http响应报文,如果响应的内容比较大,客户端怎么样判断接收完了呢?
1. http协议有正文大小说明的
content-length
2. 或者分块传输chunked的话 读到0\r\n\r\n 就是读完了
-----------------------------------------------------------------------------------------------
http响应内容比较大的话,会分成多个tcp segment 发送,不是最后一个segment的话, tcp的payload不会有http header字段,
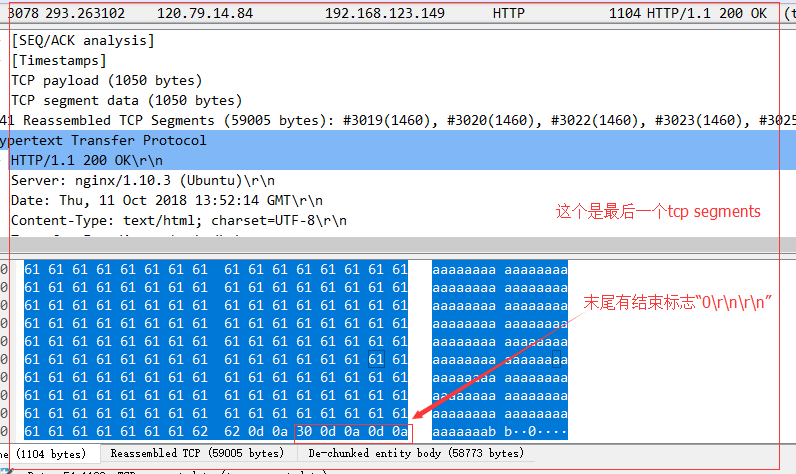
如果是最后一个tcp segment 的话,就会有http header 字段,同时, 数据的最后会有 "0\r\n\r\n" 这个东西,这个东西就表示数据都发送完了。
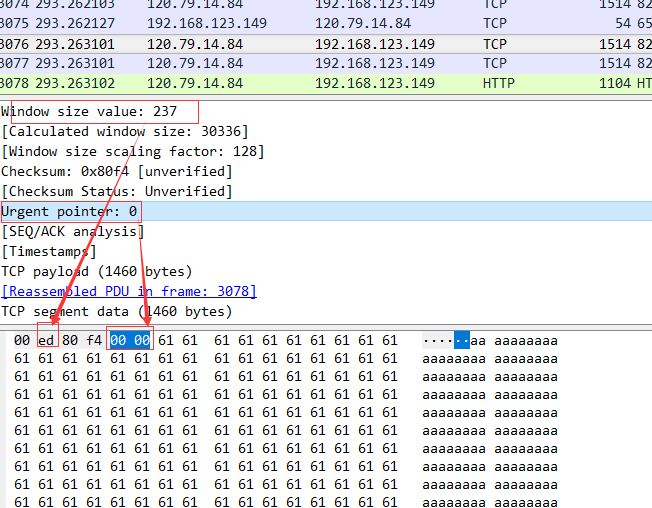
如果是最后一个tcp segment 的话,就会有http header 字段,同时, 数据的最后会有 "0\r\n\r\n" 这个东西,这个东西就表示数据都发送完了。
https://osqa-ask.wireshark.org/questions/7268/http-continuation-vs-tcp-segment
|
2
|
In fact there are at least three different issues with reassembling considered chunked HTTP transfer encoding and you must check your preferences very carefully, especially if you are dealing with 'endless' server connection sending chunks of messages. First, the application-level protocol packet, such as HTTP request may fit in single TCP segment, and may not. If the HTTP header is big enough to be split in segments (that's a rare issue, but happens if site is sending lots of cookies and optional X-headers), then you will see two or more packets in the wireshark capture, period. The same can happen to HTTP response headers and mostly it does happen to HTTP request/response bodies. Sometimes applications just do send HTTP headers in single TCP segment and HTTP body in next one. But please note, that those segments have nothing in common with chunks, when chunked Transfer-Encoding is used, because that encoding is application level and TCP is the transport level of the OSI model. So, even your single "chunk" can span multiple segments. But that's not the whole story. Single TCP segment can either fit in ethernet frame (PDU), but can be split as well. Most of the time this does not happen, but for some badly configured Windows machines the maximum size of TCP frame is bigger then usual maximum of Ethernet switches can handle. To add more fun, transport-level packets must be ACK'ed by the endpoint, and sometimes ACK is set within next TCP data packet, and sometimes it is sent separately, while still on the same HTTP port. So, if you try to analyse Web application traffic on TCP level, you'll get a loads of useless sh#t most of the time. That's why you should use filters. To help upper-level protocols collect and filter information, the wireshark dissectors have notion of 'reassembling', where higher-level dissector returns special code meaning 'hey, I need more data to properly dissect this packet' and then processing is restarted when more data arrives. If you turn off ALL reassembling options for TCP and HTTP (and SSL) protocols, then you'll see the naked packets as they are on the wire. You'll notice that 'Continuation of HTTP traffic' message in Info column when packet is with data, but neither HTTP request nor HTTP response header found within it. And all packets without data will be tagged as plain TCP in Protocol column. Mostly that's about ACKs, SYNs and FINs, so you can filter them out. If you allow TCP to reassemble streams, but leave other options unchecked - the picture won't change much, because upper level protocols won't request reassembling. If you allow HTTP to request reassembling the headers spanning multiple segments and bodies then you can already do filtering by application protocol means. E.g. enter 'http' in the Display filter and you'll can forget about all [reassembled PDU] infos - they all be marked as being 'TCP' protocol. Now the dangled part - reassembling application-level chunks. If you analyse protocol that depends upon sending data in chunks, e.g. AJAX chat over HTTP, I'd suggest leaving that option unchecked. Because reassembling stops when you receive the chunk with '0' size, which in your case you would never. However, if your application does encode HTTP bodies with gzip, and use chunked encoding just to send it in streamlined version, you'd better check option of chunk reassembling, otherwise ungzipping will fail. That was quite a lot of text above, but hope now everything is clear for you. Also, if you want more advanced filtering options for HTTP responses, you may find it useful to install following Lua script : Assocating HTTP responses to requests in Wireshark. Should you have any questions about it, feel free to ask. |
http响应报文,如果响应的内容比较大,客户端怎么样判断接收完了呢?的更多相关文章
- 重温Http协议--请求报文和响应报文
http协议是位于应用层的协议,我们在日常浏览网页比如在导航网站请求百度首页的时候,会先通过http协议把请求做一个类似于编码的工作,发送给百度的服务器,然后在百度服务器响应请求时把相应的内容再通过h ...
- HTTP 请求报文 响应报文
引言 超文本传输协议(HTTP,HyperText Transfer Protocol)是互联网上应用最为广泛的一种网络协议.所有的WWW文件都必须遵守这个标准.设计HTTP最初的目的是为了提供一种发 ...
- HTTP请求报文和HTTP响应报文
HTTP报文是面向文本的,报文中的每一个字段都是一些ASCII码串,各个字段的长度是不确定的.HTTP有两类报文:请求报文和响应报文. HTTP请求报文 一个HTTP请求报文由请求行(request ...
- HTTP请求报文和HTTP响应报文(转)
原文地址:http://blog.csdn.net/zhangliang_571/article/details/23508953 HTTP报文是面向文本的,报文中的每一个字段都是一些ASCII码串, ...
- HTTP响应报文与工作原理详解
超文本传输协议(Hypertext Transfer Protocol,简称HTTP)是应用层协议.HTTP 是一种请求/响应式的协议,即一个客户端与服务器建立连接后,向服务器发送一个请求;服务器接到 ...
- 关于HTTP请求报文和响应报文学习笔记
超文本传输协议(Hypertext Transfer Protocol,简称HTTP)是应用层的一种通信协议.它是一种请求/响应式的协议,即一个客户端与服务器建立连接后,向服务器发送一个请求;服务器接 ...
- Http请求和响应报文基础知识
一 HTTP请求报文(http://en.wikipedia.org/wiki/List_of_HTTP_header_fields) 请求报文由三部分组成:请求行,请求头和请求体. 请求行:请求方法 ...
- HTTP 请求报文 响应报文(转)
引言 超文本传输协议(HTTP,HyperText Transfer Protocol)是互联网上应用最为广泛的一种网络协议.所有的WWW文件都必须遵守这个标准.设计HTTP最初的目的是为了提供一种发 ...
- 【转】HTTP响应报文与工作原理详解
超文本传输协议(Hypertext Transfer Protocol,简称HTTP)是应用层协议.HTTP 是一种请求/响应式的协议,即一个客户端与服务器建立连接后,向服务器发送一个请求;服务器接到 ...
随机推荐
- ref:使用Dezender对zend加密后的php文件进行解密
ref:http://www.cnblogs.com/88223100/ 使用Dezender对zend加密后的php文件进行解密 在开发中需要修改一些php文件,部分是通过zend加密的,记事本 ...
- 转:在 Ubuntu 上使用 Nginx 部署 Flask 应用
转:http://Python.jobbole.com/84286/ 原文出处: Vladik 译文出处:开源中国 我职业生涯的大部分都在使用微软的架构,最近我决定走出技术的舒适区,步入开源 ...
- MNIST神经网络的训练
import tensorflow as tf from tensorflow.examples.tutorials.mnist import input_data 1.设置输入和输出节点的个数,配置 ...
- springMVC接受对象集合,name数组
这两天开发遇到一个很常见的问题,即使自己一直没遇见过,不过之前看过是实现接受对象集合的代码,只不过没注意罢了 推荐一篇文章 直接贴代码吧 public class Person { private S ...
- Sublime Text的使用技巧
来到腾讯之后,基本上整个团队都在使用Sublime Text这款编辑神器.虽说自己以前在写python的时候略有接触过,但只是把它当做简单的文本编辑器.来到这边后,才逐渐的体会到这款神作的牛逼之处. ...
- codeforce 429D. Tricky Function (思维暴力过)
题目描述 Iahub and Sorin are the best competitive programmers in their town. However, they can't both qu ...
- p1315构建双塔 dp
From easthong ☆构建双塔 描述 Description 2001年9月11日,一场突发的灾难将纽约世界贸易中心大厦夷为平地,Mr. F曾亲眼目睹了 ...
- JZYZOJ1525 HAOI2012道路 堆优化的dijkstra+pair
From Tyvj Guest ☆[haoi2012]道路 描述 Description C国有n座城市,城市之间通过m条单向道路连接.一条路径被称为最短路,当 ...
- Arab Collegiate Programming Contest 2012 J- Math Homework
思路:由于只有1-6这几个数,而这几个数的最小公倍数是60,所以只需要求出60以内有多少满足条件的数即可. 再就是求出对于给定的n,求出60的倍数.然后就是怎样求的问题了. 首先可以写成如下形式: ...
- 【BZOJ】2002: [Hnoi2010]Bounce 弹飞绵羊
2002: [Hnoi2010]Bounce 弹飞绵羊 Time Limit: 10 Sec Memory Limit: 259 MBSubmit: 14802 Solved: 7507[Subm ...
