[NepCTF2022]signin
signin
题目
from Crypto.Util.number import getStrongPrime,bytes_to_long
from gmpy2 import powmod,is_prime,invert,bit_length, next_prime
from FLAG import flag
def gen_key():
(p,q,n,e,d) = (0 for _ in range(5))
p = getStrongPrime(1024)
q = next_prime(p)
# q = p + 1
# while(True):
# q += 2 if q & 1 else 1
# if is_prime(q, 30):
# break
n = p*q
e = 65537
d = invert(e, (p-1)*(q-1)) #求逆元
par = (p,q,n,e,d)
return par
def leak(par, c):
assert len(par) == 5
(p,q,n,e,d) = par
print("Here's something for you.")
print("n =",n)
print("e =",e)
print("c_mod_p =",c % p)
print("c_mod_q =",c % q)
def enc(message, par):
assert len(par) == 5
(p,q,n,e,d) = par
m = bytes_to_long(message)
c = powmod(m,e,n)
return c
if __name__ == '__main__':
par = gen_key()
c = enc(flag, par)
leak(par, c)
"""
Here's something for you.
n = 19955580242010925349026385826277356862322608500430230515928936214328341334162349408990409245298441768036250429913772953915537485025323789254947881868366911379717813713406996010824562645958646441589124825897348626601466594149743648589703323284919806371555688798726766034226044561171215392728880842964598154362131942585577722616354074267803330013886538511795383890371097812191816934883393255463554256887559394146851379087386846398690114807642170885445050850978579391063585254346364297374019309370189128443081285875218288166996242359495992824824109894071316525623741755423467173894812627595135675814789191820979950786791
e = 65537
c_mod_p = 32087476819370469840242617415402189007173583393431940289526096277088796498999849060235750455260897143027010566292541554247738211165214410052782944239055659645055068913404216441100218886028415095562520911677409842046139862877354601487378542714918065194110094824176055917454013488494374453496445104680546085816
c_mod_q = 59525076096565721328350936302014853798695106815890830036017737946936659488345231377005951566231961079087016626410792549096788255680730275579842963019533111895111371299157077454009624496993522735647049730706272867590368692485377454608513865895352910757518148630781337674813729235453169946609851250274688614922
"""
分析
题目考查中国剩余定理,给了n,e,c modp(Cp),c modq(Cq) 没给C。
p和q很接近,应该可以暴力破解n。
factordb查不到,用yafu分解试试: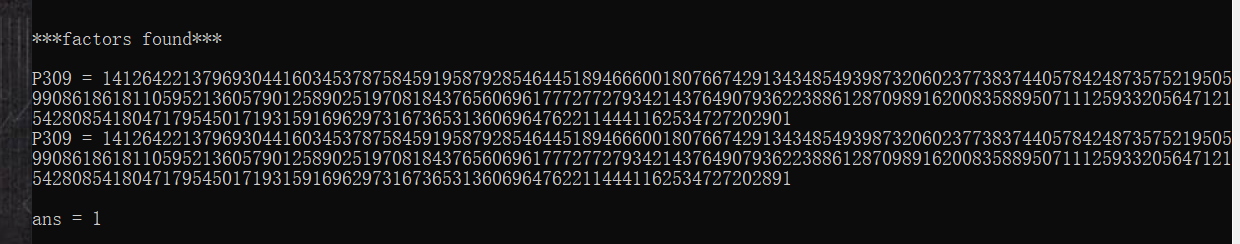
分解出来了p和q。
根据代码推断q是大的那一个,所以:
q = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202901
p = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202891
得到p,q
验算一下得到的q与分解出来的相符。
import gmpy2
p=141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202891
q = p + 1
while(True):
q += 2 if q & 1 else 1
if gmpy2.is_prime(q, 30):
break
print(q)
理论上来讲此时已经可以出m了,但是c没给我们,咱需要用c_mod_p和c_mod_q用中国剩余定理求出c。
import libnum
import gmpy2
n = 19955580242010925349026385826277356862322608500430230515928936214328341334162349408990409245298441768036250429913772953915537485025323789254947881868366911379717813713406996010824562645958646441589124825897348626601466594149743648589703323284919806371555688798726766034226044561171215392728880842964598154362131942585577722616354074267803330013886538511795383890371097812191816934883393255463554256887559394146851379087386846398690114807642170885445050850978579391063585254346364297374019309370189128443081285875218288166996242359495992824824109894071316525623741755423467173894812627595135675814789191820979950786791
e = 65537
c1 = 32087476819370469840242617415402189007173583393431940289526096277088796498999849060235750455260897143027010566292541554247738211165214410052782944239055659645055068913404216441100218886028415095562520911677409842046139862877354601487378542714918065194110094824176055917454013488494374453496445104680546085816
c2 = 59525076096565721328350936302014853798695106815890830036017737946936659488345231377005951566231961079087016626410792549096788255680730275579842963019533111895111371299157077454009624496993522735647049730706272867590368692485377454608513865895352910757518148630781337674813729235453169946609851250274688614922
q = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202891
p = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202901
#用中国剩余定理求c
def chinese_remainder(n, a):
sum = 0
prod = libnum.reduce(lambda a, b: a * b, n)
for n_i, a_i in zip(n, a):
p = prod // n_i
sum += a_i * gmpy2.invert(p, n_i) * p
return int(sum % prod)
#求出来就常规做题了
n11=[q,p]
c11=[c1,c2]
c=chinese_remainder(n11,c11)
print(c)
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
print(d)
m = pow(c,d,n)
print(libnum.n2s(int(m)))
b'NepCTF{ju5t_d0_f4ct_4nd_crt_th3n_d3crypt}'
[NepCTF2022]signin的更多相关文章
- gitlab不小心把sign-in取消了怎么恢复
环境和版本 [root@linux-node1 etc]# ll /var/cache/yum/x86_64/7/gitlab-ce/packages/ total 292928 -rw-r--r-- ...
- Integrating Google Sign-In into Your Android App
To integrate Google Sign-In into your Android app, configure Google Sign-In and add a button to your ...
- 微软Bot Framework文档中,关于Sign-in Card的一处代码错误及更正
Bot Framework文档出错处网址:https://docs.botframework.com/en-us/csharp/builder/sdkreference/attachments.htm ...
- 服务器时间误差导致的google sign-in后台验证错误(远程调试java程序)
https://developers.google.com/identity/sign-in/web/backend-auth import com.google.api.client.googlea ...
- IdentityServer4 sign-in
原文地址 Sign-in IdentityServer 代表 user 分配token之前,user必须登录IdentityServer Cookie authentication 使用 cookie ...
- 攻防世界 reverse SignIn
SignIn 2019_SUCTF __int64 __fastcall main(__int64 a1, char **a2, char **a3) { char mod; // [rsp+0 ...
- [BUUCTF]REVERSE——[SUCTF2019]SignIn
[SUCTF2019]SignIn 附件 步骤: 无壳,64位ida载入 程序调用了 __gmpz_init_set_str 函数,这是一个 GNU 高精度算法库,在RSA加密中见过几次,加上6553 ...
- ADFS3.0 Customizing the AD FS Sign-in Pages
Windows Server2012R2自带的adfs是3.0的版本,不同于以前的版本的是3.0中登陆页面的定制化全部是通过powershell指令实现,官方的介绍链接如下:http://techne ...
- gitlab 误关闭sign-in
sudo gitlab-rails console ApplicationSetting.last.update_attributes(password_authentication_enabled_ ...
- Gitlab不小心关闭了sign-in,无法登录web的坑。。。
手贱一不小心用root在gitlab后台把登录功能给关了,当时我就懵逼了. 解决方法如下: #进入数据库修改配置[root@gitlab-server ~]# gitlab-psql gitlabhq ...
随机推荐
- 基于.NetCore开发博客项目 StarBlog - (24) 统一接口数据返回格式
前言 开发接口,是给客户端(Web前端.App)用的,前面说的RESTFul,是接口的规范,有了统一的接口风格,客户端开发人员在访问后端功能的时候能更快找到需要的接口,能写出可维护性更高的代码. 而接 ...
- vuex的使用详解
一.下载vuex 在store文件夹下的index.js中 官方文档:https://vuex.vuejs.org/zh/ 需要使用的页面 sotre中 mutations的调用方法 store ...
- Python自动化结算工资和统计报表|编程一对一教学微信:Jiabcdefh
实例需求说明 你好,我是悦创. 博客首发:https://bornforthis.cn/column/pyauto/auto_base07.html 学习了 Excel 文件的写入.读取和追加内容,那 ...
- [深度探索C++对象模型]trival constructor和non-trival constructor
分清楚user-declared constructor和implict default constructor 首先要知道,如果你没有自定义一个类的构造函数,那么编译器会在暗中声明一个构造器,这个构 ...
- P4711 「化学」相对分子质量 代码
#include <bits/stdc++.h> using namespace std; double ret=0; namespace StringUtils { pair<st ...
- SICP:复数的直角和极坐标的表示(Python实现)
绪论 我们已经介绍过数据抽象,这是一种构造系统的方法学,它能够使程序中的大部分描述与其所操作的数据对象的具体表示无关,比如一个有理数程序的设计与有理数的实现相分离.这里的关键是构筑数据抽象屏障--在有 ...
- 保姆级教程-分分钟掌握常用TS语法
十分钟就搞懂TS用法 先全局安装一些工具,有助于我们编写运行代码哦 1.VScode插件 code runner 2.安装依赖 npm install typescript ts-node -g 开始 ...
- angular打包出现JavaScript堆内存不足、启动也会内存溢出解决办法\increase-memory-limit' 不是内部或外部命令,
## 打包出现JavaScript堆内存不足 最近打包遇到这种报错 Ineffective mark-compacts near heap limit Allocation failed - Java ...
- Tomcat 解决一些基本配置问题。
解决Tomcat进入manger管理界面需要账号密码问题 第一步,打开Tomcat的conf文件夹 进入tomcat-users.xml文件 在 标签里面复制以下内容 <role rolenam ...
- JDK9对集合添加的优化-Debug追踪
JDK9对集合添加的优化 通常,我们在代码中创建一个集合(例如,List或Set ),并直接用一些元素填充它.实例化集合,几add方法调用,使得代码重复. package A_Lian_one.dem ...
