kubernetes实战(二十):k8s一键部署高可用Prometheus并实现邮件告警
1、基本概念
本次部署使用的是CoreOS的prometheus-operator。
本次部署包含监控etcd集群。
本次部署适用于二进制和kubeadm安装方式。
本次部署适用于k8s v1.10版本以上,其他版本自行测试。
项目地址:https://github.com/coreos/prometheus-operator/tree/master/contrib/kube-prometheus
使用Helm安装:https://github.com/helm/charts/tree/master/stable/prometheus-operator
2、安装
下载安装文件:
[root@k8s-master01 ~]# git clone https://github.com/dotbalo/k8s.git
Cloning into 'k8s'...
remote: Enumerating objects: , done.
remote: Counting objects: % (/), done.
remote: Compressing objects: % (/), done.
remote: Total (delta ), reused (delta ), pack-reused
Receiving objects: % (/), 4.92 MiB | 553.00 KiB/s, done.
Resolving deltas: % (/), done.
[root@k8s-master01 prometheus-operator]# ls
alertmanager-config.yam.bak bundle.yaml mail-template.tmpl README.md
alertmanager.yaml deploy manifests teardown
修改相关配置:
1) 修改deploy文件中的etcd证书文件,kubeadm安装方式的无须修改
2)修改manifests/prometheus/prometheus-etcd.yaml的tlsConfig(kubeadm安装方式的无须修改)和addresses(etcd地址)
3)修改alertmanager.yaml文件的邮件告警配置和收件人配置
一键安装:(注意:如果集群是二进制安装的,首次安装注册时间可能会很长很长,kubeadm安装方式较迅速。)
[root@k8s-master01 prometheus-operator]# ./deploy
namespace/monitoring created
secret/alertmanager-main created
secret/etcd-certs created
clusterrolebinding.rbac.authorization.k8s.io/prometheus-operator created
clusterrole.rbac.authorization.k8s.io/prometheus-operator created
serviceaccount/prometheus-operator created
service/prometheus-operator created
deployment.apps/prometheus-operator created
Waiting for Operator to register custom resource definitions...done!
clusterrolebinding.rbac.authorization.k8s.io/node-exporter created
clusterrole.rbac.authorization.k8s.io/node-exporter created
daemonset.extensions/node-exporter created
serviceaccount/node-exporter created
service/node-exporter created
clusterrolebinding.rbac.authorization.k8s.io/kube-state-metrics created
clusterrole.rbac.authorization.k8s.io/kube-state-metrics created
deployment.extensions/kube-state-metrics created
rolebinding.rbac.authorization.k8s.io/kube-state-metrics created
role.rbac.authorization.k8s.io/kube-state-metrics-resizer created
serviceaccount/kube-state-metrics created
service/kube-state-metrics created
secret/grafana-credentials created
secret/grafana-credentials unchanged
configmap/grafana-dashboard-definitions- created
configmap/grafana-dashboards created
configmap/grafana-datasources created
deployment.apps/grafana created
service/grafana created
service/etcd-k8s created
endpoints/etcd-k8s created
servicemonitor.monitoring.coreos.com/etcd-k8s created
configmap/prometheus-k8s-rules created
serviceaccount/prometheus-k8s created
servicemonitor.monitoring.coreos.com/alertmanager created
servicemonitor.monitoring.coreos.com/kube-apiserver created
servicemonitor.monitoring.coreos.com/kube-controller-manager created
servicemonitor.monitoring.coreos.com/kube-scheduler created
servicemonitor.monitoring.coreos.com/kube-state-metrics created
servicemonitor.monitoring.coreos.com/kubelet created
servicemonitor.monitoring.coreos.com/node-exporter created
servicemonitor.monitoring.coreos.com/prometheus-operator created
servicemonitor.monitoring.coreos.com/prometheus created
service/prometheus-k8s created
prometheus.monitoring.coreos.com/k8s created
role.rbac.authorization.k8s.io/prometheus-k8s created
role.rbac.authorization.k8s.io/prometheus-k8s created
role.rbac.authorization.k8s.io/prometheus-k8s created
clusterrole.rbac.authorization.k8s.io/prometheus-k8s created
rolebinding.rbac.authorization.k8s.io/prometheus-k8s created
rolebinding.rbac.authorization.k8s.io/prometheus-k8s created
rolebinding.rbac.authorization.k8s.io/prometheus-k8s created
clusterrolebinding.rbac.authorization.k8s.io/prometheus-k8s created
service/alertmanager-main created
alertmanager.monitoring.coreos.com/main created
3、验证安装
查看pods
[root@k8s-master01 prometheus-operator]# kubectl get po -n monitoring
NAME READY STATUS RESTARTS AGE
alertmanager-main- / Running 2m
alertmanager-main- / Running 1m
alertmanager-main- / Running 1m
grafana-59f56c4789-dzvgf / Running 2m
kube-state-metrics-575464c49c-m8w4w / Running 2m
node-exporter-5kvxf / Running 2m
node-exporter-66p7h / Running 2m
node-exporter-clxzk / Running 2m
node-exporter-hsgm8 / Running 2m
node-exporter-m5l24 / Running 2m
prometheus-k8s- / Running 2m
prometheus-k8s- / Running 2m
prometheus-operator-8597f9b976-2hvd5 / Running 2m
查看svc
[root@k8s-master01 prometheus-operator]# kubectl get svc -n !$
kubectl get svc -n monitoring
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
alertmanager-main NodePort 10.106.201.155 <none> :/TCP 2m
alertmanager-operated ClusterIP None <none> /TCP,/TCP 2m
etcd-k8s ClusterIP None <none> /TCP 2m
grafana NodePort 10.99.143.133 <none> :/TCP 2m
kube-state-metrics ClusterIP None <none> /TCP,/TCP 2m
node-exporter ClusterIP None <none> /TCP 2m
prometheus-k8s NodePort 10.101.175.59 <none> :/TCP 2m
prometheus-operated ClusterIP None <none> /TCP 2m
prometheus-operator ClusterIP 10.107.31.10 <none> /TCP 2m
此时开放了三个端口:
- alertmanager UI:30903
- grafana:30902
- prometheus UI:30900
4、访问测试
alertmanager:

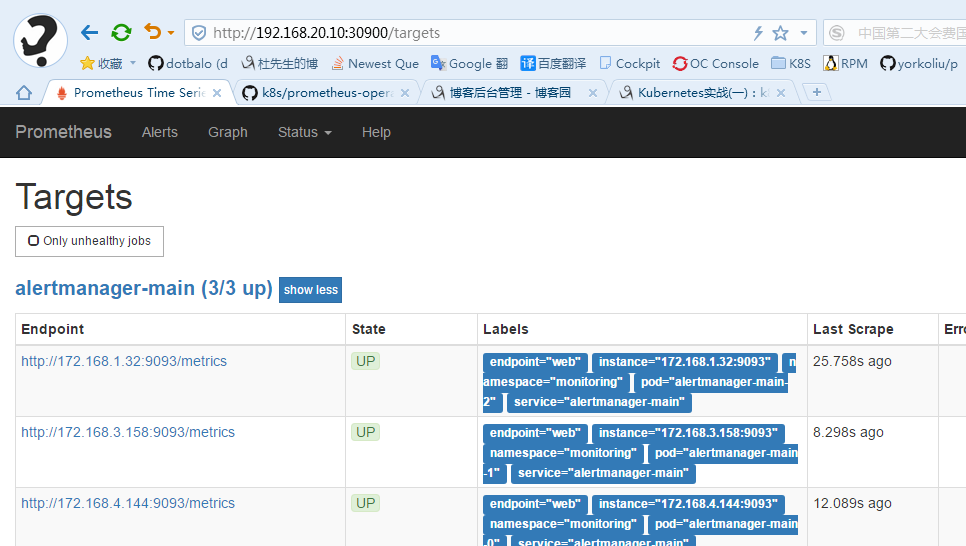
prometheus:
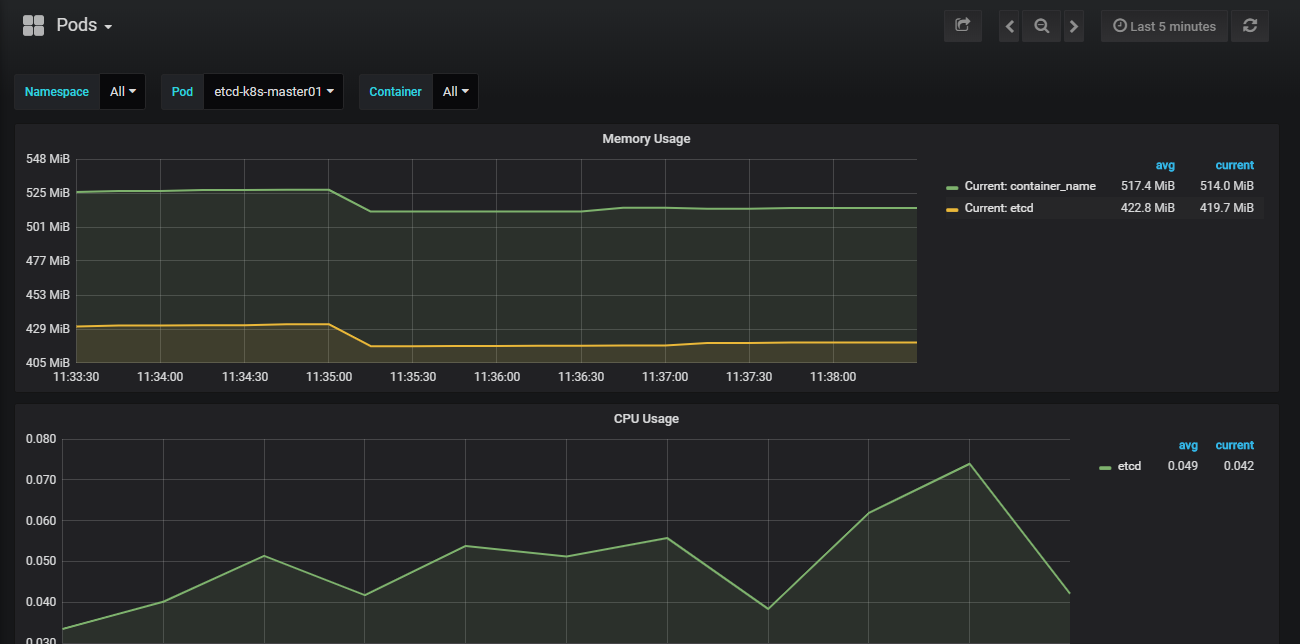
grafana:

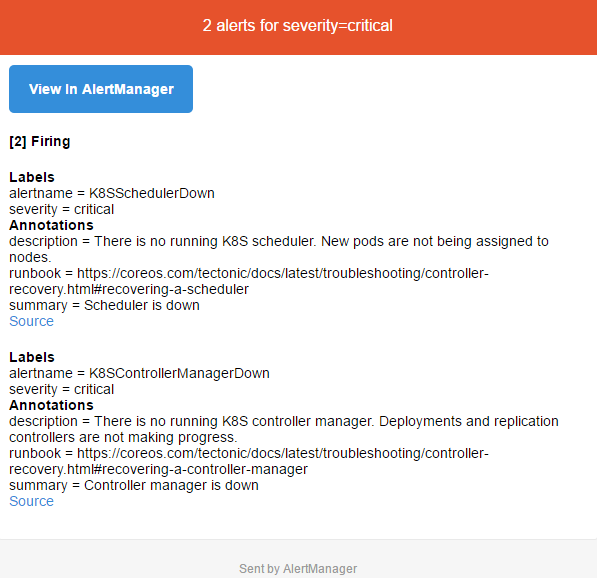
告警邮件查看:
5、卸载
[root@k8s-master01 prometheus-operator]# ./teardown
clusterrolebinding.rbac.authorization.k8s.io "node-exporter" deleted
clusterrole.rbac.authorization.k8s.io "node-exporter" deleted
daemonset.extensions "node-exporter" deleted
serviceaccount "node-exporter" deleted
service "node-exporter" deleted
clusterrolebinding.rbac.authorization.k8s.io "kube-state-metrics" deleted
clusterrole.rbac.authorization.k8s.io "kube-state-metrics" deleted
deployment.extensions "kube-state-metrics" deleted
rolebinding.rbac.authorization.k8s.io "kube-state-metrics" deleted
role.rbac.authorization.k8s.io "kube-state-metrics-resizer" deleted
serviceaccount "kube-state-metrics" deleted
service "kube-state-metrics" deleted
secret "grafana-credentials" deleted
configmap "grafana-dashboard-definitions-0" deleted
configmap "grafana-dashboards" deleted
configmap "grafana-datasources" deleted
deployment.apps "grafana" deleted
service "grafana" deleted
service "etcd-k8s" deleted
servicemonitor.monitoring.coreos.com "etcd-k8s" deleted
......
赞助作者:

kubernetes实战(二十):k8s一键部署高可用Prometheus并实现邮件告警的更多相关文章
- kubernetes实战(二十八):Kubernetes一键式资源管理平台Ratel安装及使用
1. Ratel是什么? Ratel是一个Kubernetes资源平台,基于管理Kubernetes的资源开发,可以管理Kubernetes的Deployment.DaemonSet.Stateful ...
- kubernetes实战(二十六):kubeadm 安装 高可用 k8s v1.16.x dashboard 2.x
1.基本配置 基本配置.内核升级.基本服务安装参考https://www.cnblogs.com/dukuan/p/10278637.html,或者参考<再也不踩坑的Kubernetes实战指南 ...
- kubernetes实战(二十五):kubeadm 安装 高可用 k8s v1.13.x
1.系统环境 使用kubeadm安装高可用k8s v.13.x较为简单,相比以往的版本省去了很多步骤. kubeadm安装高可用k8s v.11 和 v1.12 点我 主机信息 主机名 IP地址 说明 ...
- kubernetes实战(二十九):Kubernetes RBAC实现不同用户在不同Namespace的不同权限
1.基本说明 在生产环境使用k8s以后,大部分应用都实现了高可用,不仅降低了维护成本,也简化了很多应用的部署成本,但是同时也带来了诸多问题.比如开发可能需要查看自己的应用状态.连接信息.日志.执行命令 ...
- Kubernetes实战(二):k8s v1.11.1 prometheus traefik组件安装及集群测试
1.traefik traefik:HTTP层路由,官网:http://traefik.cn/,文档:https://docs.traefik.io/user-guide/kubernetes/ 功能 ...
- saltstack一键部署高可用
一健推送apache [root@server1 minions]# cd /etc/salt/ [root@server1 salt]# vim master [root@server1 salt] ...
- kubernetes kubeadm部署高可用集群
k8s kubeadm部署高可用集群 kubeadm是官方推出的部署工具,旨在降低kubernetes使用门槛与提高集群部署的便捷性. 同时越来越多的官方文档,围绕kubernetes容器化部署为环境 ...
- 企业运维实践-还不会部署高可用的kubernetes集群?使用kubeadm方式安装高可用k8s集群v1.23.7
关注「WeiyiGeek」公众号 设为「特别关注」每天带你玩转网络安全运维.应用开发.物联网IOT学习! 希望各位看友[关注.点赞.评论.收藏.投币],助力每一个梦想. 文章目录: 0x00 前言简述 ...
- 附012.Kubeadm部署高可用Kubernetes
一 kubeadm介绍 1.1 概述 参考<附003.Kubeadm部署Kubernetes>. 1.2 kubeadm功能 参考<附003.Kubeadm部署Kubernetes& ...
随机推荐
- Stay hungry, Stay foolish 的原义
乔布斯在斯坦福大学毕业演讲中说过,他最喜欢的一句话叫做"Stay hungry, Stay foolish". "Stewart和他的人出了好几期<地球产品目录&g ...
- HIGHGUI ERROR: V4L/V4L2: VIDIOC_S_CROP错误解决方法
在树莓派上运行在windows上正确的程序, 报错: HIGHGUI ERROR: V4L/V4L2: VIDIOC_S_CROP OpenCV Error: Assertion failed (s ...
- linux多行注释
1.多行注释: 1. 首先按esc进入命令行模式下,按下Ctrl + v,进入列(也叫区块)模式; 2. 在行首使用上下键选择需要注释的多行; 3. 按下键盘(大写)“I”键,进入插入模式 ...
- 【python3】urllib.error.URLError: <urlopen error [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed (_ssl.c:777)>
在玩爬虫的时候,针对https ,需要单独处理.不然就会报错: 解决办法:引入 ssl 模块即可 核心代码 imort ssl ssl._create_default_https_context = ...
- QSS样式表之PS黑色风格+白色风格+淡蓝色风格(开源)
用QUI皮肤生成器制作皮肤,基本上不超过一分钟就可以生成一套自己想要的皮肤,只要设置八种颜色即可.本人非常喜欢这套黑色风格样式皮肤,特意分享出来,下载地址:https://download.csdn. ...
- Android O 获取APK文件权限 Demo案例
1. 通过 aapt 工具查看 APK权限 C:\Users\zh>adb pull /system/priv-app/Settings . /system/priv-app/Settings/ ...
- 简单了解如何使用vue-router和vue-resource
我们先来看看vue-router 1.npm install vue-router --save 2.调用vue-router: 第一种方法: 直接在main.js中调用 import vueRout ...
- 用ChrootDirectory限制SFTP登录的用户只能访问指定目录且不能进行ssh登录
创建不能ssh登录的用户sftpuser1,密码用于sftp登录: sudo adduser sftpuser1 --home /sftp/sftpuser1 --shell /bin/false s ...
- 移动端前端框架UI库
移动端前端框架UI库(Frozen UI.WeUI.SUI Mobile) Frozen UI 自述:简单易用,轻量快捷,为移动端服务的前端框架. 主页:http://frozenui.github. ...
- 基于spring-cloud的微服务(4)API网关zuul
API网关是微服务架构中的很重要的一个部分,内部有多个不同的服务提供给外部来使用,API网关可以对外做统一的入口,也可以在网关上做协议转换,权限控制和请求统计和限流等其他的工作 spring-clou ...
