt only vulnerable themes
#仅漏洞主题
33 at all themes (can take a long time)
#所有主题
34 Multiple values are allowed : "-e tt,p" will enumerate timthumbs and plugi
#多值参数
If no option is supplied, the default is "vt,tt,u,vp"
无参默认
--exclude-content-based "<regexp or string>"
Used with the enumeration option, will exclude all occurrences based on the regexp or string supplied.
You do not need to provide the regexp delimiters, but you must write the quotes (simple or double).
--config-file | -c <config file> Use the specified config file, see the example.conf.json.
配置文佳
--user-agent | -a <User-Agent> Use the specified User-Agent.
指定用户代理
--cookie <String> String to read cookies from.
cookie字符串读取
--random-agent | -r Use a random User-Agent.
代理
--follow-redirection If the target url has a redirection, it will be followed without asking if you wanted to do so or not
跟踪重定向目标网址
--batch Never ask for user input, use the default behaviour.
不请求用户输入使用默认
--no-color Do not use colors in the output.
不在输出中使用颜色
--wp-content-dir <wp content dir> WPScan try to find the content directory (ie wp-content) by scanning the index page, however you can specified it.
Subdirectories are allowed.
WPScan尝试通过扫描索引页面来查找内容目录(即wp-content),但是您可以指定它。允许使用子目录。
49 --wp-plugins-dir <wp plugins dir> Same thing than --wp-content-dir but for the plugins directory.
If not supplied, WPScan will use wp-content-dir/plugins. Subdirectories are allowed
ame比--wp-content-dir但是对于plugins目录。 如果没有提供,WPScan将使用wp-content-dir / plugins。 允许子目录
--proxy <[protocol://]host:port> Supply a proxy. HTTP, SOCKS4 SOCKS4A and SOCKS5 are supported.
If no protocol is given (format host:port), HTTP will be used.
53 --proxy-auth <username:password> Supply the proxy login credentials.
提供代理登陆凭证
54 --basic-auth <username:password> Set the HTTP Basic authentication.
设置HTTP基本认证
--wordlist | -w <wordlist> Supply a wordlist for the password brute forcer.
为暴力密码破解指定密码字典
--username | -U <username> Only brute force the supplied username.
指定暴力破解用户
--usernames <path-to-file> Only brute force the usernames from the file.
仅从密码字典中暴力破解用户名
--threads | -t <number of threads> The number of threads to use when multi-threading requests.
多线程指定线程数
59 --cache-ttl <cache-ttl> Typhoeus cache TTL.
--request-timeout <request-timeout> Request Timeout.
请求时间间隔
61 --connect-timeout <connect-timeout> Connect Timeout.
连接时间间隔
--max-threads <max-threads> Maximum Threads.
最大线程数
63 --throttle <milliseconds> Milliseconds to wait before doing another web request. If used, the --threads should be set to .
在执行另一个Web请求之前等待的毫秒数。 如果使用,则--threads应设置为1。
--help | -h This help screen.
--verbose | -v Verbose output.
--version Output the current version and exit. Examples :
帮助
-Further help ...
ruby ./wpscan.rb --help
做“非侵入性”检查
-Do 'non-intrusive' checks ...
ruby ./wpscan.rb --url www.example.com
使用50个线程对枚举的用户做单词列表密码蛮力…
-Do wordlist password brute force on enumerated users using threads ...
ruby ./wpscan.rb --url www.example.com --wordlist darkc0de.lst --threads
做单词表密码蛮力上的“管理员”用户名只…
-Do wordlist password brute force on the 'admin' username only ...
ruby ./wpscan.rb --url www.example.com --wordlist darkc0de.lst --username admin
枚举安装的插件…
-Enumerate installed plugins ...
ruby ./wpscan.rb --url www.example.com --enumerate p
枚举安装的主题
-Enumerate installed themes ...
ruby ./wpscan.rb --url www.example.com --enumerate t
枚举用户
-Enumerate users ...
ruby ./wpscan.rb --url www.example.com --enumerate u
枚举安装的TimTrBBS
-Enumerate installed timthumbs ...
ruby ./wpscan.rb --url www.example.com --enumerate tt
使用HTTP代理
-Use a HTTP proxy ...
ruby ./wpscan.rb --url www.example.com --proxy 127.0.0.1:
使用SoCKS5代理
-Use a SOCKS5 proxy ... (cURL >= v7.21.7 needed)
ruby ./wpscan.rb --url www.example.com --proxy socks5://127.0.0.1:9000
使用自定义内容目录
-Use custom content directory ...
ruby ./wpscan.rb -u www.example.com --wp-content-dir custom-content
使用自定义插件目录
-Use custom plugins directory ...
ruby ./wpscan.rb -u www.example.com --wp-plugins-dir wp-content/custom-plugins
更新数据库
-Update the DB ...
ruby ./wpscan.rb --update
调试输出
-Debug output ...
ruby ./wpscan.rb --url www.example.com --debug-output >debug.log See README for further information.
2.对配置好的靶机进行扫描
wpscan -u 192.168.64.138 /wpscan --url 192.168.64.138
命令详解:对目标地址进行扫描
root@kali:~# wpscan -u 192.168.64.138
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team
Version 2.9.
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________ [+] URL: http://192.168.64.138/
[+] Started: Fri Aug :: [!] The WordPress 'http://192.168.64.138/readme.html' file exists exposing a version number
[+] Interesting header: LINK: <http://192.168.64.138/index.php/wp-json/>; rel="https://api.w.org/"
[+] Interesting header: SERVER: Apache
[+] XML-RPC Interface available under: http://192.168.64.138/xmlrpc.php [+] WordPress version 4.7. identified from advanced fingerprinting (Released on --)
[!] vulnerabilities identified from the version number [!] Title: WordPress 2.3-4.8. - Host Header Injection in Password Reset
Reference: https://wpvulndb.com/vulnerabilities/8807
Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html
Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html
Reference: https://core.trac.wordpress.org/ticket/25239
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295 [!] Title: WordPress 2.7.-4.7. - Insufficient Redirect Validation
Reference: https://wpvulndb.com/vulnerabilities/8815
Reference: https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11
Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066
[i] Fixed in: 4.7. [!] Title: WordPress 2.5.-4.7. - Post Meta Data Values Improper Handling in XML-RPC
Reference: https://wpvulndb.com/vulnerabilities/8816
Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/
Reference: https://github.com/WordPress/WordPress/commit/3d95e3ae816f4d7c638f40d3e936a4be19724381
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9062
[i] Fixed in: 4.7.
对具有漏洞的脚本进行扫描···· [+] Finished: Fri Aug ::
[+] Requests Done:
[+] Memory used: 50.062 MB 使用内存
[+] Elapsed time: ::04 耗时
3.通过漏洞插件扫描用户
wpscan -u 192.168.64.138 -e u vp
命令详解 -e使用枚举方式 u 扫描ID1-ID10 vp扫描漏洞插件
root@kali:~# wpscan -u 192.168.64.138 -e u vp
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team
Version 2.9.
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________ [+] URL: http://192.168.64.138/
[+] Started: Fri Aug :: [!] The WordPress 'http://192.168.64.138/readme.html' file exists exposing a version number
[+] Interesting header: LINK: <http://192.168.64.138/index.php/wp-json/>; rel="https://api.w.org/"
[+] Interesting header: SERVER: Apache
[+] XML-RPC Interface available under: http://192.168.64.138/xmlrpc.php [+] WordPress version 4.7. identified from advanced fingerprinting (Released on --)
[!] vulnerabilities identified from the version number [!] Title: WordPress 2.3-4.8. - Host Header Injection in Password Reset
Reference: https://wpvulndb.com/vulnerabilities/8807
Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html
Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html
Reference: https://core.trac.wordpress.org/ticket/25239
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295 [!] Title: WordPress 2.7.-4.7. - Insufficient Redirect Validation
Reference: https://wpvulndb.com/vulnerabilities/8815
Reference: https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11
Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066
[i] Fixed in: 4.7. [!] Title: WordPress 2.5.-4.7. - Post Meta Data Values Improper Handling in XML-RPC
Reference: https://wpvulndb.com/vulnerabilities/8816
Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/
Reference: https://github.com/WordPress/WordPress/commit/3d95e3ae816f4d7c638f40d3e936a4be19724381
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9062
[i] Fixed in: 4.7. [+] Enumerating usernames ...
[+] Identified the following user/s:
+----+-------+-----------------+
| Id | Login | Name |
+----+-------+-----------------+
| | admin | admin – TurnKey |
+----+-------+-----------------+
[!] Default first WordPress username 'admin' is still used [+] Finished: Fri Aug ::
[+] Requests Done:
[+] Memory used: 52.52 MB
[+] Elapsed time: ::
3.使用密码字典对用户进行爆破
wpscan -u 192.168.64.138 -e u --wordlist /root/wordlist.txt
命令详解: -e枚举方式 u 用户ID1-ID10 --wordlist使用指定字典进行密码爆破 /root/wordlist.txt 字典路径及字典文件 wordlist.txt字典文件需自己准备或使用kali自带字典
root@kali:~# wpscan -u 192.168.64.138 -e u --wordlist /root/wordlist.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team
Version 2.9.
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________ [+] URL: http://192.168.64.138/
[+] Started: Fri Aug :: [!] The WordPress 'http://192.168.64.138/readme.html' file exists exposing a version number
[+] Interesting header: LINK: <http://192.168.64.138/index.php/wp-json/>; rel="https://api.w.org/"
[+] Interesting header: SERVER: Apache
[+] XML-RPC Interface available under: http://192.168.64.138/xmlrpc.php [+] WordPress version 4.7. identified from advanced fingerprinting (Released on --)
[!] vulnerabilities identified from the version number [!] Title: WordPress 2.3-4.8. - Host Header Injection in Password Reset
Reference: https://wpvulndb.com/vulnerabilities/8807
Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html
Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html
Reference: https://core.trac.wordpress.org/ticket/25239
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295 [!] Title: WordPress 2.7.-4.7. - Insufficient Redirect Validation
Reference: https://wpvulndb.com/vulnerabilities/8815
Reference: https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11
Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066
[i] Fixed in: 4.7.
[!] Title: WP Super Cache <= 1.4. - PHP Object Injection
Reference: https://wpvulndb.com/vulnerabilities/8198
Reference: http://z9.io/2015/09/25/wp-super-cache-1-4-5/
[i] Fixed in: 1.4. [+] Enumerating usernames ...
[+] Identified the following user/s:
+----+-------+-----------------+
| Id | Login | Name |
+----+-------+-----------------+
| | admin | admin – TurnKey |
+----+-------+-----------------+
[!] Default first WordPress username 'admin' is still used
[+] Starting the password brute forcer
[+] [SUCCESS] Login : admin Password : Root******** Brute Forcing 'admin' Time: :: <===== > ( / ) 66.66% ETA: ::
+----+-------+-----------------+------------------+
| Id | Login | Name | Password |
+----+-------+-----------------+------------------+
| | admin | admin – TurnKey | Root********* |
+----+-------+-----------------+------------------+ [+] Finished: Fri Aug ::
[+] Requests Done:
[+] Memory used: 53.016 MB
[+] Elapsed time: ::
4.其他常用命令
wpscan -u 192.168.64.138 -e u --wordlist /root/wordlist.txt -t 50
-e枚举方式 u 用户ID1-ID10 --wordlist使用指定字典进行密码爆破 /root/wordlist.txt 字典路径及字典文件 wordlist.txt字典文件需自己准备或使用kali自带字典 -t 指定50个线程数
此文为本人学习实践后所写,转载请注明出处
本文博客地址 https://www.cnblogs.com/WangYiqiang/p/9490869.html
因本人在带学校智能汽车竞赛,写文精力实属有限,请读者多多包涵
若本文有错误或者不足之处,请读者批评指正
如果喜欢本文请点击【推荐】
【IT电子书资源强力推荐,各类图书免费下载】
电子书网页制作 | CSS教程 | javascript电子书 | ASP电子书 | PHP电子书 | .NET电子书 | 编程开发 | 网络安全 | ajax 电子书 | VBS电子书 | 站长书籍 | hta电子书 | 数据库XML | 正则表达式 | 图形图像 | 网络相关 | 电脑技术 | 电脑报刊 | 电脑硬件 | 随书源码 | 服务器 | Linux_unix | dos批处理 | VBA |
数据库xmlsqlserver | Oracle | mysql | DB2 | xml | VFP | 数据库其它 |
软件开发程序基础 | VB 书籍 | Delphi | PowerBuilder | Flash/ActionScript | java电子书 | C/C++/C# | Android | IOS | Ruby教程 | perl | Python教程 | matlab | 汇编语言 | 编程其它 |
地址https://itbook.download/
WPScan扫描Wordpress漏洞的更多相关文章
- WordPress漏洞扫描工具WPScan
WordPress漏洞扫描工具WPScan WordPress是主流的PHP网站模版,以构建博客而闻名.WordPress可以通过安装插件和主题的方式扩展功能,这也带来的安全隐患.WordPres ...
- 使用WPScan破解wordpress站点密码
我这里使用的Kali Linux,它默认安装了WPScan. 在使用WPScan之前,先更新它的漏洞数据库: # wpscan –update 扫描wordpress用户 wpscan -–url [ ...
- WPscan扫描工具安装使用
WPScan是Kali Linux默认自带的一款漏洞扫描工具,它采用Ruby编写,能够扫描WordPress网站中的多种安全漏洞,其中包括WordPress本身的漏洞.插件漏洞和主题漏洞.最新版本WP ...
- NodeJs的包漏洞扫描与漏洞测试攻击
一个典型的Node应用可能会有几百个,甚至上千个包依赖(大部分的依赖是间接的,即下载一个包,这个包会依赖其他的好多包),所以最终的结果是,应用程序就会像是这个样子的:
- 利用AWVS扫描Web漏洞
实验目的 利用AWVS扫描Web漏洞. 实验原理 AWVS是一款知名的网络漏洞扫描工具,它通过网络爬虫测试你的网站安全,检测流行安全漏洞. 实验内容 AWVS是一个自动化的web应用程序安全测试工具, ...
- 小白日记1:kali环境Wpscan渗透Wordpress
一.什么是Wpscan?什么是Wordpres? 1.Wpscan WPScan是一款针对wordpress的安全扫描软件:可以扫描出wordpress的版本,主题,插件,后台用户以及爆破后台用户密码 ...
- 360安全检测出的WordPress漏洞的修复方法
1.跨站脚本攻击(XSS) 这个漏洞注意是因为用户评论可以提交代码,有安全风险.虽然你的WordPress以及是最新版,但是你的WordPress主题却不一定跟着更新!因此,需要稍微修改一下评论相关的 ...
- 织梦Dedecms系统可疑文件include/filter.inc.php扫描出漏洞,该如何解决?
今天在做网站监察的时候,发现网站出了一个问题,在对网站做木马监测的时候,扫描出一个可疑文件:/include/filter.inc.php,建议删除,但仔细检查后,发现此文件是织梦(Dedecms)系 ...
- Nmap目录扫描和漏洞扫描(9.27 第十三天)
目录扫描:扫描站点的目录,寻找敏感文件(目录名.探针文件.后台.robots.txt[].备份文件等) 目录:站点结构,权限控制不严格 探针文件:服务器配置信息,phpinfo.php readm ...
随机推荐
- 防止 IE 自动跳兼容模式
在HTML <head> 中增加如下: <meta http-equiv="x-ua-compatible" content="IE=edge" ...
- MFC框架之线程局部存储
线程局部存储中用到的API基础:(TLS:Thread Local Storage) 1.在主线程中申请索引 g_index=::TlsAlloc(); 2.在线程函数中使用索引 存值:::TlsSe ...
- [日常] Go语言圣经--Channel习题
练习 8.3: 在netcat3例子中,conn虽然是一个interface类型的值,但是其底层真实类型是*net.TCPConn,代表一个TCP连接.一个TCP连接有读和写两个部分,可以使用Clos ...
- Eclipse 中设置JVM 内存
Eclipse 中设置JVM 内存 今天在eclipse 中测试把文档转换为图片的时候,报出了下面的错误: java.lang.OutOfMemoryError: Java heap space 从上 ...
- 基于hive的日志分析系统
转自 http://www.cppblog.com/koson/archive/2010/07/19/120773.html hive 简介 hive 是一个基于 ...
- 虚拟机中安装完 CentOS7minimal 版本后无法联网的问题
问题描述 安装完系统后无法上网,然后进入到目录 /etc/sysconfig/network-script 查看.发现只有一个 ifcfg-lo. 解决办法 这种情况是没有识别到网卡. 在 VMwar ...
- 面试之Mysql优化问题
一.前言 MySQL对于很多Linux从业者而言,是一个非常棘手的问题,多数情况都是因为对数据库出现问题的情况和处理思路不清晰.在进行MySQL的优化之前必须要了解的就是MySQL的查询过程,很多的查 ...
- Mysql实现级联操作(级联更新、级联删除)
一.首先创建两张表stu,sc create table stu( sid int UNSIGNED primary key auto_increment, name ) not null) TYPE ...
- python的深浅拷贝以及fromkeys的用法
1.join()的用法:使用前面的字符串.对后面的列表进行拼接,拼接结果是一个字符串 # lst = ["alex","dsb",'wusir','xsb'] ...
- python3获取一个网页特定内容
我们今天要爬取的网址为:https://www.zhiliti.com.cn/html/luoji/list7_1.html 一.目标:获取下图红色部分内容 即获取所有的题目以及答案. 二.实现步骤. ...
