ssh 认证
ssh 秘钥认证流程
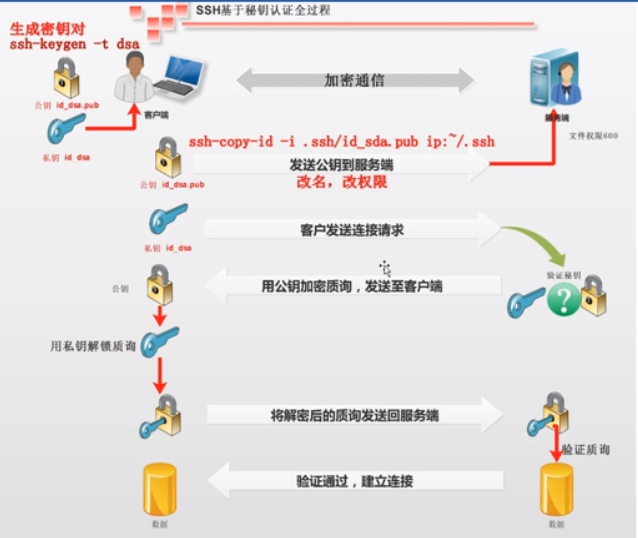
ssh配置认证
基于口令(密码)的安全验证
[root@m01 ~]# ssh 10.0.0.41 hostname
root@10.0.0.41's password:
backup
[root@m01 ~]# ssh 10.0.0.41 whoami
root@10.0.0.41's password:
root
[root@m01 ~]# ssh lewen@10.0.0.41 whoami
lewen@10.0.0.41's password:
lewen
基于秘钥的认证
1.生成钥匙和锁头
[root@m01 ~]# hostname
m01
[root@m01 ~]# ssh-keygen -t dsa
Generating public/private dsa key pair.
Enter file in which to save the key (/root/.ssh/id_dsa):
Enter passphrase (empty for no passphrase): # 给秘钥加密码
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_dsa.
Your public key has been saved in /root/.ssh/id_dsa.pub.
The key fingerprint is:
::1b:e1:9f:0a:ab::a0:fc:::2d:bc::dd root@m01
The key's randomart image is:
+--[ DSA ]----+
| |
| . + . |
| = + E |
| . + . o |
| o . S |
| ..o = . |
| .o.... o |
| .o..o.. |
| .+o.. |
+-----------------+
2.把锁头发送到目标机器
发送到 backup
[root@m01 ~]# ssh-copy-id -i /root/.ssh/id_dsa.pub root@172.16.1.41
The authenticity of host '172.16.1.41 (172.16.1.41)' can't be established.
RSA key fingerprint is ac:0f:aa:d2:5b:ff:cf:ac:f0:::a6:be::b9:f9.
Are you sure you want to continue connecting (yes/no)? y
Please type 'yes' or 'no': yes
Warning: Permanently added '172.16.1.41' (RSA) to the list of known hosts.
root@172.16.1.41's password:
Now try logging into the machine, with "ssh 'root@172.16.1.41'", and check in:
.ssh/authorized_keys
to make sure we haven't added extra keys that you weren't expecting.
[root@m01 ~]# ssh 10.0.0.41 hostname
backup
#nfs01
[root@m01 ~]# ssh-copy-id -i /root/.ssh/id_dsa.pub root@172.16.1.31
The authenticity of host '172.16.1.31 (172.16.1.31)' can't be established.
RSA key fingerprint is ac:0f:aa:d2:5b:ff:cf:ac:f0:::a6:be::b9:f9.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.16.1.31' (RSA) to the list of known hosts.
root@172.16.1.31's password:
Now try logging into the machine, with "ssh 'root@172.16.1.31'", and check in:
.ssh/authorized_keys
to make sure we haven't added extra keys that you weren't expecting.
[root@m01 ~]# ssh 172.16.1.31 hostname
nfs01
3.免密发送
sshpass 软件
yum install sshpass -y #sshpass 给ssh类提供密码
[root@m01 ~]# sshpass -p123456 ssh 172.16.1.41 hostname
backup
sshpass -p123456 ssh -o StrictHostKeyChecking=no 172.16.1.41 hostname
backup
非交互式创建 钥匙锁头
[root@m01 ~]# ssh-keygen -t dsa -P '' -f ~/.ssh/id_dsa
非交互式 分发公钥
不用输入密码将公钥发送到目的机器
[root@m01 ~]# sshpass -p123456 ssh-copy-id -i /root/.ssh/id_dsa.pub "-o StrictHostKeyChecking=no root@172.16.1.41"
Now try logging into the machine, with "ssh '-o StrictHostKeyChecking=no root@172.16.1.41'",
and check in:
.ssh/authorized_keys
to make sure we haven't added extra keys that you weren't expecting.
[root@m01 ~]# sshpass -p123456 ssh-copy-id -i /root/.ssh/id_dsa.pub "-o StrictHostKeyChecking=no root@172.16.1.31"
Now try logging into the machine, with "ssh '-o StrictHostKeyChecking=no root@172.16.1.31'",
and check in:
.ssh/authorized_keys
to make sure we haven't added extra keys that you weren't expecting.
[root@m01 ~]# ssh 172.16.1.41 hostname
backup
[root@m01 ~]# ssh 172.16.1.31 hostname
nfs01
Usage: /usr/bin/ssh-copy-id [-h|-?|-f|-n] [-i [identity_file]] [-p port] [[-o <ssh -o options>] ...] [user@]hostname
-f: force mode -- copy keys without trying to check if they are already installed
-n: dry run -- no keys are actually copied
ssh 认证的更多相关文章
- ssh 认证指定端口
[root@database2 ~]# cat ssh.sh if [ ! $# -eq 2 ] ;then echo "请输入用户密码以空格分开" exit else ssh-k ...
- 批量的单向的ssh 认证
<pre name="code" class="python">if [ ! $# -eq 2 ] ;then echo "请输入用户密码 ...
- debian下使用gitosis+gitweb搭建SSH认证的git服务器
搭建完成Git服务器后,需要使用两台机器进行测试,一台机器作为服务器端server,一台服务器作为客户端client.整个系统,需要三个计算机账户,这里假设server端的账户名为git,client ...
- github添加ssh认证
总概:在使用git的时候,和目标仓库建立关系有两种方式https,ssh.一般用的是https认证(这样简单方便),但有个缺点,pull,push等操作需要频繁输入用户验证.虽然可以把用户验证账号密码 ...
- Linux学习笔记总结--ssh认证登录
原理简介 SSH证书认证登录的基础是一对唯一匹配密钥: 私钥(private key)和公钥(public key).公钥用于对数据进行加密,而且只能用于加密.而私钥只能对使用所匹配的公钥,所加密过的 ...
- git ssh认证
一般新手用git时,使用HTTPS都需要输入用户名和密码,这是一个很低效的开发过程.(虽然有时可以让开发人员减少push的次数).github提供了几种连接方式,其中以https:开头的代表https ...
- 华为SSH认证配置
[设备型号]华为switch-S5700s ————1: [SW1] rsa/dsa local-key-pair create #创建本地密钥对 The key name will be: SW1_ ...
- Jenkins - SSH认证方式拉取Git代码
1.本地生成密钥 [root@root ~] ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which ...
- [Linux] 一次SSH认证失败引发的关于通过日志查错误的思考
一.缘由: 早上在用SSH公钥认证打通所有的机器,有一台机器在完成一些列操作后密钥登陆失败,其他机器一切正常. 错误如下:Public-key authentication with the serv ...
随机推荐
- PAT L3-001 凑零钱(01背包dp记录路径)
韩梅梅喜欢满宇宙到处逛街.现在她逛到了一家火星店里,发现这家店有个特别的规矩:你可以用任何星球的硬币付钱,但是绝不找零,当然也不能欠债.韩梅梅手边有104枚来自各个星球的硬币,需要请你帮她盘算一下,是 ...
- seek引发的python文件读写的问题
我的需求很简单,就是统计一下我的安装脚本执行的次数和时间,格式是这样的 install_times:1|install_times:2018-09-03 15:58:46 install_times: ...
- ThinkPhp框架开发微信支付——刷卡支付
首先讲讲我遇到的坑: 1.下载了微信的demo,界面如下,一直调试不通过,原来点击链接地址是微信测试的网页地址...要改成自己开发的网页地址.... 2.demo不是用ThinkPhp框架的,我不懂, ...
- YII2表单中上传单个文件
有些时候我们提交的表单中含有文件.怎么样让表单里的数据和文件一起提交. 我的数据表tb_user内容如下: CREATE TABLE `tb_user` ( `id` int(11) unsigned ...
- 获取URL某个参数
/* 获取URL某个参数(可以是中文) * 返回:字符串 */ function getUrlParam(key) { // 获取参数 var url = window.location.search ...
- input 原生上传文件(type = file)
1.表单上传文件的步骤: - 1)设置enctype 默认为:enctype="application/x-www-form-urlencoded"(一般不设置) 若要表单中有需要 ...
- Linux locales
一.简介 二.语法 三.实例 aptitude install locales dpkg-reconfigure locales ; vi /etc/default/locale more / ...
- 看看用PS来转基因的动物,居然很欢乐!!
出于礼貌,我先笑一下,哈哈哈哈哈哈!好了,开始.Gyyporama是挪威的一名程序员,他无聊的时候会从网上找来一些动物的图片,把他们的头和身体进行混合,生成另一种奇怪的动物.然后邀请其他网友过来给他们 ...
- Collection和Collections的区别是什么
1)java.util.Collection是一个集合顶层接口,该接口的设计目的是为各种具体的集合提供最大化的统一的操作方式,它提供了对集合对象进行基本操作的通用接口方法,实现该接口的类主要有List ...
- About how fast is fast enough for a web application?
About how fast is fast enough for a web application? Here’s a quick overview of key performance metr ...
